1. Overview
With the development of Internet applications, anonymous communication technology plays a very important role in protecting privacy. The purpose of anonymous communication is to hide the confidential information of each end user, including identity and content, and to avoid being tracked and discovered by third parties. However, for anonymous communication systems, anonymity and communication efficiency have always been a trade-off. Generally, the better the anonymity of the system, the worse the communication efficiency. This is because the enhancement of anonymity is usually accompanied by the complexity of the communication process, which will also lead to a decrease in communication efficiency. Therefore, different anonymous communication technologies need to be matched for different business scenarios to achieve a balance between anonymity and communication efficiency.
Anonymous networks are currently mainly used by network security law enforcement departments for confidential work. They ensure the security of communication transmission through anonymous networks, hide their real network address and physical address during the execution of tasks, and prevent the possibility of information leakage through technical means.

The Adaptive Internet Security Access System is a complete solution for the hidden network, which is a composite network hidden channel solution. It completes the protection of hidden channel communication through technologies such as multi-level encryption and channel noise. It realizes the security protection of nodes through behavior-based intrusion detection technology. Once an abnormal behavior occurs, the self-destruct device of the node will immediately start to prevent the attacker from tracing the source of the system. The system can hide the real IP in the network and simulate unknown networks, ensuring the safety of personnel and equipment accessing the system through dedicated access gateways, privacy operating systems, and multiple personal authentication. It can provide a stable and reliable data transmission channel and can achieve concealed file transmission.
2. Solution
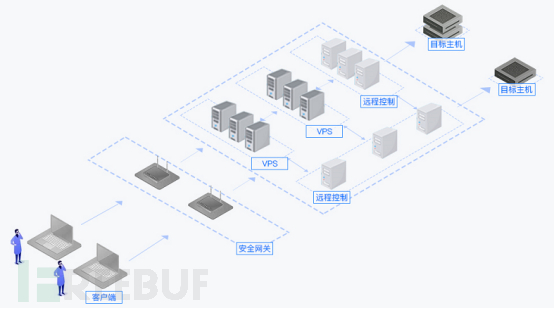
In general, regular business traffic will pass through several routers to reach the access target. In a sense, routers are also stepping stones, but when routers forward data, they will not discard the source IP address of the internet user, thus lacking the attribute of anti-tracing. The core principle of the system is also to forward network traffic through multiple-level stepping stones, but the multi-level stepping stones of the system are based on multi-level stepping stones at the host and application layers, which do not carry the source address when forwarding data. Therefore, the more forwarding levels, the lower the probability of being traced, thus protecting the identity security of business users. In addition, each node in the system uses encrypted data transmission to ensure that any stepping stone node that is compromised and intercepted cannot easily obtain real traffic information.
The system is mainly composed of two parts: the secure gateway and the hidden network.
The secure gateway is a bridge between the client and the hidden network, and the client needs to connect to the hidden network through the secure gateway. The secure gateway mainly has the following functions:
The hidden network access function allows business personnel to access the hidden network through the secure gateway, access the target through the encrypted transmission of the hidden network, and thus achieve the purpose of hiding the identity of the business personnel when accessing the target machine.
The hidden network path selection function is achieved by the secure gateway through network probing of VPS and remote control nodes within the hidden network, intelligently calculating all possible paths to the target and the priority levels of the paths based on the probing results. According to the priority levels of the paths, the communication link of the hidden network is selected.
The hidden network is responsible for encrypting and transmitting information, and at the same time, it performs traffic obfuscation during the transmission process. The main functions of the hidden network include the following points:
Data encryption and decryption functions, each node within the hidden network must perform data encryption and decryption operations to ensure that there is no plaintext data transmission throughout the entire communication link.
The private proxy protocol is used for communication between the secure gateway and the hidden network, as well as between nodes within the hidden network. It can proxy TCP, UDP, and ICMP protocol data.
With traffic obfuscation functionality, false traffic can be added to the encrypted business traffic to confuse the business traffic, thereby improving the self-deception of the traffic.
Identity authentication function, the security gateway must pass the identity authentication of the hidden network before it can access the hidden network, ensuring that unauthorized devices cannot access the hidden network.
3. Function Introduction
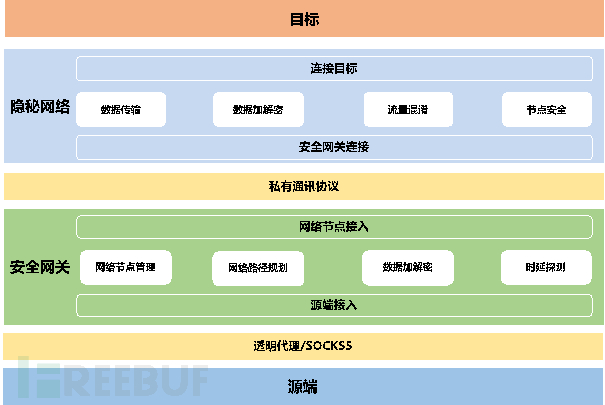
(1) Security Gateway
The security gateway is the intermediate bridge connecting the source end and the hidden network, with functions such as source end access, network node management, network path selection, data encryption and decryption, link latency detection, and hidden network access.
