Welcome to follow the original public account:

This series of articles is divided into 8 parts, mainly sharing the author's own experience summary in the process of corporate network security construction and operation and maintenance guarantee, including network security management, network security architecture, network security technology, and security practice, striving to fully elaborate on all aspects of corporate network security, and provide practical guidelines for corporate network security construction.
3. Network Security Domains
Overall planning and division of corporate network security, according to the comprehensive aspects of corporate network security construction, the field of network security technology is subdivided into 9 security sub-domains, among which the network security baseline is the basic domain. Through the construction and implementation of various sub-domains, the construction of the network security baseline is continuously improved, and the network security baseline is used as the standard of network security technology, implemented uniformly, and the overall defense capability of corporate network security is improved.


1. Security Baseline
Security baselines are the standard cornerstone of network security technology and the standard basis for network security technology. Based on the network security baseline, network security construction and implementation are carried out, providing security baseline implementation for specific technical implementation, including system installation, application deployment, database deployment, and so on.
In fact, security baselines have international standards organizations and best practices, namely CIS. CIS® (Center for Internet Security) is a non-profit organization, and CIS Controls and CIS Benchmarks are global standards and recognized best practices to protect IT systems and data from the most common network attacks. CIS Benchmarks provide a series of guidance manuals to protect operating systems, software, and networks that are vulnerable to network attacks. The main contents include the following:
1 | Operating Systems | Amazon Linux, CentOS Linux, Debian Linux, Oracle Linux, Red Hat Linux, SUSE Linux, Ubuntu Linux, Apple OS, IBM AIX, Oracle Solaris, Windows |
2 | Databases | IBM DB2, Microsoft SQL Server, MongoDB, Oracle Database, Oracle MySQL |
3 | Servers | Apache HTTP Server, Apache Tomcat, Microsoft IIS |
4 | Cloud | Amazon Web Services, Microsoft Azure |
5 | Containers and Virtual Machines | Docker, VMware |
6 | Mobile Devices | Apple iOS, Google Android |
7 | Browser | Google Chrome, Mozilla Firefox, Microsoft Internet Explorer, Safari Browser |
8 | Desktop Software | Microsoft Office, Microsoft Exchange Server |
9 | Network Devices | Cisco, Palo Alto Networks |
* CISAlso provides configuration assessment tools CIS-CAT Pro, currently supporting 85+ CIS Benchmarks.
* More information please refer to:https://www.cisecurity.org/cis-benchmarks/
The best practice for the establishment and implementation of the baseline is as follows:
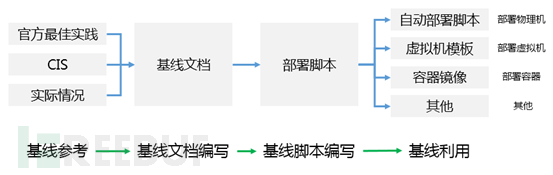
Based on official best practices, CIS, and actual specific conditions, the baseline documentation for the corresponding content is first completed. Then, while writing the baseline documentation or based on the baseline documentation, scripts are written and deployed (technical engineers can output scripts and documents at the same time when writing the baseline documentation). By solidifying the deployment methods of systems, applications, and databases through baseline documentation and baseline scripts, and forming automated deployment, based on this, combined with actual architecture, forming standard virtual machine templates or container images, and then accompanying with customized scripts, the implementation of the baseline can be completed.
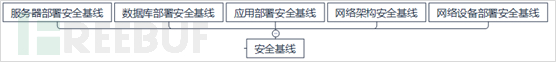
2. Physical Security Domain
The physical security domain mainly includes: the physical facilities and equipment security of access control and security, video surveillance, phone recording, and data center security in the process of enterprise operation.
