
This script can help researchers collect all important information related to events, which can then be applied to scenarios such as information security forensics, threat hunting, and troubleshooting.
The current version of Get-AppLockerEventlog supports extracting the following log information:
EXE
DLL
MSI
Script
Encapsulated App deployment
Encapsulated App execution
Valuable information that can be obtained
FileType,
EventID,
Message,
User,
Computer,
EventTime,
FilePath,
Publisher,
FileHash,
Package
RuleName,
LogName,
TargetUser.
Tool download
Since this script is developed based on PowerShell, we can only use this script on Windows devices or devices configured with PowerShell environments.
Researchers can use the following command to clone the source code of this project locally:
git clone https://github.com/RomaissaAdjailia/Get-AppLockerEventlog.git
Tool usage
HunType parameter
This parameter specifies the type of event you want to retrieve and provides four values for selection.
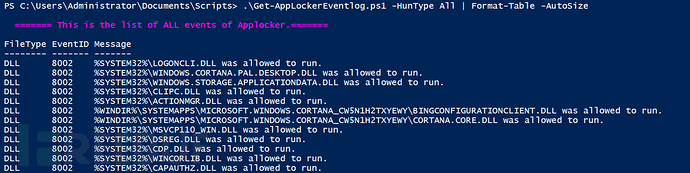
1、All
This option will retrieve all AppLocker event logs related to threat search, information security forensics, and troubleshooting. This option is also the default value for the HunType parameter:
.\Get-AppLockerEventlog.ps1 -HunType All
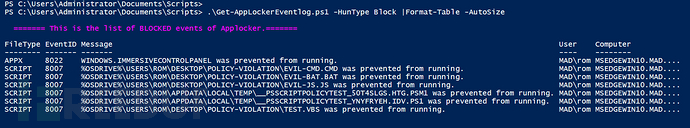
2、Block
This option will retrieve all events triggered by applications blocked by AppLocker. This type of event log is crucial for threat search or security forensics and has a high priority because it indicates an attempt at malicious behavior or suggests that previous malicious activities have attempted to bypass defense mechanisms:
.\Get-AppLockerEventlog.ps1 -HunType Block |Format-Table -AutoSize
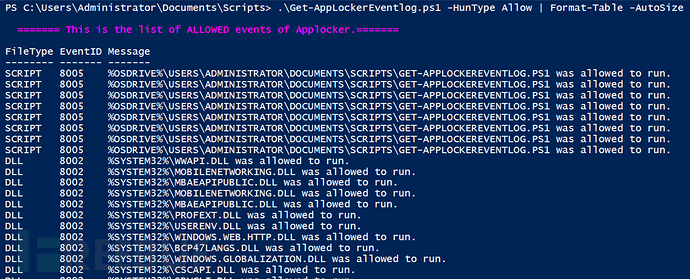
3、Allow
This option can retrieve all events triggered by applications allowed by AppLocker. This log information is very important for threat search or security forensics, as well as application behavior monitoring, because it can help us detect any possible bypasses or configuration errors:
.\Get-AppLockerEventlog.ps1 -HunType Allow | Format-Table -AutoSize
4、Audit
If the enforcement mode (audit mode) is enabled, the tool will retrieve all events generated when AppLocker blocks applications. These events can help us check for misconfigurations and malicious operations that occurred during the audit phase:
.\Get-AppLockerEventlog.ps1 -HunType Audit
Output results
The analysis output of the tool will be displayed directly on the screen:
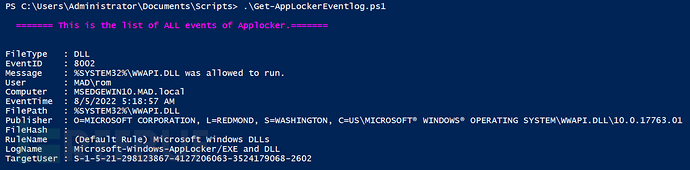
At the same time, the tool will output the results to a CSV file: AppLocker-log.csv
License agreement
The development and release of this project followMITOpen source license agreement.
Project address
Get-AppLockerEventlog:【GitHub Gateway】
Reference materials
https://medium.com/@elromaissa2/diving-in-applocker-for-blue-team-57a7328ce5c0
评论已关闭