2.3 Concurrency Containers and Utility Classes in Java
Author:JDHealth,ZhangNa1.ThesignificanceandchallengesofconcurrentprogrammingThesignifica...
2.2.1 Data Lineage Analysis
AbstractDatagovernanceisnotasimpleoperationalbehavior,butasetofactivitiesthatexercise...
2.2 Generate a device file based on two device files
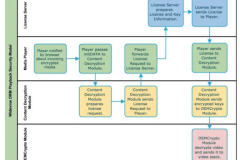
DRM,shortforDigitalRightsManagement,isatechnologyforaccesscontroltopreventcopyrighted...
2.1.1 vscode-lua-format
I.SummaryTheLucisystemisanopen-sourcesystemwritteninlualanguage,mainlyintroducingsome...
2.1. Obtain the password of the optical network terminal super administrator account (telecomadmin)
Author:Xuéyú@DuncanSecTeam0x00:PrefaceChinaTelecomisthelargestfixed-linebroadbandaccessse...
2.1 Find the location and the root cause of the problem in the code for the large object
Author:KoreanHANfromJDTechnologyFirst,problemdiscoveryandinvestigation1.1Findthecauseof...

2. WIFI-Pumpkin wireless fishing
I.Environmentalpreparation:1.Softwareaspects:ThewirelesspenetrationusesKaliandDClinux,and...

2. Why Conduct Chaos Exercise
I.IntroductiontoChaosEngineering1.WhatisChaosEngineeringChaosengineeringisasystemstabil...
2. View scheduled tasks & startup items
BackgroundAccordingtothesecuritythreatdetectionofasecuritycompany,in2019,thenumberof...

2. Use ShardingSphere-Proxy to implement sensitive data encryption
Intermsofenterprisedatasecuritygovernance,inadditiontobeingfamiliarwiththeprovisionso...