0x01 Tracing of Phishing Emails
1. Event Background
A certain unit received a batch of the same phishing emails.
2. Email Tracing
We reviewed the email content and its source code and found that the sending address of this email belongs to a company, which is very likely to be a stolen email address.

In the email content, the phishing attacker requires the customer to send the modified account password to another email address - this is also a characteristic of email theft, because if the phishing attacker replies directly, they will not receive the email.
We found that this email is a foxmail email, and foxmail is an affiliate product of QQ email. When we searched for this email in QQ, we found some QQ accounts, but we could not determine which one is the phishing attacker.
The delivery of the email does not require confirmation from the recipient, and the QQ email APP can also add the recipient to the contact list without confirmation. Although we cannot obtain detailed information, we can compare the avatar according to the contact list.
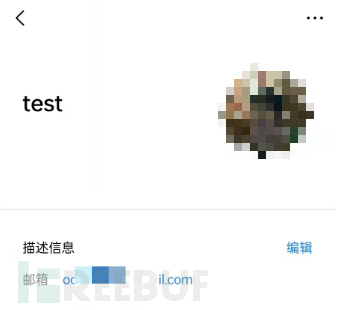
This matches a QQ number searched, and the QQ space exposes a large amount of personal information.
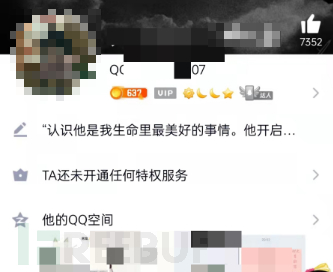
Then use the contact list function of the QQ email APP to compare the built-in 'QQ number + qq.com' email.

The secret protection phone number is verified to be domestic
0x02 On-site Emergency in a Multi-Virus Environment
In this case, the internal network environment is complex, the types of viruses are numerous, and due to the limitations of the on-site environment, it is difficult to locate the problem host, which belongs to a relatively difficult emergency event.
1. Event Background
An alert from a unit, some hosts haveAbnormal trafficExternal connection.
2. Confirmation of Abnormal Phenomena
Remote overflow attacks were initiated using the 'Blue Keep' vulnerability, but the hosts initiating the attacks were all judged as low-risk by the system. Why is that?
By reviewing the records, we finally found a host that was infected with the trojan virus first and fell victim to it.

The trojan has the following characteristics:
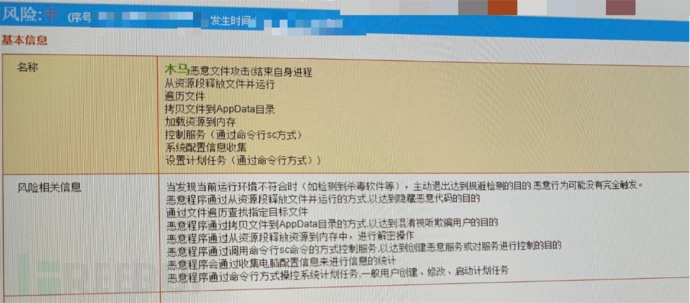
Through the log, the remote control IP of the malicious trojan was successfully found.
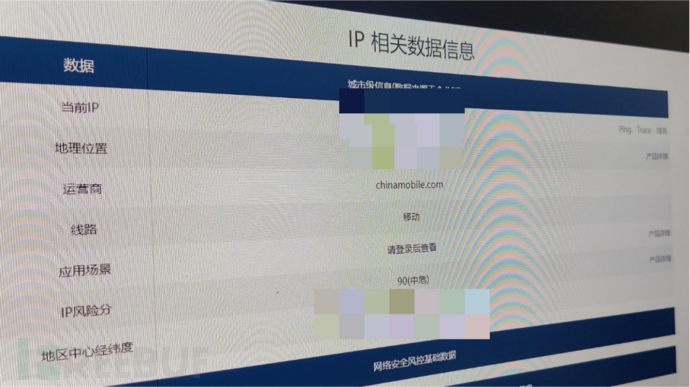
But in this incident, the real difficulty lies in handling: due to the late launch time of the related platform, the number of infected hosts is far more than just a few in the system.
3. Problem Handling
In this case, it is worth mentioning that since the IP is configured using DHCP, the most difficult thing in the process of problem handling is to find the host that needs to be handled and executed the trojan file.
The range of the customer's host is very large, and it is impossible to ping the trojan host at a branch main hub, which is very strange. Therefore, we decided to deal with the few hosts that have external IP 445 ports from the alert of the situation awareness platform first. We arrived at the location of the host assigned the IP segment, and found that most of the hosts had the situation of external IP 445 ports.
Check the process name through the PID number:
wmic process get name,executablepath,processid | findstr PID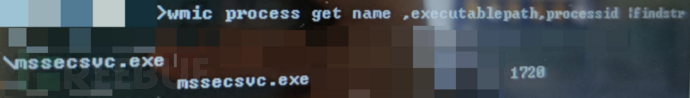
This mssecsvc.exe isWannacry ransomwareFile.
After scanning, another virus file wtime21.exe was found.

