1. Overview
The Internet of Things is a relatively complex field involving a lot of knowledge related to electrical engineering, communication engineering, electronic engineering, and other fields. The security technologies and frameworks in the IoT field also have significant differences from the Internet. In order to help engineers understand the analysis framework and technology of IoT device security as systematically as possible, this article starts from the perspective of hardware tools and systematically introduces the commonly used analysis tools in IoT security analysis.
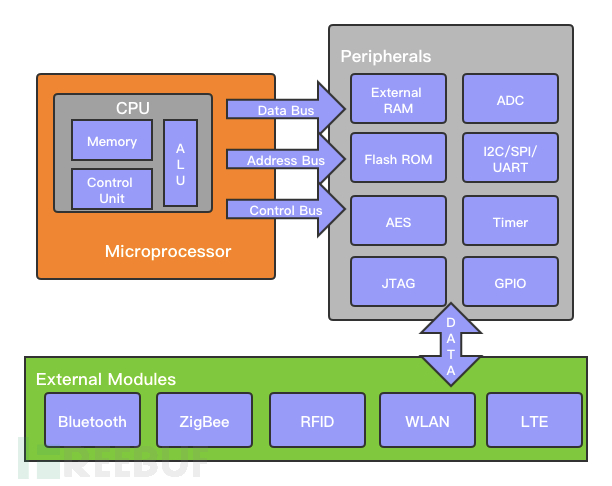
2. Internal Architecture View
When looking at an IoT device alone, it can be divided into three parts:
Microprocessor: It is responsible for the most core calculations of the device
Peripherals: They are composed with Microprocessors to form an MCU, responsible for connecting with the external world
External Modules: Different types of Internet of Things (IoT) devices handle different data and perceive the physical world through different Modules
3. Interface Debugging Tools
3.1 JTAG
3.1.1 Introduction
JTAG is the abbreviation of Joint Test Action Group, which is the commonly used name for the IEEE standard 1149.1 known as Standard Test Access Port and Boundary Scan Structure. This standard is used to verify the functionality of the printed circuit boards produced by design and testing. To put it simply, through the JTAG interface, it is possible to read and write the values in the device memory and registers, making it a powerful 'back door'.
3.1.2 Schematic
In addition to the obvious JTAG interface base, there are also some that need to be searched by themselves according to the chip pins and auxiliary tools, such as JTAGulator, JTAGenum.

3.1.3 Debugging Tools - Hardware
BusPirate
BusPirate is an open-source hacker tool that provides access to UART, JTAG, I2C, and other functions.

Jlink
SEGGER J-Links is the most widely used debugging probe series on the market. With unparalleled performance, a rich set of features, support for more CPUs, and good compatibility.

3.1.4 Debugging Tools - Software
OpenOCD
Open On-Chip Debugger (OpenOCD) is a free open-source JTAG debugging software designed to provide debugging, in-system programming, and boundary scan using a debugging adapter.
3.2 UART
3.2.1 Introduction
The Universal Asynchronous Receiver/Transmitter (UART, commonly known as UART) is an asynchronous receiver/transmitter that is part of computer hardware, which converts data between serial communication and parallel communication.
In simple terms, data interaction with the device can be performed through the UART port, accessing the Shell, burning firmware, and so on.
3.2.2 Schematic
The four contact points outlined in the picture correspond to the GND, TX, RX, VCC pins used by UART.
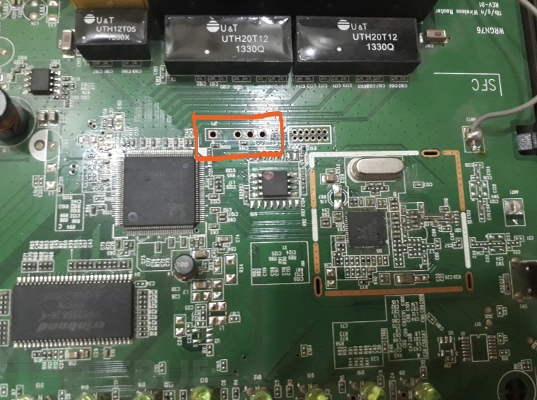
3.2.3 Debugging Tools - Hardware
Common tools for accessing UART interfaces of devices include BusPirate, USB to TTL, and other tools.
As shown in the figure is a USB to TTL tool of a certain brand.

