Who does the data belong to?
We all say that in the era of informatization, data is wealth, data is assets, this metaphor is very good, indicating more is the importance of data. However, compared with money, data has more particular characteristics. For individuals, the money in the wallet, the balance in the bank account, belongs to themselves, others can't see or touch it, let alone use it arbitrarily.
However, this guy, data, does not have exclusivity. You say who it belongs to, and it is difficult to define. For example, when I bought a piece of clothing on Taobao, a piece of order data was generated, which contains a wealth of data, such as your name, home address, phone number, product content. So many data, you say, does it belong to this Taobao platform, or to you personally? Subjectively, consumers naturally believe that data is their own privacy, belonging to themselves, but the problem is that the data is generated by the Taobao platform, and at the same time, merchants need to use it, and logistics couriers also need to see it, and the community express delivery station also needs to review it. You say it belongs to you, but you have no control over it.

Taobao order data
Looking at it this way, data is said to be wealth. At a superficial level, it is not the wealth of individuals at all; it can be Taobao's wealth, because this data helps Taobao better understand your interests and hobbies; it may be the wealth of a logistics company, because it helps the logistics company know you, and when the logistics company wants to do local life business or other new local delivery business, it can conveniently send you marketing messages; it may be the wealth of a community kiosk, through which the kiosk knows all the contact information of the owners, and when other owners of the community ask the kiosk where they can rent a parking space, it can also directly serve as an information relay station.
Who is most capable of protecting data has the responsibility to protect data security
Data, in terms of reasonableness, belongs to individuals, and in terms of protection responsibility, belongs to institutions or enterprises, which is also the target of various national laws and regulations (Data Security Law, Cybersecurity Law, Personal Information Protection Law).
Personal data not only exists in public applications or platforms, but also within enterprises, various employees may come into contact with and process these data. In addition to establishing strict operational specifications and procedures, enterprises also spare no effort in adopting various technical means to protect the security of personal privacy data. What is worth mentioning here is the endless variety of so-called data non-landing technical solutions.
The general meaning of data non-landing is that (the enterprise) allows you (employees) to use the data, but you (employees) cannot take away these data. The mindset of enterprises and employees is like a tug-of-war during the Spring Festival.
Definition and goal of data non-landing
In a broad sense, any persistent data with a fixed carrier that does not disappear instantly is considered as landed data, such as data stored on hard drives. Correspondingly, data stored in memory or transmitted over the network, which disappears after use, is not landed data. In an enterprise, any data that employees can edit and process without downloading to local devices can be understood as non-landed data.
Data not landing on the ground solution - cloud desktop
This is not an educational article. Readers who can be patient and read to this point should not need to普及 the definition of cloud desktops anymore. There are many similar names, and there are differences in product differences, but the essence is the same, such as DaaS (Desktop As A Service), VDI, virtual desktop, remote desktop. Using internal systems in an independent Windows desktop environment, processing documents, writing source code, and ensuring that data cannot leave this desktop environment through measures such as blocking USB and network communication.
Summarize several keywords according to the overall characteristics, comprehensive, expensive, slow, heavy.
Security effect | Comprehensive, can manage client software and Web applications, can write documents, and can write source code |
|---|---|
Internal network system | Manageable |
External network system | Can't control |
Price | Expensive, software needs to be authorized and fees, and a lot of servers need to be prepared |
Performance | Slow, always slower than local computers, and domestic virtualization protocols are relatively backward compared to foreign ones |
Implementation and operation and maintenance | Heavy, server management, network configuration, thin client management, daily operations and maintenance |
Applicable population | Rich, general government, general finance, automotive, education, where security is more important than efficiency |
Data not landing on the ground - sandbox (Sandbox)
This is a localization solution with Chinese characteristics for the zero-trust security concept in China. Early sandboxes referred to lightweight virtual machines running in the operating system, where software runs without affecting the outer layer operating system. It can even be compared to the cloud desktop above, where the inner logic is consistent, and it is also to establish an isolated environment for processing data, just that one is in the cloud and this one is in the terminal computer, and the implementation technology is also different. Early applications of this technology were in virus analysis, where security personnel put the virus into this sandbox to analyze it to prevent the virus from damaging the outer layer local computer. Now, various security companies, in order to cater to the popularity of data security, have begun to turn their thinking and use this technology in data leakage prevention scenarios.
