Written at the beginning
To record some of my understanding of endpoint security and ideas, for the convenience of future comparisons and discussions with everyone, and for further learning. If there are any errors or omissions, I hope everyone can give some advice. For the parts involving COPY, I will try to indicate the source, because some of the content I cannot remember, and if there is no indication of the source, I hope everyone will correct me.
What is endpoint security
The terms such as endpoint security and endpoint protection refer to the security methods that protect endpoints from the harm of malicious activities. EPP, EDR, CWPP, etc., are all solutions for endpoint security, providing endpoint security capabilities and functions in different ways, methods, perspectives, and roles.
What is called an endpoint

Endpoints are typically computing platforms that have the right to participate in predefined activities, and are the main subjects of various data production, processing, storage, and applications. All endpoints are assets of the organization, providing value to the organization. Currently, the scope of terminals has expanded from traditional PC terminals to a variety of 'general terminals' including mobile terminals, cloud hosts, and IoT (Internet of Things) terminals, or what can be called the new generation of terminals. Traditional dumb terminals and non-intelligent terminals are also moving towards varying degrees of intelligent terminals, and cloud hosts based on virtualization are experiencing explosive growth.
I understand that the current endpoints, in addition to the common PC, server, mobile devices, IoT devices, etc., any device with an operating system deployed at the network edge should be called an endpoint, which should be acceptable.
Endpoint security products
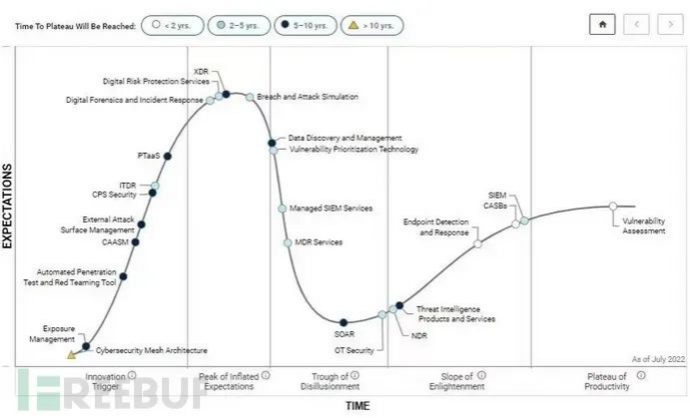
The Gartner 2021 Endpoint Security Maturity Curve shows that emerging endpoint security technologies are mainly reflected in virtual desktop infrastructure (VDI), desktop as a service (DaaS), unified endpoint security (UES), extended detection and response (XDR), and 'AI-based' endpoint security engines. Unified Endpoint Security UES is still in the early stages of innovation; Extended Detection and Response XDR is about to enter the expectation inflation period; endpoint security engines have evolved from 'rule-based' to 'AI-based'; antivirus determination methods have changed from code-based features to user behavior-based malicious determination, from local determination to a combination of cloud and endpoint determination, and then combined with threat intelligence for protection; endpoint security management has been extended to mobile terminals and IoT terminal layers; host security is developing towards the cloud. The Gartner 2021 Technology Maturity Curve shows that Extended Detection and Response (XDR) is in the inflation period, and technologies such as Endpoint Detection and Response (EDR), Security Information and Event Management (SIEM), and Vulnerability Assessment (VA) that have been developed for many years are relatively mature and stable.