3.2.4 Debugging Tools - Software
Tools such as Picocom, Putty can be used.
4. Microcontroller Unit Analysis Tools
4.1 Side Channels
4.1.1 Introduction
Side-channel attack is a type of attack that relies on information obtained from the physical implementation of a cryptographic system rather than brute force methods or theoretical weaknesses in algorithms. For example: time information, power consumption, electromagnetic leakage, or even sound can provide additional information sources, which can be used to further crack the system. Side channels refer to the leakage of sensitive information through power changes, time changes, and other means during the operation of the device.
4.1.2 Common Tools
Oscilloscope
Chipwhisperer
Logic Analyzer
Multimeter
Isolation Transformer
Hot air gun, soldering iron
Here, we will focus on introducing Chipwhisperer and logic analyzers.
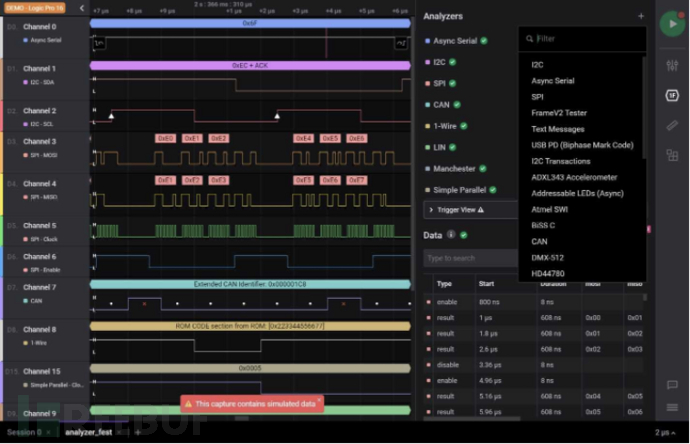
Logic Analyzer
A logic analyzer is an instrument for collecting and displaying digital circuit signals. The main function of a logic analyzer is to determine the timing. Unlike an oscilloscope, which has many voltage levels, a logic analyzer only displays two voltages, logic 1 and logic 0, as well as the uncertain x. Using a logic analyzer, you can read the digital signals of a chip and decode them.

