Preface
Recently, the renowned information technology research and consulting firm Gartner released the latest issue of the 2021 Security and Risk Management Trends Report, summarizing the eight security and risk management trends in the information technology industry in 2021.
Among them, the first point mentions the 'network security mesh' technology:
Network security mesh is a modern security method that can deploy control measures where they are most needed. Network security mesh does not allow each security tool to run in an 'island', but through the provision of basic security services and centralized strategy management and coordination, enables interoperability between tools. Now many IT assets are outside the traditional enterprise boundaries, and the network security mesh architecture enables corporate institutions to extend security control measures to distributed assets.
Compared to the trend report of 2020, the same is the first point -- "XDR improves accuracy and productivity":
Extended Detection and Response (XDR) solutions are emerging continuously, which can automatically collect and correlate data from multiple security products to improve threat detection and provide event response functions. For example, attack behaviors such as triggering email, endpoint, and network alerts can be merged into a single event. The main goal of the Extended Detection and Response solution is to improve detection accuracy and enhance the efficiency and productivity of security operations.
Both have the same meaning, mentioning the core concept of XDR and discussing the value of 'integration', 'association', and 'expansion'. It is evident that XDR is of great importance in today's security operations field. This is also in line with our product philosophy. In this article, we will briefly discuss the thinking on XDR products from the perspective of technological development.
From Service Mesh to Security Mesh
"Security Mesh" seems to be another new term, but from the perspective of cloud native, this is not a new concept. Similar concepts such as Service Mesh (service mesh) have become one of the very important basic concepts in cloud native (Cloud Native).
The current trend in cloud technology is to grind and refine the computational model and computational power, making them more granular and flexible. From the perspective of system process architecture, each link in the process, such as computing, storage, network, security, middleware, big data processing, and artificial intelligence, has been completely decomposed and decoupled, allowing for various flexible combinations and packaging; and from the perspective of computational power, hardware virtualization, operating system virtual machines, application environment isolation, containers, process isolation, microservices, servless, and function computation, the scale of computational power has also been divided into more and more refined levels.
All of this is to eliminate IOE, better utilize the value of large-scale low-cost hardware, and the deeper reason is the requirement of business development. To a certain extent, the trend of technology is to match the trend of business, that is, the current "business explosion". The "explosion" brings two major challenges: first, the exponential increase in business complexity, and second, the increasingly fast pace of business changes. Therefore, the concept of Service Mesh (Service Mesh) has evolved in IT architecture.
To put it simply, Service Mesh (Service Mesh) does two things: first, "splitting", and then "combining". Through "splitting", the business module and business support module are stripped off; the business module is customized and functional; while the business support module is general and common. Therefore, the architecture is decomposed into a series of double-module combinations, that is, the so-called sidecar form. And through "combining", the common business support modules are connected together, forming a grid network. The grids communicate, cooperate, and coordinate with each other, and are managed by a unified control system.

This kind of service mesh at least brings two major benefits:
Firstly, it is to further decouple the business logic and basic components, using the "zero trust security" theory to explain it is to decouple the "control plane" and "data plane", allowing business developers to focus on the implementation of business logic without considering basic and general issues, thereby solving the response difficulties caused by the fast pace of business changes.
Secondly, through the service network, a common support standard for control components has been formed, endowing the business with capabilities that are not originally possessed, such as elasticity, scalability, and security. Of course, directly "splitting" and "combining" does not solve the problem of complexity, but only transfers it. Fortunately, there are frameworks like Istio in the industry that have accepted complexity and solved the problem of complexity.
The control center of the security grid - XDR platform
Understanding the core concept of Service Mesh (Service Mesh), we will naturally associate it with the fact that "security" is also one of the common attributes of the system. Can we transform "cloud-native" into "security-native" through a similar approach, and build a security architecture system? Is there also a similar security operation platform to bear the complexity mentioned above?
Of course, the answer is yes, this is the decision-making platform of Jidun Technology.
Let's take a more detailed look at the architecture of Service Mesh (Service Mesh), which includes "Service", "Proxy", and "Control", respectively corresponding to business logic, proxy execution, and control center. In the security architecture system, "Service" is the business we need to protect, such as email, code, office systems, IT environments, and so on; "Proxy" is the single-point security products and devices we connect to, responsible for the specific execution and inflow and outflow of data and alarm information, such as WAF, firewall, NTA, NIDS, and so on; while "Control" is the positioning of the decision-making platform, responsible for "unifying analysis and decision-making to the same platform", solving common problems such as flexibility and complexity.
