Written in advance
Continuing the content of the previous article, to start the arbitrary chatter about the functions of endpoint security products. Let's talk about endpoint assets first.
Compatibility
Under the impact of various endpoint security protection products, users are more inclined to consider purchasing a comprehensive integrated endpoint solution. Users only need to choose the most suitable solution for their environment. When considering endpoint security products, in addition to considering technical issues such as functionality, performance, scalability, stability, and security, it is more urgent to understand whether the product can be deployed on various endpoints in the enterprise environment, and whether it will damage the stability and security of the endpoint itself. If you want to be a hero, you can't even enter the door, let alone do anything else.

Think about what endpoints are described in the first article, and list the compatibility issues that endpoint security products need to face:
agent client program
The performance of the client program installed and deployed on the operating system directly affects the overall feeling of the product.
The cross-certificate recognized by Microsoft has expired, and the driver software is facing the problem of being unable to be signed. After April 2021, the existing third-party code signing certificates can be used to sign non-kernel driver programs. The code signed with these certificates can only run in user mode and will not be allowed to run in the kernel unless it has an effective Microsoft signature. After July 1, 2021, WHQL signatures must be used to sign kernel mode driver programs. Affected systems: WINDOWS XP, WINDOWS 7, WINDOWS SERVER 2008 and below. (The above is excerpted from)Anxin Laboratory(Microsoft also has certain remedial measures:)
https://new.qq.com/omn/20191231/20191231A07HLQ00.html
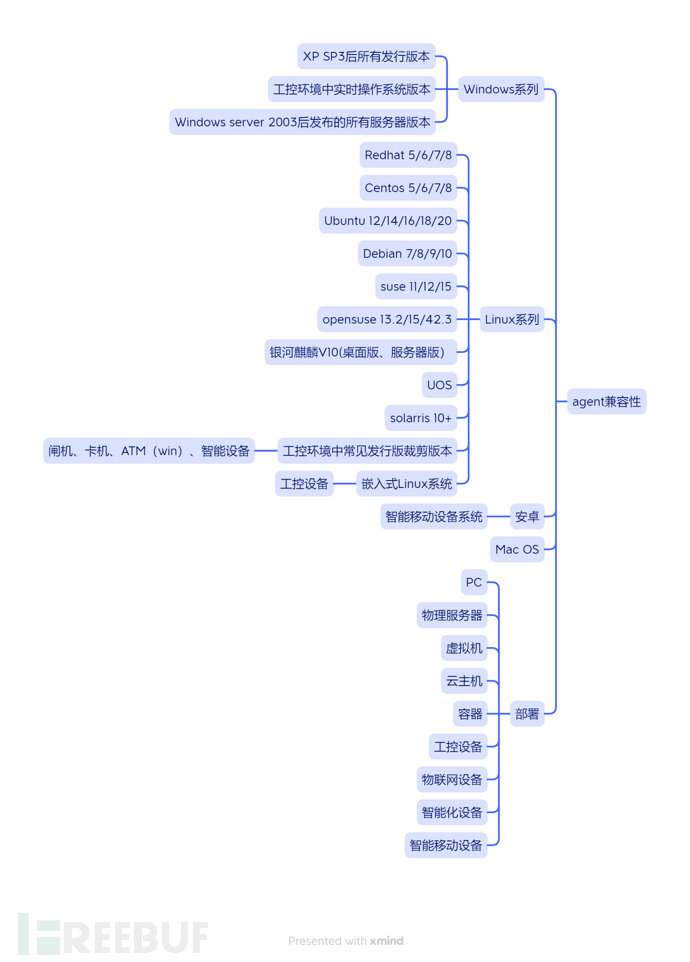
Currently, a considerable number of domestic industry customers still use Windows 7 systems and some XP systems. Windows Server 2003 and 2008 can also be encountered at any time, so it is a must for an endpoint security product to provide an overall solution covering the operating system, which is a labor-intensive task. To involve real-time operating systems in production, industrial control, and IoT environments, it is necessary to consider; for power and financial industry consolidation systems, it is necessary to consider; if your customers are more concerned about small machine security, you also need to consider AIX, HP, and solarris; it is best to support various major Linux distributions, but considering the return on investment, it is possible to set a lower limit such as kernel version 2.6 or above. If it is lower, the return on investment is not high, as no one will spend 1-2 months developing and adapting for a few machines. There is a demand for Mac OS, such as DiDi and Baidu, where employees use Apple, but I think the endpoint security company will not outsource, but organize some people to develop it themselves, and they can accumulate whatever functions they want. If there are too many points of procurement, it will be a lot of money (there is a legend that DiDi has developed a DLP to support 8W DiDi employees); mobile devices (Android, Apple) such as Zhi Zhuan Yi are mainstream in the domestic market. However, in the past two years, other manufacturers have also considered adapting to Android, but it is not clear whether the market is willing to spend money to continue to develop. If there is an APP with a similar PC EDR function on Android, it can be checked what each APP does, and control the advertisements and stealthy actions, which is not very good.