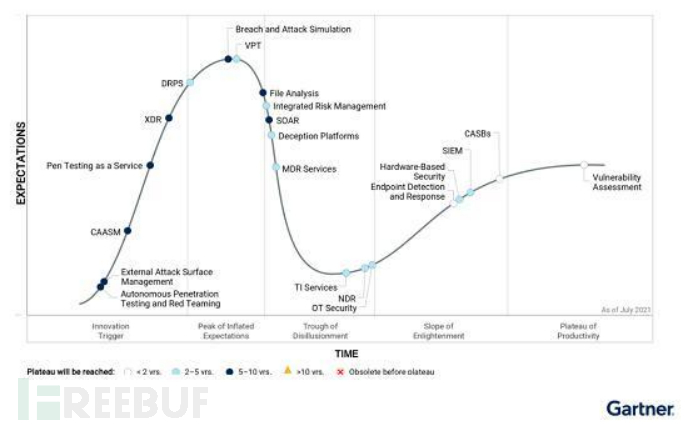
According to Gartner's 2022 Security Operations Maturity Curve, Extended Detection and Response (XDR) has reached the top of the Peak of Inflated Expectations, becoming one of the most popular technologies in the security operations system. Gartner defines XDR as: XDR is a SaaS-based security threat detection and event response tool bound to a specific vendor, which integrates multiple security products into a unified security operations system that contains all licensed security components. The ideal XDR technology is actually the integration of security information and event management (SIEM), security orchestration, automation, and response (SOAR), endpoint detection and response (EDR), and network traffic analysis (NTA) products.
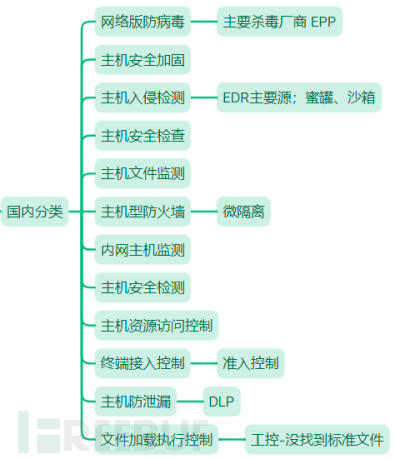
Endpoint-related product categories
It seems that domestically, there has always been a sense of not keeping up with the pace in terms of product names and categories. Each manufacturer needs to put some thought into making their products available in the domestic market. Currently, there are only a few categories of sales licenses, and both new and old products need to match the functions clearly stipulated in these detection standards. For example, most manufacturers of EDR have chosen the path of HIDS host intrusion detection, but some manufacturers have chosen other product categories such as network antivirus. Looking at the HIDS category alone, in addition to EDR, there are also PC sandboxes and honeypot products included. The functions, performance, and roles of various products are very different, but they still use the same detection standards, which have become a way to obtain a certificate by doing some functions unrelated to the product. There are also overlapping functional items among these detection standards, and it is a long way to redefine product standards. There should not have been many products applying for this certificate before EDR was launched. Looking at the many manufacturers making products now, it seems that there should be something like HIPS to create a separate category.
Domestic endpoint security products
Domestic endpoint security products are mainly categorized according to the sales license product classification, mainly including antivirus products, host security reinforcement, host intrusion detection, host security inspection, host file monitoring, host firewalls, internal network host monitoring, host security detection, host resource access control, terminal access control, and host anti-leakage.
1.Host Security Check
1.1Product Description
Technical requirements for security technology of host security check products for information security technology - GAT 1142-2014: The product consists of an agent and a management console. Based on the pre-defined security policy template, the management console performs security checks on the hosts that have installed the agent, collects data, analyzes data, and generates reports through the management console, aiming to discover problems in the security configuration. In addition, the host security check product itself and its internal important data are also protected assets.
The project scenarios to be checked include several aspects: configuration check, system resources (CPU, memory, hard disk), antivirus software, processes, services, system shared resources, startup items, peripheral interface devices, system accounts, software installation, hardware configuration, network connection, and system vulnerabilities.
Host security check products are deployed in a C/S mode or a single-machine mode, and execute security functions. The target of the security check is the host that has installed the engine.
