
1. Basic statement
- Data security is different from traditional security, and the objects that need to be protected in data security are much larger than those in traditional security. Therefore, the first thing to face in the construction of data security is data classification and level. Only through data classification and level can we achieve targeted protection and provide object basis for data desensitization and encryption.
- This article includes the concepts, processes, precautions, and solutions of data classification and level, and introduces what needs to be done and the possible problems that may be encountered in classification and level from the shallow to the deep. It can help enterprises find a suitable solution when they are at a loss when facing data classification and level for the first time, and inform enterprises in advance of the possible problems and solutions they may encounter in the actual classification and level process.
- This article lists the data classification and level specifications of the automotive, financial, medical, and telecommunications industries, and all are equipped with official links, saving a lot of time in searching for classification and level reference materials.
2. Conceptual standards
- Classification: based on the data'sSource, content, and usageClassify data;
- Classification: according to the data'sValue, content sensitivity, impact, and distribution scopeDifferent levels of sensitivity classification for data
- Function:
- It is convenient for enterprises to take corresponding security control measures for control
- It can minimize the use of sensitive data, and assign designated data to designated users
- It is convenient for enterprises to assess losses and the scope of impact when data leakage occurs
- Level division:
- Top secret
- Secret
- Confidential
- Privacy
- Sensitive
- Public
- Division basis:
- Data usage
- Data value
- Data lifespan
- Leakage hazards
- Legal provisions
3. Technical process
(i) System support
- Article 21 of the Data Security Law of the People's Republic of China:The state establishes a data classification and level protection system, classifies and protects data according to the importance of data in economic and social development, as well as the degree of harm caused to national security, public interests, or the legitimate rights and interests of individuals and organizations once the data is tampered with, destroyed, leaked, or illegally obtained or used. The coordination mechanism for national data security work coordinates and coordinates the relevant departments to formulate an important data catalog and strengthen the protection of important data.
- data related to national security, the lifeline of the national economy, important people's livelihood, and major public interests belong tonational core dataimplement more stringent management systems.
- Each region and department shall, in accordance with the data classification and level protection system, determine the specific catalog of important data in their respective regions, departments, and related industries and fields, and give priority protection to the data listed in the catalog.
- important datarefers to data that, once leaked, may directly affect national security, economic security, social stability, public health and safety, such as non-public government information, large-scale population, genetic health, geography, mineral resources, and so on. Important data generally does not include information on corporate production and operation and internal management, as well as personal information
- Based on the law:
- 《The Data Security Law of the People's Republic of China》
- 《The Personal Information Protection Law of the People's Republic of China》
- 《Data Security Technology Data Classification and Grading Rules》:GB/T43697-2024, is the latest version of the national standard data classification and grading specification
- 《Industrial Data Classification and Grading Guide (Trial)》
- 《Information Technology Big Data Data Classification Guide》
- 《Network Security Standard Practice Guide - Network Data Classification and Grading Guidance》
- 《Automotive Data Security Management Several Provisions (Trial)》
- 《Securities and Futures Industry Data Classification and Grading Guidance》
- 《Basic Telecommunications Enterprise Important Data Identification Guide》
- 《Basic Telecommunications Enterprise Data Classification and Grading Method》
- 《Energy Big Data Data Classification and Grading Guidance》
- 《Guangdong Province Health Medical Data Security Classification and Grading Management Technical Specification》
(2) Formulate specifications
- Enterprises can formulate enterprise data classification types in accordance with the aforementioned legal provisions and the characteristics of enterprise data, and can be classified according to the following references:
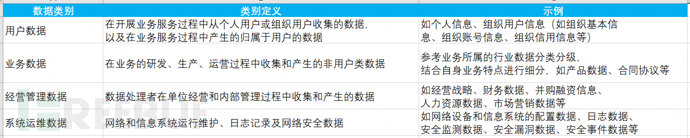
- Enterprise classification needs to be judged by combining personal reputation influence, enterprise business influence, enterprise reputation influence, national security influence, social order influence, and public interest influence.
- Common considerations for data field identification, such as
- Industry fields;
- Business lines, business categories;
- Business operations and activities;
- Process links;
- Content themes;
- Fields related to national security, economic operation, social order, and public interest, etc.
