Account password is the most frequently used basic parameter in daily use, and it is the last line of defense for overall information security protection. 'Handing over the password' is equivalent to 'surrendering arms' in the information security confrontation. To meet the overall prevention and control of information security, improve the awareness of password security among all staff, and ensure the safe use of passwords is crucial.
 How are passwords stolen?
How are passwords stolen?
Malicious attackers will try to crack into your account using the most common passwords, or guess passwords by using your publicly available information on social websites (software), such as various dictionary and social engineering databases. If successful, they will attempt to crack other website accounts of yours using the same password.
Malicious attackers may also attempt to lure people into revealing their passwords by sending phishing emails with forged links to suspicious websites, or by using persuasive techniques through social software.
Even if you have protected your own password, if a company database that records your detailed information is leaked, they may still be stolen, and you have no way to do anything about it. Malicious attackers will use these stolen user information (such as usernames and passwords) to try to access and crack other systems.
Practical suggestions
1.1 Suggestions for administrators
Maintain the minimum length requirement of 8 characters (and longer is not necessarily better).
Cancel the mandatory character complexity composition requirements.
Cancel the mandatory periodic password reset requirements for user accounts.
Prohibit the use of common and commonly used passwords to exclude the most vulnerable dictionary attacks from being attacked.
Guide your team members not to use their work passwords for non-work related matters.
As far as possible, force the registration and use of multi-factor authentication.
1.2 Suggestions for individuals
Enterprise employees have the responsibility to ensure the security of office password passwords.
Change the initial password! Remember that the first step in using any system is to change the initial password.
Create a unique password for office applications instead of using the same as personal accounts.
Set a password that is easy to remember and relatively complex for the system, do not use common phrases.
Keep the terminal computer operating system, browser, and software up to date.
Be cautious when opening email attachments and links within emails, and be cautious when entering account passwords.
Break the cognitive误区
2.1 The longer the password, the better
The password settings we usually see are that the password length should be kept above 8 characters (including 8 characters), even longer. Although, the longer the password length of the account, the longer the time it takes to be attacked (and the attack on passwords has long been not just brute force), but too many length requirements (more than 14 characters) increase the possibility of adopting other unsafe practices, such as difficult to remember and write down the password (commonly seen in plaintext passwords written on sticky notes or notebooks), using repeated passwords, random word pinyin combinations, or storing plaintext passwords in PC documents.
To encourage individuals to consider using unique passwords for important systems, it is recommended to maintain a minimum length of 8 characters, not too long, and recommend 8-14 characters, which actually also conforms to our guidance on prohibiting common passwords.
2.2 The more complex the password, the better
Passwords have very complex characteristics, and it cannot be determined that the password you are using is necessarily a secure password. Setting passwords should be both secure and easy to remember. Too complex passwords are more likely to cause forgetfulness or loss, and frequent password resets will also make it difficult for you to set new passwords.
2.3 The shorter the password change cycle, the better
Research shows that the cognitive resource pool of human knowledge is limited. Frequent password changes will consume the password pool resources in your cognitive area, and you will tend to set passwords that have been used before, similar passwords (such as consecutive months or years).
2.4 Password security only needs to focus on setting a secure password
In internal network attacks aimed at obtaining computer passwords or system login permissions, brute force cracking of computer passwords is no longer the only method. Methods such as email phishing, social engineering, web malware, malicious software programs, 0day vulnerabilities in terminal operating systems and software can all achieve the purpose of stealing password credentials and obtaining system permissions. Therefore, ensuring password security not only requires setting a secure password but also requires preventing other forms of network attacks, being cautious about email phishing, browsing websites securely, keeping computer operating systems, antivirus software, and other application software up to date (patches can solve more than 90% of security issues), and regularly scanning for malicious programs.
Personal User Guide
3.1 Do not use office accounts and passwords on ordinary websites
You must have many important website accounts for you (such as online banking, Taobao, Alipay, WeChat, etc.), and using relatively independent passwords on each site is more secure. We do not recommend using office account passwords for personal accounts, such as using office email to register and as an account for other sites, using the same password for OA systems on personal forums, etc., which may make you more vulnerable to attacks.
Therefore, as a deterrent strategy, please set a unique office account password and do not reuse passwords between multiple sites.
3.2 Do not easily leak your email or account information
Do not easily disclose information such as corporate email accounts or internal office systems. This will reduce the difficulty of account password attacks. When setting security questions, please use password answers that only you know personally, rather than using simple public answers such as your department name or company name. When setting passwords, it is likely that you will use words related to yourself (such as birthdays of you and your family, nicknames of your children, and words you like to use), so remember to ensure that your password is difficult to guess.
3.3 Reasonably set password complexity requirements
Most systems enforce certain levels of password complexity requirements (passwords need characters from three categories: uppercase letters, numbers, and recognizable special characters), but most people use similar patterns (such as uppercase letters at the first position, symbols at the last or middle position, and numbers at the end), company patterns (company name abbreviation + year), or personal patterns (name abbreviation + birth date). Attackers know these and use common synonyms for dictionary attacks, so seemingly complex passwords are actually weak passwords.