1.2 Main Products
Product Name | Inspection Unit |
Beijing神州泰岳 Software Co., Ltd. | |
Fengyan Host Computing Environment Security Monitoring Platform | Beijing Lingping Data Processing Co., Ltd. |
Bozhi Industrial Control Terminal Baseline Verification System | Jiangsu Bozhi Software Technology Co., Ltd. |
Beijing Bangbang Security Technology Co., Ltd. | |
Yiyang Security Technology Co., Ltd. | |
Shanghai Xishu Information Technology Co., Ltd. | |
Shanghai Anshi Network Technology Co., Ltd. | |
Beijing神州绿盟科技有限公司 | |
Beijing Aike Net Information Technology Co., Ltd. | |
Shenzhen Xinfeng Technology Co., Ltd. | |
Information Technology Co., Ltd. of Communication Industry of China (Beijing) | |
Beijing Communications Signal Research and Design Institute Group Co., Ltd. | |
Beijing Xinyuan Security Configuration Verification Management System | Beijing Beixinyuan Software Co., Ltd. |
Beijing Tianrongxin Network Security Technology Co., Ltd. | |
Beijing Baidu Netcom Technology Co., Ltd. | |
Beijing神州泰岳 Software Co., Ltd. |
2Data Leakage Protection
2.1 Product Description
Technical requirements for security technology of data leakage protection products for information security technology - GA/T 912-2018: Data leakage protection products identify the content of files and data running, stored in or transmitted over the host or network, monitor and control the operation and transmission process of data, and protect data from being leaked out of the security domain in an unauthorized manner; at the same time, such products should also have basic identity authentication, security management, auditing, and alarm functions. The deployment and implementation methods of such products can be divided into host-based, network-based, or integrated (including data clients and network devices).
2.2 Main Products
Product Name | Inspection Unit |
Beijing Mingchao万达 Science and Technology Co., Ltd. | |
Zhejiang Huatu Information Security Technology Co., Ltd. | |
Beijing Yisaitong Technology Development Co., Ltd. | |
Shenzhen UnitedSoft Technology Co., Ltd. | |
McAfee (Shanghai) Software Co., Ltd. | |
Beijing Beixinyuan Software Co., Ltd. | |
Beijing Zhongbao Net盾 Technology Co., Ltd. | |
Beijing Qimingxingchen Information Security Technology Co., Ltd. | |
Beijing Netyee Information Technology Co., Ltd. | |
Beijing Shanshi Netcom Information Technology Co., Ltd. | |
Alibaba Cloud Computing Co., Ltd. | |
Beijing Tianrongxin Network Security Technology Co., Ltd. | |
Symantec Software (Beijing) Co., Ltd. | |
Xiamen Tianrui Science and Technology Co., Ltd. | |
NetDragon Information Technology (Beijing) Co., Ltd. | |
Hangzhou Meichuang Technology Co., Ltd. | |
Beijing神州绿盟科技有限公司 | |
Beijing神州泰岳 Software Co., Ltd. | |
Runlian Software System (Shenzhen) Co., Ltd. | |
Shenzhen Hongtu Chuangcheng Technology Co., Ltd. | |
Shanghai Ruisi Information Technology Co., Ltd. | |
Beijing Sky卫士 Network Security Technology Co., Ltd. | |
SiRuiJiaDe (Beijing) Information Technology Co., Ltd. | |
Beijing Yanqianxin Security Technology Co., Ltd. |
3Host firewall
3.1 Product Description
《GA/T 1177-2014 Information Technology Security Second-generation Firewall Security Technology Requirements》:The host firewall is installed on the end-user computer (including personal computers and servers) in the form of software, preventing threats from outside to inside and from inside to outside. The host firewall can not only monitor and control network-level data flows, but also monitor and control applications, making up for the deficiencies of traditional defense means such as gateway firewalls and antivirus software. In addition, the host firewall generally running on the server can also centrally control all nodes, implement unified security policies and responses.
The assets protected by the host firewall are the host services and files protected by the security policy. In addition, the host firewall software itself and important data such as security policies are also protected assets.
