As I have encountered two interviews recently that asked about emergency-related knowledge points, and I also had an emergency response training a few days ago, I thought it would be good to review the knowledge and briefly summarize some handling plans in emergencies, which is convenient for handling emergency events efficiently.
The following content is all summarized from practice, and I believe that handling emergency events must be carried out in the fastest way to solve the problem. Tools are attached to the articles, and from the perspective of operational thinking, beginners can also handle some routine emergency events accordingly.

Firstly, the event classification encountered in the emergency response process, the common types are basically web page tampering, web page trojan, ransomware, mining malware, denial of service attack, DNS hijacking, IOC alert, APT attack, etc. The following will explain the handling plans for these situations.
Web page tampering
Web page tampering can also be classified into the following three situations
Routine suicide type, directly replace the homepage file, which may be a prank by some hackers.
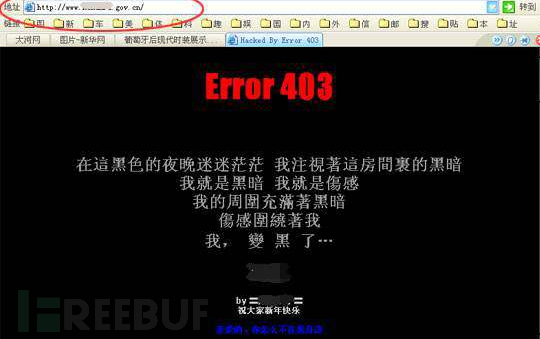
For black hat activities, the web page is redirected to a菠菜 website, and this type is generally used to scan in batches with scripts and automatically modify certain file contents, and redirect the access to the target菠菜 website.

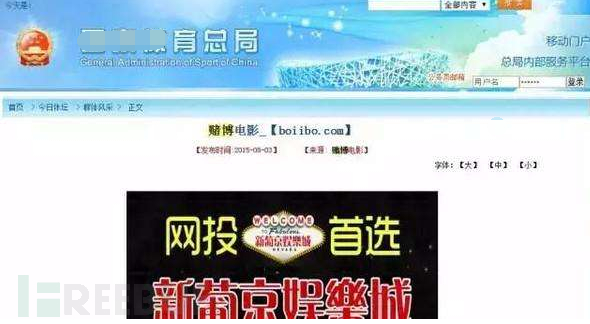
In addition to direct jumps, there is also a type where the website is normally accessed, but when searching through Baidu and other search engines, some article content is replaced.
For the first two types, when accessing the homepage and finding it is a black page or a菠菜 website, we need to check whether the page is affected by DNS hijacking, and this step can be completed with a simple ping command.
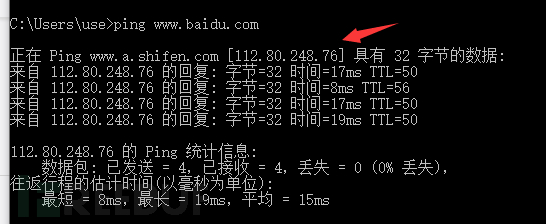
If there is no problem with the IP address of the domain name resolution, it is indeed the customer's IP address asset (PS: if it is a CDN situation, then see if the CDN is the user's own), without considering the situation that the CDN has also been hacked, it can basically be confirmed that the web page has indeed been tampered with.
For the handling plan of this type of event, it should be prioritized to disconnect the user from the network, at least disconnect the external mapping first, and then use it locally.D盾Perform webshell malware scanning, and delete the confirmed malware (this step should first communicate with the website administrator to confirm, to avoid accidental deletion).