3.4 Do not use common password phrases
When setting a password, do not use common passwords, pinyin words, or phrases, as they are more easily cracked. For example, 12345678, password, iloveyou, Jtyh@2019, 1234!@#, jtyh@888, are all weak passwords.
Passwords can be composed of pinyin words or English words, but they should be unique to your life, with both memorability and distinctiveness; your company name, name abbreviation, and birthday are not suitable.
Do not use keyboard sequence passwords. Passwords set by consecutive keys on the keyboard may be complex but are not sufficiently secure. For example, '1234qwer', '1qaz@wsx', 'asdfjkl;', '567890-='.
3.5 Be careful of suspicious emails and websites
It doesn't matter what the password is, because if you are phished, the malicious attacker can steal it. Therefore, be vigilant about suspicious emails and URL links, which may entice you to click and lead to the installation of malicious software or the theft of your password credentials. Pay attention to the following matters:
- Be cautious when opening and clicking on URL links in emails or documents
- You can copy the URL link or directly input the URL in the browser address bar to avoid some phishing links
- Establish browser bookmarks for commonly used websites (such as OA and email), and open each time from the bookmark tab
- When entering passwords on a website, pay attention to check whether the URL is correct
3.6 Keep system software up to date
Keep your operating system, browser, antivirus software, and other software up to date to enhance the ability to resist common malware, phishing, and other common attacks. For personal computers, installing antivirus software and timely patch updates can resist more than 90% of attacks, including malware or backdoor programs that can steal passwords.
3.7 Try to use multi-factor authentication
Passwords may be forgotten or leaked, so the best choice is not to use passwords at all, or to have an additional authentication method. Therefore, in life, if conditions permit, you should use as many authentication methods as possible, such as SMS verification codes, fingerprint, or facial recognition (fingerprint recognition is recommended for terminal computers).
3.8 Regularly confirm the security of your account password
After long-term use of passwords, there may be password leakage situations. If you use office accounts or email to register other types of website applications, your password may also become insecure due to data leakage of users on other types of websites.
Password security guidelines do not recommend frequent password changes, but considering that passwords may be spread or leaked during use, we suggest that the password change cycle be around 6 months for the most part (you can choose not to change the password if the password is sufficiently complex and has never been leaked).
Is the new password you set secure, and is it among the passwords in the historical password leak database? You can log in to the website haveibeenpwned (https://haveibeenpwned.com/Passwords(*Other social engineering libraries, tg robots) website for detection.
3.9 Increase vigilance
Gaining access to corporate internal employee account passwords through social engineering is the most effective attack method against enterprises. 'Don't give away your password just because someone treats you to a meal,' so it is necessary to enhance personal security awareness, be vigilant against password requests in daily life, do not share passwords with others, and pay attention to account password reset emails and other phishing attempts. If you find similar incidents, you can report them to the IT operations management department in a timely manner.
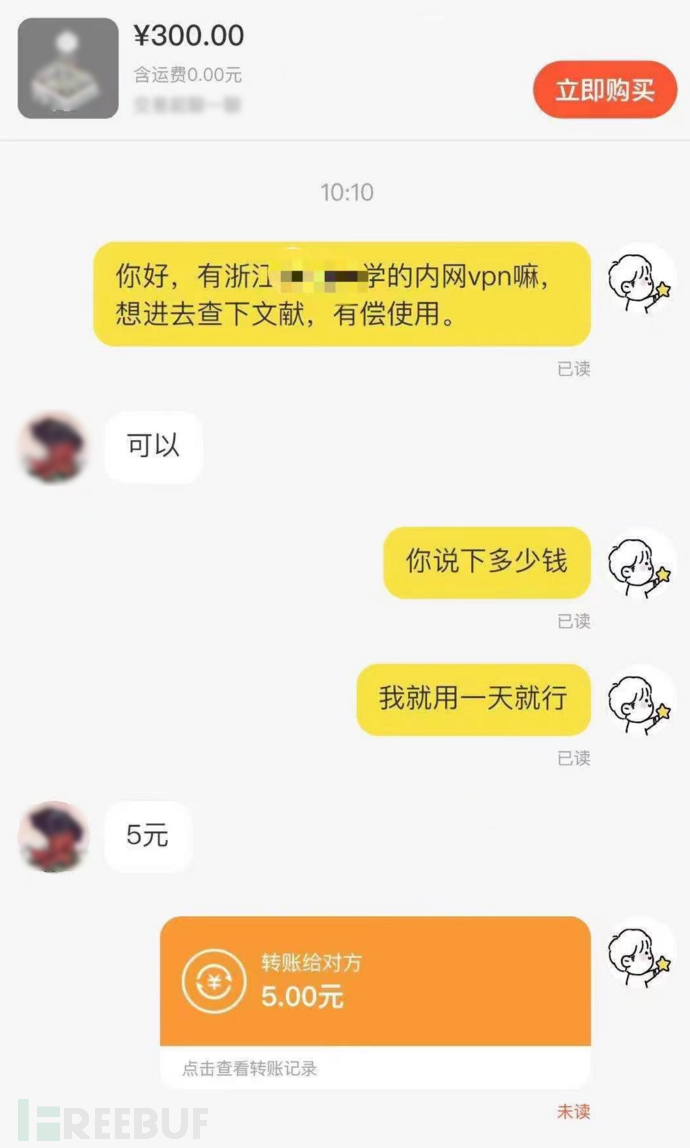
Don't give up your password just because someone invites you to dinner.