The logic analyzer signal decoding interface is shown below: connect the logic analyzer probe to the pin of the chip and decode communication data. The logic analyzer can decode common protocols such as UART/SPI/I2C.
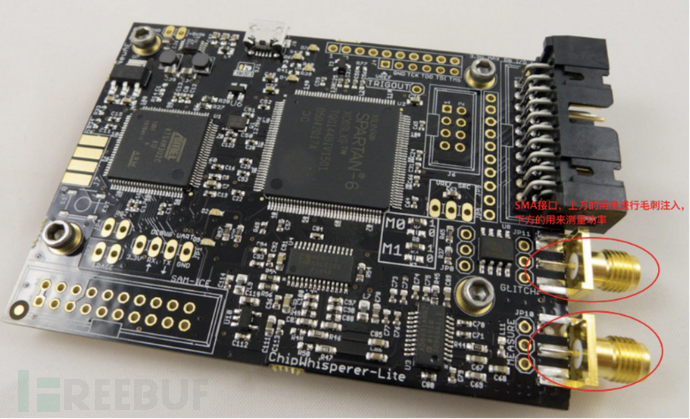
Chipwhisperer
ChipWhisperer is an open-source side-channel attack platform. ChipWhisperer mainly focuses on power analysis attacks, as well as voltage and clock fault attacks. These interruptions can disrupt the power or clock signals of a device, leading to unexpected behavior (such as skipping password checks). An oscilloscope is usually required for auxiliary power measurement.
4.2 Flash Dump
4.2.1 Introduction
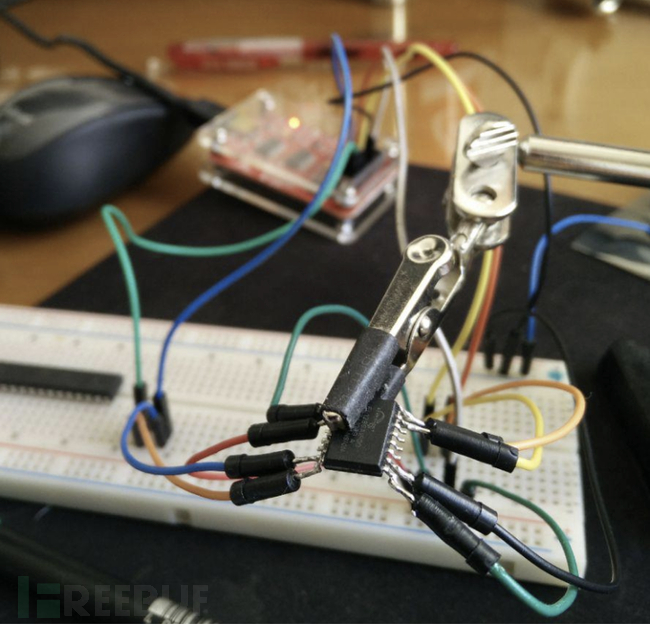
Flash memory chips on physical devices are commonly used to store firmware. If this chip does not have read-write protection permissions set, attackers can directly read (through dump or debugging interfaces) firmware, analyze and modify the firmware to bypass interface authentication. At the same time, attackers can further analyze business logic through the firmware dump, thereby gaining a clearer understanding of the entire business.
4.2.2 Diagram
4.2.3 Reading Tools - Hardware
BusPirate
Hot air gun and soldering iron
4.2.4 Reading Tools - Software
Flashrom
flashrom is a utility for identifying, reading, writing, verifying, and erasing flash memory chips.
5. Communication Protocol Analysis Tools
5.1 Near Field Communication
5.1.1 Bluetooth
Bluetooth is a wireless communication technology standard that allows fixed and mobile devices to exchange data over short distances to form a personal area network. It uses short wave high-frequency radio waves to communicate through the ISM frequency band of 2.4 to 2.485 GHz. Bluetooth has two communication channels: broadcast channels and data channels (advertising channels and data channels), as shown in the figure below, where the broadcast channel uses only channels 37, 38, and 39. The data channel includes a total of 37 channels. During data transmission, devices will use frequency-hopping algorithms to hop between data channels. Common CC2540 does not have the ability to capture data from data channels, and expensive professional Bluetooth devices (tens of thousands of yuan) or Ubertooth are needed for capture (hundreds of yuan, but unstable and only capable of capturing BLE).
The two common types of Bluetooth are:
CLASSIC
BLE
BLE analysis tool
Ubertooth One is an open-source 2.4 GHz wireless development platform for Bluetooth experiments. Ubertooth allows you to use Bluetooth in monitor mode, which is a 'promiscuous' mode that causes the radio to pass all received content to the host.

5.1.2 ZigBee
5.1.2 ZigBee
Capture tools—hardware. The 433MHz technology uses the 433MHz wireless frequency band, and therefore, compared to WiFi and Zigbee, the significant advantage of 433MHz is its strong penetration of wireless signals and the ability to propagate over greater distances. However, its缺点is also quite obvious, that is, its data transmission rate is only 9600bps, much less than the data rate of WiFi and Zigbee, so the 433MHz technology is generally only suitable for applications with less data transmission.
ZigBee, also known as ZigBee, is a low-speed short-distance wireless network protocol, the underlying layer of which uses the IEEE 802.15.4 standard specification for the media access control layer and the physical layer. Its main features include low speed, low power consumption, low cost, support for a large number of network nodes, support for various network topologies, low complexity, reliability, and security.
CC2531 USB dongle

CC2531 USB dongle provides the PC with an interface to access IEEE802.15.4 / ZigBee applications, with the accompanying CC2531ZNP-Prod firmware, which allows the dongle to be directly inserted into PC / Raspberry Pi, etc., to be used as a Zigbee packet sniffer.
RZUSBSTICK

