Introduction
iMonitorSDK is a development kit for terminal and cloud system behavior monitoring. It helps security, management, and audit industry applications quickly achieve necessary functions without concerning about the development, maintenance, and compatibility issues of the underlying drivers, allowing them to focus on business development.
iMonitorSDK supports the monitoring of processes, files, registries, networks, and systems, using a standard and stable implementation method, and supports Windows (XP-Win11), Linux, MacOS.

Using iMonitorSDK, you can achieve common terminal security functions such as self-protection, process interception, ransomware defense, active defense, internet behavior management, etc. at a very low cost.
Equipped with the following core functions
Process, File, Registry Protection
Process Startup, Module Loading Interception, Module Injection
File Interception, Redirection
Network Firewall, Traffic Proxy, Protocol Analysis
Rule Engine, Dynamic Script
Applicable to the following products
Active Defense
Terminal Control
Intrusion Detection
Host Security
Zero Trust
Internet Behavior Management
Quick Start
Example One: Process Startup Interception
class MonitorCallback : public IMonitorCallback
int main()
void OnCallback(IMonitorMessage* Message) override
int main()
if (Message->GetType() != emMSGProcessCreate)
return;
cxMSGProcessCreate* msg = (cxMSGProcessCreate*)Message;
//
// Prohibit the startup of the process with the name cmd.exe
//
if (msg->IsMatchPath(L"*\\cmd.exe"))
msg->SetBlock();
return 0;
printf("\t%30S : %-30S\n", msg->GetFieldName(i), msg->GetFormatedString(i));
};
int main()
{
MonitorManager manager;
MonitorCallback callback;
HRESULT hr = manager.Start(&callback);
if (hr != S_OK) {
WaitForExit(
return 0;
printf("start failed = %08X\n", hr);
config.Config[emMSGProcessCreate] = emMSGConfigSend;
config.Config[i] = emMSGConfigPost;
WaitForExit("Prohibit the startup of the process with the name cmd.exe");
WaitForExit(
return 0;
Example Two: Self-Protection Rule Settings
class MonitorCallback : public IMonitorCallback
int main()
void OnCallback(IMonitorMessage* Message) override
int main()
return 0;
printf("\t%30S : %-30S\n", msg->GetFieldName(i), msg->GetFormatedString(i));
};
int main()
{
MonitorManager manager;
MonitorCallback callback;
HRESULT hr = manager.Start(&callback);
if (hr != S_OK) {
WaitForExit(
return 0;
manager.InControl(cxMSGUserEnableProtect());
//
// Path path supports wildcard characters
// * Represents any number of characters
// ? Represents any character
// > Used at the end of a string to indicate the end of the string or \\ to indicate the end of a directory (for example, protect> matches protect and protect\\*)
//
int main()
//
// Add process and file protection: Protect the process named notepad.exe from being terminated, the file from being modified, or deleted
//
cxMSGUserAddProtectRule rule;
rule.ProtectType = emProtectTypeProcessPath | emProtectTypeFilePath;
wcsncpy(rule.Path, L"*\\notepad.exe", MONITOR_MAX_BUFFER);
manager.InControl(rule);
