The Windows registry contains binary blocks (Blobs), some of which are used to store certificates, as shown below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates
HKEY_CURRENT_USER\SOFTWARE\Microsoft\SystemCertificates
Certificate through DERFormat is encoded, always starting with 0x30. However, it can be found that the binary block found in the registry does not start with 0x30, because the certificate prefix stores some metadata. Search for 0x30 to find the location of the certificate: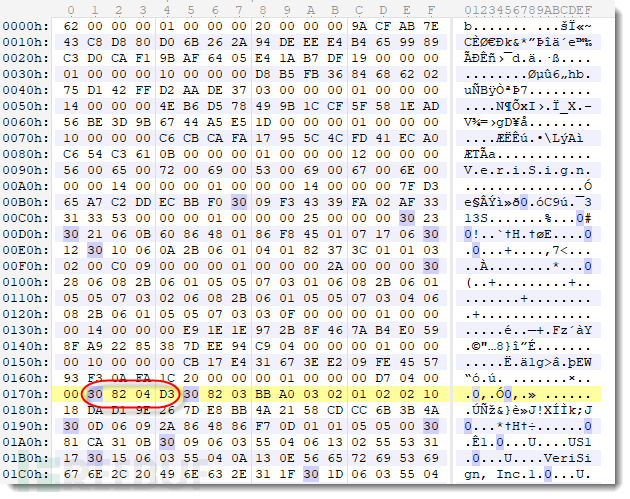
Not all byte sequences starting with 0x30 are valid certificates. Search from 0x30 8 and extract the byte sequence until the end of the binary block to find the certificate.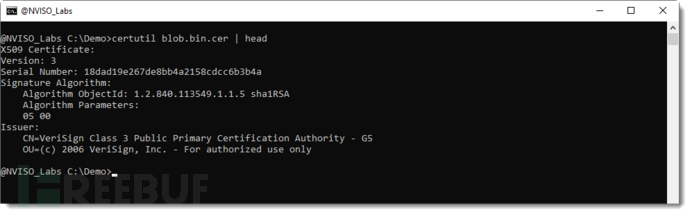
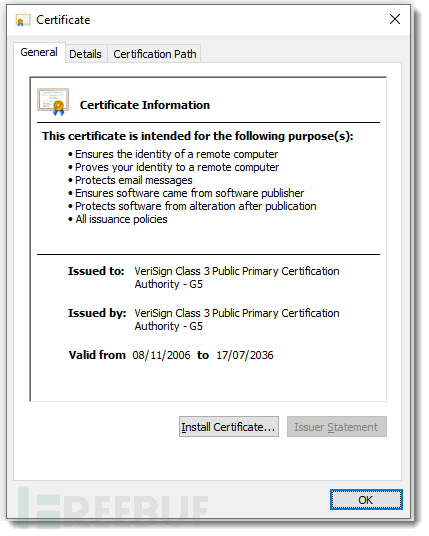
This method is not accurate, and it can be found by viewing several binary blocks: each certificate starts with a 4-byte prefix, which encodes the length of the certificate (in little-endian order), and then this length field is preceded by an unchanging 8-byte prefix: 20 00 00 00 01 00 00 00.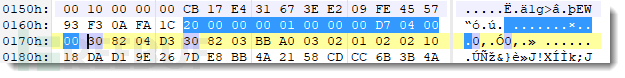
appears to be TLVformat, each certificate's type is 20 00 00 00 01 00 00 00. The tool format-bytes.pyis a tool for parsing binary data, which can be used to parse TLV records, as follows: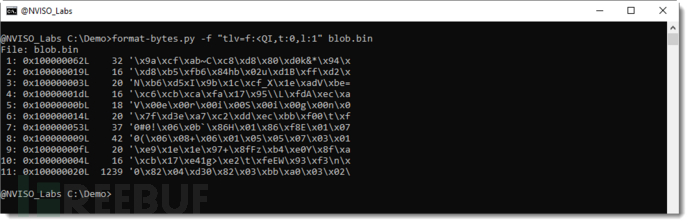
<QIin <Represents little-endian order,QRepresents unsigned long long (8 bytes),IRepresents unsigned int (4 bytes).t:0This means that the type field is the first field.l:1This means that the length field is the second field.