3.2 Main Products
Product Name | Inspection Unit |
Video data resource interconnection front-end security gateway (network-wide) | Shanghai Yuanzhe Electronic Technology Co., Ltd. |
Fujian Wine Pocket Network Technology Co., Ltd. | |
Shenzhen Haqing Shixun Technology Co., Ltd. | |
Beijing Rose Cloud Technology Co., Ltd. | |
Jiangnan Xinyan (Beijing) Technology Co., Ltd. | |
Shanghai Yuanzhe Electronic Technology Co., Ltd. |
4Host resource access control
4.1 Product Description
GA/T 1138-2014 Information Security Technology - Technical Requirements for Host Resource Access Control Products: Host resource access control products for controlled hosts uniformly allocate user login permissions and access permissions to host resources, thereby ensuring that users can access the resources of controlled hosts (including system login permissions, files and folders, peripheral interfaces, applications, processes, etc.) according to predefined access control policies, in order to protect host resources from unauthorized access and use
Host resource access control products are generally composed of three parts: servers, clients, and management consoles. Access control policies are issued from the server to the client. The assets protected are host resources, and the host resource access control products themselves and their internal important data are also protected assets.
4.2 Main Products
Product Name | Inspection Unit |
Beijing Xinda Huanyu Security Network Technology Co., Ltd. |
5 Antivirus
5.1 Product Description
GB/T 37090—2018 Information Security Technology - Technical Requirements and Test Methods for Virus Prevention and Treatment Products: Virus prevention and treatment products are products that use malicious software protection as their entire or partial function, used for detecting, discovering, or preventing the spread of malicious software, and for preventing tampering, theft, and destruction of host operating systems, application software, and user files.
5.2 Main Products
Beijing Anhua Doctor Information Security Technology Co., Ltd. | |
Beijing Antiy Network Security Technology Co., Ltd. | |
Beijing Beixinyuan Software Co., Ltd. | |
Beijing Chenxin Lingchuang Information Technology Co., Ltd. | |
Beijing Dongfang Weidian Information Technology Co., Ltd. | |
Beijing Guanqun Jinchen Software Co., Ltd. | |
Heng'an Jiaxin Zombie Network Trojan and Worm Monitoring and Disposal System | Beijing Heng'an Jiaxin Security Technology Co., Ltd. |
Beijing Huorong Network Technology Co., Ltd. | |
Beijing Jiangmin New Technology Co., Ltd. | |
Kingsoft Security Antivirus System (Special Network Edition) | Beijing Hunter Security Technology Co., Ltd. |
Tianxun Internal Network Security Risk Management and Audit System | Beijing Qimingxingchen Information Security Technology Co., Ltd. |
Beijing Rising Network Security Technology Co., Ltd. | |
Beijing神州绿盟科技有限公司 | |
Beijing Tianrongxin Network Security Technology Co., Ltd. | |
Beijing Unisource Information Technology Co., Ltd. | |
Beijing Netyee Information Technology Co., Ltd. | |
Hangzhou Anheng Information Technology Co., Ltd. | |
Heng'an Jiaxin Zombie Network Trojan and Worm Monitoring and Disposal System | Heng'an Jiaxin (Beijing) Technology Co., Ltd. |
Kaspersky Technology Development (Beijing) Co., Ltd. | |
McAfee (Beijing) Security Software Co., Ltd. | |
Qianxin Technology Group Co., Ltd. | |
Shenzhen Xinfeng Technology Co., Ltd. | |
Shenzhen Bit梵德 Technology Co., Ltd. | |
Unisoft UniEDR Terminal Detection and Response System (Antivirus) | Shenzhen UnitedSoft Technology Co., Ltd. |
Shenzhen Tencent Computer System Co., Ltd. | |
Shenyang Dongruo System Integration Engineering Co., Ltd. | |
Microsoft (China) Co., Ltd. | |
Yaxin Security Antivirus Wall Network Edition Software OfficeScan | Yaxin Technology (Chengdu) Co., Ltd. |
6Internal Network Host Monitoring
6.1 Product Description
The 'GA/T 910-2010 Information Technology - Security Technology for Internal Network Host Monitoring Products': A product that monitors various activities on controlled hosts using an agent/server structure.
