Author: JD Technology, Liu Qingjie
1, Pain Points (*)
There are two forms of automated testing: interface automation and UI automation. UI automation is often blocked by login nodes, such as captcha, graphics, sliders, etc. Although some methods can recognize graphics and locate the position of sliders, the success rate is not high and cannot truly realize automated execution; and if the automated testing of http interfaces depends on cookies, it also cannot realize automated execution.
a, How to bypass login and realize automation execution from the front end to the back end
b, How to deal with complex login verification that cannot be automatically obtained cookies directly, requiring manual login operations, and cookies have a time limit and cannot be used for a long time
This solution will effectively solve the above problems. In the face of complex login verification and the mode with cookie expiration, short-term effective cookies can be changed to long-term effective, truly realizing UI automation and interface automation based on cookie authorization.
2, What is a cookie
Cookies are called session tracking technology, which is a small text file stored on the user's machine by the browser. Cookies are plain text and do not contain executable code. They store some information that the server needs, and each time a request is made to the site, the corresponding cookie is sent. These cookies can be used to identify user information and other purposes
3, Method of viewing expiration time
Open the browser and navigate to the website you want to view the cookies on.
Press the F12 key to open the browser's developer tools.
In the 'Debug Tools' tab of the developer tools, click the 'Storage' button.
In the 'Website Data' list on the left, click 'Cookies'.
In the 'Value' list on the right, check each cookie's 'Expires' or 'Max-Age' field. These fields show the expiration time of the cookie.
4, Cookie Mechanism
The client sends a request to the server --> The server sends an HttpResponse response to the client, which includes the Set-Cookie header --> The client saves the cookie, and then when sending a request to the server, the HttpRequest request will include a Cookie header --> The server returns the response data
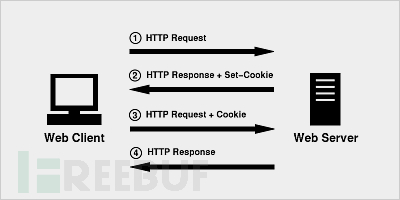
Validity Limitation: Each cookie has a validity period, the default validity period is, session level: that is, when the browser is closed, the cookie is immediately destroyed. However, we can also manually set the expiration time of the cookie when storing it.
5, Infinite Extension Scheme for Cookie Validity (*)
5-1, Precondition
a. The login node has a verification mechanism, such as SMS verification code, graphic recognition, slider, etc.
b. The cookie has a validity period, and it is necessary to log in again if the validity period is exceeded;
c. The same account will not log out or log in on multiple platforms
5-2, Implementation Principle
This scheme provides an interface through a microservice for automated calls, passes the account, returns the permanent cookie, embeds this step into the automated process, replaces the login and cookie acquisition node, and permanently extends the validity of the cookie, so that it will not expire, ensuring that the subsequent automated process can be executed normally in a permanent loop.
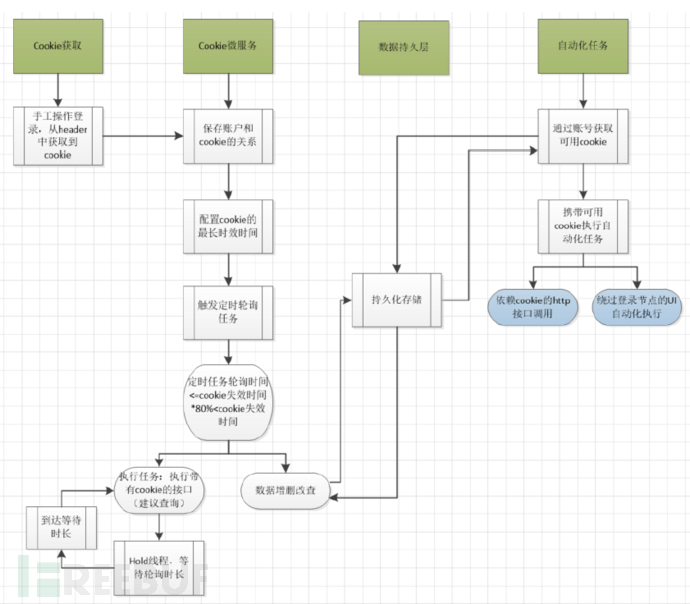
5-3, Core Process Steps
Step 1: First manually log in, obtain the cookie from the header, and store this cookie and validity value on the microservice platform (only one manual login is needed for one account, and no subsequent login operation is required).
Step 2: The microservice platform will persistently store this account, cookie, validity value, and related business interface, calculate the polling duration based on the validity value, and trigger the polling task execution. In the task, this cookie will be used to call the business interface, maintain a long session, and hold the process waiting. When the polling duration reaches, the task execution continues, and the process is held again, and the cycle continues to ensure that the session of this cookie is permanently maintained.
Step 3: Before the automated task is executed, the microservice interface is called to obtain the permanent cookie through the account, and the subsequent automated tasks are executed with this cookie.
6, Implementation Cases
Currently, through the following scheme, the purpose of one-time configuration and long-term use of cookie has been achieved.

Practical Effect Comparison
Before: When the ui automation and http interface automation are executed, the cookie expiration often occurs, and it is necessary to manually log in again and update the cookie on the automation platform, which is cumbersome and affects the success rate of automatic execution at midnight
Now: After using the above scheme, it is only necessary to manually configure the cookie on the cookie microservice platform once, and there is no need to update the cookie again in the future
7, Patent Description
https://zhuanli.tianyancha.com/811840799431036187d34680d5b10ae3
评论已关闭