Foreword
In the previous article, we shared how to capture the request packets of Android APPs using Charles and Burpsuite. When capturing HTTPS request packets, you also need to import the certificate. After Android 7, Android no longer trusts user certificates, and you also need to import the user certificate into the system trusted credentials. Many applications in order to prevent packet capture will detect whether a proxy is used. If a proxy is found, the request will not be initiated. At this time, we can capture packets through VPN proxy.
0x00 Preparation
In this session, we use Postern (Postern is a very popular proxy / Virtual Private Network management program in the Android system, and is a global proxy tool under Android) to set the proxy, download the Postern apk: https://www.apkmonk.com/app/com.tunnelworkshop.postern/.
0x01 Configure Charles

Select Proxy -> Proxy Settings, check the socks proxy, and configure the port
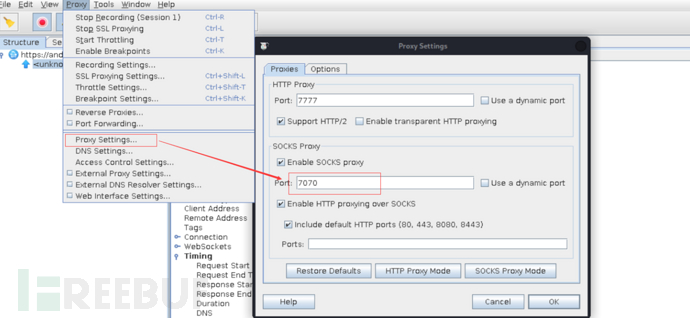
0x02 Install Postern on the phone and configure
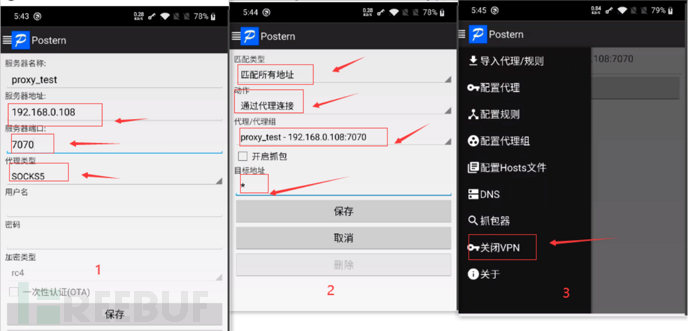
Download the Postern apk that is ready on the Android phone, and then configure the proxy after the Android
- Select the configuration proxy, fill in the proxy server address, proxy port, and change the protocol type to socks5
- Then, select the configuration rules, as shown in the figure below
- Enable VPN option
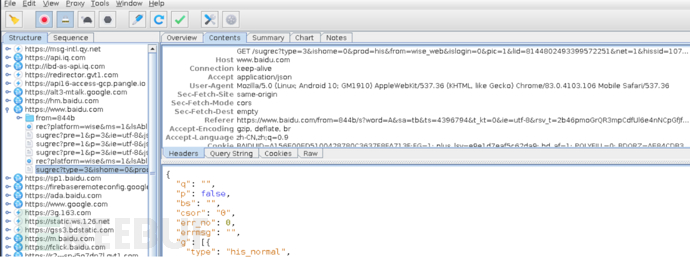
0x03 Packet Capture Attempt
Attempt to capture packets, can successfully capture https requests
0x04 Conclusion
This article shares the method of packet capture through Charles combined with VPN proxy. So far, many App request packets have been captured. However, in practical combat, some Apps have anti-packet capture checks, such as using SSL Pinning and two-way verification, etc. At this time, we need to adopt the corresponding bypassing and countermeasures technology, and the next article will continue to share the related technology of counter-packet capture.
评论已关闭