
In this article, we will discuss the vulnerability CXVE-2021-45462, as well as the security risks that the vulnerability brings to dedicated 5G networks, including the analysis of related DoS attack risks.
Background Information
5G technology unlocks many application scenarios that traditional wireless connections cannot achieve, not only helping a wide range of enterprises accelerate their digital transformation and reduce operating costs, but also maximizing productivity to achieve maximum return on investment. To achieve this goal, 5G relies on several key service types to realize its functions: massive machine type communication (mMTC), enhanced mobile broadband (eMBB), and ultra-reliable low-latency communication (uRLLC).
With the continuous development of 5G technology and the continuous expansion of commercial spectrum, the usage rate and popularity of 5G private networks are also increasing. Manufacturing, defense, ports, energy, logistics, and mining industries are among the earliest users of 5G private networks, especially those enterprises that rely on IoT Internet of Things to achieve the digitalization of production systems and supply chains. Unlike the public power grid, the cell infrastructure equipment in private 5G may be owned and operated by the user enterprise itself, system integrator, or operator. However, the increasing research and exploration on the development of various technologies using 5G has also led to network threat actors seeking to develop attack techniques targeting 5G communication and infrastructure.
5G topology
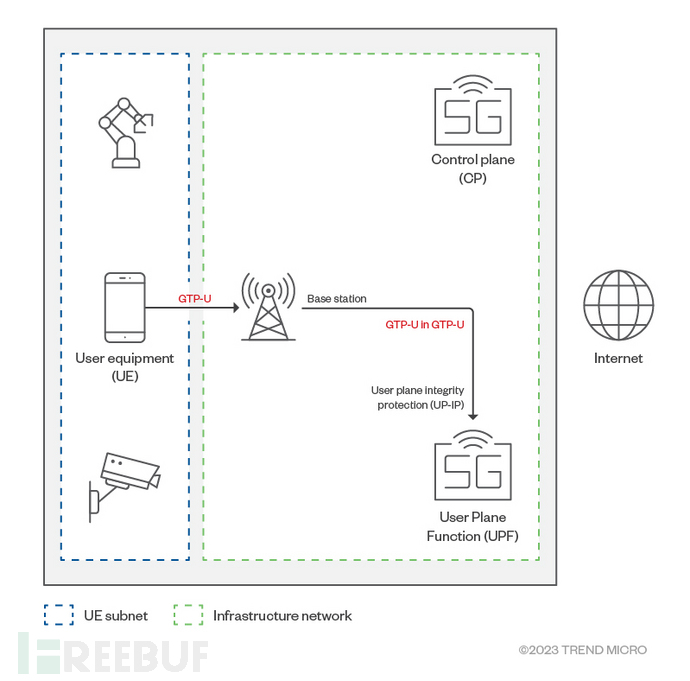
In the end-to-end 5G cellular system, user devices (also known as UE, such as mobile phones or IoT devices) can connect to the base station via radio waves. Then, the base station will connect to the 5G core network through a wired IP network.
Functionally, the 5G core can be divided into two parts, namely the control plane (Control Plane) and the user plane (User Plane). In the network, the control plane is responsible for carrying signals and forwarding data traffic from one endpoint to another based on the signals. At the same time, the user plane is responsible for connecting and processing user data from the wireless access network (RAN).
The base station is responsible for sending control signals related to device connection and establishing a connection with the control plane through NGAP (Next Generation Application Protocol). User traffic from the device is then sent to the user plane using GTP-U (GPRS Tunneling Protocol User Plane), and the data traffic will be routed from the user plane to the external network.
