
DEScrypt uses a two-byte salt (composed of characters [a-zA-Z0-9https://www.freebuf.com/articles/database/][1]) by default, which means that we need to generate about 65536 unique rainbow tables, so the efficiency of using DEScrypt's collision cracking to find plaintext passwords will be higher.
Function introduction
1, Can crack hashes based on file or single input;
2, Support detecting CPU cores;
3, Support adjusting the number of threads;
4, Support comma-separated output files;
5, Clear and readable output display;
6, The average hash rate of 10 threads on a single CPU core is 22000 per second by default;
Tool download
Researchers can use the following command to clone the source code of this project locally:
git clone https://github.com/rek7/DEScrypt-CPU-Collision-Cracker.git
Tool compilation
Next, switch to the project directory in the command line terminal and run the following command to complete the code build:
g++ -std=c++11 src/main.cpp -pthread -lcrypt -O2 -o DEScrypt
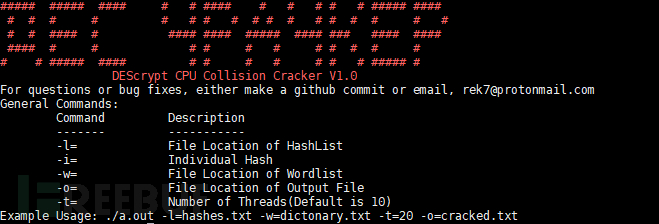
Command options
Command Description ------- ----------- -l= File path of hash list -i= Single hash -w= File path of dictionary list -o= File path of output file -t= Number of running threads (default is 10)
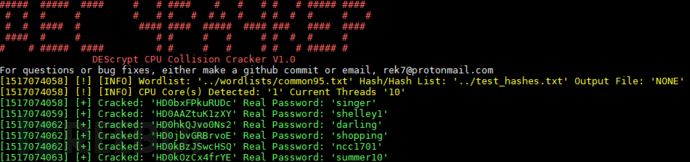
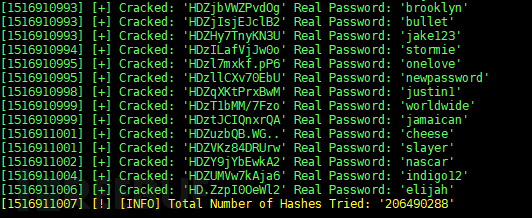
Tool operation screenshot
License agreement
The development and release of this project followMITOpen source license agreement.
Project address
DEScrypt:【GitHub Gateway】
Reference materials
评论已关闭