Written in advance
Many lists have been mentioned before about products and manufacturers, and later, some ideas will be discussed, both with extracts and descriptions.
Some ideas
Enterprises need a monitoring and reporting system to provide feasible data on the current state of enterprise assets, collect as much information as possible about the network infrastructure and communication status, and use it to improve their security status. Similarly, enterprises should also collect as much information as possible about endpoint systems and asset status, and use it to improve their security status. Endpoint security products should always work as if there were attackers on the endpoint. The endpoint security detection and response system based on static feature and behavior analysis is mainly used for the identification, detection, protection, and response of risk threats on the endpoint, providing security protection capabilities for endpoint assets such as operating systems, applications, services, and users on terminal and server endpoint systems, and achieving effective detection of known and unknown threats.

Unified functions such as security protection, terminal management, operation and maintenance management, and document management to provide a lower total cost of ownership. Automatically collect and correlate data from multiple proprietary security components to improve risk analysis and response capabilities while reducing the performance consumption on the terminal. By combining UES and XDR, the terminal load will be lower, and the overall protection effect will be better.
The solution is based on a unified information, a single data collection, a data bus, a process engine, and a graphical platform, with the basic idea of decentralized control, centralized operation, hierarchical management, flexible configuration, and convenient configuration.
A unified information: various security products and management products deployed on the endpoint should have unified data information names, formats, and identifiers, whether they are deployed independently or as components/modules, which is convenient for later data analysis and processing.
A data collection: the primary function of the endpoint client is data collection. For general basic data content, such as operating system information, host information, network and application information, etc., it should be prohibited to read repeatedly by various components and modules to reduce system consumption.
A data bus: the processing of metadata collected by endpoint security products should be processed one by one through strategies in a pipeline manner, to prevent repeated operations such as screening and matching.
A process engine: the processing, analysis, and alarm of metadata in the system should be handled through a unified event response mechanism for event types, time, subjects, objects, and event details, etc.
A graphical platform: all endpoint data, events, alarms, and other content should be displayed on the same graphical interface. Administrators can view and handle operations for all endpoints within their management scope through this graphical platform.
Target and purpose
The endpoint security product line aims to continuously ensure asset security, relying on risk identification, security defense, security detection, security response, and security recovery technologies, integrating EPP\EDR\CWPP and other single control consoles into a unified platform to provide better security protection and simpler management.
- Basic environment
Endpoint security products are widely deployed in various hosts and devices, and need to be compatible with mainstream operating systems on the market to meet users' needs for endpoint unified management.
- Core technical capabilities
IoA enables users to actively seek potential attack signals, IOC covers basic security needs, IOB is used to meet higher security needs; based on the IoA method, security teams can collect and analyze network behavior in real-time and accurately, based on IOC detection is the industry's conventional, can be carried out retrospective analysis, based on behavioral IOB detection can do threat tracking, with the ability to discover potential risks.
- Basic capabilities
Realize various basic functions, forming endpoint products adapted to different application scenarios and environments through functional coupling and combination.
- Visualization
Identify, protect, detect, respond, and dispose of security risks and events need to be presented in a visual way, allowing users to have a direct sense, experience, and operation, graphical display and operation allow users to directly perform various operations on risks and security events, forming their own knowledge accumulation.
- Continuous operation
Through endpoint security operations, users can continuously improve their corporate endpoint security protection capabilities during the use of the product, and at the same time, they can also improve the product and service in terms of functional requirements, design, operation, and other aspects.
- Linkage and docking
Achieve overall security protection through integration with platforms such as SIEM, SOC, and state awareness; define new endpoint security products through technologies such as UEBA and SOAR.
Main capabilities
- Endpoint security solutions can resist known and unknown malware without depending on daily updates, many domestic environments cannot directly connect to the Internet. Relying on scheduled updates and rules does not solve the problem but makes it more麻烦.
- Can detect malicious activities based on the behavior of the process.
- Store IoC, IoA, IoB data in a centralized location for retrospective analysis.
- Provide the ability to detect and prevent fileless attacks.
- Can automatically delete malicious software when detected, that is, delete/isolate files/terminate processes. Domestic users are difficult to allow the system to automatically delete malicious files, which is not only considering the possibility of accidental deletion but also the consequences of not trusting the product itself and being unable to control it after deletion. There are also cases where a system needs to run with malware.
- Allow suppression and ignoring false positives from the management console without excluding all protection technologies, such as file detection suppression, but still monitor behavior. Filtering and merging of various event reports are essential skills of the product, and malicious behavior of可信 files should be recorded and alarmed.
- The management center supports the use of a multi-tenant infrastructure based on cloud-based SaaS-style operated, managed, and maintained by the supplier. Multi-tenant functions are very necessary in the current application environment, and both manufacturers and users are worthy of having.
- The management center view displays the complete process tree to identify how the process was generated and perform actionable root cause analysis. Product logic usage.
- Provides threat hunting, including tools to search across multiple endpoints from the management center for IoC/IoA/IoB (such as, file hashes, source/target IP, registry entries).
- Identifies changes made by malware and provides recommended remedial steps or rollback functions. It's indeed a cool ability if you can roll back or remediate files, folders, and configuration files.
- Provides options to integrate threat intelligence and reputation services into the management center, connect to various external threat intelligence sources, and import/export black and white lists.
- Implement protection against common application vulnerabilities and memory exploitation techniques.
- When the hosted endpoint device is located outside the company network or in an offline state, continue to collect suspicious event data, and the client should be able to execute and record independently.
- Can perform static on-demand malware detection scans on folders, drives, or devices (such as USB drives).
- All functions are provided in a single client program or directly integrated into the operating system.
- Implements virtual patches for known vulnerabilities in the operating system and non-operating system applications.
- Regulates risk-based vulnerability reporting and priority, which is also required in the detection standards for vulnerability and patch management.
- Implements configurable default blacklists.
- Supports advanced queries of the database using operators and thresholds (i.e., 'Show all machines with new portable executable PE files in less than a week, and on less than 2% of machines or unknown machines').
- The endpoint client program includes endpoint lures designed to expose attackers.
- Provides application isolation to separate untrusted applications from the rest of the system (container/sandbox or hardware-based management program).
- The report should include guiding analyses and remedial measures based on collected intelligence, and what are the next steps needed to mitigate this threat?
- Provides the ability to report attribution information and potential motives behind the attack.
- Provides the ability to automatically integrate multiple alerts from multiple sources into a single event.
- Has the ability to associate and enrich multiple weak events/alerts from multiple sources/sensors into strong detection.
- Allows coordination of responses and interconnection across multiple security products.
Main Function
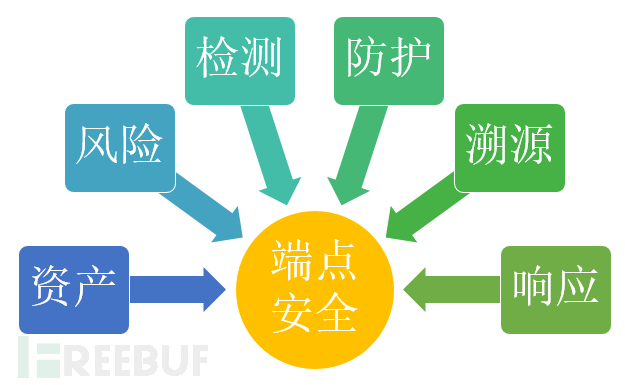
It is very similar to IPDRR, but also quite different. The subsequent content will be expanded separately.
评论已关闭