The following figure shows the basic architecture of the 5G network infrastructure:
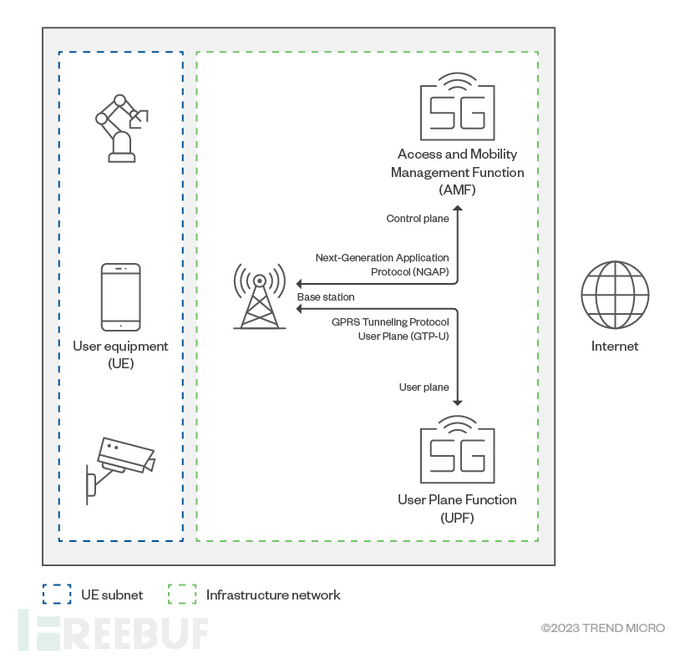
The UE subnet and the basic network are independent and isolated from each other, and user devices are not allowed to access infrastructure components. This isolation mechanism can protect the 5G core from CT (Cellular Technology) protocol attacks generated by user devices.
But can this isolation mechanism really protect the security code of the 5G core? Let's analyze together how network threat actors use components of the 5G infrastructure to carry out attacks.
GTP-U
GTP-U is a tunneling protocol existing between base stations and 5G user planes, which uses port 2152. Below is the structure of the user data packet encapsulated by GTP-U:
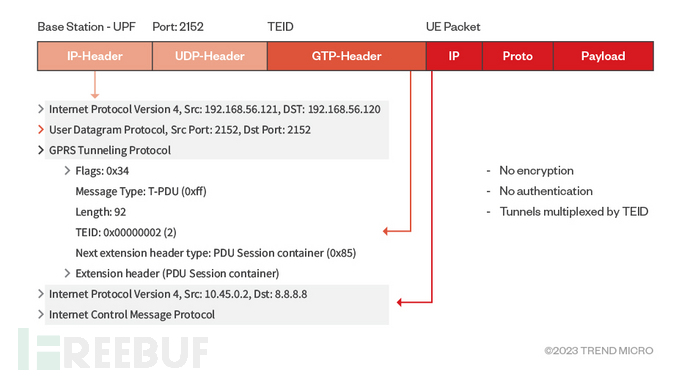
A GTP-U tunnel data packet can be created by attaching a Header to the original data packet, and the added Header consists of a UDP transmission Header and a GTP-U Header. Among them, the GTP-U Header is composed of the following fields:
1. Flags: containing version and other information;
2. Message Type: for GTP-U messages carrying user data, the message type is 0xFF;
3. Length: the length of all content after the Tunnel Endpoint Identifier (TEID) field, in bytes;
4. TEID: the unique value of the tunnel, which can map the tunnel to the user device;
The GTP-U Header is added by the GTP-U node, and users cannot view the Header content on the device's user interface, therefore, they cannot directly operate on the Header fields.
Although GTP-U is a standard tunneling technology, its usage scenarios are mainly between base stations and UPFs, or between UPFs in the CT environment. Assuming the signal tunnel between the base station and UPF is encrypted, protected by a firewall, and access from outside is prohibited.
