Case Summary
According to the IEEE802.3 protocol, when the broadband network PON system transmits signals, it uses time-division multiplexing technology. Under normal conditions, the ONU should send data packets in the upstream direction according to the specified timestamp. However, when an ONU does not emit light according to the specified timestamp but emits light for a long time or irregularly, it will cause transmission conflicts with the optical signals of other normally emitting ONUs, thereby disrupting the normal reception of the PON port of the OLT device. This results in a Layer 2 (Data Link Layer) DOS attack on the OLT device, leading to a large number of users being disconnected or experiencing network outages under the entire PON port. The ONU that does not send light signals according to the allocated timestamp is俗称为rogue ONU.
Case background
A large number of users hanging under slot 2 port 2 of an OLT went offline, and the ONU was frequently on and off as viewed on the network management side. And through the command line, a large number of error codes were found on the PON port, indicating that it may be poor optical path quality or the presence of a rogue cat under the PON.
Case study
First, the DOS attack behavior and principle analysis of rogue ONUs:

1/As shown in the following figure, first view and analyze the key points of the problem network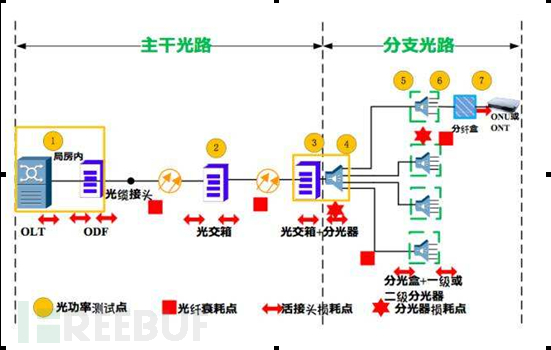 When transmitting data, the PON access network adopts TDM and TDMA technology. In normal conditions, the ONU should send data packets to the upstream direction according to the specified timestamp. As shown in the following figure:
When transmitting data, the PON access network adopts TDM and TDMA technology. In normal conditions, the ONU should send data packets to the upstream direction according to the specified timestamp. As shown in the following figure: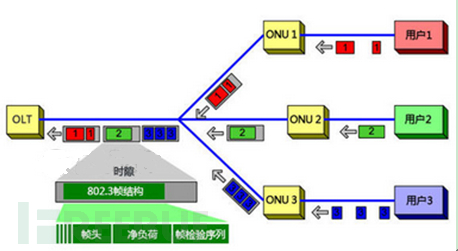
But when an ONU does not emit light at the specified timestamp, but emits light for a long time or irregularly, it will conflict with the light signals of other normally emitting ONUs. This ONU that does not send light signals according to the allocated timestamp is called a rogue ONU, forming a second-layer DOS attack on the OLT device, causing some users under this device to be unable to access the internet normally. Common types of rogue optical modems: long-time emitting rogue optical modems, irregularly emitting rogue optical modems (such as: low version mutual exclusion, anonymous, self-loop, MAC address drift, etc.). The DOS attack example of long-time emitting rogue optical modems is as follows: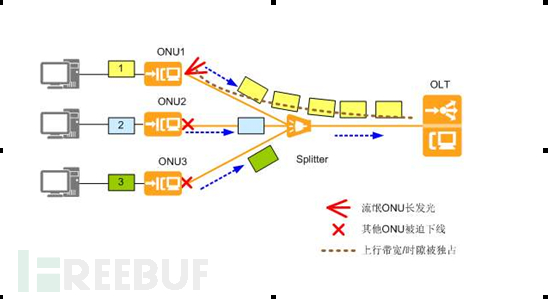 The network phenomena affected by DOS attacks are as follows table:
The network phenomena affected by DOS attacks are as follows table: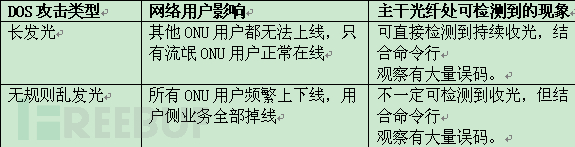 The cause analysis is as follows table
The cause analysis is as follows table Firstly, judge the cause of the fault according to the fault phenomenon. There are many fault phenomena caused by rogue ONU DOS attacks, which may be reflected as device out-of-control, frequent on-off, and fiber break alarm on the network management side, and as service interruption, momentary disconnection and recovery, slow internet speed on the user side. When judging the cause of the fault, if there are a large number of “fiber break alarms” on the network management side, and a large number of CRC error codes are viewed through the command line, it indicates that there may be optical path or rogue ONU problems. Further checking the optical path is normal, then it can be basically determined that there is a rogue ONU.
Firstly, judge the cause of the fault according to the fault phenomenon. There are many fault phenomena caused by rogue ONU DOS attacks, which may be reflected as device out-of-control, frequent on-off, and fiber break alarm on the network management side, and as service interruption, momentary disconnection and recovery, slow internet speed on the user side. When judging the cause of the fault, if there are a large number of “fiber break alarms” on the network management side, and a large number of CRC error codes are viewed through the command line, it indicates that there may be optical path or rogue ONU problems. Further checking the optical path is normal, then it can be basically determined that there is a rogue ONU.
Second, troubleshooting and location of rogue ONUs:
Locating rogue ONUs among a large number of ONU. The general location determination methods are as follows:
1.PON ONU can be basically located through the Debug command;
2.Turn off the upstream time slot channel of the ONU;
3.Turn off the ONU laser;
4.Field fiber pulling
There are two points to note:
1/Due to the possibility of a large number of ONU, it is generally adopted to investigate in batches;
2/Be careful to prevent the situation where multiple rogue ONUs exist in the network at the same time, leading to incomplete investigation.