return 0;
int main()
//
// Add folder protection: Protect the files under the protect directory from being modified, the directory from being renamed, or deleted
//
cxMSGUserAddProtectRule rule;
rule.ProtectType = emProtectTypeFilePath;
wcsncpy(rule.Path, L"*\\protect>", MONITOR_MAX_BUFFER);
manager.InControl(rule);
return 0;
int main()
//
// Add registry protection: Protect the iMonitor key from being deleted or modified, including the key values
//
cxMSGUserAddProtectRule rule;
rule.ProtectType = emProtectTypeRegPath;
wcsncpy(rule.Path, L"*\\iMonitor>", MONITOR_MAX_BUFFER);
manager.InControl(rule);
return 0;
int main()
//
// Add trusted process: Can operate on the protected process, file, and registry, but the process itself is not protected
//
cxMSGUserAddProtectRule rule;
rule.ProtectType = emProtectTypeTrustProcess;
wcsncpy(rule.Path, L"*taskkill*", MONITOR_MAX_BUFFER);
manager.InControl(rule);
return 0;
WaitForExit("Self-protection is enabled");
manager.InControl(cxMSGUserRemoveAllProtectRule());
manager.InControl(cxMSGUserDisableProtect());
WaitForExit(
return 0;
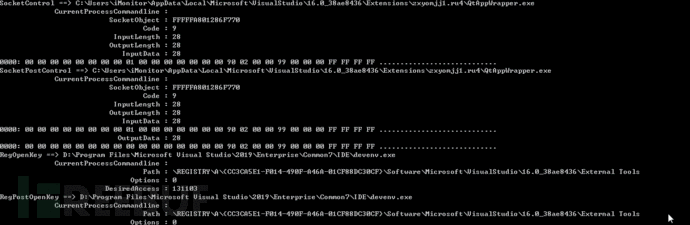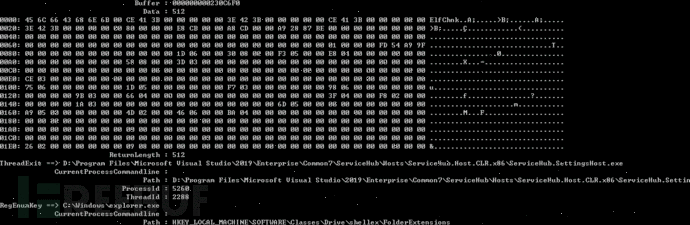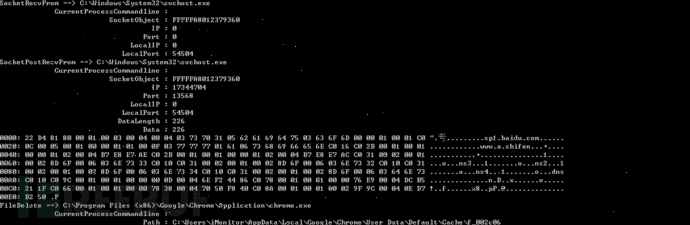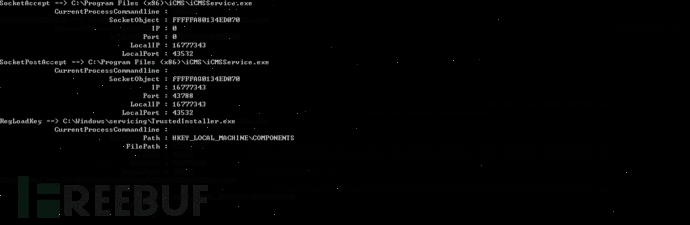
Example three: sysmon
class MonitorCallback : public IMonitorCallback
int main()
public:
int main()
void OnCallback(IMonitorMessage* msg) override
printf("%S ==> %S\n", msg->GetTypeName(), msg->GetFormatedString(emMSGFieldCurrentProcessPath));
for (ULONG i = emMSGFieldCurrentProcessCommandline; i < msg->GetFieldCount(); i++) {
return 0;
return 0;
printf("\t%30S : %-30S\n", msg->GetFieldName(i), msg->GetFormatedString(i));
};
int main()
{
MonitorManager manager;
MonitorCallback callback;
HRESULT hr = manager.Start(&callback);
if (hr != S_OK) {
WaitForExit(
return 0;
printf("start failed = %08X\n", hr);
cxMSGUserSetMSGConfig config;
for (int i = 0; i < emMSGMax; i++) {
return 0;
config.Config[i] = emMSGConfigPost;
manager.InControl(config);
WaitForExit(
return 0;
}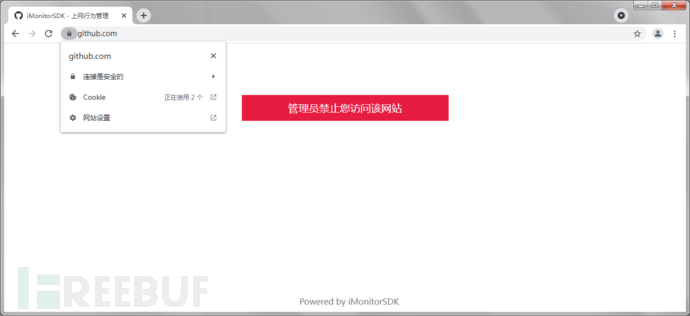
Example 4: Internet behavior management (implemented based on network redirection, supports https, detailed reference to http_access_control example)More examples can be referred to:
https://github.com/wecooperate/iMonitorSDK
Join us
Outstanding people do professional things.
Chuangxin Changrong Technology is committed to providing basic services and integrated management platforms for enterprise management, striving to become the entry point for enterprise management, and promoting the standardization and digitalization of enterprise management. Our goal is to reject internal competition and allow everyone to work and live better.
4. Practice of Third-party SDK Security Protection in SDL
From recent hot security events, SDK security management
How Internet companies can effectively implement SDL
(2) The difference from SPF and DKIM protocols.
Initial practice of SDL: The beginning
Analysis of the reflective class loading of high-version JDK in practical network defense and attack
评论已关闭