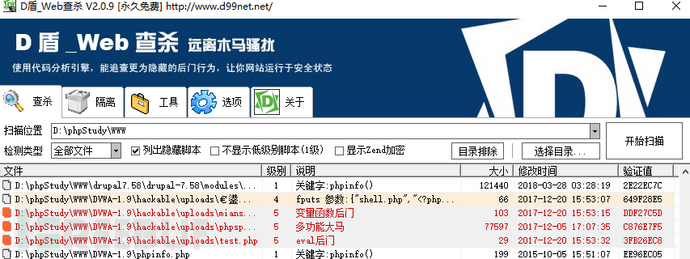
After reviewing the web logs, suspicious accesses within the time period of the modified page, such as 2017-12-20 15:53 (you can start with a week before and after this period), are filtered. Combined with the malware feature names scanned, such as the filename feature of test.php, a comprehensive judgment is made to confirm the attack IP, and then the access records of the attack IP are inferred to identify potentially vulnerable files, and code analysis and repair are carried out.
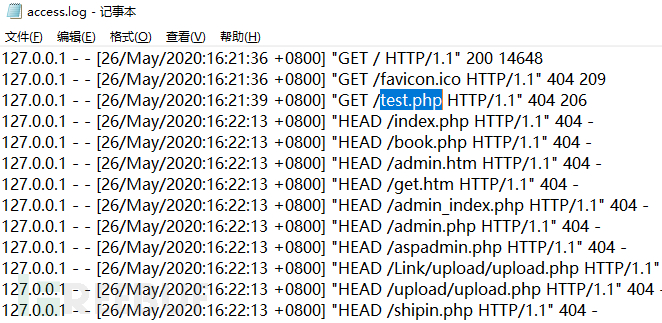
After the website is restored and backed up, the processing is complete.
In some cases, the user may not have a backup file. In this case, it is recommended to use the seay source code audit tool to search for keywords in the website source code, such as referer, the ua of various search engines, and the corresponding betting website domain names. Of course, there may be situations where the content is encrypted, and the handling method can only be to investigate the files modified in recent days according to the file modification time.
Web page trojan horse
The event of web page trojan horse is that hackers leave a trojan backdoor after hacking into the website. It is generally detected by security products or some security companies, and the relevant administrators need to take emergency measures after receiving the email notification.
The way to deal with trojans is the same as that of tampering events, use D shield all at once, and then analyze the logs, screen through the trojan name characteristics, and analyze the intrusion process.
It is also possible to encounter the problem of no existing logs. At this time, it is necessary to first understand and analyze the target environment, obtain necessary information from the website administrator, such as the operating system version, the external mapping ports, the type of website middleware, whether the website is secondary developed, which CMS is used, considering that the rce of fastjson is increasing recently, it is necessary to understand the development language and version information used by the website, and thus infer the possible vulnerabilities existing on the website. For example, if it is learned that the website uses weblogic 10.3.6, and considering that weblogic has been contributing vulnerabilities to the security community, then this is likely the problem. Based on this inference, we can use relevant tools for verification.
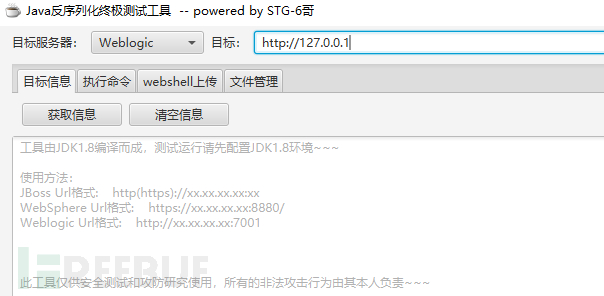
If there are existing vulnerabilities, it is likely that this problem leads to the website being hacked.
No matter web page tampering or trojan horse, it is recommended to regularly do security assessment work for subsequent protection.
Ransomware
In general, when ransomware arrives at the customer's site, the first thing to do is to communicate with them. From my personal experience, I have encountered several times where the communication with the sales team may be the problem. After handling the tracing on the scene, the customer still asked, 'We don't have backups, can the data be recovered?' As a service person on the side, I can only tell him that if you are not ready to pay, then the data is basically unrecoverable. Therefore, that emergency ended was not very pleasant, so in the subsequent emergency process, I will communicate with the customer first and clarify the needs before carrying out the emergency.