It can be seen that this binary block contains 11 TLV records, the last one has a length of 1239 and contains the certificate type 0x100000020L.
Further researchIndicatesThe type field is actually composed of two fields: the attribute identifier field and the reserved field, both of which are four bytes. Possible values for the attribute identifier can be found in Windows Developer Centerand found in the wincrypt.h header file.
This means that the TLV records within the binary block can be format-bytes.py -f "tlv=f:<III,t:0,l:2" blob.binPerform analysis: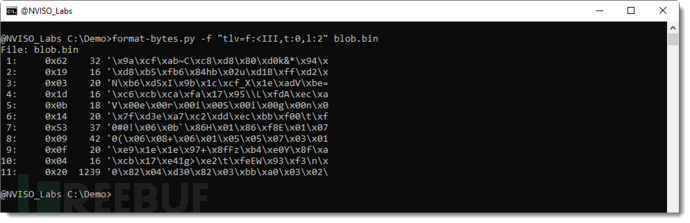
For example, the type of record 5 is 0x0b, representing CERT_FRIENDLY_NAME_PROP_ID: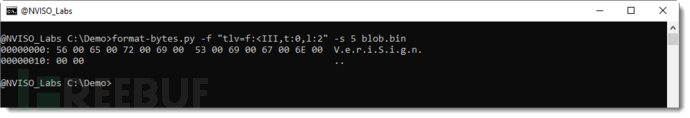
As shown in the figure above, it includes the issuer name encoded in UTF16. As shown below, the certificate itself is located within record 11 (type 0x20):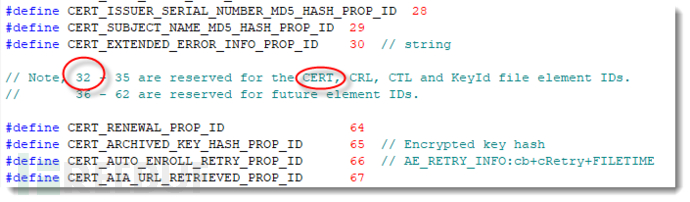
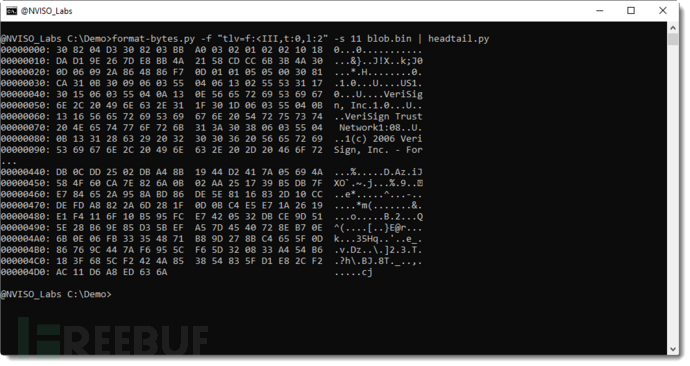
To extract the certificate, please use -dExecute binary dump and write to a local file: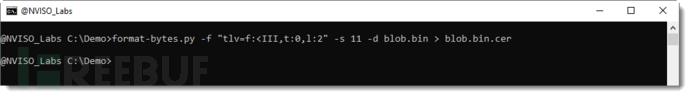
Conclusion
TLV records often appear in binary data blocks. If you want to identify data in binary blocks, comparing several examples may help you find the defined pattern. Certificates and metadata are stored together in the registry, and the metadata structure is the TrLV record. The certificate itself is stored inside the record, with a type of 0x20.
Reference Source
评论已关闭