Introduction to cloud functions
Cloud functions (Serverless Functions) are an event-driven computing service that allows developers to write and deploy code without managing underlying server resources. Through cloud functions, developers can focus on the implementation of business logic and do not need to worry about infrastructure operations and scaling issues. It belongs to Serverless architectureA form of, usually closely integrated with cloud platforms (such as AWS Lambda, Alibaba Cloud Function Compute, and more).
Characteristics of cloud functions
Serverless management:Users do not need to manage or maintain servers. The cloud platform automatically handles the execution environment, resource allocation, load balancing, and automatic scaling of functions.

Pay-as-you-go:The billing method of cloud functions is usually based on the actual computing resources and time consumed, charging based on the number of calls and execution duration. This pay-as-you-go billing model helps users avoid unnecessary resource waste and is particularly suitable for handling intermittent or low-latency requests.
Event-driven:Cloud functions are usually triggered by certain events, such as HTTP requests, file uploads, database changes, message queues, and more. Developers can write code logic based on these events.
Automatic scaling:Cloud functions can automatically scale up or down resources based on the number of requests to meet different load requirements. It can quickly expand when the number of requests increases and automatically reduce when the load is lightened.
Fast deployment and iteration:Developers can quickly upload function code to the cloud platform and make it effective immediately. For frequently changing business needs, cloud functions also provide a more flexible iterative approach.
Application scenarios of cloud functions
API backend:Build and run lightweight RESTful APIs or web services.
File processing:File upload, image processing, video transcoding, and more.
Data processing:Process data from sources such as streaming media, logs, message queues, and more.
Automated tasksScheduled tasks, email notifications, data synchronization, and other automated operations.
Internet of Things (IoT)Process data uploaded by devices or control commands.
Event-driven computingRespond to user actions, monitor events, system notifications, etc.
Deploy server-side service
Choose Tencent Cloud for demonstration: https://console.cloud.tencent.com/scf/index
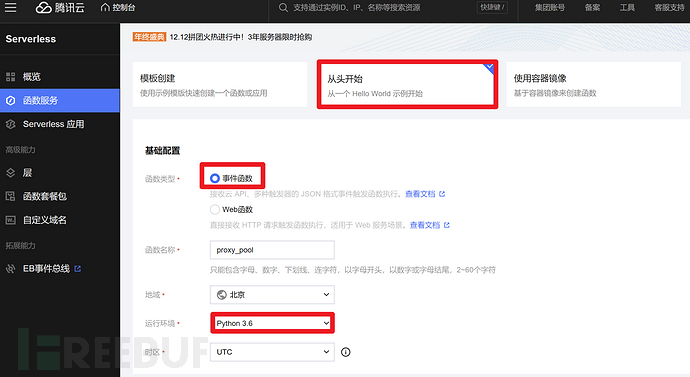
Create a new function
Choose to start from scratch, event function, the runtime environment is python3.6, others can be filled in arbitrarily
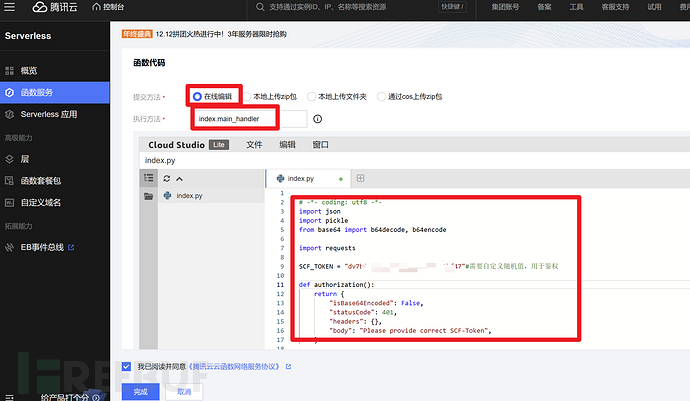
Configure function code
Choose online code editing, write server-side code
# -*- coding: utf8 -*-
import json
import pickle
from base64 import b64decode, b64encode
import requests
SCF_TOKEN = "TOKEN" # need to customize with a random value, for authentication
def authorization():
return {
"isBase64Encoded": False,
"statusCode": 401,
"headers": {},
"body": "Please provide correct SCF-Token",
{}
def main_handler(event: dict, context: dict):
try:
token = event["headers"]["scf-token"]
except KeyError:
return authorization()
if token != SCF_TOKEN:
return authorization()
data = event["body"]
kwargs = json.loads(data)
kwargs['data'] = b64decode(kwargs['data'])
r = requests.request(**kwargs, verify=False, allow_redirects=False)
serialized_resp = pickle.dumps(r)
return {
"isBase64Encoded": False,
"statusCode": 200,
"headers": {},
"body": b64encode(serialized_resp).decode("utf-8"),
{}
评论已关闭