Introduction
With the increasing attention to data security, the necessity of data security assessment is also becoming more prominent. Usually, there are two methods of data security assessment: one is to conduct an assessment through external agencies, and the other is to conduct an assessment by internal personnel. The following article will introduce in detail how enterprises can carry out self-assessment and what aspects and materials need to be paid attention to in the process of self-assessment. Firstly, a brief introduction to the background and purpose. In recent years, data security assessment has become a requirement that needs to be carried out at least once a day. We plan to reduce security cost expenditure by alternating between self-assessment and external assessment, and to ensure that the team fully understands the current situation of the enterprise and participates in the process. During the process, there are some relatively professional materials left by external assessments, so it is recommended that a third-party organization be used for an initial assessment, and then fully collect their assessment materials as the basis and process materials for their own assessment. For the client, it may not be realistic to design it independently because the security team personnel are already few.
Work Background
The background of data security assessment mainly lies in the continuous emergence of various data sources and the exponential growth of data volume, which leads to the extensive application of data in various industries, from traditional internet applications to intelligent manufacturing, healthcare, and other fields.各国 have formulated a series of security laws and regulations for data security, putting forward higher requirements for enterprise data security. In the new era, data security risk assessment should also have the characteristics of the times, and its development must start from the fundamental perspective of the 'Data Security Law' and aim at network security risk assessment.


Work Objective
The main goal of data security assessment is to actively discover potential security risks, which is achieved based on compliance requirements and industry best practices. During the operation process, scientific, automated methods and means will be used to identify and analyze the risks faced by the organization's data assets and related processing activities such as data collection, storage, transmission, use, processing, handling, and destruction.
Specifically, the objectives of data security assessment also include the following aspects:
- It is necessary to understand the types, scale, and distribution of data and other basic situations; secondly, it is necessary to understand the situation of data processing activities.
- It should discover data security issues and risks that may affect national security, public interest, or the legitimate rights and interests of individuals and organizations;
- It should be able to discover data security issues and risks in activities such as sharing, trading, entrusted processing, and providing important data to overseas entities.
In addition, while promoting the development of key information infrastructure and digital economy, data security risk assessment also needs to further enhance the ability to ensure data security and the ability to discover risks. This aims to ensure that data security risks are controllable, which is of great significance for effectively maintaining national sovereignty, national security, and social development interests.
Work Requirements
The work requirements for data security assessment mainly focus on the following aspects:
- Risk identification is focused on data and data processing activities, focusing on security risks that may affect the confidentiality, integrity, availability, and rationality of data processing.
- It is necessary to master the overall situation of data security, find out potential data security hazards, and put forward suggestions for data security management and technical protection measures to enhance the ability to prevent attacks, destruction, theft, leakage, and misuse of data.
In addition, during the assessment process, it is also necessary to identify relevant elements such as data processors, business and information systems, data assets, data processing activities, and security measures through information research. Next, identify potential risks and hazards from aspects such as data security management, data processing activities, data security technology, and personal information protection. Finally, sort out the list of risk sources, analyze data security risks, evaluate risks as appropriate, and provide improvement suggestions.
In terms of operation, the methods of data security risk assessment include self-assessment and entrusted third-party assessment. Regardless of which method is used, it is necessary to form an important basis for the development of data security governance strategies.
At the same time, the work of data security assessment also needs to comply with the requirements of relevant laws and regulations, such as the 'Data Security Law of the People's Republic of China' and the 'Cybersecurity Law of the People's Republic of China'. This is to standardize data processing activities, strengthen data security management, ensure data security, promote the development and utilization of data, protect the legitimate rights and interests of individuals and organizations, and maintain national security and development interests.

Work Content
Data security risk assessment is conducted on the basis of information research, focusing on aspects such as data security management, data processing activities security, data security technology, and personal information protection. The framework of the assessment content is shown in Figure 1.
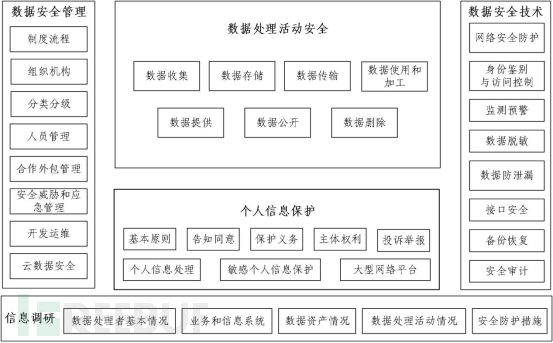
Figure 1 Framework for Data Security Risk Assessment
Figure 2Number
评论已关闭