Introduction
In our daily work, we often monitor malicious domain name requests from office networks. However, due to the lack of assistance from EDR tools, the efficiency of locating these malicious requests is often low. Therefore, we have summarized some methods that can help improve the efficiency of location, including the use of open-source tools and the use of system logs for analysis. These methods can all help us locate the processes that send malicious domain name requests from office networks more quickly and accurately, and improve our security response capabilities.
MacOS Edition
Security Tools
When considering this issue, the first thought is to use existing security tools, so I researched several tools with network monitoring capabilities, and below are the actual usage effects of two tools that meet the requirements.
FireBlade for Mac

FireBlade provides the ability to monitor processes for network activities.
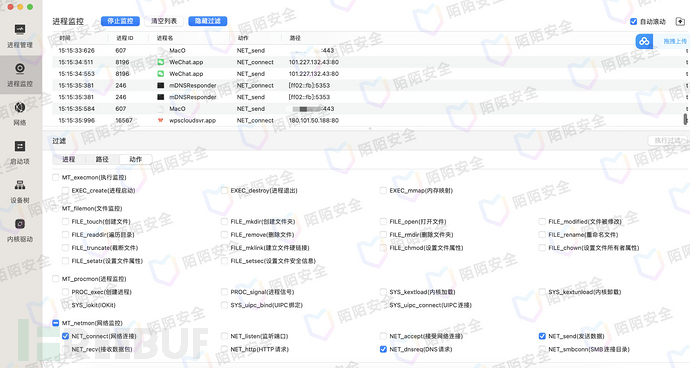
In actual testing, enabling the filtering of DNS requests does not produce any output. However, for fixed domain names that require DNS resolution, you can assist in locating by enabling monitoring and filtering specified IPs.
DNSMonitor
DNSMonitor is an open-source security tool that uses Apple's Network Extension Framework to monitor DNS requests and responses.
Project address:https://github.com/objective-see/DNSMonitor
Download address:https://objective-see.org/products/utilities.html
Usage:
Unzip the software to the Applications directory, run it, and allow it to load system extensions and monitor dns traffic to use it.
DNSMonitor.app/Contents/MacOS/DNSMonitor -h
DNSMonitor usage:
-h or -help Display this usage information
-json The output is formatted as JSON
-pretty The JSON output is 'pretty-printed'
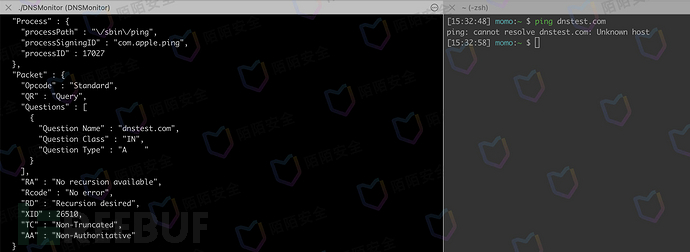
The monitoring effect is as follows, which can obtain the program path and process ID of the program executing dns requests, and can perfectly match the requirements.
Enable and query the private data logs of MacOS unified logging
macOS unified logging is a new logging system introduced for the first time in Mac OS X 10.12 Sierra. It integrates multiple log sources into a unified log file, including system logs, application logs, and security logs, etc. It includes DNS request logs, but they are recorded as private data logs by default and need to be manually enabled. Different methods of enabling are available in different system versions after Sierra.
From Sierra to Mojave
Run the following command in the terminal to enable it.sudo log config --mode "private_data:on"
Catalina <10.15.3
The above method is no longer valid in Catalina. Researcher Saagar Jha has provided aPrivateLogsThe tool is used to enable private data logs.
Run the following command in the terminal to enable it.
$ PrivateLogs enable
$ PrivateLogs status
enabled
Catalina 10.15.3+
In higher versions, you can open private data logs by installing a description file.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>ManagedClient logging</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>com.apple.logging.ManagedClient.1</string>
<key>PayloadType</key>
<string>com.apple.system.logging</string>
<key>PayloadUUID</key>
<string>ED5DE307-A5FC-434F-AD88-187677F02222</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>System</key>
<dict>
<key>Enable-Private-Data</key>
<true/>
</dict>
</dict>
</array>
<key>PayloadDescription</key>
<<string>Enable Unified Log Private Data logging</string>
<key>PayloadDisplayName</key>
<string>Enable Unified Log Private Data</string>
<key>PayloadIdentifier</key>
<string>C510208B-AD6E-4121-A945-E397B61CACCF</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>D30C25BD-E0C1-44C8-830A-964F27DAD4BA</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
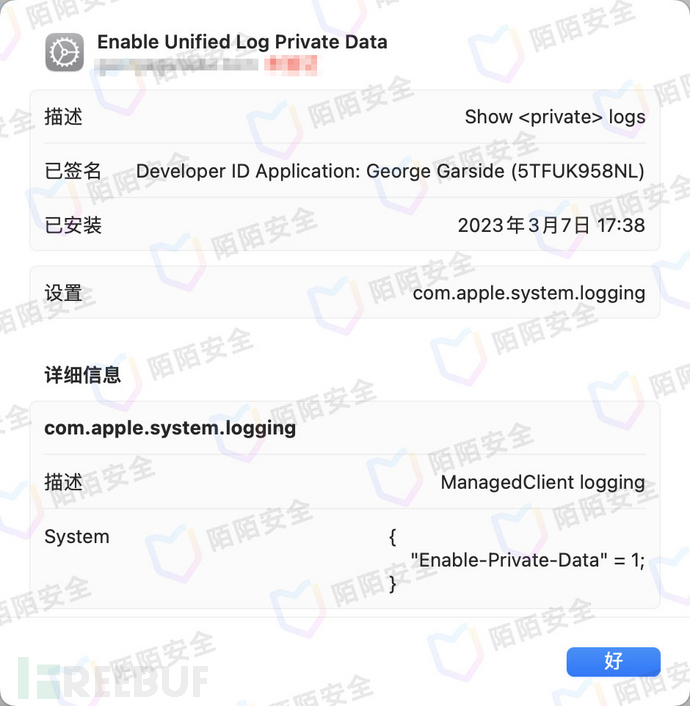
The effect is as follows:
Log query method
Run the following command in the terminal to check if it has been successfully enabled
$ sudo log config --status
System mode = INFO PRIVATE_DATA
Run the following command in the terminal to query logs from the past hourlog show --last 1h --predicate 'eventMessage CONTAINS[cd] "dns"' |grep "mDNSResponder" |grep "START PID"
The effect is as follows: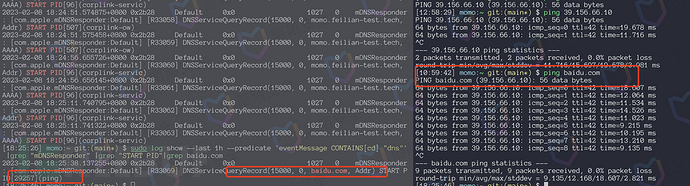
Note: Only logs that have enabled private data logging can be queried, historical logs are still displayed in the form of private logs. In actual testing, only some private data logs were displayed in Ventura, and due to limited resources, further investigation was not followed up.