Physical security is often overlooked. The threats to physical security mostly belong to the category of social attack tactics. The impact caused by neglect or poor prevention is often great and extremely destructive, such as fire in data centers, power outages, etc. For aspects such as video surveillance and data center construction, there are almost always international and national standards and requirements for specification. By constructing and implementing according to national standards and specifications, and conducting regular inspections and troubleshooting, physical security incidents can be effectively prevented. Especially as the physical carrier of application systems and data, the security of data center machine rooms needs to be particularly emphasized. Attention should be paid to strengthening physical security from the following aspects: choosing a scientifically reasonable location for data center construction; strictly controlling the access rights of the data center; through security and access control, preventing the data center from being stolen or destroyed; according to standards and specifications, constructing and constructing the data center to have functions such as lightning protection, fire prevention, waterproofing, moisture-proofing, static electricity prevention, and effective control of temperature and humidity, maintaining stable power supply, and electromagnetic protection.
From the perspective of corporate network security, departments such as security, access control, surveillance, and phone recording may not belong to the IT department or the network security department. However, this area should still receive sufficient attention from network security personnel. Once the physical defense line is breached, any higher-level protective measures will become as fleeting as clouds. In terms of physical security, the concept of disaster recovery can also be extended, which can avoid significant impacts caused by single-node physical failures through means such as establishing disaster recovery data centers and off-site backups.
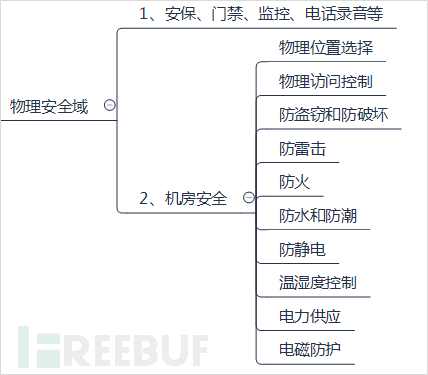
3. Network Security Domain
The network security domain mainly refers to the security of network planning architecture, network protection, and control, which is a narrow sense of network security compared to enterprise network security. It is only the security of the 'network' aspect.
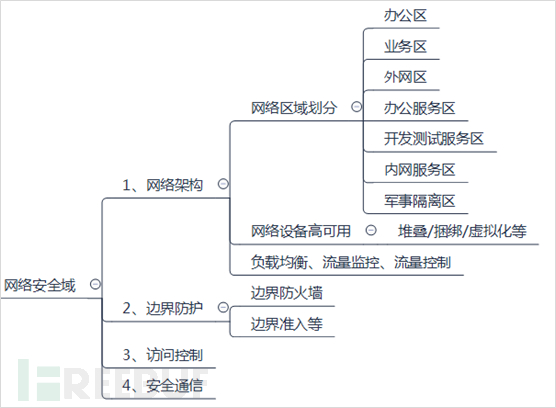
The construction of network security domain protection should be carried out from four aspects: network architecture, boundary protection, access control, and secure communication, as specified below:
- Network Architecture
The design of network architecture plays an important and decisive role in network security. The quality of the architecture directly determines the difficulty and workload of subsequent network security work. The network architecture can be divided into three parts:
①Divide Network Areas
According to actual business needs, divide the network into scientific and reasonable areas, and adopt ACL control strategies and whitelist mechanisms (even area firewalls) between different network areas to maximize the prevention of the spread of network security and network attacks. Generally speaking, the division of network areas can be referred to by these areas: office area, business area, office system service area, development and test service area, internal system service area, military isolation area (DMZ), etc. Different areas provide different services, with less coupling between areas, and policy isolation is performed.
②High Availability of Network Devices
The design and deployment of network architecture must ensure the high availability of network devices and network lines, avoiding single point failures. Core switches, access switches, and aggregation switches should be avoided as single units, and it is recommended to stack or virtualize deployment with multiple units, and the connecting lines should be dual lines to the maximum extent possible to avoid single point failures of devices and lines. If resources or design are limited, the dual units and dual lines of the core switch are the basic requirements.
③Network Load Balancing and Traffic Control
The design of network architecture should also include the planning and construction of network load balancing, traffic monitoring, and traffic control引流. While avoiding single operator failures (in fact, the situation of operator optical cable being cut often occurs), it provides efficient network services for different network users and can dynamically adjust and control according to real-time traffic monitoring.