Management end
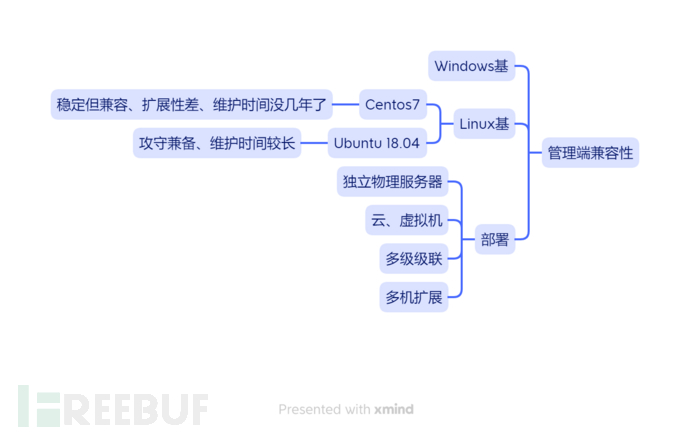
The management end has seen some installed on Windows server, but now they should be very few, mostly based on Linux, although there are various reasons for using different versions.
Endpoint asset
Theoretically, endpoint security products cannot provide security protection for unrecognized assets, nor can they perform security detection on unrecognized assets and take subsequent response actions. The product must identify all assets to make all assets visible, so that they can be classified, configured, and monitored.
1. What are the endpoint assets? Which endpoint devices, operating systems, applications, and services within the management scope are used? This includes continuously monitoring and improving the security status of these assets during vulnerability and threat detection.
2. Who is using it? Which accounts, credentials, and human entities access and use endpoint assets, including automatic operations performed by processes, services, and other data assets used.
3. What is happening to the assets on the endpoint? It is necessary to have a deep understanding of the access patterns and interaction messages between assets.
4. How are data assets protected? What are the protection strategies for information during storage, transmission, and use?
Build an endpoint security system with assets as the core, and lay a solid foundation for security construction from asset management. Identifying a detailed asset list is the basic premise of security protection, as it is impossible to protect assets that have not been identified. The scope and granularity of asset identification determine the detection, analysis, response, and display content of other functions. The use and change of asset status are basic functions of asset management. Asset management is the main input of the entire system and also the first item for users to check the capabilities of endpoint products.