The characteristics of ransomware are generally very obvious, and they will attach a considerate readme.txt after encryption.
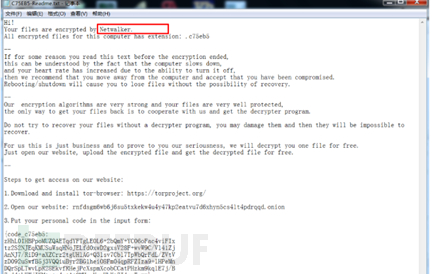
And you can also find the name they gave to this ransomware wave in the readme. Although the files are probably unrecoverable, it is necessary to have relevant evidence, which can be found inhttps://lesuobingdu.qianxin.comAfter inquiry, based on file information, we found netwalker and confirmed that it cannot be recovered.
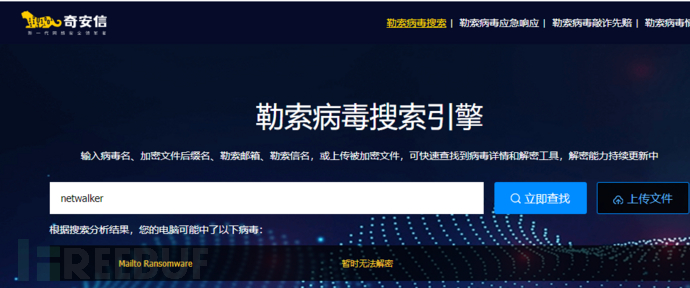
The handling of ransomware mainly focuses on tracing the source, with the purpose of preventing the host from being infected again and avoiding the infection of more hosts. Therefore, the first step on the scene is to disconnect the target host (unplug the network cable).
Actually, from the perspective of probability theory, the target customer is unlikely to be the only one affected, so there must be some relevant analysis materials on the Internet. Generally, search engine search similar keywords can be found.
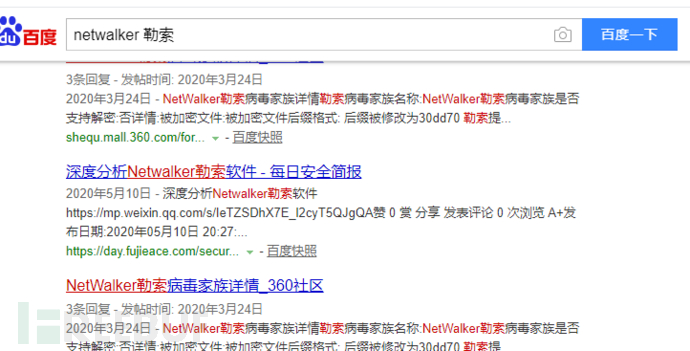
it is very easy to find the corresponding analysis, and then carry out corresponding disposal based on the analysis.
Considering that it is not possible to find relevant analysis articles online, it is usually possible to first find the corresponding analysis through360 AntivirusandHuorongthese security software to locate the trojan
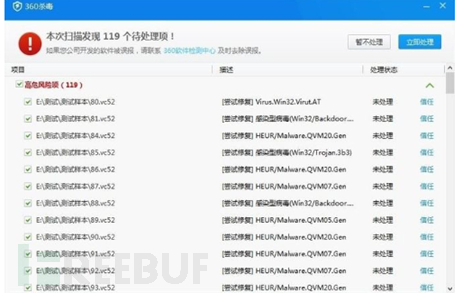
Then put it into an automated sandbox for analysis. This recommendsWeiboyun sandbox
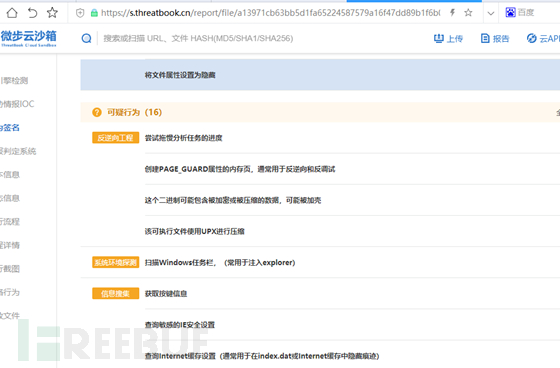
Because I am not familiar with reverse binary, I can only rely on this kind of sandbox for analysis. If there are experts with strong reverse engineering skills, you can ignore this step.