Analysis tools—Software
RZUSBSTICK is a tool used for development, debugging, and demonstration of various low-power wireless applications (including IEEE 802.15.4, 6LoWPAN, and ZigBee networks).
SmartRF Packet Sniffer
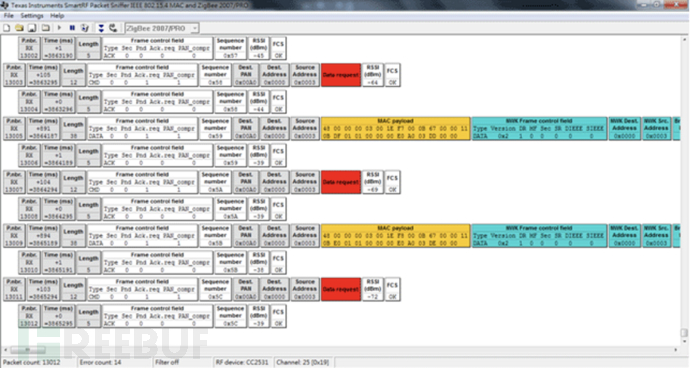
SmartRF Packet Sniffer is a PC software application that can display and store radio packets captured by the listening RF device.
KillerBee
KillerBee is a framework and toolset based on Python, used for exploring and exploiting the security of ZigBee and IEEE 802.15.4 networks. Using KillerBee tools and compatible IEEE 802.15.4 radio interfaces, you can eavesdrop on ZigBee networks, replay traffic, attack password systems, and more. Using the KillerBee framework, you can build your own tools, implement ZigBee fuzz testing, simulation, and attack terminal devices, routers, and coordinators, etc.
5.1.3 RAW RF(433MHz)
Capture tools—hardware. The 433MHz technology uses the 433MHz wireless frequency band, and therefore, compared to WiFi and Zigbee, the significant advantage of 433MHz is its strong penetration of wireless signals and the ability to propagate over greater distances. However, its缺点is also quite obvious, that is, its data transmission rate is only 9600bps, much less than the data rate of WiFi and Zigbee, so the 433MHz technology is generally only suitable for applications with less data transmission.
HackRF One
HackRF One is a software-defined radio device capable of transmitting or receiving radio signals in the frequency range of 1 MHz to 6 GHz. HackRF One is designed to support testing and development of modern and next-generation radio technologies, and it is an open-source hardware platform that can be used as a USB peripheral or programmed for independent operation.

Signal analysis tools and platforms
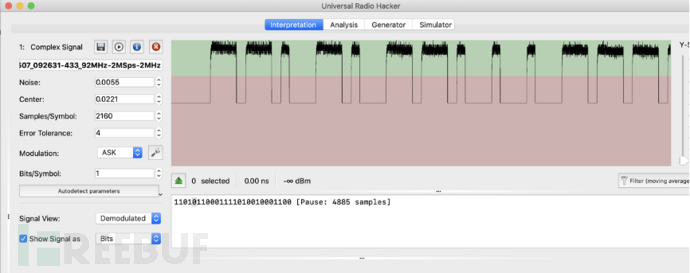
URH
Universal Radio Hacker (URH) is a complete suite for wireless protocol investigation and has local support for many common software-defined radios. URH can easily demodulate signals and automatically detect modulation parameters, thus easily identifying bits and bytes in the air.
As shown in the figure below, communication data simulation signals are captured using HackRF + URH and demodulated into digital signals.
5.1.4 RFID (IC card, ID card)
Radio Frequency Identification (RFID) is a wireless communication technology that can identify specific targets and read/write related data through radio signals without the need to establish mechanical or optical contact between the identification system and the specific target. The signal of the radio is transmitted from the tag attached to the item by modulating the electromagnetic field into radio frequency, to automatically identify and track the item.
The IC cards and ID cards we commonly use are based on this technology.
Analysis tools—Hardware
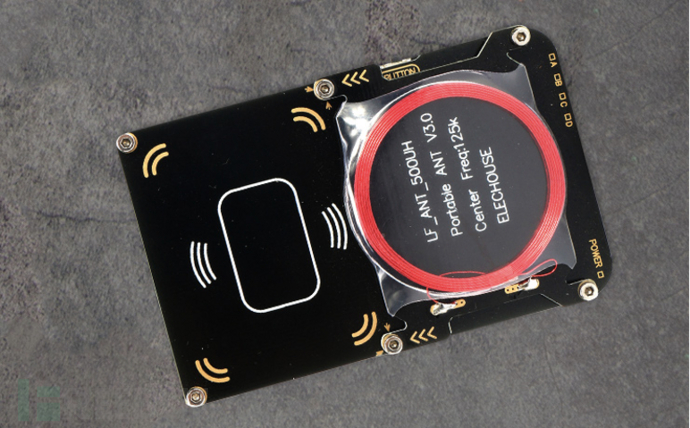
Proxmark
Proxmark is a multi-functional RFID tool that can interact at both high and low levels with the vast majority of RFID tags and systems globally.
Analysis tools—Software
Proxmark 3
Proxmark 3 is a dedicated, powerful multi-functional tool for RFID analysis, which can provide reading, writing, analysis, monitoring, replay, simulation, modulation, demodulation, decoding, encoding, decryption, and encryption for any RFID system operating at 125KHz, 134KHz, and 13.56MHz frequencies.
5.2 Wlan&Ethernet
There are many tutorials on packet capture and analysis methods for Wlan and Ethernet, which will not be elaborated here.
5.3 4G/5G communication
The cost of analysis equipment for 4G/5G communication is much higher than that of other communication methods. The commonly used equipment is as follows.
Hardware tools
Ettus B210 and BladeRF are high-performance SDR devices that can better realize 4G/5G communication simulation and monitoring.
ettus b210

