0X00 Preface
Attackers are increasingly using attack techniques targeted at cloud applications and identities. This article is an introduction summarizing the events in which attackers target enterprises without needing to contact the terminal or traditional network systems and services. This article will discuss the current attack techniques in detail, providing technical support for the construction of enterprise SOC security.
0X01 The popularity of cloud and SaaS applications
The SaaS revolution and product-driven growth have had a huge impact on the network structure of companies and the location of core business systems and data. Today, many organizations use dozens to hundreds of SaaS applications in their business functions. Some are completely native to SaaS and have no traditional network to speak of; but most adopt a hybrid model, which combines local, cloud, and SaaS services to form the pillars of the business applications in use.

Most SaaS is controlled by users rather than centrally managed by IT, with an inherent characteristic of bottom-up growth driven by product orientation. The latest data from Push Security shows that only one-fifth of SaaS applications have been approved by the business. Most SaaS applications are unknown and have never been reviewed. Cloud and SaaS applications are designed to interconnect, functioning like closed networks of internal business applications used in the past. The core of this interconnection is identity, with the most basic form being the user account created during the registration service, which includes a username/email and password. To reduce the risk of account takeover and the complexity of managing an increasing number of accounts, enterprises are using the services of identity providers (IdPs), utilizing protocols such as Single Sign-On (SSO) and OAuth to manage authentication and authorization separately, concentrating access within applications to a single platform and identity.
The composition of an identity can vary greatly. Depending on the application, the same account may have multiple authentication mechanisms (e.g., through SAML, social login (OIDC), and username and password). Although SAML requires administrators to set up the corresponding account for the SaaS program in advance, users can simply register for the application by using the third-party login feature. In fact, this creates multiple identities bound to a single account, which may introduce many confusions and complexities (e.g., merely deleting the account by the IdP administrator does not mean that the application/account cannot be accessed through one of the other created login methods). This may make it difficult to understand which applications are in use and what identities exist in the organization. Therefore, in practice, the following combinations may occur:
Identity providers (on average, about 3 per organization) (e.g., Okta, Entra/Microsoft, Google)
Applications that act as connectors to SSO platforms for connecting applications (e.g., Atlassian Access, Adobe Creative Cloud)
SaaS applications using different authentication (SAML, OIDC) and authorization (OAuth) protocols
SaaS applications with local usernames and passwords
Credentials and secrets stored in password managers and validator applications (which can be in browsers, local operating systems, and third-party applications)
This may become quite complex - most organizations have more than 100 applications in their inventory, leading to tens of thousands of identity extensions. Then, based on the OAuth scope approved for a given application, the permissions and workflows of one application may affect other applications because they are approved to communicate with each other.
Identity is the glue that holds this ecosystem together. However, the control over protecting identity has serious limitations. Companies typically believe that all applications and identities have deployed MFA, or that all applications are behind SSO. But the fact is, only 1/3 of the applications actually support SSO (many only at the advanced level, with a significant increase in price). In addition, about 60% of unique identities (i.e., not using SSO) are not registered with MFA. Therefore, there are significant gaps in the security controls for protecting cloud identities, while identity and cloud applications are becoming more and more prevalent.
0X02 Attackers are targeting cloud identity vulnerabilities for intrusion
Attackers are closely monitoring potential intrusion points in cloud identity vulnerabilities. According to Verizon's 2024 DBIR report, 74% of all incidents involved human factors, targeting threatened user accounts through human error, permission abuse, use of leaked credentials, or social engineering. Although this is not a new development (since 2013, some descriptions of identity/phishing attacks have been a major attack vector), Crowdstrike's latest global threat report further indicates that 75% of access acquisition attacks are malware-free, and 'cloud-aware' attacks (intentional rather than opportunistic attacks on cloud services to disrupt specific functions) have increased by 110%. Microsoft also points out that there are approximately 4,000 password attacks against cloud identity per second, while advice from Google employees suggests that attacks seeking to steal session cookies (thus bypassing multi-factor authentication) are as frequent as password-based attacks.
From the public perspective, evidence of violations tells the same story. Threat organizations such as APT29/Cozy Bear/The Dukes and Scattered Spider/0ktapus have shown how attackers actively target IdP services, SaaS applications, and SSO/OAuth for high-profile attacks against companies like Microsoft and Okta.