Password management methods
Everyone has the responsibility to ensure the security of their password, including not setting empty passwords, safe password settings, periodic changes, and setting error locks, etc. The basic principle of password security settings is 'easy to remember while sufficiently complex'.
4.1 Reasonable classification and management
In daily password settings, it is recommended to separate the office systems used from the personal registered website applications, and important systems from ordinary systems. Set passwords with different security levels separately.
- Set up passwords independently for office systems (OA, email, VPN, financial management, etc.)
- For personal online shopping, online banking, Alipay/WeChat, private cloud disks, etc., it is appropriate to set higher requirements for passwords
- The passwords of ordinary personal accounts such as technical forums, communities, recruitment websites, short video websites, etc. can be reduced in requirements
4.2 Password management
With too many websites and too many passwords to manage, how to solve this problem. You can use the password reminder function of similar browsers like Chrome (Chrome has had a password reminder vulnerability in low versions), or password management tools like 1password, to set different complex passwords for different websites and applications, and manage them with such tools. You only need to remember the password to open the tool. On mobile terminals, it is recommended to use KeePass, AppLock, 1password, or the password reminder function of the phone, etc.
4.3 Setting complexity
It is recommended to set the password length between 8-12 characters for password setting, which is both secure and easy to remember. Of course, it is not appropriate to use only lowercase letters and numbers, and it should contain two or more types of uppercase and lowercase letters, numbers, punctuation marks (or printable special characters). Some special techniques can be used, such as symbol transformation and symbolic transformation:
- 1337 language
The 1337 language is rumored to be a hacker language in legend, just like the slang of江湖 people (Reference and self-judgmentThrough the transformation of uppercase and lowercase letters into symbolic numbers or characters, it can achieve the characteristics of encryption and difficulty in reading. For example, the following conversion list can be used, or you can change it according to your own ideas:
Characters | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | | | a | b | c | d | F | G | H | W | X | P | S | t |
Transformation | o | I/L | z | e | a | s | g | t/T | B | i/I | @ | |3 | ( | oi | |= | 6 | |-| | vv | >< | |* | $ | + |
Therefore, you can use your own ideas to create transformations, such as turning 'advanced search' into '4dV4NC3d 534RC|-|'.
- Password generation tool
Using online or offline password generation tools on the Internet, you can choose options to generate sufficiently complex passwords, including length, uppercase and lowercase letters, and printable characters, and save them for use. However, such passwords are usually difficult to remember.
4.4 密码设置技巧
密码设置可以利用以下方法,结合字形变换,设置一个既复杂安全又易于记忆的密码。
- 喜爱的句子
找到一个生僻但易于记忆的短语或句子(可以摘自你喜欢的歌曲、小说或电影),然后创建它的缩写形式,其中可以包含大小写字母或数字或标点符号等。比如”我的女儿豆豆出生在9点15分”改写成密码“WnDDborn@9:15”,电影台词“听过很多道理,依然过不好这一生”改写成密码“Dhenduo!!!gbh1~”。
- 唐诗宋词八百首
从唐诗宋词中,选择背诵一首七言律诗,使用每一句变换进行设置密码,四句轮换使用也可以解决周期性修改密码的难题(请自己选择词句,网络上搜索到的例子已被各社工库登记,不再安全)。
例如选择唐代李商隐的《锦瑟》中“锦瑟无端五十弦,一弦一柱思华年”,改写成你的密码“Jswd50~#1~1!shn”。“娉娉袅袅十三余,豆蔻梢头二月初”可改写成密码“ppnn13%dkstFeb.1st”。
- 方言/外语
利用你的知识域,设置密码时可以使用一些非主流语言、利用英语与汉语拼音的转换、英语与汉语拼音的混用等等。比如将“2020年结婚”可以改写成“z0z0y3aR@結婚する”或者“Z0Z0Y3ar&jiehunshengzi”。
- 不易被猜测的常识
有些大众都了解的常识理论或知识,但不常被用于密码猜测,因为常识理论使资源池足够广,所以可以被很好的用于密码设置。比如可列举以下案例:
常识知识 | 转化成密码 | |
1 | 党的生日 | CPC-shengri@7.1 |
2 | 浙江省会是杭州 | ZJ3h^^^hangzhou |
3 | 10月1日是国庆节 | Holiday=10yue1 或者 Oct.1 |
4 | 女神刘亦菲 | NvS,L1f. |
5 | 2020是鼠年 | 2o2o=shuYe4r |
6 | 要奔三了怎么办 | 30IScoming??? |
7 | 我忘记了我的密码 | #Wwjlwdmm$ |
此文以企业中的实践指南,经过理想情况的演绎和修订,在实践中可能并不能全部实现,同时需要各种规章制度的约束和技术管理工具的结合,本指南仅供参考,实践意义自行评估。
评论已关闭