Under the concept of 'dynamic data security, full lifecycle management of data', it is necessary to establish protection at all important links of the data lifecycle and form a multi-layer joint protection system.Database encryption is the most core layer in the multi-layer protection systemBased on an active defense mechanism, data encryption storage can effectively prevent internal unauthorized operations such as downloading or copying database files, as well as direct analysis of data files leading to data leakage; it can respond to external hacker attacks on databases, and unauthorized encrypted sensitive information will not be leaked; it can enhance access control to prevent DBAs or high-privileged accounts from obtaining plaintext sensitive data.
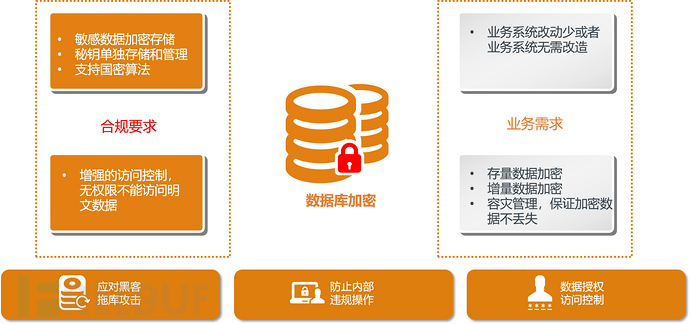
Database encryption must meet both compliance requirements and user business needs.

1
compliance requirements
sensitive data is encrypted and stored
keys are stored and managed separately
supporting national encryption algorithms
enhanced access control, unauthorized access cannot access plaintext data
2
business requirements
business system modifications are minimal or the business system does not require modification
existing data encryption
ensuring that encrypted data is not lost
Theoretically, there can be multiple technical implementation methods for database encryption, and the more widely used method in the industry at present isnative database encryptionandApplication transformation encryption,Ming Dynasty's database encryption supports both of these methods simultaneously.
1
Native database TDE encryption
Using the database's own TDE encryption function, the database maintains transparency to external access after encryption, supporting operations such as queries, inserts, updates, and deletions, as well as features such as SQL statement access, stored procedures, triggers, user-defined functions, primary keys, foreign keys, and various constraints, and supporting ciphertext indexes. Database operation and maintenance tools and general SQL statements, stored procedures, and development interfaces can be accessed transparently without any modifications.
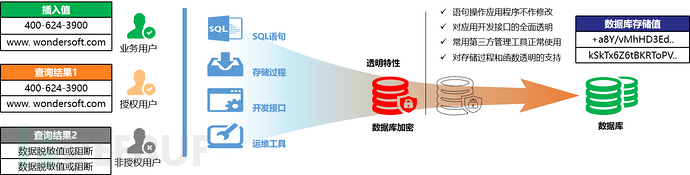
The TDE encryption supported by Ming Dynasty's native database encryption includes the following three encryption methods:
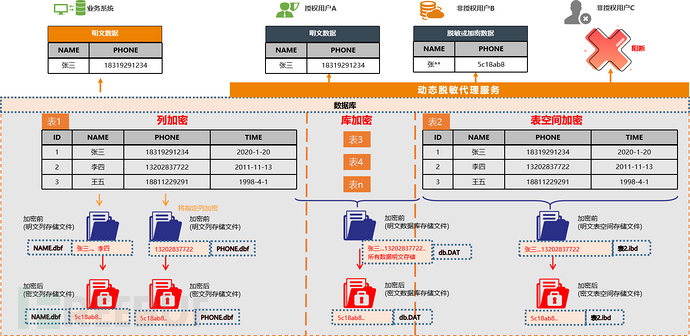
▷Database-level encryption:The entire database is used as a unit of encryption, using a unified encryption algorithm and data encryption key.
▷ Table space-level encryption:Tables can also be used as the unit of encryption, or multiple tables can be merged into a space group as a unit of encryption. Each table (or a table space group) uses a data encryption key and encryption algorithm.
▷ Column-level encryption:Data columns are used as the unit of encryption, and each column has its own data encryption key and encryption algorithm.