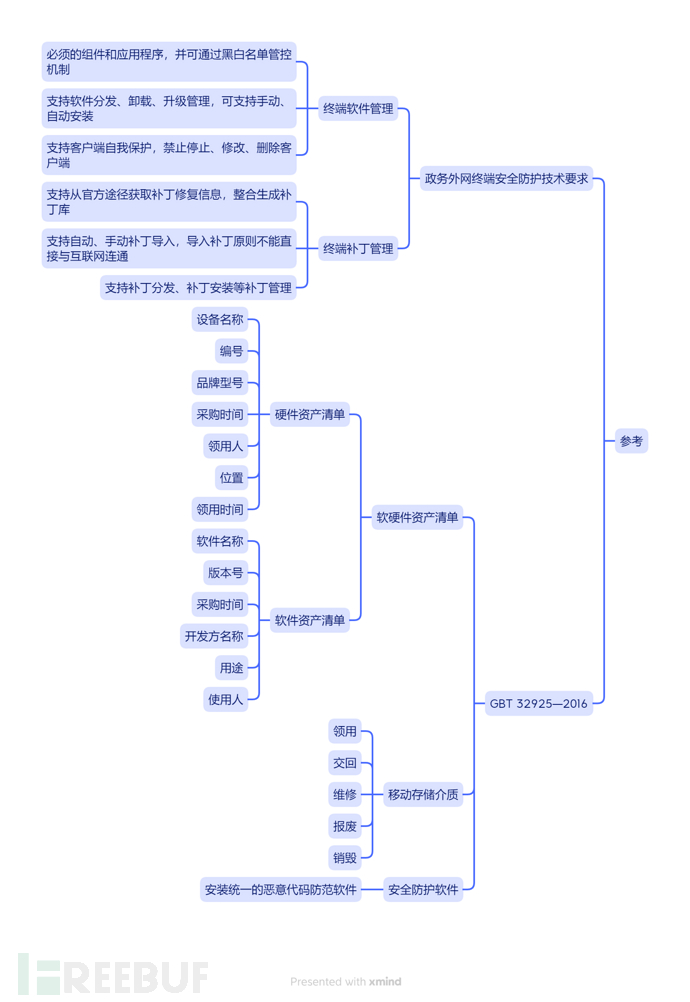
List of functions that should be considered:
System asset | Hardware asset information: Automatically collect hardware asset information of all registered terminals in the network, including device provider, model, CPU, memory, hard disk (partition status, size), motherboard, graphics card, sound card, network card |
System Information: automatically collect system information of all registered terminals in the network, including operating system type, version, system language, MAC address, IP address, gateway, terminal name, and other information, system installation date, environment variables, kernel module | |
Discovery of unregistered terminals: automatically discover unregistered devices in the network, can display unknown device name, IP, MAC address, and network card manufacturer information, can be marked as known unregistered host through remark tags management | |
Application Assets | Application software, database, middleware, WEB service |
Name, version, listening port, port mapping to process | |
Container | |
Asset Changes | Record changes for key assets of the host (terminal name, operating system (major version upgrade), language, CPU, hard disk, memory, network adapter, IP address, MAC address) |
Administrators can specify key asset settings change alerts | |
Record changes for host account information (new account, deleted account, user group change) | |
Change of application software (addition, deletion, modification) | |
Real-time Information | Real-time process information of the host (process name, PID, PPID, start time, path, CPU, memory, user) can view detailed information of specified processes and stop process operations |
Asset Grouping | Add group, edit group, move group, delete group, filter unassigned groups, close group management |
IP automatic grouping: automatically classify the host that logs on within the set IP range into the corresponding group | |
Network Access | Record of host access IP and port (file path, category, destination IP, destination port, time) |
Reverse lookup domain name of access IP | |
Online Track | Probe online and offline time (including probe itself safety and status detection mechanism, such as host normal operation, probe abnormal offline) |
External Device Assets | USB external devices, CD-ROM, serial port, parallel port, 1394, infrared, Bluetooth, smart card readers, PCMCIA; CD-ROM, floppy drive, SD adapter, modem, image recording equipment, infrared devices, smartphones, vendor-customized devices, vendor security USB flash drives |
Manage external devices, capable of monitoring usage time and device type, setting whitelist and blacklist for external devices, and recording usage status | |
MDM Integration | Query the Mobile Device Management system to add asset attributes |
Supplementary
There are two reference contents:
2. Differences between GDPR and DPDP Act
Endpoint Security Discussion (Twelve) - Wazuh Discussion (Part One)
Endpoint Security Discussions (V) Some ideas
Endpoint Security Discussions (Fourteen) Wazuh White Paper (Part 2)
Endpoint Security Discussions (Part 1) Overview
6 Main Quality Assurance of Buried Points -- Buried Point Testing
Knowledge Point 5: Bypass CDN through Space Engine & Use Tools for Global CDN Bypass Scanning
评论已关闭