As the file is not encrypted temporarily, we first deal with the ransomware and will deal with this unexpected problem later.
Interrupt harmful processes, isolate harmful files, and block ports with scripts:
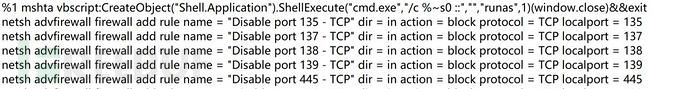
Then let's look for the threat processes related to wtime32.dll:
Command:
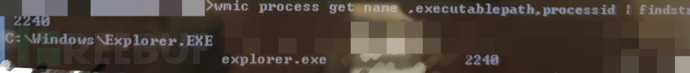
tasklist /m wtime32.dll
But according to this dll, the process we located is explorer.exe. We still use the method we just mentioned to find the file path of the process related to the PID. The process name remains unchanged, still explorer.exe, but the file name is Explorer.EXE.
After reviewing the information, we found that this is actuallyFaedevour wormThe virus. Faedevour worm first appeared in 2013 and has been spreading in the wild. After running, it will implant a backdoor on the infected host, steal information, execute commands, and spread by copying itself to portable storage devices and shared folders. The Faedevour virus can completely control the victim machine by executing commands, allowing attackers to steal user information, drop other malicious programs, execute malicious commands, and has great harm.
When we arrived on the scene, the virus had already executed the last step, injecting wtime32.dll into the explorer.exe process. The injection thread will create a new thread to run the backdoor payload, connecting to the C&C server. Therefore, it was a very correct choice to close the external port in time.
Since some of the infected hosts were not alert hosts, after disposal, we found one of the alert hosts and pinged the host that uploaded the trojan on that machine, and found that it could be pinged!
Since the external IP and the trojan host were not in the same network segment, we first went to the server of the external IP, tested the network situation with the trojan host, and found that they could connect. Then we went back to the secondary hub of the trojan host we tried to ping at the beginning, but it was just like the first experiment, sometimes connected and sometimes not. Finally, through the control variable method and continuous trial and error, we found the host that had been implanted with the trojan.
After antivirus, investigation, port blocking, and disposal, we found the familiar 'Explorer.EXE' again.
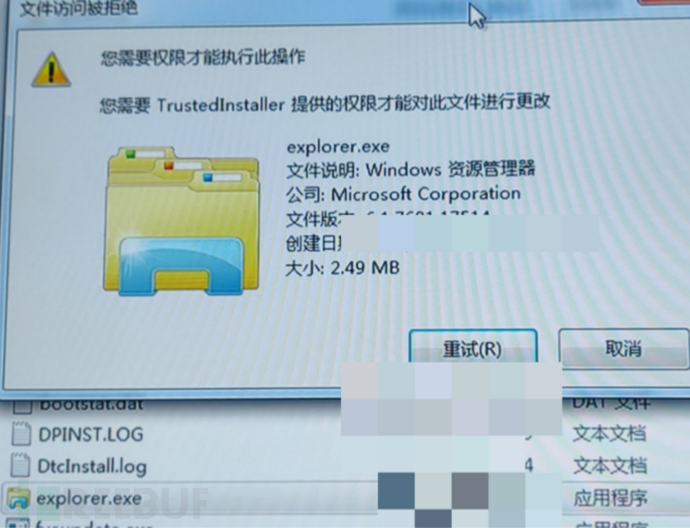
Here, the explorer.exe and the previous file have the same size.
This time, when we inserted tools like EDR into the USB interface, we found that all the folders in the USB had become executable files...
In the top-level folder, we saw a strange file: Autorun.inf.
Modifying the visible status, we found that the original folder was not changed to .exe, but it was simply hidden. And those folders with .exe at the end are not folders at all; they are application files created by the virus with the same name (you can check their properties). To camouflage itself, it changed its icon to the icon of a folder. When you open it, it will activate the virus.
And this type of Autorun.inf virus also uses 'explorer.exe' to disguise itself, which is the 'Explorer.EXE' we saw before.
(The following figure is from the Internet, not exactly the same as the real situation, used for demonstration purposes only)
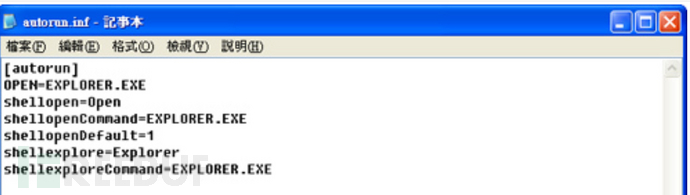
Fortunately, we detected it in time and did not click on the executable file, thus preventing the spread of the virus. After backing up the files, we formatted the USB drive and disposed of the virus.
Reference link
Construction and basic usage of a 5G network environment using Free5gc and UERANSIM
3. Multi-party Security Computation - MPC (Secure Multi-Party Computation)
Emergency response of the Windows system from the perspective of permission maintenance
Follow the Cybersecurity Medicine Water Brother to fight the target field (emergency response)
评论已关闭