Based on the results of the sandbox run, we can take corresponding preventive measures. This is a simple analysis process. After handling a machine, we usually need to trace the source, which directly checks the system log login records, investigates suspicious records. It needs to be explained that ransomware generally enters through system weak passwords or remote code execution vulnerabilities, so a permission to execute shell commands is needed, and the process of obtaining permissions to execute commands must have a relative login record, so it is recommended to view the 4625 and 4624 records in the log, which is too time-consuming to do manually.A tool written by the big guy uknowOne-click to view login records, very convenient.
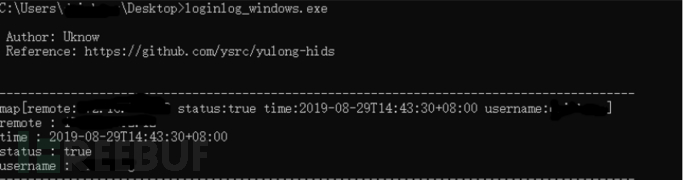
Find the suspicious target IP and then repeat the above steps to find the source target host. According to experience, more than 80% of the cases encountered are due to weak passwords on the source host, such as Pass1234 and Admin@123, which seem to be safe passwords.
Therefore, for the defense against ransomware, it should mainly focus on changing complex passwords and timely updating patches, and VPN or ACL can be used if conditions permit.
Mining trojan
Mining trojans can generally be confirmed by checking the current CPU running status, which can be seen in the Windows task manager, or use the top command under Linux to see if a process keeps running at 80%-90% or more of the CPU, which is basically the corresponding trojan process. In Windows, you can usually locate the corresponding directory by selecting and right-clicking on the file location of the process.
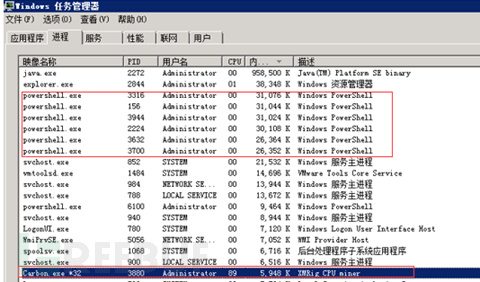
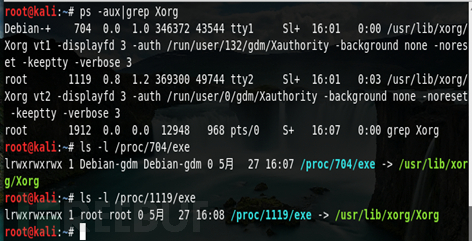
Under Linux, you can use ps -aux|grep "trojan process name" to find the corresponding path and file
After locating the trojan, you need to perform a cleanup operation. The trouble with mining trojans is that they stay in the system, and Windows recommends Microsoft'sautorunsI personally think it is very useful, as it avoids the hassle of manually checking the registry and startup items.
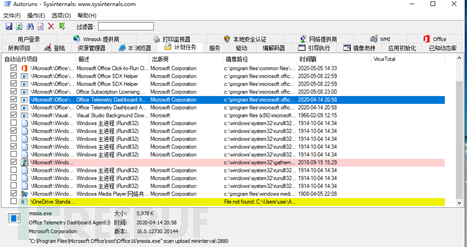
Find the scheduled tasks, services, WMI, etc., related to mining processes and trojans, and clean them up. Of course, you need to end the trojan process and delete the trojan file before restarting to observe whether there are any problems.