6.2 Main Products
Product Name | Inspection Unit |
Beijing Beixinyuan Software Co., Ltd. | |
Beijing Dingpu Technology Co., Ltd. | |
Beijing Lisense Computer Technology Co., Ltd. | |
Beijing Hunter Security Technology Co., Ltd. | |
Beijing Pusishidai Technology Co., Ltd. | |
Tianxun Internal Network Security Risk Management and Audit System | Beijing Qimingxingchen Information Security Technology Co., Ltd. |
Beijing Sipeng Great Wall Information Technology Co., Ltd. | |
Beijing Shengbo Run High-tech Co., Ltd. | |
Beijing Tianrongxin Network Security Technology Co., Ltd. | |
Beijing Wanlihong Science and Technology Co., Ltd. | |
Beijing Netyee Information Technology Co., Ltd. | |
Xinda Information Security Protection System - Security Management System | Beijing Xinda Huanyu Security Network Technology Co., Ltd. |
Hangzhou Lishishen Anke Technology Co., Ltd. | |
Yingao Multi-dimensional Terminal Security Management System | Hangzhou Yinggao Technology Co., Ltd. |
LanTun Internal Network Security Management and Audit System | LanTun Information Security Technology Co., Ltd., LanTun Information Security Technology Co., Ltd. |
Qianxin Technology Group Co., Ltd. | |
Shanghai Gaogong Information Technology Co., Ltd. | |
Shanghai Xina Information Technology Development Co., Ltd. | |
Shenzhen UnitedSoft Technology Co., Ltd. | |
Tencent Cloud Computing (Beijing) Co., Ltd. | |
Xi'an Jiaotong University Jiepu Network Technology Co., Ltd. | |
AINSG-TSM Security Terminal Management System of Yaxin Security | Yaxin Technology (Chengdu) Co., Ltd. |
7 Terminal Access Control
7.1 Product Description
The 'GA/T 1105-2013 Information Technology - Security Technology for Terminal Access Control Products': A product that implements access control based on user identity and terminal security status for terminals accessing the local area network using authentication methods such as 802.1x. This type of product can detect the behavior of terminals accessing the network and take appropriate measures according to the access control strategy to ensure that unauthorized or non-compliant terminal devices cannot access the network, and sets up remediable isolation areas for terminals to correct their own security status to meet the security policy requirements.
7.2 Main Products
Product Name | Inspection Unit |
Beijing Aike Net Information Technology Co., Ltd. | |
Beijing Beixinyuan Software Co., Ltd. | |
Beijing Jiangnan Tian'an Technology Co., Ltd. | |
Beijing Lisense Computer Technology Co., Ltd. | |
Beijing Qimingxingchen Information Security Technology Co., Ltd. | |
Beijing Shengbo Run High-tech Co., Ltd. | |
Beijing Tiandihexing Technology Co., Ltd. | |
Beijing Tianrongxin Network Security Technology Co., Ltd. | |
Beijing Wanlihong Science and Technology Co., Ltd. | |
Beijing Netyee Information Technology Co., Ltd. | |
Beijing Winut Technology Co., Ltd. | |
Beijing StarNet Ruijie Network Technology Co., Ltd. | |
Gel Software Co., Ltd., Shanghai Gel Security Technology Co., Ltd. | |
Guangzhou Safeguard Information Technology Co., Ltd. | |
Guodian Nanrui Science and Technology Co., Ltd. | |
Hangzhou Yinggao Technology Co., Ltd. | |
Hangzhou Yu Xia Technology Co., Ltd. | |
Huawei Technologies Co., Ltd. | |
Shandong Huaruan Jindun Software Co., Ltd. | |
Zhongwang Yun'an Network Access and Service Management System | Shandong Zhongwang Yun'an Intelligent Technology Co., Ltd. |
Shenzhen Xinfeng Technology Co., Ltd. | |
Shenzhen UnitedSoft Technology Co., Ltd. | |
Tangs (Beijing) Technology Co., Ltd. | |
Xinhua Three Technology Co., Ltd. | |
Yinsaike Technology (Beijing) Co., Ltd. | |
China Software & Technology Services Co., Ltd. |
8 Host security detection
8.1 Product Description
The 'GA/T 1536-2018 Information Technology - Computer Host Security Detection Product Assessment Criteria': The indicators of such products involve detection capabilities of viruses, identity authentication, access control, security auditing, residual information protection, intrusion prevention, malicious code prevention, resource control, and data detection.