Cloud applications and identity have become new opportunities for attackers. Due to the shift to cloud services, the value they provide is equivalent to that of traditional attacks through endpoint intrusion into network boundaries. In many ways, identity itself is a new attack surface. Unlike other security boundaries such as networks or endpoints, in terms of existing control measures, it presents much smaller obstacles in defending this new boundary. Attacks based on identity were previously often limited to endpoints or adjacent 'identity systems' such as active directories. The attacker's goal is to break through this boundary and move within the organization. Now, identity is more dispersed, making it an entry point to an interconnected ecosystem of cloud applications and services accessible via the internet. This significantly changes the level of challenge faced by security teams. After all, preventing credential stuffing attacks against 100 SaaS applications is much more difficult than preventing the past single, centralized external VPN/network email endpoint.
0X03 Cloud identity is becoming a new security boundary
Corporate operations personnel are very clear that cloud identity is the new digital boundary. This is not a prediction of the future, but a threat that is facing us now. What is not yet certain is what offensive technologies and skills will emerge, and what the industry will do to prevent them.
| Security route | Attack techniques | Security plan |
|---|---|---|
| The years 2000-2010 were traditional peripheral hacker attacks | Port scanner, vulnerability scanner, buffer overflow attack, Web application attack, WiFi attack, client/server backdoor | 防火墙、DMZ、安全编码、WPA、渗透测试 |
| 2010年后是端点成为新的边界 | 水坑攻击、Office宏钓鱼、浏览器漏洞、内存驻留植入、C2 框架 | 端点强化、EDR、 SIEMS、红队、威胁追踪 |
| 2020年后是云身份是新的边界 | ??? | ??? |
2023年Push Security在 GitHub上发布了一系列SaaS攻击技术(受到更注重端点的 MITRE ATT&CK 框架的启发),展示了攻击者如何在不接触网络或端点等传统表面的情况下瞄准企业。这些技术综合运用,就可使得攻击者能够在云环境中完成端到端的攻击。Push还发布了许多博客文章,介绍如何使用这些技术最流行的技术总结如下:
| 技术 | 概述 |
|---|---|
| AiTM 网络钓鱼 | AiTM网络钓鱼使用专用工具作为受害者与受害者有权访问的应用程序的合法登录门户之间的Web代理,主要是为了更容易地破坏MFA保护。通过实时代理到目标登录门户,攻击者可以访问有效密码和有效会话cookie,他们可以窃取并用于劫持会话。登录后,受害者用户将看到他们通常希望看到的所有真实数据(例如他们自己的电子邮件/文件 等),因为它是真实应用程序的代理。这减少了他们意识到由于代理应用程序的真实工作性质而受到损害的机会。 |
| 企业通讯软件网络钓鱼 | Teams和Slack等IM应用程序是攻击者规避针对恶意链接和附件更严格的基于电子邮件的网络钓鱼防护的好方法。 IM 的即时性和实时性使其成为网络钓鱼攻击的有用载体,因为用户不太熟悉这些应用程序作为网络钓鱼攻击的传递载体。使用 IM,可以欺骗/冒充用户、使用机器人帐户创建可信的对话、滥用链接预览功能以及追溯编辑消息和帐户以清除攻击者的踪迹。 |
| SAML 劫持 | SAML劫持是攻击者利用他们控制的SaaS租户的SAML SSO配置设置,以便在身份验证过程中将用户重定向到他们选择的恶意链接。这对于网络钓鱼非常有效,因为原始URL将是合法的SaaS URL,并且用户希望提供凭据。如果SaaS应用程序的管理员帐户受到威 胁,它还可以用于横向移动,方法是修改或启用SAML,将URL指向看起来像或代理合法身份验证服务(例如 Google 或 Microsoft)的凭证网络钓鱼页面。然后,攻击者可以通过向租户发送看似合法的应用程序登录页面链接来瞄准用户,然后以水坑攻击的方式发挥作用。 |
| Okta hijacking | Attackers can set up their own Okta tenant for highly trusted phishing attacks. This attack is effective because Okta forwards the login credentials of accounts associated with AD to their own AD proxy running on the target network. Then, Okta allows the proxy to report whether the login was successful. This enables attackers who can disrupt the AD proxy or simulate an AD proxy to monitor Okta users' login credentials and provide a universal key-like function to authenticate to Okta in any user identity they prefer. It can also be used for lateral movement similar to SAML hijacking - just without the need to redirect to a separate malicious domain. |
| Shadow workflows | Shadow workflows are a technology that uses SaaS automation applications to provide methods similar to code execution, used to execute malicious operations from legitimate sources through OAuth integration. This can be anything from exporting files from shared cloud drives every day, automatically forwarding and deleting emails, cloning instant messages, exporting user directories - basically any operation that can be implemented using the target application API. |
0X04 Threats of network attack techniques
Luke Jennings used a video (Video link) vividly demonstrated the actual operation of a series of network attack techniques, including: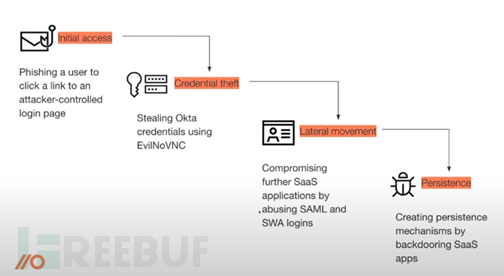
