
This section discusses the attack behavior of USB from the perspective of human characteristics. For example: the use of confidential USB by external personnel or organizations.
0xA1 External Threats
Most security professionals believe that all USB attacks involve the host inserting an external USB device, which usually carries various forms of malicious code. Malicious individuals will go to great lengths to deceive users into inserting an untrusted device into their host. In the realm of social engineering, this is not a particularly difficult task. According to Steve Stasiukonis' report 'Social engineering, the USB way', during a penetration test in 2006, hackers inserted threat USB drives into 75% of the hosts within the target company within three days. The U.S. Department of Homeland Security also confirmed this result in a similar experiment, with 60% of government equipment having the opportunity to be accessed by external personnel; more interestingly, the report also points out that when drivers, secretaries, and other professions have more access rights to places, the number of external personnel accessing terminal equipment rises to 90%.
0xA2 Internal Threat
The rapid decline in the cost of USB devices has led companies and consumers to choose to use USB devices to store and transmit confidential data. Like any physical device, USB drives may also be damaged or discarded due to human error. Such handling often leads to harmful consequences. In 2011, the Ponemon Institute (Ponemon Institute) released a study on 400 different companies; they found that these companies lost $2.5 million due to the casual disposal of USB devices. Later in 2011, an Australian defense assistant lost top-secret files stored on a USB drive while passing through Kuwait. The more perfect a person is, the more likely they are to make mistakes, which will always bring heavy costs to companies and even countries.
 USB media also provides a convenient way for insider attackers to leak confidential information. In 2010, Private Chelsea Manning was arrested for violating the Counterintelligence Law due to leaking private videos of the US military. Manning used portable storage devices because of loose export controls to break through the gaps in the military network and leak information to the outside world. Edward Snowden (Snowden) used similar technology to steal top-secret data of the US National Security Agency from a military base in Hawaii. Of course, the domestic Huang* incident is also a typical case (as shown in the figure below). The universality and portability of USB devices are both challenges and opportunities. On the one hand, their ease of use greatly helps consumers and companies complete daily tasks. On the other hand, USB devices themselves actually transcend the technical scope into the administrative security and ethics field, which may have a significant impact on organizations.
USB media also provides a convenient way for insider attackers to leak confidential information. In 2010, Private Chelsea Manning was arrested for violating the Counterintelligence Law due to leaking private videos of the US military. Manning used portable storage devices because of loose export controls to break through the gaps in the military network and leak information to the outside world. Edward Snowden (Snowden) used similar technology to steal top-secret data of the US National Security Agency from a military base in Hawaii. Of course, the domestic Huang* incident is also a typical case (as shown in the figure below). The universality and portability of USB devices are both challenges and opportunities. On the one hand, their ease of use greatly helps consumers and companies complete daily tasks. On the other hand, USB devices themselves actually transcend the technical scope into the administrative security and ethics field, which may have a significant impact on organizations.

Second, Application Layer
Application layer attacks involve host user space processes and their interactions with device functions. Attacks at this layer are usually divided into two categories: code injection attacks and data filtering attacks.
0xB1 Code Injection
USB storage has been exploited by multiple malicious software. In the cases I know, the Duqu virus used an application layer rootkit to hide malicious files on USB storage devices. The Conficker and Flame viruses used 0day attacks and malicious autorun. When a USB flash drive is connected to the host, the inf file automatically executes malicious software. Although the autorun feature has been restricted after becoming one of the main threats on the Windows platform, similar functions are still available due to operating system vulnerabilities (such as Bad-USB).
0xB2 Data Filtering
As USB devices usually do not authenticate the applications communicating on the host, applications may write or read data to or from USB devices. For example, the storage of local data of network cameras, the saving of local logs of USB devices, and various security vulnerabilities existing at the application layer of USB devices may all become critical factors.
Three, Transmission Layer
0xC1 Protocol Forgery
USB devices take advantage of the host's complete trust in any connected devices, and they often provide additional driver layer interfaces for the terminal operating system. Like USB rubber ducks or USBdriveby(http://samy.pl/usbdriveby/)When such a device is connected to the host system, all the callback interfaces of the driver layer protocol stack (including those unknown to the user) will be enumerated. This function can be hidden by embedding malicious code into other normal devices (such as the network adapter in a Bluetooth earphone).
TURNIPSCHOOL project(http://www.nsaplayset.org/turnipschool)is an improved USB cable, which has a 4-layer PCB board, an interface expansion with an integrated chip USB HUB, an integrated radio frequency transceiver microcontroller from Texas Instruments, and a 3D printed plastic mold. After the device is connected to the host, the software running on the host can extract data or receive commands through the RF interface. This makes the USB transmission layer programmable twice, which can be used for the development of security filtering products for USB devices.
It has traditionally been difficult to identify and mitigate these malicious interfaces. Because the opponent can simply reprogram any USB basic data (VID, PID) to circumvent the device whitelist or blacklist rules in the operating system. In addition, since malicious personnel can reasonably use combined devices such as audio headphones, the attack surface is wide, the hiding rate is high, and the cost of the attack is reduced.
0xC2 Protocol Vulnerabilities
The host's USB protocol stack only needs to comply with the USB standard, and third parties can freely expand, so there will definitely be a large number of transmission protocol layer vulnerabilities. Using FaceDancer for Fuzzing technology (the author will write a tutorial on FaceDancer in the future), we found many arbitrary code execution vulnerabilities in the kernel layer. In 2017, Google researchers also found more than 40 vulnerabilities in different Linux kernel USB drivers. In some cases, these vulnerabilities may be exploited during the device enumeration of the host. They may also be used as a man-in-the-middle device to snoop on data.
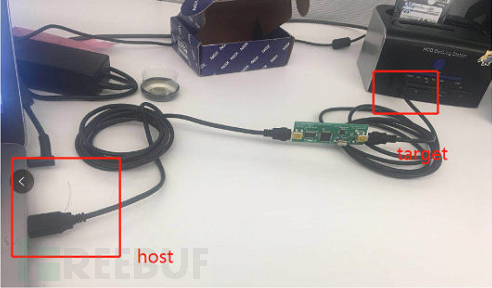
Four, Physical Layer
Physical layer attacks include attacks on the confidentiality and integrity of USB bus communication.
0xD1 Physical Interception
Regardless of whether the data is sensitive, it always needs to be exposed in the pipeline for a period of time during transmission. Excluding transparent encryption, most traffic will meet the USB underlying transmission standard, and we use hardware keyboard recorders to conduct a large traffic audit, extracting important information from USB storage, even USB keyboards. Keyboard recorders are small devices, placed between the host port and peripherals to capture packets. Before USB 3.0, malicious peripherals could eavesdrop on the downlink traffic of all connected devices.
(A transparent defense against USB eavesdropping attacks) M. Neugschwandtner