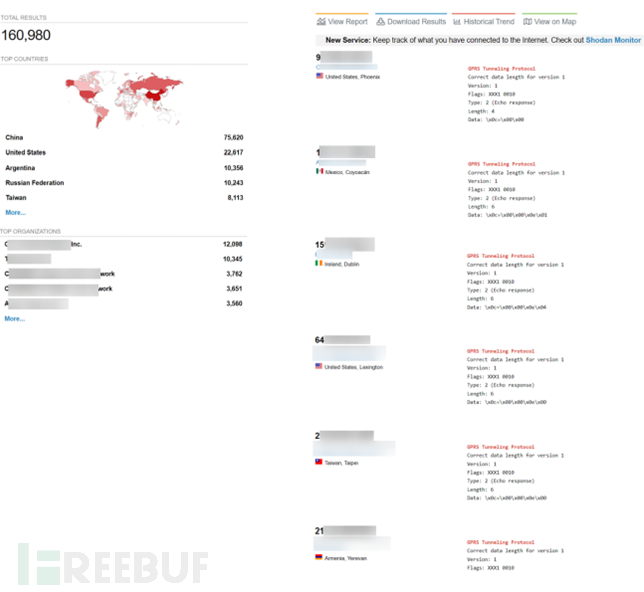
Ideally, GSMA recommends using IPsec for communication between the base station and the UPF. At this time, data packets going to the GTP-U node will only come from authorized devices. If these devices can follow the specifications, they will not send abnormal data packets. However, it is still necessary to analyze the specific situation. Generally, operators are not willing to deploy IPsec on the N3 interface because it is a CPU-intensive solution that will reduce the throughput of user traffic. In addition, since user data is usually considered to be protected at the application layer (using TLS or other additional protocols such as transport layer security), some researchers may consider IPsec security to be redundant. Moreover, some people may also think that all powerful systems need robustness checks to detect any obvious anomalies. However, according to our research, many N3 nodes (such as UPF) that should not be exposed to the Internet worldwide are exposed to the Internet.
The following diagram shows the UPF interface statistics exposed due to configuration errors or the lack of a firewall (from Shodan):
GTP-U node: base station and UPF
The GTP-U node is the endpoint for encapsulating and decrypting GTP-U packets, and the base station is the GTP-U node on the user device side. When the base station receives user data from the UE, it will convert the data into an IP packet and encapsulate it into a GTP-U tunnel.
The UPF is a GTP-U node on the 5G core network (5GC) side. When the UPF receives GTP-U messages from the base station, it will decrypt the outer GTP-U header and extract the inner message. Then, the UPF will look up the target IP address in the routing table (also maintained by the UPF), at this time, the content of the internal packet will not be checked, and then continue to send the packet.
GTP-U in GTP-U attack
What will happen if the user device creates an abnormal GTP-U data packet as shown and sends it to the packet core?
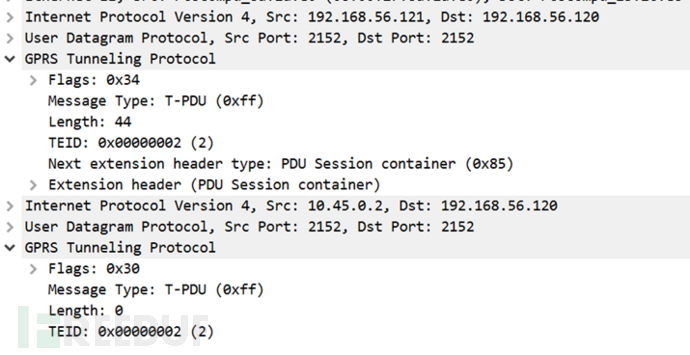
The following diagram shows the process flow of sending an abnormal GTP-U data packet from the user device:
As expected, the base station will transmit this data packet within its GTP-U tunnel and send it to the UPF, resulting in the GTP-U packet reaching the UPF. Currently, there are two GTP-U packets in the UPF: the external GTP-U packet header is created by the base station to encapsulate data packets from user devices. The message type of the external GTP-U packet is 0xFF, with a length of 44, which is a normal header. The other internal GTP-U header is created by the user device and sent as a packet. Like the external GTP-U, the internal GTP-U message type is also 0xFF, but the length is 0, which is not right.