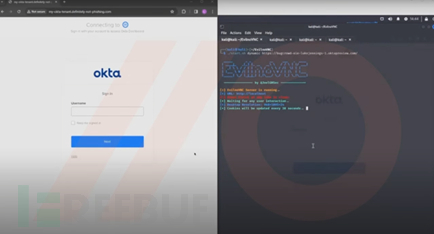
Gaining initial access rights: Luke utilized an attack tool named EvilNoVNC, which is a browser-based browser (BitB) phishing framework, to hijack the user's Okta session in this way;
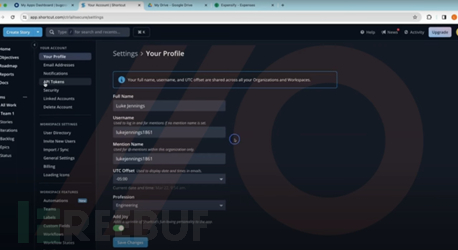
Stealing credentials from browser sessions: Luke successfully stole user credentials from browser sessions and accessed more applications through Okta SSO. Then, he configured these applications to create persistent access permissions and backdoors;
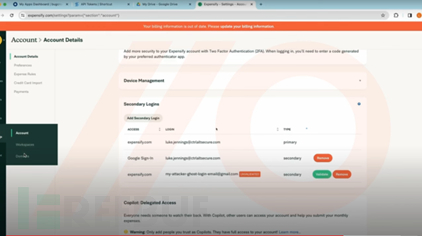
Further credential theft: Luke exploited the abuse of SAML and SWA login to steal credentials from other users of the applications within the company tenant, and successfully accessed sensitive data of the compromised applications.
0X05 How to detect and respond to this type of attack?
These types of attacks now pose a real challenge to many organizations, as they bypass the gaps in existing security tools and services. How can we detect and respond to such attacks?
Can you detect the initial AiTM phishing attack?
How many users will be threatened in SAMLjacking attacks?
Can you find all the different backdoors in multiple SaaS applications? Or just reset the Okta account password and MFA token? What about the passwords for all non-SAML applications?
Most organizations have security gaps when dealing with identity-based attacks. This is largely because, the controls around identity security are usually focused on protecting the central identity system (such as Active Directory/Entra ID), rather than the larger identity infrastructure related to cloud applications and services. Similarly, the investments in controls by organizations are largely bypassed by these attacks. EDR tools used to protect the underlying operating system have little impact here because these applications are accessed through browsers - which are increasingly hailed as the new operating system. As mentioned in this article, protecting identity is absolutely crucial for protecting cloud services. And a significant part of the attack chain - such as, the usual phishing attempts, including AiTM and BitB technologies aimed at bypassing MFA, or password sharing across applications and services, cannot be covered by endpoint security tools, IdP logs, or SaaS logs from individual applications and services.
0X06 Tourist Reviews
As a security professional, identity security is undoubtedly an important part of the information security field, especially in today's digital world, the management and protection of digital identity are becoming increasingly important. Observing and analyzing identity security from the perspective of attack surface management will provide enterprises with a new dimension to understand and respond to identity security issues. It should be noted that identity security is a broad concept that governs the permissions of individuals to access corporate resources. Personal identity security, on the other hand, focuses more on the protection of individuals' sensitive information. Both are committed to reducing the risks of identity theft and information leakage, but their focus is different.
From the perspective of attack surface management, when considering identity security, we need to focus on how to minimize the potential attack surface and prevent attackers from obtaining illegal access rights through identity fraud. This includes: comprehensive password policies, multi-factor authentication, etc., to ensure the accuracy of user identity; access control should be based on the principle of least privilege, that is, users can only access the resources required to perform their work and cannot access other information, etc., to ensure corporate information security.
Reference links:
https://github.com/pushsecurity/saas-attacks#the-saas-attacks-matrix
https://www.huntandhackett.com/blog/hunting-for-a-sliver
https://www.mcafee.com/blogs/
评论已关闭