On June 9th,Security engineer Tian YeminginFreeBuf Party A Community Fifth Internal Live Broadcastand served as a guest speaker,Share data leakage investigation
Data is an intangible asset for enterprises, and once data is leaked, it will cause immeasurable losses. Possible causes of data leakage include identity fraud, unauthorized operation, illegal operation, accidental operation, configuration failure, uncontrollable infrastructure, social engineering phishing, and security vulnerabilities.
How do enterprises monitor and know about data leakage incidents? Tian Yeming introduces,Enterprises usually have three ways to know about data leakage: external intelligence, internal monitoring, and supervisory notifications
External intelligence is generally throughThreat intelligence provided by security vendors, white hats, or the discovery of enterprise data being sold on the dark web. Tian Yeming reminds that data leakage intelligence obtained from external sources needs to be confirmed by business parties and DBAs for the authenticity of the sample data, and then investigate the possible channels of leakage based on the characteristics of the sample data; if enterprise data is found on the dark web, it needs to be carefully checked to see whether it is sensitive data and the timeliness of the data.
Internal monitoring is through paying attention towhether the user interface has been excessively traversed abnormally, and whether there are abnormal external behavior of usersandFraud customer complaints. Enterprises need to formulate different investigation plans according to different channels and scenarios of leakage.
In addition, enterprises also need to pay attention toSupervisory notifications from direct supervisory agenciesAccording to the content of the supervisory department's notification, sort out the possible channels of leakage and carry out rectification.
4W1H investigation approach
If an unfortunate data leakage incident occurs, the enterprise or data subject needs to investigate in a timely manner and initiate an emergency response.
4W1H refers to what, why, when, who, and how.What represents what data has been leaked, the specific feature format, and the approximate scale of the leaked data. Why represents why these data were leaked and the possible channels of leakage. When represents the time of data leakage. Who represents which individuals have the authority to access the leaked data. How is to roughly confirm the possible channels of leakage, narrow down the investigation scope, and formulate an investigation plan to start the specific investigation.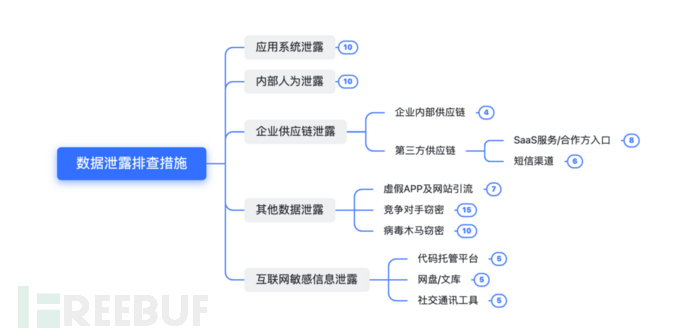
post-event review
Tian Yeming also mentioned thatIt is necessary to carry out post-event review in time after a data leakage event occursEvent review, analysis of reasons, fault summary, improvement plan, and event closure are the five phases
When reviewing the event, it should be reconstructed in the form of a timeline, the problems encountered in the event investigation process should be proposed, and it should be judged whether the handling results have reached the expected level.
In the analysis of reasons phase, it is necessary to analyze whether the pre-event execution is sufficient, whether the process is standardized, whether the strategy is comprehensive; it is also necessary to analyze whether the monitoring mechanism during the event is established, whether it is covered, whether the rules are updated in time, whether alarms are configured, whether there is human negligence, and whether the cause of the event is not located in time.
In the fault summary phase, attention should be paid to the exposure of problems and responsibility identification. Sort out which work-related problems were exposed by the data leakage event, clarify the rights and responsibilities of the parties involved in the event, and facilitate follow-up improvement in the future.
In the improvement plan phase, an implementable improvement plan is formulated based on the problems found during the review.
In the event closure phase, the relevant person in charge follows up on the improvement plan formulated and makes regular progress reports. At the same time, the projects involved in the improvement plan are archived for easy review or audit in the future.
How to classify data leakage events
In the interactive Q&A session, an audience mentioned how to classify data leakage events. Tian Yeming said that the classification of data leakage events is roughly the same as the classification of traditional enterprise information security events, which is divided intoEspecially major events, major events, relatively major events, and general eventsThe indicators of the rating include data sensitivity level, impact on business degree, and influence on the company's reputation; it is also necessary to consider the special nature of the industry in which the company is located, the regulatory requirements of the industry, and other factors for comprehensive rating.
There are also audience questions:How to promote the cooperation of downstream data leakage investigationTian Yeming replied that when enterprises purchase external services, they need to impose pre-event, in-event, and post-event constraints on the service provider in the procurement contract. For example, when data leakage occurs, the service provider needs to provide remote assistance or on-site investigation within 24 hours. After the event, the service provider is required to make timely improvements.
Finally, Tian Yeming also drew a number of interactive audiences with the host to send out exquisite gifts.
Join the FreeBuf first-party community
The exciting review of this live broadcast is over. In addition, FreeBuf will regularly hold different first-party community live broadcasts. If you want to learn more about topics and views, come and scan the QR code for free to apply to join the FreeBuf first-party group!
Join to get the FreeBuf monthly album for free, and there are more exciting contents in the exclusive community for FreeBuf first-party members. The assistant sends welfare every week, and there are surprises every week in the community. Why not act quickly?
Application process: scan to apply - background review (2-5 working days) - email notification - join the member club
If you have any doubts, you can also scan the QR code to add the assistant's WeChat!

Application process: scan to apply - background review (2-5 working days) - email notification - join the member club
If you have any doubts, you can also scan the QR code to add the assistant's WeChat!
评论已关闭