I. Database Security Protection Design Reference
CIS Internet Security Center, also known as Center for Internet Security, is most famous for CIS controlsR (CIS Control Items) and CIS BenchmarksTM (CIS Benchmarks), which are globally recognized as the best practices for IT system and data security. At the same time, CIS is mapped to CSF security functions and matches NIST CSF 2.0. Additionally, the internal security management standards of some leading internet companies at the basic level are highly consistent with CIS Controls.
CIS divides control content into 3 implementation groups (Implementation Group, IG) to form a priority classification. Each IG is a CIS control subset, applicable to a category of enterprises with similar resource scale or security risk.

IG1:Applicable to a very limited number of small and medium-sized enterprises in IT and cybersecurity, the protective measures mainly ensure the normal operation of the enterprise's business and prevent downtime. The sensitivity of enterprise data is relatively low, mainly related to employee and financial information. The IG1 protective measures should not rely on professional security knowledge and are mainly aimed at general non-targeted attacks, also suitable for small or home office environments.
IG2 (including IG1):IG2 is generally applicable to enterprises that have dedicated personnel responsible for managing and protecting IT infrastructure. Different departments of the enterprise face different risks based on their functional roles and tasks, and there is a burden of regulatory compliance. IG2 enterprises usually need to store and process sensitive customer or enterprise information, can withstand temporary service interruptions, but if there is a violation, it will bring public relations problems. IG2 protective measures help the security team deal with increasing operational complexity, but some measures depend on enterprise-level technology and the professional skills of experts in specific fields.
IG3 (including IG1 and IG2):IG3 is applicable to enterprises that generally have dedicated cybersecurity experts (including risk management, penetration testing, application security, and other fields). These enterprises' assets and data contain regulated sensitive information or functions, as well as compliance supervision, so it is necessary to solve the protection issues of service availability, sensitive data confidentiality, and integrity. Once the enterprise network is attacked, it may cause significant damage to public welfare. IG3 protective measures must prevent targeted attacks from skilled attackers and reduce the harm and impact of zero-day attacks.
NIST is the abbreviation of National Institute of Standards and Technology, usually called 'United States National Institute of Standards and Technology' in China. It is related to cybersecurity and has two frameworks:
1. Privacy Framework
2. Cybersecurity Framework, abbreviated as CSF
2. Based onCISRisk Assessment of Databases
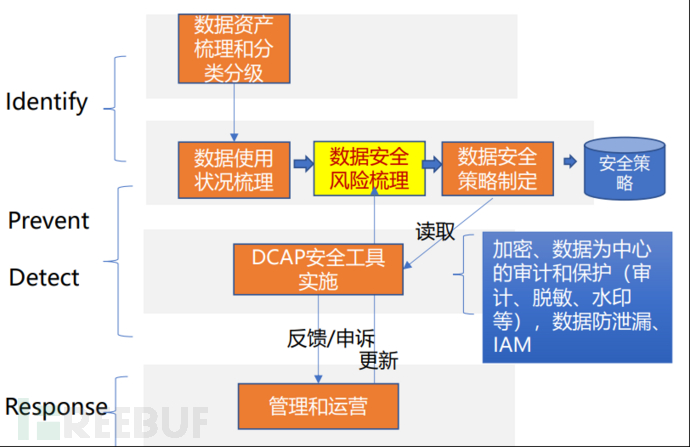
The following internal database of the company is evaluated based on the CIS control items, and finally forms risk items and risk priorities. In the actual risk assessment, it can refer to CIS_RAM_WORKBOOK for execution and calculate the risk score. This article quickly generates risk items through research and interviews to provide input for the solution. It is necessary to pay attention to the latest version of CIS, which has added Govern (governance) to IPDRR (Identify, Protect, Detect, Respond, Recover), highlighting management responsibilities and process design, namely GIPDRR. The author believes it is more comprehensive and applicable.