8.2 Main Products
Product Name | Inspection Unit |
Beijing Antiy Network Security Technology Co., Ltd. | |
Beijing Tiandihexing Technology Co., Ltd. |
9 Host-based intrusion detection
9.1 Product Description
The 'GAT 403.2-2014 Information Technology - Intrusion Detection Product Security Technical Requirements Part 2: Host-based Products': Host-based intrusion detection products use system logs, application logs, and other means (such as monitoring system calls) to collect information from the target host for analysis, thereby discovering intrusion detection systems with abnormal behavior.
9.2 Main Products
Product Name | Inspection Unit |
Beijing Antiy Network Security Technology Co., Ltd. | |
Beijing Jieshi Security Technology Co., Ltd. | |
Beijing Qihoo Technology Co., Ltd. | |
Beijing Qimingxingchen Information Security Technology Co., Ltd. | |
Beijing Shengxin Network Technology Co., Ltd. | |
Beijing Tianrongxin Network Security Technology Co., Ltd. | |
Beijing Netyee Information Technology Co., Ltd. | |
Beijing Xiaoyou Technology Co., Ltd. | |
Beijing Yuanzhidian Information Security Technology Co., Ltd. | |
Beijing Yunyi Technology Co., Ltd. | |
Beijing Changting Future Technology Co., Ltd. | |
Beijing Zhi Ren Zhi Xin System Integration Co., Ltd. | |
Beijing Zhonganwangxing Technology Co., Ltd. | |
Guangzhou Feifan Information Security Technology Co., Ltd. | |
Guoli HuaYe Technology Co., Ltd. | |
Hangzhou Anheng Information Technology Co., Ltd. | |
Hangzhou Yidun Information Technology Co., Ltd. | |
Huawei Technologies Co., Ltd. | |
Hypersight (H-Sensor) Intrusion Perception and Threat Tracing System | Jiangsu Chuanyu Shield Security Technology Co., Ltd. |
SecurityDog Cloud Eye - (Cloud) Host Intrusion Detection and Security Management System | Xiamen Fuyun Information Technology Co., Ltd. |
Shanghai Guan'an Information Technology Co., Ltd. | |
Shenzhen Xinfeng Technology Co., Ltd. | |
Shenzhen UnitedSoft Technology Co., Ltd. | |
Tencent Cloud Computing (Beijing) Co., Ltd. | |
NetDragon Information Technology (Beijing) Co., Ltd. | |
Wangsu Technology Co., Ltd. | |
Youkai Data Storage Technology Co., Ltd. |
10 Host File Monitoring
10.1 Product Description
The 'GAT 1392-2017 Information Security Technology Host File Monitoring Product Security Technical Requirements': Host file monitoring products, based on predefined security policies, monitor and alarm the status and modification behavior of host files (including important system files, configuration files stored on the host, and other predefined files) through means such as file integrity checks, file attribute checks, and keyword checks, thereby ensuring that the file resources on the host are not accessed and operated without authorization.
10.2 Main Products
Product Name | Inspection Unit |
Anxinwangdun (Beijing) Technology Co., Ltd. | |
Beijing JiaoTu Technology Co., Ltd. | |
Beijing Shengxin Network Technology Co., Ltd. | |
Beijing Weibu Online Technology Co., Ltd. | |
Beijing Zhongdun Security Technology Development Co., Ltd. | |
Guangdong Yanjie Electronics Technology Co., Ltd. | |
Guangzhou Anhong Network Technology Co., Ltd. | |
Mingyu Host Security and Management System Endpoint Security Management System | Hangzhou Anheng Information Technology Co., Ltd. |
Hangzhou Meichuang Technology Co., Ltd. | |
Yinggao Internet Access Confidentiality Review Assistance System | Hangzhou Yinggao Technology Co., Ltd. |
Heng'an Jiaxin (Beijing) Technology Co., Ltd. | |
Huidun Information Security Technology (Suzhou) Co., Ltd. | |
McAfee (Shanghai) Software Co., Ltd. | |
Shanghai Guan'an Information Technology Co., Ltd. | |
Shanghai Yiheng Software Co., Ltd. | |
Shenzhen Shenmi Xin'an Technology Co., Ltd. | |
Suzhou Guanchen Computer Information Technology Co., Ltd. | |
Tencent Cloud Computing (Beijing) Co., Ltd. | |
Qianxin Network Immortal Cloud Lock Server Security Management System | NetDragon Information Technology (Beijing) Co., Ltd. |
Xinhua Three Technology Co., Ltd. |
11 Host Security Enhancement
11.1 Product Description
According to 'GAT 1393-2017 Information Technology - Host Security Enhancement System Technical Requirements': The host security enhancement system is based on the general operating system, and by means of security marking of the operating system subjects and objects, adding mandatory access control, integrity protection and other technical means, the security functions of the operating system are enhanced to make up for the defects of the low security of the general operating system, and improve the security protection capability of the operating system.