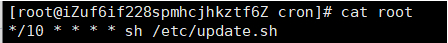
Under Linux, it is generally written in the scheduled task crontab -l command or ls /var/spool/cron/ to check for any suspicious content.
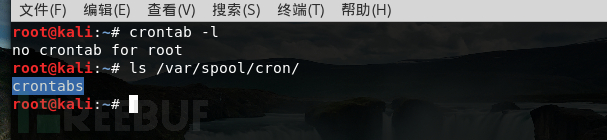
After finding the malware script, clean it up together
For the tracing of malware, the analysis results of the logs are mainly used. If only the web service port is open, after locating the time range, carry out an investigation. If other ports are open, you need to investigate according to the script creation time. The thinking is limited, and it is focused on directly obtaining system permissions issues, such as management software issues with weak passwords in ssh under Linux, system vulnerability issues with unauthorized issues in redis, and application layer issues such as rce in middleware weblogic.
Under Windows, in addition to website logs, system logs are mainly used.
There are many logs under Linux, you can refer to the following paths for analysis
Path 1: /var/log/messages: Records Linux kernel messages and public log information of various application programs
Path 2: /var/log/cron: Records event information generated by crond scheduled tasks
Path 3: /var/log/dmesg: Records various event information during the Linux operating system's boot process
Path 4: /var/log/maillog: Records email activities entering or leaving the system
Path 5: /var/log/lastlog: Records the most recent login events of each user
Path 6: /var/log/secure: Records security event information related to user authentication
Path 7: /var/log/wtmp: Records each user's login, logout, and system startup and shutdown events
Path 8: /var/log/btmp: Records failed, incorrect login attempts, and verification events
Another point to note is that mining and ransomware often accompany worm events. I haven't categorized them separately because in this era, it is almost impossible to see worms that simply cause destruction (here refers to the field we can encounter in daily life, not including those events such as national power outages organized by some countries), because those attackers are mainly for profit, and simple destruction can't bring any benefits.
In practice, I have encountered many cases of blue screen and restart phenomena in large-scale local area networks. On-site inspections are mostly due to the spread of MS17010. Of course, to confirm, you can runA tool written by the big guy uknow, you can see a large number of failed anonymous login requests, and you can also use msf's auxiliary/scanner/smb/smb_ms17_010 module to confirm it within the internal network. If there is a backdoor after the attack is successful, there will be corresponding prompts in the results.
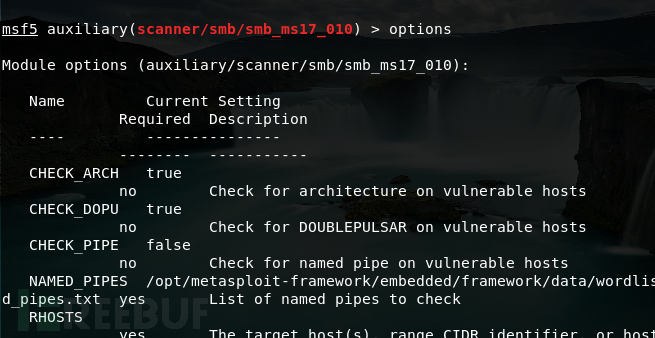
After confirmation, install the corresponding patch for the customer.
Summary
Due to space constraints, the other several will be analyzed in subsequent articles. This article is still aimed at beginners, hoping that friends who are just getting started in emergency response can handle some routine security incidents with this article.
*Author: 3unshine, please indicate the source as FreeBuf.COM when转载.
Follow the Cybersecurity Medicine Water Brother to fight the target field (emergency response)
Emergency response of the Windows system from the perspective of permission maintenance
II. Emergency Response Case (a customer in the education industry of a certain district)
Development of Burp plugin for sensitive information detection based on deepseek local large model
https www.meraevents.com event hacker-hire(MeraEvents Coupons)
评论已关闭