- Boundary Protection
Boundary protection mainly includes boundary firewalls and boundary access strategies (usually whitelist mechanism). Boundaries include the boundary between enterprises and the Internet, as well as the boundaries between internal network areas, and the boundaries between enterprises and third-party cooperative units and branches. Boundary protection is the first line of defense in network security and should provide solid and strong network protection functions, capable of mitigating the vast majority of network attacks.
- Access Control
Access control mainly involves control strategies for network area access, as well as which network terminals and office terminals can access which network areas and system applications.
(4)Secure Communication
Secure communication refers to preventing the network from being monitored and tampered with during the process of network transmission. Common solutions include SSL data transmission encryption.
4、Host Security Domain
The host security domain mainly includes host server security and terminal security.
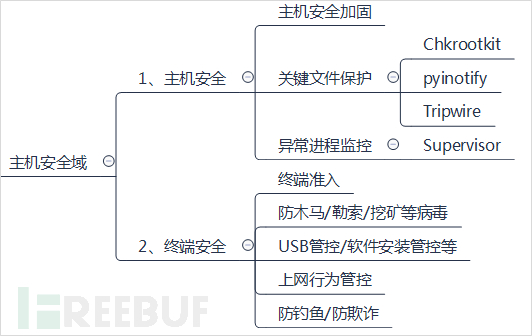
(1)Host Security
The security of the host server, based on the deployment of the host security baseline, mainly includes three contents, which can be used for host security defense:
① Host Security Hardening
Host security hardening mainly refers to strengthening the security of the operating system during the installation and deployment of the operating system, such as: kernel upgrade, ssh upgrade, root prohibition of remote login, modification of ssh port, history command time addition, prohibition of rm, etc. For more details, please refer to:
Terminal Compliance Security Settings Document (Windows platform)
https://mp.weixin.qq.com/s/ov0GvC9MmTM3i_0ixlungA
Terminal Compliance Security Settings Document (Linux platform)
https://mp.weixin.qq.com/s/YGfRLLFy7DO8GkpKCNnoog
In fact, this part is continuously improved with the security baseline. During the actual deployment process, it is enough to implement according to the baseline.
② Key File Protection
Key file protection refers to the protection of the core and important files of the operating system through technical means to prevent them from being deleted or tampered with. Taking Linux as an example (in fact, Linux is the best to do), commonly used tools include Tripwire, Chkrootkit, and pyinotify. Through these tools, illegal modifications to key files can be rejected, and alarms can also be triggered. Additionally, during the host security hardening mentioned above, there is actually another aspect that can rename the names of critical operations of the operating system, such as:
# Lock the key file system to prevent modification
chattr +i /etc/passwd
chattr +i /etc/inittab
chattr +i /etc/group
chattr +i /etc/shadow
chattr +i /etc/gshadow
chattr +a /var/log/messages
# After using the 'chattr' command, for security reasons, we need to rename it
mv /usr/bin/chattr /usr/bin/lockkeyfile
By protecting key files, the overall security of the system is improved. Additionally, when the system is attacked, its basic commands are still in a trusted state. Otherwise, in the case that the system has been compromised, it is highly possible that a command like 'cd /home' is actually 'rm -rf /home'.
③ Abnormal Process Monitoring
Record the commonly used processes in the system and fix them in the process whitelist, and monitor the system processes in real time. When a non-whitelist process is started, it will be automatically killed, and an email notification will be sent for investigation.
In fact, through host security hardening, key file protection, and abnormal process monitoring, the security and stability of the host can be greatly ensured. At the same time, by combining certain virus intrusion analysis methods and scripts, a more complete and perfect host antivirus and abnormal automatic detection system can be established.