3. Database Security Solutions
The CAPE framework of a domestic security vendor, similar to CIS/NIST's IPDRR, is a落地 in the database scenario. The CAPE framework mainly tests the technical level, lacking management functions from the enterprise perspective: namely, defining responsibilities and establishing processes. Data security solutions should mainly include: management responsibilities, processes, and technical solutions.
1. Management Responsibilities
The management responsibility of database security is of great importance. It is necessary to identify the database management owner, clarify the security management responsibilities of the owner, and secondly, formulate and form a unified internal database security management strategy and standards, so that there are people to manage and system requirements. Thirdly, establish a database security contact person, also known as the executor. Here, the executor includes not only the operation and maintenance team such as dba but also professional security personnel in information security.
2. Process Construction
Systematize the management system and requirements of database security management, and continuously improve it, that is, complete the process of 'first solidify, then rigidify, and finally optimize'. In the process of involvement and management, cross-departmental collaboration and communication are naturally involved. For companies with high internal communication costs and departmental walls, promoting database security management through processes may be a method that achieves twice the result with half the effort. The specific processes involved in database security are referred to as follows:
- Database asset accounting and registration
- Database data classification and grading
- Database account management process
3. Technical Solutions
The technical solution mainly involves dimensions such as access control, account management, vulnerability management, data security management, and audit traceability. For the security technical solutions of databases, many have matured, and the key point lies in implementation. However, due to the core position of databases in business, many intrusive database security protection solutions are difficult to implement. Database security audit systems have almost become the standard for database security, which also verifies the embarrassment of the difficulty in implementing intrusive solutions. Another aspect is to combine the actual risk status of databases, that is, based on the risk assessment mentioned above, to determine the priority of technical solutions.
This article introduces the dimensions of data identification, classification and grading, data encryption, and data desensitization from the perspective of data security.
3.1 Classification and Grading
Now many enterprises are engaged in data classification and grading. The author believes that classification and grading is not the ultimate goal of information security. The ultimate goal is to achieve the protection of key data with limited security resources through the tasks and projects of data classification and grading. There are many solutions for data classification and grading products now, claiming to improve the accuracy of classification and grading by utilizing the capabilities of large models. Some of them are worth taking, such as using large models to identify and classify standardized data, such as internal human resource data, customer, supplier, and personal information, etc. The protection of personal privacy data and data cross-border scenarios are also the focus of enterprise data security, which is also the entry point for many enterprises to do data classification and grading. From another perspective, the data needed for large model training is still required by many enterprises to be deployed privately, and they will not share their data with large model manufacturers to avoid the risk of data leakage. Many enterprises still do not have data classification and grading standards, and the business has no perception of it. The data security responsibilities of the owner have not been assigned yet, and the business has not finally confirmed the data classification and grading. How can we talk about the accuracy of data classification and grading?
3.2 Data encryption
The main driving force for database encryption comes from regulatory compliance requirements, but involving key management, performance, and stability impact, the actual implementation still faces great challenges.