(2) Hidden Network
The hidden network, as an intermediate layer between the source end and the target, is composed of multiple anonymous nodes and has functions such as security gateway access, data transmission, data encryption and decryption, traffic obfuscation, and node security.
Introduction to Security Gateway Functions
According to business needs, the security gateway selects multiple network nodes to form a link channel. The main functions of the security gateway are as follows:
(1) Node Management
The security gateway system manages the node information and link information used by the devices; node information includes node IP, port, region, etc. Link information includes nodes on the link, node status, and link latency.
(2) Network Path Selection
The security gateway supports the selection of node regions and the number of nodes. According to business needs, the number of nodes and regions for building the hidden network link can be selected, with the minimum number of nodes being 4 and the maximum being 12, considering the timeliness of the link.
When building a link, the security gateway will simultaneously build a primary and backup link when there are sufficient nodes, improving the speed of link switching. For established links, the security gateway has a security detection function to check the link status and whether it is communicating normally. When a node is disconnected, the security gateway will try to reconnect or choose the optimal path to the target node, until the connection is successful. If it fails to connect multiple times, the link will be interrupted to prevent information leakage.
(3) Data Encryption and Decryption
All traffic through the security gateway is forwarded after being encrypted. On the security gateway, dual encryption is used to encrypt the source IP address and the transmitted data. The encryption key is generated dynamically and randomly using a key exchange algorithm with forward security.
(4) Latency Detection
The overall link latency of the hidden network changes in real-time with the node status. In the hidden network, the security gateway and nodes detect the network latency between each other and display it in the link diagram for user reference. When the latency is too high, the link can be switched to maintain optimal communication.
Introduction to Hidden Network Functions
As an intermediate layer between the security gateway and the target, the hidden network is responsible for the encryption and transmission of information, and also performs traffic obfuscation during data transmission. The hidden network mainly has the following functions:
(1) Data Transmission
The hidden network is a communication network for data forwarding composed of various nodes. To ensure the efficient forwarding of data, intermediate nodes in the communication link only forward data without performing encryption and decryption processing, and only the node closest to the target performs data encryption and decryption processing.
(2) Data encryption and decryption
In the hidden network, each node performs traffic obfuscation and secure transmission of data between the established secure gateway and the target; the hidden network node only accepts encrypted data sent by the secure gateway. In this way, the secure gateway and the hidden network node guard the data entrance and exit between the operational terminal and the target, encrypting the transmitted data to ensure security. The intermediate nodes in the link do not perform data encryption and decryption, and the last hop node performs source data decryption and transmission processing, while encrypting and sending the return packet data at the same time.
(3) Traffic obfuscation
Each node in the hidden network is equipped with traffic obfuscation capabilities, forwarding forged false traffic within encrypted traffic during communication, performing feature analysis on externally intercepted traffic, and each node's traffic has different characteristics, thereby improving the self-deception and security of the traffic.
(4) Node security
There will be no static code or data residue on the physical storage of the hidden network VPS nodes. Through traffic capture methods, only encrypted communication traffic between local nodes and superior/subordinate nodes can be seen; after the node restarts, it will return to the original state, leaving no valuable or usable information.
4. Application value
- Link security
During anonymous communication, all data is forwarded through the link that has been successfully established. The security of the link determines the security of anonymous communication. To achieve a better anonymous effect, link switching will be randomly performed during communication, and link switching supports both automatic switching and manual switching, with automatic switching at least once every 5 minutes; manual switching mode is based on the user's own needs, clicking the immediate switch button to perform link switching. At the same time, the hidden network supports disconnection protection, and any fault affecting node communication will directly disconnect the communication connection, ensuring that no real requests are leaked.
- Hidden node security
The hidden network is composed of VPS nodes distributed globally, and all nodes are anonymous nodes. Nodes are both the foundation for building network bridges and the vulnerable points of the entire link. The methods to penetrate nodes can be technical means or administrative means, therefore, nodes themselves need to have certain security, and the key points of node security design lie in minimizing the exposure of information and reducing complexity.
There will be no static code or data residue on the physical storage of the hidden network VPS nodes. Through traffic capture methods, only encrypted communication traffic between local nodes and superior/subordinate nodes can be seen; after the node restarts, it will return to the original state, leaving no valuable or usable information.
- Communication content security
The system adopts nested multi-level encryption technology, that is, during communication, data is encrypted in a nested multi-level manner, and at the same time, the encryption key is automatically changed to avoid brute force and replay attacks, ensuring the security of the real traffic content.
Each node in the hidden network is equipped with traffic obfuscation capabilities, forwarding forged false traffic within encrypted traffic during communication, performing feature analysis on externally intercepted traffic, and each node's traffic has different characteristics, thereby improving the self-deception and security of the traffic.
2025 latest & emulator WeChat mini-program packet capture & mini-program reverse engineering
Join the FreeBuf first-party community
Git leak && AWS AKSK && AWS Lambda cli && Function Information Leakage && JWT secret leak
'Black Ball' attack is still in progress: from anti-virus detection to installation of mining
评论已关闭