- 终端安全
终端安全主要是指常见的办公终端、移动终端等终端设备的安全。终端安全的内容有:终端准入,允许哪些终端连接哪些系统或是设备;终端防木马、防勒索、防挖矿等;USB管控/软件安全装管控(实际上终端管理实现)、上网行为管控以及防钓鱼、防欺诈等。
终端安全关系到每一个终端使用者,提高终端使用者的安全意识和安全基本技能,也是终端安全防护的重要内容且非常行之有效的方式之一。
5、应用安全域
应用安全域主要覆盖应用系统的网络安全,特别是web应用系统,由于web应用系统多对外发布,故所面临的的安全威胁和攻击相比内网系统要高得多,甚至每时每刻都处于被扫描和被攻击中。非营利性组织开放式Web应用安全项目(OWASP)正式发布了十大最关键的Web应用安全风险:
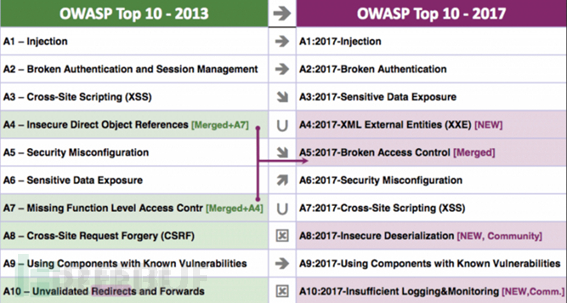
A1:2017-Injection(注入漏洞)
当不可信的数据作为命令或查询语句的一部分被发送给解释器的时候,会发生注入漏洞,包括SQL、NoSQL、OS以及LDAP注入等。攻击者发送的恶意数据可能会诱使解释器执行计划外的命令,或在没有适当授权的情况下访问数据。
A2:2017-BrokenAuthentication(中断身份认证)
与认证和会话管理相关的应用函数经常被错误地实现,从而允许攻击者破坏密码、密钥或是会话令牌,或者利用其他的应用漏洞来暂时或永久地获取用户身份信息。
A3:2017-Sensitive DataExposure(敏感数据泄露)
许多web应用程序和API不能正确的保护敏感数据,如金融、医疗保健和PII(个人身份信息)等。攻击者可能会窃取或篡改这些弱保护的数据,从而进行欺诈、身份盗窃或其他犯罪行为。在缺少额外保护(例如,在存放和传输过程中加密,且在与浏览器进行交换时需要特别谨慎)的情况下,敏感数据可能会受到损害。
A4:2017-XML ExternalEntities(XXE)XML外部处理器漏洞
许多过时的或配置不当的XML处理器在XML文档内进行外部实体引用。外部实体可用于泄露内部文件,通过使用文件URI处理器、内部文件共享、内部端口扫描、远程代码执行以及拒绝服务攻击等手段。
A5:2017-Broken AccessControl(中断访问控制)
(Break access control)
The command to limit 'which operations authenticated users can perform' is not executed correctly. Attackers can exploit these vulnerabilities to access unauthorized features and data, such as accessing other users' accounts, viewing sensitive files, tampering with other users' data, changing access permissions, and so on.A6: 2017-SecurityMisconfiguration
(Security misconfiguration)
Security misconfiguration is the most common problem. This is usually caused by insecure default configurations, incomplete or ad hoc configurations, open cloud storage, incorrectly configured HTTP headers, and detailed error messages containing sensitive information. In addition to the security configuration of all operating systems, frameworks, libraries, and applications, it is also necessary to update and upgrade the system in a timely manner.: 2017-Cross-SiteScripting(XSS)) Cross-Site Scripting
If an application can include untrusted data in a new web page without proper validation or escaping, or use browser APIs that can create HTML or JavaScript to update existing web pages containing user-provided data, a XSS vulnerability may occur. XSS allows attackers to execute scripts in the victim's browser, which can hijack user sessions, destroy websites, or redirect users to malicious websites.
A8: 2017-InsecureDeserialization(Unsecure deserialization)
Unsecure deserialization vulnerabilities usually lead to remote code execution issues. Even if deserialization errors do not lead to remote code execution, they can be used to execute attacks, including replay attacks, injection attacks, and privilege escalation attacks, etc.
A9: 2017-UsingComponents with Known Vulnerabilities(Using components with known vulnerabilities)
Components (such as libraries, frameworks, and other software modules) are run with the same privileges as the application. If a component with a vulnerability is exploited, this attack may lead to serious data loss or server takeover crises. Applications and APIs using known vulnerability components may disrupt the defense system of the application, thereby initiating various forms of attacks, causing more severe impacts.