BladeRF

4G/5G platform tools
srsRAN
srsRAN is a free open-source 4G and 5G software radio suite. The srsRAN suite currently includes:
srsUE - a full-stack 4G and 5G NSA UE (User Equipment) application (5G SA coming soon)
srsENB - a full-stack 4G eNodeB (Basestation) application (5G NSA and SA coming soon)
srsEPC — a lightweight 4G EPC (Core Network) implementation with MME, HSS, and S/P-GW
AirScope
AirScope is a software-defined radio LTE air interface analyzer. It provides real-time wireless decoding functions for network analysis using standard PCs and general-purpose SDR front ends, such as Ettus b210 and BladeRF.
5.4 Contact Smart Cards
Smart cards are divided into contact and contactless types. The chip of the contact card is directly encapsulated on the card base, while the contactless card is composed of a chip and a coil. Smart cards usually use communication protocols based on the iso7816 standard.
Analysis Tools — Hardware & Software
Osmocom SIMtrace 2
Osmocom SIMtrace 2 is a software, firmware, and hardware system for passively tracking the communication between SIM cards and mobile phones (SIM-ME) and remote SIM operations.

5.5 USB
Universal Serial Bus (USB) is a serial bus standard for connecting computer systems to external devices, and also a technical specification for input/output interfaces, widely used in information and communication products such as personal computers and mobile devices.
USB Tools — Hardware & Software
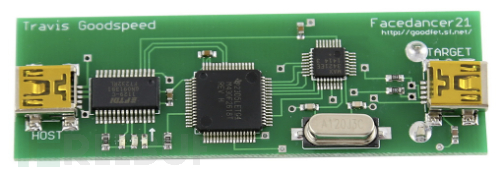
FaceDancer
FaceDancer board is a simple hardware device acting as a 'remote control' USB controller. With appropriate software, you can quickly and easily emulate USB devices using these development boards and perform Fuzz testing on USB host controllers.
6. Auxiliary Equipment
Isolation Transformer
Isolation transformer is a transformer, which is usually used for safety reasons to transmit power from AC power supply to certain equipment or equipment, while isolating the receiving equipment from the power supply. The single-phase power line consists of live wire, neutral wire, and ground wire. When multiple physically separate devices share a power line, due to the different grounding potential of the devices, a grounding loop may occur. Grounding test equipment (such as oscilloscope) may unintentionally cause a short circuit of the power supply of these devices. Moreover, high-frequency noise may be generated on the AC power line, causing problems with sensitive sensors and instruments. By correctly using isolation transformers between the power input end and the equipment, all these problems can be avoided.

Multimeter
Multimeter is a multi-purpose electronic measuring instrument, mainly used in physical, electrical, and electronic measurement fields, and generally includes functions such as ammeter, voltmeter, and ohmmeter.

7. Summary
This article briefly introduces the commonly used hardware analysis tools according to the abstract model of Internet of Things embedded devices. The content is not difficult to understand, but it can also be seen that the complexity of Internet of Things technology. Each section in the article is just an introduction, and engineers and enthusiasts can start with the use of tools, combine with practice, and thus better understand each separate field.
评论已关闭