11.2 Main Products
Product Name | Product Type | Inspection Unit |
An Tong Enchuang Information Technology (Beijing) Co., Ltd. | ||
Beijing Beixin Yuan Software Co., Ltd., Beijing Zhongruo Huatai Information Technology Co., Ltd. | ||
Beijing Chuang'an Hengyu Technology Co., Ltd. | ||
Beijing Guoji Huadian Technology Co., Ltd. | ||
Beijing San Shi Zhen Zhi Information Technology Co., Ltd. | ||
Beijing Tiandihexing Technology Co., Ltd. | ||
Beijing Southwest Jiaotong University Shengyang Science and Technology Co., Ltd. | ||
Beijing Youxuan Software Co., Ltd. | ||
Beijing Zhongnengke Yue Electric Power Technology Co., Ltd. | ||
Hangzhou Tingfeng Yun Technology Co., Ltd. | ||
Mao Sheng Wisdom (Beijing) Technology Co., Ltd. | ||
Nanjing NARI Information and Communication Technology Co., Ltd. | ||
Shenzhen可信计算技术有限公司 | ||
Shenzhen Rong'an Network Technology Co., Ltd. | ||
Qianxin NetDragon Cloud Lock Server Operating System Security Enhancement System (Linux Edition) | NetDragon Information Technology (Beijing) Co., Ltd. | |
Yaxin Security Terminal Security Fortification Software AOS-ISL-PLUS | Yaxin Technology (Chengdu) Co., Ltd. | |
Yinsaike Technology (Beijing) Co., Ltd. |
12 Host Security Audit
12.1. Product Description
GBT 20945—2013 Information Security Technology System Security Audit Product Technical Requirements and Test Evaluation Method: Records and analyzes events of host systems and takes corresponding actions for specific events.
12.2. Main Products
Product Name | Inspection Unit |
Beijing Guapanchuanshi Technology Development Co., Ltd. | |
Beijing Kunyuanhengtai Technology Development Co., Ltd. | |
Beijing Tiandihexing Technology Co., Ltd. | |
Beijing Englishpeak Technology Co., Ltd. | |
Beijing Zhongke Fuxing Information Technology Co., Ltd. | |
Guangzhou Jinxing Network Technology Co., Ltd. | |
LanTun Information Security Technology Co., Ltd. | |
Shandong Jinyu Electronic Technology Co., Ltd. | |
Shanghai Hanbang Jingtai Digital Technology Co., Ltd. | |
Shanghai Huawanda Information Technology Development Co., Ltd. |
International Classification of Endpoint Security
Classification | Descriptive Definition |
EDR | Endpoint Detection and Response: An active endpoint security solution that records terminal and network events and stores this information locally on the endpoint or in a centralized database. It combines known attack indicators (Indicators of Compromise, IoCs), behavioral analysis databases, continuous data search, and machine learning technologies to monitor any potential security threats and respond quickly to these threats. It also helps in quickly investigating the scope of the attack and provides response capabilities. |