Summary
The above methods have their own advantages and disadvantages. DNSmonitor can perfectly solve the problem mentioned at the beginning, while FireEye's monitoring capabilities in this scenario are slightly inferior to DNSmonitor, but its capabilities are not limited to network monitoring. If you do not want to use third-party tools, you can refer to the corresponding method in the article above according to the system version to enable private data logs, and if you do not trust third-party description files, you can also refer toofficial documentationwritten by yourself
Windows section
Microsoft's Sysmon 10 integrates DNS query record functionality, which will allow Sysmon users to record DNS queries performed by processes on monitored computers. From the functional introduction, it meets the needs.
throughofficial download addressdownload, execute in the cmd command windowsysmon.exe -accepteula -i sysmonconfig-export.xmlcommand to install, configuration file from the Github open source projectsysmon-config.
After installation, you can view the DNS request logs in the Event Viewer under Application and Services Logs/Microsoft/Windows/Sysmon/Operational, with EventID 22.
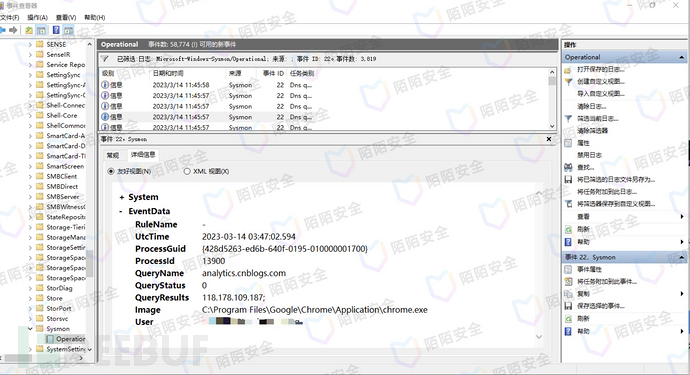
If you want to query a specific domain, you need to edit the XML query statement to filter it. Here is a PowerShell script that can query the specified domain and the user and process ID that initiated the DNS request within a specified time period.
Query logs for events with EventID 22 and domain www.baidu.com within the past 1 hour
$xml ='<QueryList>
<Query Id="0" Path="Microsoft-Windows-Sysmon/Operational">
<Select Path="Microsoft-Windows-Sysmon/Operational">*[System[(EventID=22)
and TimeCreated[timediff(@SystemTime) ≤ 3600000]]] and *[EventData[Data[@Name="QueryName"] and (Data="www.baidu.com")]]</Select>
</Query>
</QueryList>'
$events = Get-WinEvent -FilterXml $xml
$i=0
while ($i -lt $events.length) {
$time=$events[$i].TimeCreated
$dns=[regex]::matches($events[$i].Message, 'QueryName:(.+)') | %{$_.Groups[1].Value.Trim()}
$id=[regex]::matches($events[$i].Message, 'ProcessId:(.+)') | %{$_.Groups[1].Value.Trim()}
$user=[regex]::matches($events[$i].Message, 'User:(.+)') | %{$_.Groups[1].Value.Trim()}
Write-Host $time, ' QueryName:'$dns' ','ProcessId:'$id' ','User:'$user
$i++
}
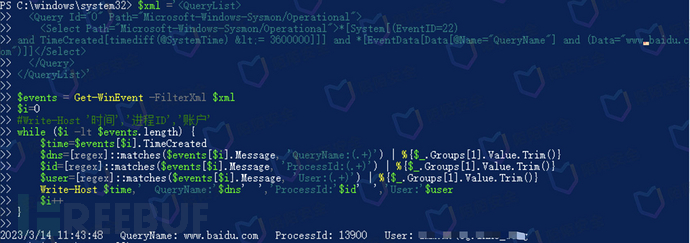
The execution effect is as follows:
Reference
https://github.com/SwiftOnSecurity/sysmon-config
https://huorong.cn/info/1620802825658.html
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
https://georgegarside.com/blog/macos/sierra-console-private/#google_vignette
https://saagarjha.com/blog/2019/09/29/making-os-log-public-on-macos-catalina/
评论已关闭