- Common considerations for data group identification, such as
- Crowds;
- Groups, units, organizations;
- Networks, information systems, data centers;
- Resources, raw materials, materials;
- Components, equipment;
- Projects;
- Infrastructure;
- Groups related to national security, economic operation, social order, and public interest, etc.
- Common considerations for data area identification, such as
- Administrative divisions;
- Specific areas;
- Geographical environment;
- Important places;
- Cyberspace;
- Areas related to national security, economic operation, social order, and public interest, etc.
(3) Implement scanning
- Scanning generally uses two methods for scanning:
- Regular expression matching: The most common scanning method, matching data features through writing regular expressions to achieve identification
- Machine learning: Input standard rules and examples of enterprises, train the model through machine learning, and achieve automatic matching
- Scan process:
- Enter the database connection information (generally including IP, port, database type, database account, and database password)
- Scan and identify the database name, table name, table comments, field name, field comments
- Extract data examples
- Perform regular expression matching on the obtained database name, table name, table comments, field name, field comments, and data examples to achieve classification and grading.
(4) Review the results
- Manually review the results that have been classified and graded, mainly to determine whether the data field names and field comments correspond to the classification situation. If they correspond, it indicates that the rules are correct; if not, the matching rules need to be modified.
- If the enterprise initially implements data classification and grading, it needs to manually review the scan results. If the enterprise has fully optimized the scan rules after scanning, then only spot checks are needed, and a certain proportion of classification and grading results are extracted from each result table for review to judge the accuracy of the scan.
(5) Modify Matching
- When there is a mismatch, the classification and grading rules need to be modified.
- The following principles should be followed when modifying matching rules:
- Gradual improvement: modifying rules may not be able to be perfected at one time, and continuous modification and improvement can be used to perfect the rules.
- Targeted modification: targeted modification is made, and multiple categories are targeted for modification, which can achieve twice the result with half the effort.
(6) Rescan
- After the rules are modified, a rescan is required to determine whether the rules are effective and whether they are correctly matched.
- When rescan is performed, focus should be on the locations where errors occurred previously, and there is no need to conduct a full review again.
- When re-examining, if no other issues are found, the scan results can be regarded as the final scan and version management can be implemented.
(7) Result Utilization
- Classification and grading is not the ultimate goal, and the main considerations for the utilization of the following results are classified and graded.
- Display of classification and grading results, showing the data types and sensitivity levels of the database data of the system.
- Data grading control, implement hierarchical control for data of different levels, focus on monitoring databases containing core data and important data to prevent data leakage.
- Implement hierarchical authorization control, implement different authorization control requirements for data of different sensitivity levels, and require approval from the company's leadership for core data and important data.
- Implement data technology control, implement different desensitization, encryption and other technical controls for data of different sensitivity levels, and share core data and important data after desensitization, and implement encrypted storage.
4. Matters needing attention
- Even if the enterprise spends a lot of manpower and material resources to improve and modify the matching rules, it is impossible to be 100% accurate, and in fact, it is not necessary to be 100% accurate.
- Attention should be paid to the realization of the purpose of data classification and grading. When formulating the classification and grading plan at the beginning, the purpose of classification and grading should be considered. And keep moving towards this goal continuously, while also being targeted and grasping the main purpose to achieve classification and grading, which can save time and money for the enterprise.
- Version control is required for the classification and grading results of data. Since the data in the database is not static, when system iteration occurs, it is necessary to compare and differentiate the scan results of different versions.
- The encryption of data storage will affect the classification and grading scan results. If classification and grading as well as encryption and desensitization can be implemented on the same platform, it is the optimal solution. Not only can it compare and measure the effects of encryption and desensitization, but it can also directly use the results of classification and grading for encryption and desensitization control.
- Data security classification and grading should be integrated with data governance as a part of the data management process. When data field names have been standardized, the process of identifying data becomes very easy.
最后修改时间:
Data Anonymization Technologies
上一篇
2025年03月28日 05:19
Data Compliance for Businesses Going Global: The Relationship between CCPA and CPRA
下一篇
2025年03月28日 05:42
评论已关闭