One effect of the native TDE encryption of the database is to encrypt the data storage files. Directly viewing the data storage files before encryption can see plaintext information, and sensitive information is easy to leak; after encryption, the data storage files cannot directly see plaintext information. This way, even if the files are leaked, it will not cause the leakage of sensitive data.
The effect of the native TDE encryption of the database is to make the application transparent, that is, the original business system directly accesses the database, and whether it is encrypted or not is imperceptible. Therefore, it is necessary to prevent unauthorized access to sensitive data through enhanced access control mechanisms. Ming Dynasty Wanда database native TDE encryption implements enhanced access control mechanisms through dynamic data masking proxy services.
2
Application transformation encryption
Application transformation encryption requires the transformation of the application system, where the application system independently calls the encryption engine interface to achieve encryption and decryption of data.
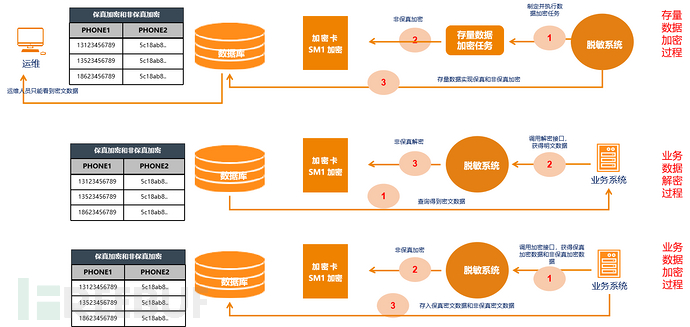 Ming Dynasty Wanда database encryption completes encryption of existing sensitive data in the database through the establishment of data encryption tasks, which is a one-time task.
Ming Dynasty Wanда database encryption completes encryption of existing sensitive data in the database through the establishment of data encryption tasks, which is a one-time task.▷ Data Encryption:The business system first calls the encryption system interface to encrypt plaintext data, and finally stores it in the database by the business system.
▷ Data Decryption:The business system reads ciphertext data from the database, and then calls the encryption system interface to obtain plaintext data.
Ming Dynasty Wanدا database encryption supports fidelity encryption, which allows certain query business of the business system to be unchanged without transformation; it supports integration with third-party encryption cards to implement some hard encryption algorithms, such as SM1 national encryption algorithm, to meet the requirements of encryption evaluation. At the same time, database operation and maintenance personnel directly access the encrypted ciphertext data after encryption, which can achieve the purpose of preventing sensitive data leakage.
Ming Dynasty Wanدا application transformation encryption is open to the public for data encryption and decryption capabilities through the task subscription mode.
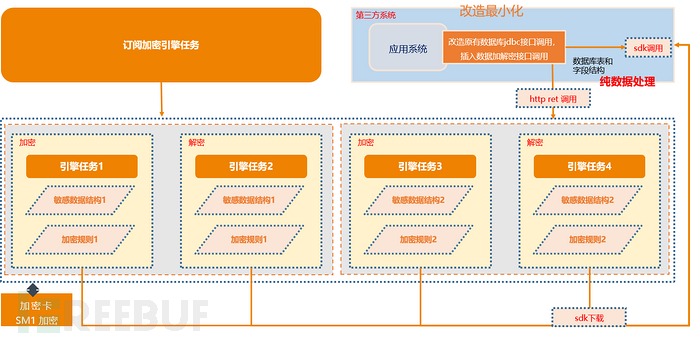
Different engine tasks can be subscribed according to different encryption and decryption needs. Each engine task has an independent http ret call interface and provides a separate SDK package for integration download. The user's business application system can implement simple data encryption and decryption processing by calling the ret interface of the engine task or the integration SDK call interface.
The data structure of the encryption engine interface can be configured to be the same as the database table and field structure of the business system. The business system only needs to insert a call to the encryption engine interface for data encryption and decryption at the place where the database jdbc interface is called, without adjusting the original business logic of the application function, achieving the purpose of minimizing the transformation of the application system.
评论已关闭