We can even carry out attacks through USB current sniffing, oscilloscope channel collection, and other methods. The channel data can obtain important feature information of the current host, which malicious smartphones can use to compose the elevation of privileges shellcode for the target. (Android Security Research Overview) Jiang Shaolin
Another method of USB sniffing is to use a USB protocol analyzer to extract the timing characteristics of the bus state and use machine learning classification to infer the host's operating system and obtain specific information. Betas proposed a fingerprint printing scheme based on time intervals, which can be initiated from commercial smartphones. They showed that specific operating system versions and models can be detected with an accuracy of up to 90% through the intervals of data packets sent between devices. Although timing-based fingerprinting significantly raises the threshold for evading vulnerabilities, experienced malware designers can modify their timing characteristics to evade detection.
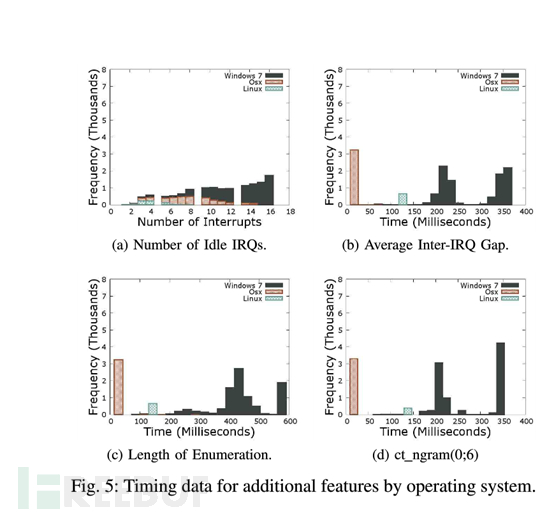
0xD2 Side-channel attack (electromagnetic, power attack)
In recent years, researchers have studied how attackers use implanted radio frequency transmitters to steal data from ordinary terminals. This method requires a hard-modified USB plug or device, as well as a dedicated embedded radio frequency transmitter. USBee is a device that emits electromagnetic radiation as a radio frequency transmitter, performing operations such as encoding/capturing sensitive data. Of course, if the attacker cannot access the target machine, they can use a regular wire to touch the exposed metal parts of the target machine, and the signal obtained can be used to extract important key information. Oswald et al. demonstrated how to extract an AES 128-bit key from Yubikey 2 based on power consumption and electromagnetic radiation. (Side-channel attacks on the yubikey2one-time password generator) Oswald
 The ability to inject electricity is also used to cause physical damage to the terminal. The USB Killer embeds multiple capacitors on both sides of the PCB board of the USB key. Once connected to the host, the USB killer consumes current from the host USB bus to charge its capacitors. Once fully charged, -200V DC is discharged through the host's USB data line. This charging/discharging cycle continues until the USB killer is removed or the terminal is destroyed. In the new version of USB power transmission and Type-C connector standards, devices can obtain and transmit up to 100W of power, which can damage the host and is not repairable. (End)
The ability to inject electricity is also used to cause physical damage to the terminal. The USB Killer embeds multiple capacitors on both sides of the PCB board of the USB key. Once connected to the host, the USB killer consumes current from the host USB bus to charge its capacitors. Once fully charged, -200V DC is discharged through the host's USB data line. This charging/discharging cycle continues until the USB killer is removed or the terminal is destroyed. In the new version of USB power transmission and Type-C connector standards, devices can obtain and transmit up to 100W of power, which can damage the host and is not repairable. (End)

*Author: Li Quan @War Profiteer, please indicate the source as FreeBuf.COM when转载
评论已关闭