Preface
Usually, when performing virus analysis, a well-configured virus analysis environment is required. FireEye has also released a pre-configured virtual machine, but the installation process of the virtual machine is very slow, so it is better for us to configure it ourselves. Below, we will elaborate on the configuration of the virtual machine and the basic principles of virus analysis, which is the first step in virus analysis.
Virtual machine environment configuration
Taking VMware as an example, explain the relevant operations of the virtual machine
System preparation

Download and install the operating system as follows in the virtual machine, the process of installing the system in the virtual machine is the same as the normal installation, but it is necessary to ensure that the disk'sSize is sufficient, to ensure that there is no disk shortage when taking snapshots later:
- Windows 7 system SP1 and above
- Windows 10 system
Basic settings
- Do not connect the USB flash drive to the virtual machine, or set the virtual machine to prevent automatic connection of the USB flash drive;

- Select Virtualization Intel VT-x/EPT or AMD-V/RVI (Settings - Processor)
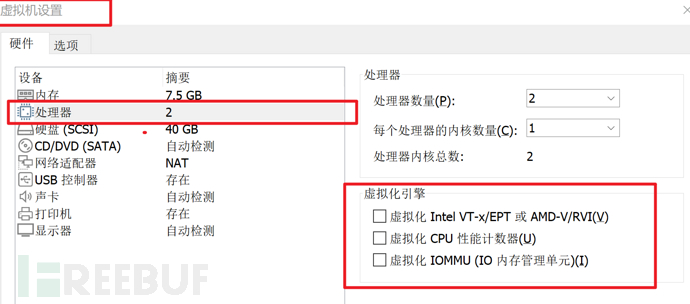
- File options -> Show file extensions and hidden files; View -> Details: it is to directly see the file suffix and other information, in order to prevent file forgery and deception.
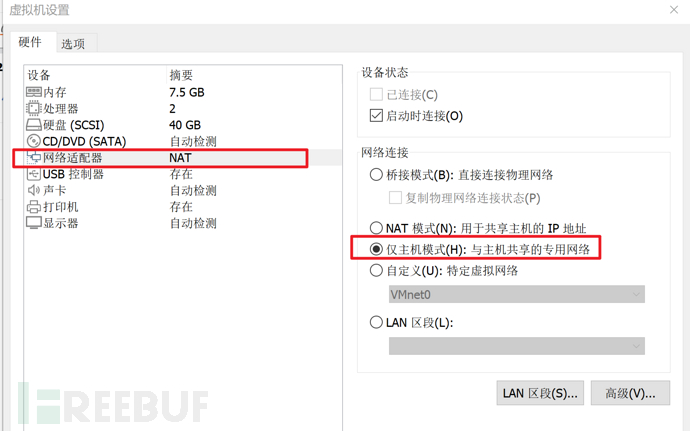
- Network requirements: host-only or disconnected
Basic operations of the virtual machine
1. Before analyzing malicious softwareBefore analysis, analysis toolsAfter installation,Create a snapshotThe purpose is to be able to recover to the state before infection in the future; snapshot
The process of creating a snapshot is as follows:
Right-click to take a snapshot:
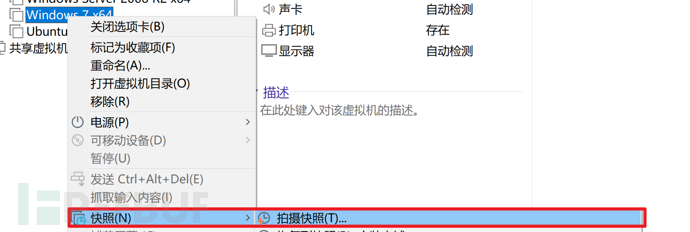
Take a snapshot and fill in the snapshot description, as shown in the following example:

2. Each time you need to install a new tool, first restore a snapshot, then install the tool, and create a new snapshot again (PS: according to your needs, you can also remove the redundant snapshots in the middle)
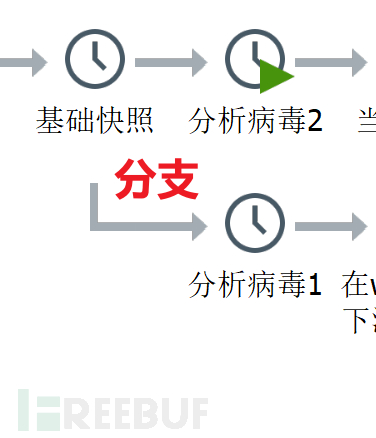
3. Snapshots can be rolled back to the base snapshot and then take a snapshot, which can have branches: you can analyze another when one analysis is not finished
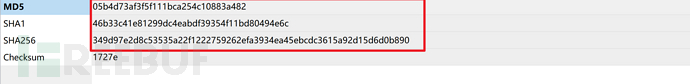
4. Samples can only be queried by hash value, and it is not allowed to upload samples. If you use pebear to open a virus, you can see the hash value:
Tool Installation
Virus analysis cannot do without useful tools. Here are some recommended useful analysis tools of various types.
PE-related tools
Check the PE information of the program, and have a preliminary understanding of whether the program is packed or not
ExeinfoPe
LordPE
PE-bear
pestudio
Dynamic debugging tools
When there are unclear details during virus analysis, use dynamic debugging to understand the program execution process step by step; or, viruses often encrypt data, and execute shellcode after decryption. At this time, dynamic debugging can directly obtain the decrypted shellcode.
x64dgb: A powerful tool for analyzing PE files, an open-source project with a good community environment
dnSpy: A .net language decompilation tool
WinDbg: A kernel mode and user mode debugger included in Windows debugging tools
Ollydbg: A well-known debugger for I love cracking, recently released in 64-bit
Static analysis tools
Static analysis tools are needed to decompile the source files and view the implementation of function functions and the program logic flow during virus analysis.
ida pro: A static decompilation master
Binary Ninja: As above
Jeb Decompiler: Android decompiler
jd-gui: As above
Behavior analysis tools
When a virus is executed, it has a series of operations, including registry, file creation, communication, etc. Behavior analysis tools can capture these behavior information, helping us understand the behavior of the virus.
ProcessExplorer
ProcessMonitor
FireBlade
SysTracer
Hexadecimal editor
010Editor
Network-related tools
inetsim: A tool for simulating virus communication in the Linux environment
wireshark: Capture traffic packets to obtain virus communication
Other software
CyberChef: A program for encryption, encoding, compression, and data analysis
Sublime Text 3: A text editor with virus analysis related plugins
Stripper
XVolkolak: Can decrypt most shells, and it is convenient to strip.
Note: After installing these tools, you need to take a basic snapshot.
Summary
This article mainly introduces the basic environment construction of virus analysis, among which the steps of taking snapshots and the settings are relatively important, providing readers with a way of thinking for taking snapshots.
In the subsequent articles, we will explain the practical operation of virus analysis for each tool.
Declaration
The original intention of this article is to share knowledge about network security. Please do not use technology to engage in any behavior that危害网络安全. Any direct or indirect consequences and losses caused by the dissemination and use of the information provided in this article are borne byUsersI am responsible for it, and it has nothing to do with the SpaceSec security team or the author!
Part of the learning content in this article comes from the internet, and the internet is回馈. If there is any copyright issue, please contact us to delete it.
评论已关闭