The summary of the rogue ONU processing flowchart is as follows: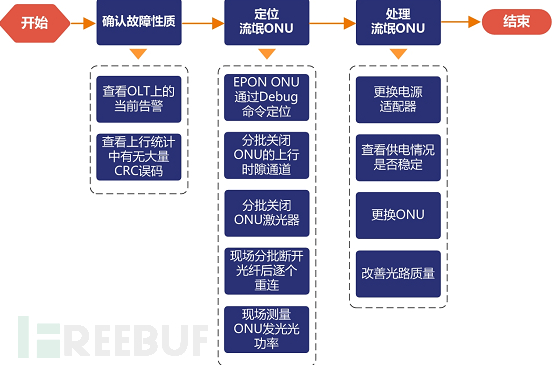 The specific steps to determine the problem are as follows:
The specific steps to determine the problem are as follows:
Step 1
Check the alarms on the OLT to confirm the nature of the fault.
From the network management menu bar, select “Alarm”→“Current Alarm” to view the characteristics of the alarm and judge whether it is a rogue ONU issue.
Step 2
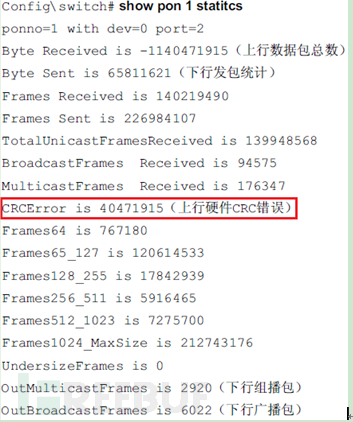
Log in to the service盘, and further view the upstream statistics count of PON through the command line to check if there are a large number of CRC error codes. If so, it can be judged that there are optical path problems or rogue ONU in the network.
Taking the GPON service盘 as an example, when there are a large number of CRC error codes, as shown below:
 Step 3:
Step 3:
1) Directly open the malicious cat detection function on the OLT to quickly locate and solve the long emission phenomenon. The processing flow is shown in the figure below: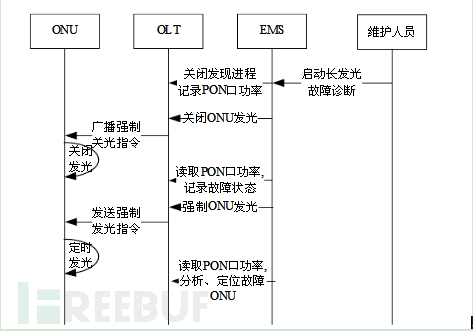 2) Irregular emission phenomenon requires on-site disconnection of optical fibers (also applicable to long emission phenomenon) to locate the malicious ONU. It is recommended to operate at the optical junction box, which can facilitate operation and quickly accurately locate the location of the malicious ONU, reducing the time for traveling between various ONU deployment points.
2) Irregular emission phenomenon requires on-site disconnection of optical fibers (also applicable to long emission phenomenon) to locate the malicious ONU. It is recommended to operate at the optical junction box, which can facilitate operation and quickly accurately locate the location of the malicious ONU, reducing the time for traveling between various ONU deployment points.
If there are not many ONU on the site, you can pull them all out and plug them in one by one to observe;
If there are many ONU on the site, you can pull out the optical fibers of half of the ONU, observe whether the malicious ONU is among them. After repeating several times, you can locate the malicious ONU.
Step 4:
Determine whether there is a malicious ONU in the system by measuring the sending light power of the ONU.
1. Set the light power meter parameters, unit: dBm, wavelength: 1310nm;
2. Pull out the ONU's PON port optical fiber, use optical fiber jumper to connect the ONU's PON port and light power meter;
3. Continuously measure and read data for two minutes;
4. Judge whether it is a malicious ONU according to the measurement data.
If the light power meter never has readings, then this ONU is not a malicious ONU;
If the light power meter always has readings, then this ONU is a long emission malicious ONU;
If there are readings on the light power meter from time to time, but not always, then this ONU is an irregular emission malicious ONU.
III. Solutions for solving malicious ONU:
Step 1: Check whether the ONU power adapter is suitable for the ONU. An unsuitable power adapter may cause the ONU to malfunction and needs to be replaced with a power adapter matching the model of the ONU.
Step 2: Check whether the power supply is stable. Unstable environmental voltage may cause the ONU to emit light uncontrollably, and it is necessary to ensure that the power situation of the ONU's environment is good.
Step 3: Replace the ONU and check whether the fault has been eliminated.
ONU may have software or hardware anomalies, causing unstable emission, which requires replacement.
Step 4: Improve the light path quality and check whether the fault has been eliminated.
Poor light path quality may cause a large number of reflections and abnormal light power loss, etc., which need to be investigated and replaced one by one and optical fibers or ODN components.
Case Summary
In the operation and maintenance of broadband Internet, there is often a difficult phenomenon of DoS attacks on PON device ports by malicious cat ONU, which causes other users to be unable to access the Internet normally and greatly reduces the normal perception of users' Internet access. The network experts see frequent on and off-line of user ONU on the network management side, and through command line, there are a large number of CRC errors on the PON port, predicting that it may be due to poor light path quality or DoS attacks by malicious cats on the PON port. After excluding the normal light path, it is necessary to quickly locate the location of the malicious ONU, which is conducive to the rapid handling of DoS attack events.
Network operators should reasonably plan and allocate the ODN network to improve the quality of light paths; standardize the use of ONU power adapters, and at the same time, establish an emergency response plan for quickly locating and dealing with malicious ONU network security incidents.
评论已关闭