Sandbox, also known as sandbox, is a network programming virtual machine execution environment, which is a virtual system program. It creates an environment logically isolated from the personal environment on the terminal through driver layer or application layer redirection technology, and controls all system operations of the software (application) running in the sandbox, and can implement communication encryption, file encryption on the ground, isolation of internal and external network access, clipboard control, external device control, program control, and file external control and other data protection functions. This article directly quotes the following article, which analyzes the sandbox from a technical perspective and is very comprehensive.
https://www.freebuf.com/articles/endpoint/355519.html
Security effect | Comprehensive, can manage client software and Web applications, can write documents, and can write source code |
|---|---|
Internal network system | Manageable |
External network system | Can't control |
Price | Moderate |
Performance | Excellent local experience |
Implementation and operation and maintenance | Heavy, requires network configuration, terminal compatibility issues are numerous, software adaptation issues are numerous, and high computer configuration requirements |
Applicable population | Game industry source code protection, material protection |
Transparent encryption and decryption for data not landing
Transparent encryption and decryption refers to the process in which encrypted software automatically encrypts the data to be stored at the moment and automatically decrypts it when used, in order to prevent the possibility of data leakage when used abnormally. Corresponding security products include those for databases and terminal files. The common ones are for terminal files. Dynamic encryption and decryption at the database level are generally not used. Any unstable factors may cause business paralysis and permanent data loss, which is too risky.
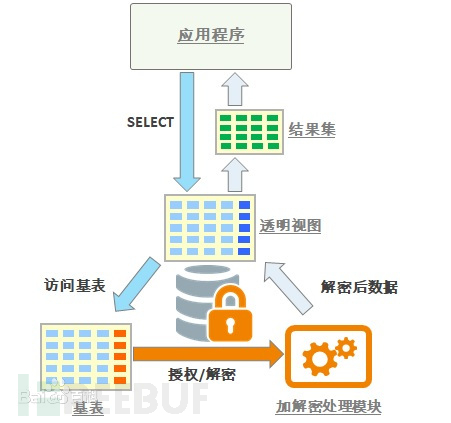 Transparent encryption and decryption of databases
Transparent encryption and decryption of databases
Transparent encryption and decryption effect of terminal files, for example, taking a Word document as an example, it is actually encrypted when stored on the disk. When an employee opens an encrypted document to edit and use it, it will be automatically decrypted in memory, and the employee can use it normally without any impact. However, when trying to send the file through WeChat, QQ, and other channels, the decryption process will not be triggered, and the file sent out is just an encrypted file. Even if the recipient receives it, it has no significance.
Such products have existed for more than 20 years. At present, all traditional security companies are standard products, but the ancestor-level in China is still IP-Guard this one.
Security effect | Not comprehensive, not divided by software type, but can only manage unstructured data |
|---|---|
Internal network system | Manageable |
External network system | Manageable |
Price | Moderate |
Performance | Excellent local experience |
Implementation and operation and maintenance | Moderate |
Applicable population | Manufacturing, drawings, and other unstructured data are the main scene, which is intuitive |
Browser kernel security for data not landing
This is a completely new model, which still relies on the background of cloud computing. Everything is moving to the cloud, and now the main business systems of various enterprises are in the cloud, data is in the cloud, and applications are in the cloud. Enterprise office is also increasingly relying on online office models, such as online document writing, online meetings, and online collaboration. This means that all data is in the cloud. The new office form requires a new security solution, and all data access is gradually narrowed down to the browser. Then, based on the security protection of the browser kernel and the data not landing solution, it is a trial to cater to the times and dare to innovate in security.
There is not much reference material for this, because there is only one company in the market doing this content, and its technical threshold and direction are completely different from the traditional model. It is recommended that everyone pay attention.
Security effect | Not comprehensive, can manage structured and unstructured data, but cannot manage terminal client software systems |
|---|---|
Internal network system | Manageable |
External network system | Manageable |
Price | Moderate |
Performance | Excellent local experience |
Implementation and operation and maintenance | Lightweight, no software adaptation, no terminal adaptation, no software conflict |
Applicable population | All enterprises |
Data not landing
The above-mentioned are all for enterprise office types, employee data operation, non-local solutions, and there is another block for scenarios and solutions where data computation does not land, which refers to scenarios where large amounts of data are computed online or on the server side, such as Homomorphic encryption, multi-party computation, SGX Wait, another chapter will be introduced later.
评论已关闭