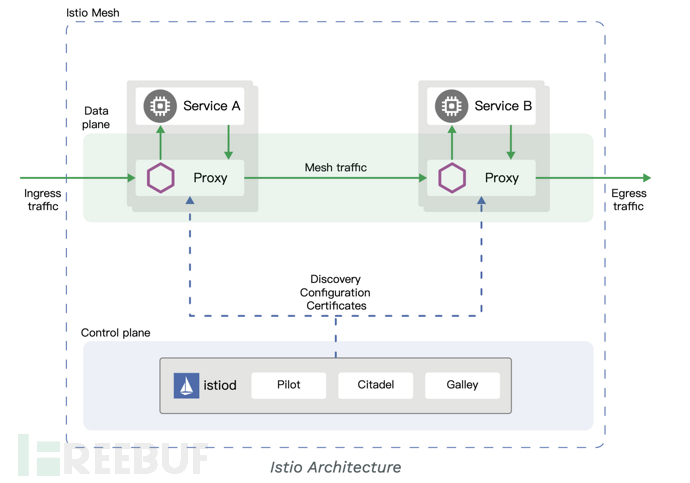
From Service Mesh to Security Mesh, the Jiuce XDR platform brings revolutionary security operation architecture to customers, expanding the boundaries of security operation.
This brings many advantages that traditional big data security products cannot achieve:
1. Without changing the existing security investment of customers, help customers give full play to the capabilities of the existing security platform to achieve the effect of 1+1>2.
2. 'Security Native', for platforms without native security capabilities, quickly upgrade them to the 'Security Plus' version; for security products that have certain security analysis capabilities but are not flexible and powerful enough, do single-point enhancement.
3. Built-in and reusable security operation capabilities, by solidifying security operation experience into the system, can help customers continuously accumulate and share security operation experience capabilities.
4. Further breaking down the security data silos.
There are many other advantages that will not be listed one by one.
Thoughts on XDR products
As a comprehensive security operation platform, Jiuce focuses on the following three points: 'user experience', 'efficiency and intelligence', and 'effectiveness sustainability', which are complementary to each other and mutually promote.
Before product development, after repeated discussions and confirmation of priorities, we focus on two of the most core key points: real-time and adaptive capabilities.
Jiuce can complete the execution of hundreds of rules, strategies, and models within 10 milliseconds, 'instantly' returning detection results, which is a huge improvement for most existing offline or semi-real-time detection methods in the security industry. The new generation of security attacks no longer satisfies the detection method of t+n, and scenarios such as hvv that require rapid response further intensify this demand.
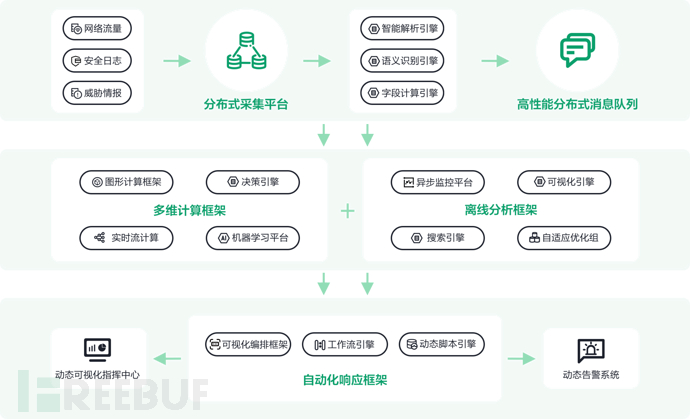
Adaptive solutions address the sustainability of effectiveness, behind which intelligent capabilities help users mask the complexity of system use and update processes. Through technologies such as anomaly identification, unsupervised algorithms, and automated recommendations, the system optimizes existing models in parallel in the background and continuously calculates the final effect. Once the user triggers feedback, the existing rules, strategies, and models can be updated with one click. Through this immediate feedback mechanism, it can also promote the continuous labeling of users, ultimately forming a closed loop to achieve the effect of 'the better the more used'.
This is our analysis and interpretation of Gartner's latest security trends report. We welcome everyone to communicate at any time and also invite more friends to try the Jiudun strategy platform and give us good suggestions.
评论已关闭