Indicator | Application plugin solution | Encryption machine external solution | Database built-in solution |
Implementation cost | The implementation workload is small, without the need to modify the application code. | The implementation workload is large, requiring modification of the application code and integration of the encryption machine client SDK. | The implementation workload is small, some databases have the built-in TDE function, which is usually called tablespace encryption or transparent encryption. |
Reliability | High reliability, the plugin becomes part of the application, without running a separate process, the reliability of the plugin depends on the reliability of the application itself. | Medium reliability, data needs to be transmitted to a centrally deployed encryption machine for encryption and decryption, forming a performance bottleneck and single point of failure risk. | High reliability, with the database's built-in security capabilities. |
Performance | High performance, based on high-performance national encryption algorithms and desensitization algorithms. | Medium performance, data needs to be transmitted to and from the encryption machine, which increases network latency. | High performance, with fewer encryption algorithms supporting the SM series. Oracle: According to different versions, AES128 and AES192 are supported by default, supporting HSM hardware encryption machines and Oracle Key Vault software form. MySQL InnoDB supports TDE and supports AES encryption algorithm, for details, please refer to: MS SQL SERVER supports AES128 and AES256 as optional, for other more key information and encryption and decryption function calls, please refer to: |
Compatibility | Supports the majority of databases, decoupled from the database. | Supports the majority of databases, depending on the type of SDK programming language. | Supports only some databases such as Oracle, Oracle, MS SQL SERVER, etc. |
Data flow | Without changing the original data flow path and network topology, data and desensitized data can be encrypted and decrypted on the spot without module modification. | Changing the data flow path, plaintext is first transmitted to the encryption machine through the SDK, and after encryption, the ciphertext is returned to the SDK and finally stored in the database. | Encryption and decryption are completed internally within the database without changing the data flow path. |
Expandability | It can be flexibly expanded, with unified visual strategy management, covering more applications horizontally without affecting the encryption and decryption performance of deployed applications. | The expansion cost is high, and the encryption strategy needs to be implemented through hard-coded, which is not flexible and has high risk. | There are differences in the expansion costs among various versions of the database. |
Impact of application upgrade | The encryption and decryption functions do not affect the application upgrade and are loosely coupled with the application. | The application upgrade requires maintenance of encrypted code, with encryption and decryption tightly coupled with the application code. | The application upgrade needs to evaluate the database, which may affect the performance resources of the database server, and the impact may exist depending on the backup method. |
3.3. Data Masking
The data masking here refers to dynamic masking, which is generally divided into two implementations in technology, and pseudo-masking implemented by the front-end through JavaScript scripts is not included here.
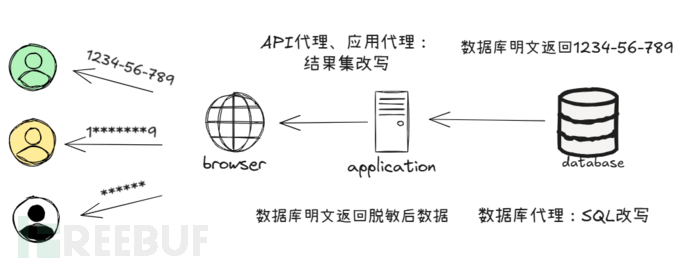
Firstly, based on SQL rewriting
Advantages:
1. Early Filtering: Desensitization at an early stage of data access can reduce unnecessary data transmission and improve efficiency.
Disadvantages:
1. High Complexity: SQL rewriting requires parsing and modifying complex SQL statements, which is relatively difficult to implement.
2. Performance Impact: SQL rewriting may increase the parsing and execution time of the database, leading to a decrease in performance.
3. Compatibility Issues: SQL syntax may vary between different database systems, and adaptation is required for different systems.
mysql> SELECT id, mask_ssn(CONVERT(ssn USING binary)) AS masked_ssn
mysql> FROM customer
mysql> WHERE first_name = 'Joanna' AND last_name = 'Bond';
+-----+-------------+
| id | masked_ssn |
+-----+-------------+
| 786 | XXX-XX-0007 |
+-----+-------------+
Secondly, based on the rewriting of the returned result set
Advantages:
1. Simple Implementation: Compared to SQL rewriting, result set rewriting is relatively simple and does not require parsing complex SQL statements.
2. Easy Maintenance: The impact on existing SQL queries is small, making it easy to maintain and upgrade.
3. Flexibility: The returned result set can be processed flexibly at the application layer to meet different business needs.
Disadvantages:
1. Performance Impact: Since desensitization is performed after data query, it may increase the response time.
2. Resource Consumption: Processing the returned result set will increase the load on the application server, especially in cases of large data volumes.
Reference Content
https://github.com/bytebase/bytebase
https://dev.mysql.com/doc/refman/5.7/en/innodb-data-encryption.html
评论已关闭