At this time, the source IP address of the internal packet belongs to the user device, and the source IP address of the external packet belongs to the base station. The internal and external packets have the same target IP address, that is, the target IP address of UPF.
UPF decrypts the external GTP-U and passes the function check, and the destination of the internal GTP-U data packet is again the same UPF. What will happen next is:
1. Implementing a state machine that continuously traverses packets, and if the implementation of the state machine encounters an error, it may cause it to process this internal GTP-U data packet. This packet may have passed the inspection stage because it shares the same packet context with external packets. Ultimately, it will lead to abnormal packets inside the system, which cannot pass the security robustness check.
2. Since the destination of the internal packet is the IP address of UPF itself, the packet may be sent to UPF. In this case, the packet may encounter a function check.
Attack Vector
Some 5G core network suppliers may choose to use Open5GS code, such as NextEPC (a 4G system renamed to Open5GS in 2019 to add 5G features) has enterprise products for LTE/5G based on the code of Open5GS. However, researchers have not observed any in-the-wild attacks or threat signs, but our tests show that there are potential risks associated with the use of this technology.
The most critical part of security testing is the attack vector, that is, the cellular infrastructure attack from the UE. The security issues described in this article, network threat actors only need to use a phone (or a computer connected via a cellular adapter) and a few lines of Python code to abuse this vulnerability and initiate such attacks. GTP-U in GTP-U attack is a well-known technique, and backhaul IP security and encryption cannot prevent this type of attack. In fact, these security measures may even hinder firewalls from performing security checks on packet content.
Mitigation Solution & Summary
The medical and utility industries are just one of the early adopters of private 5G systems, and the breadth and depth of its popularity is expected to grow further. The continuous and reliable operation of the system is crucial for these industries, as it may concern life and real-world impacts. Therefore, the 5G system must provide reliable connections, as any successful attack on 5G infrastructure could lead to the paralysis of the entire network.
The vulnerability scenario (CVE-2021-45462) introduced in this article, once successfully exploited by an attacker, may lead to a DoS attack. The root cause of CVE-2021-45462 (and most GTP-U-in-GTP-U attacks) is the improper error checking and handling in the packet core. Although GTP-U-in-GTP-U itself is harmless, manufacturers must make appropriate repairs to mitigate the threat risk.
In addition, GTP-U-in-GTP-U attacks can also be used to leak sensitive information, such as the IP addresses of infrastructure nodes. Therefore, GTP-U peer nodes should handle GTP-U-in-GTP-U packets securely and appropriately. In the CT environment, they should use intrusion prevention systems (IPS) or firewalls that can understand the CT protocol. Since GTP-U is not normal user traffic, especially in 5G dedicated networks, security teams can even prioritize and discard GTP-U-in-GTP-U traffic.
Generally, the registration and use of SIM cards must be strictly regulated and managed. An attacker with a stolen SIM card can insert it into the attacker's device to connect to the network, which also brings more arduous tasks for security operations.
References
https://www.trendmicro.com/en_gb/ciso/22/i/pros-cons-5g.html
https://www.gsma.com/security/wp-content/uploads/2020/02/FS.31-v2.0.pdf
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-45462
https://www.gsma.com/membership/wp-content/uploads/2017/09/Positive-Technologies-White-Paper.pdf
https://www.trendmicro.com/en_gb/business/products/iot/mobile-network-security.html
Reference Source
https://www.trendmicro.com/en_gb/research/23/i/attacks-on-5g-infrastructure-from-users-devices.html
Indirect attack methods in LLM attacks and defense methods against LLM attacks
Example of Spring MVC HttpURLConnection Vulnerability
3. Multi-party Security Computation - MPC (Secure Multi-Party Computation)
Attack methods and defense strategies of bucket attacks in corporate cloud security
Full analysis of Android security strengthening technology (Part 2)
评论已关闭