EPP | Endpoint protection platforms: Terminal protection platform; It is an integrated solution with functions such as anti-malware, personal firewall, port and device control. The EPP solution usually also includes: vulnerability assessment, application control, application sandboxing, enterprise mobility management (EMM) (usually in parallel non-integrated products), memory protection, monitoring of application code behavior, endpoint detection and repair technology, full-disk and file encryption, also known as mobile data protection; endpoint data loss prevention (DLP) |
CWPP | Cloud Workload Protection Platforms: Cloud work protection platforms; Aimed at multi-cloud/hybrid cloud environments, large-scale distributed deployment, and product forms with continuous security protection capabilities for cloud workloads (virtual machines and containers). It provides a way for information security leaders to protect these workloads through a unified management platform and provides a way to express security policies regardless of where the workloads run on infrastructure |
UES | Unified Endpoint Security: Unified endpoint security; By the internal needs of IT organizations, all security events are presented in the same security control center |
UEM | Unified Endpoint Management: Unified endpoint management; Beyond managing PCs and mobile devices, it provides more in-depth endpoint analysis and integration of identity and access management |
XDR | Extended Detection and Response: Extended threat detection; A threat detection and event response tool for specific suppliers, which unifies multiple security products into a single security operating system |
MDR | Managed Detection and Response: Operation detection and response; Provides services for buyers who hope to improve threat detection, event response, and continuous monitoring capabilities, but lack professional knowledge or resources |
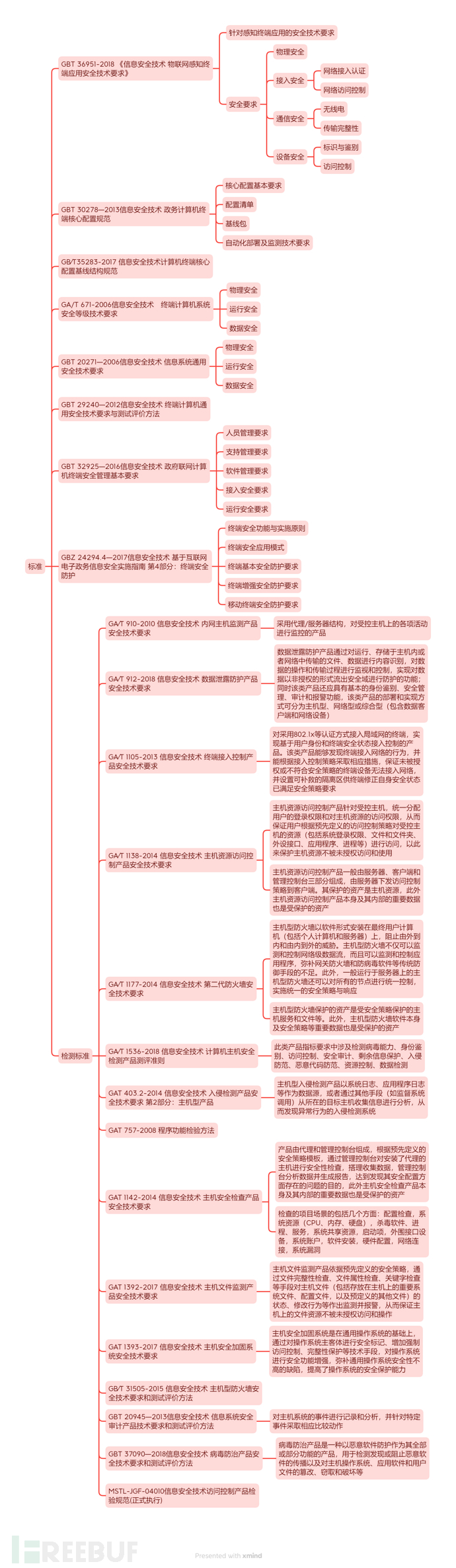
End-point related standards
Listed some standards, not sure if they are complete
Endpoint Security Discussion (Twelve) - Wazuh Discussion (Part One)
Endpoint Security Discussions (Fourteen) Wazuh White Paper (Part 2)
A brief discussion on security detection in the context of security attack and defense scenarios
Endpoint Security Discussions (V) Some ideas
A Brief Discussion on Data Security Governance and Hierarchical Classification Implementation
评论已关闭