A10: 2017-InsufficientLogging & Monitoring(Insufficient records and monitoring vulnerabilities)
Insufficient records and monitoring vulnerabilities, combined with inadequate incident response capabilities and the lack of effective integration, allow attackers to further attack the system, maintain persistence, and turn to attacking more systems, as well as tampering with, extracting, or destroying data. Most data leakage studies show that it usually takes more than 200 days to detect the occurrence of data leakage, and it is usually external organizations that discover the fact of data leakage first, rather than through internal audit processes or monitoring.
The most effective way to avoid these application security issues is to carry out secure coding and secure testing during the development of application systems, that is, to solve most of the problems at the root. The specifications for secure coding have been explained in the above chapters and are also the secure coding specifications given by OWASP. In addition, through the use of secure devices and security policies, we can protect our application systems to prevent them from being attacked and destroyed.
Gateway security is an aspect that needs to be paid special attention to after the application system architecture is implemented in a microservices architecture. With the innovation of new application system architecture, the security aspects of the new architecture need to be re-examined from the aspects of system architecture and security policies. This point is often overlooked, which requires our architects and IT leaders to carry out security risk assessment for the security and stability of the new architecture when making technical architecture changes, especially for new technologies and new frameworks.
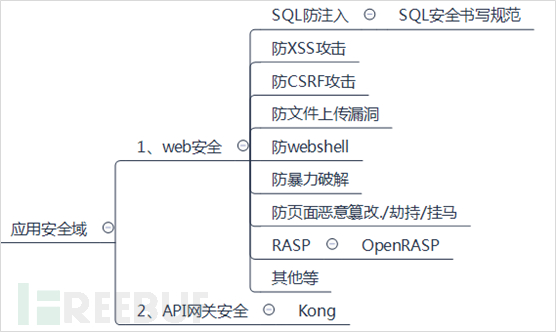
In fact, in the application security domain, the most important security device is WAF, the WEB application firewall. Generally, a WEB application firewall should have common web protection functions such as SQL injection prevention, XSS attack prevention, CSRF attack prevention, file upload vulnerability prevention, webshell detection and blocking, brute force attack prevention, preventing pages from being maliciously tampered with, and page hijacking. With the coordination of security policies, it can also prevent the vast majority of security attacks.
6. Data Security Domain
The data security domain is one of the most core contents in the network security domain. Because all application systems are ultimately transformed into data for storage, management, and use, and data is also one of the most important core assets of enterprises.
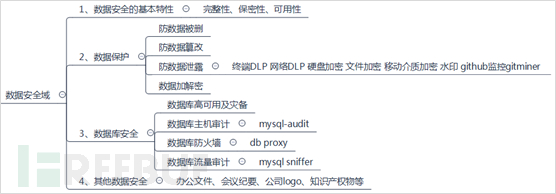
Data security mainly includes four parts: the basic characteristics of data security, data protection, database security, and other data security.
- In coordination with the five characteristics of information security (integrity, confidentiality, availability, non-repudiation, controllability), the three characteristics of data security are availability, integrity, and confidentiality:
The availability of data refers to the fact that authorized legitimate users must receive normal services provided by the system and network. It is not permissible to reject legitimate users for the sake of protecting data leakage. Data security must provide convenient services for legitimate users.
The integrity of data refers to the fact that data must not be modified without authorization, ensuring that data is not tampered with, destroyed, stolen, or lost during storage and transmission. This requires the use of multiple plans and technologies based on encryption. Integrity is the core of data security. To ensure data integrity, it is necessary to set department personnel permissions and file security levels. This can strictly control the flow of files, monitor the operation behavior of file access personnel, and control data leakage from the source. In addition, considering that the target of hacker attacks is usually high-privileged accounts, the system has established a complete log audit system. It fully records the operation of files, especially high-privileged accounts. Through monitoring and analysis, the overall security situation is presented in real-time, and threat behaviors are identified and prevented to prevent data leakage.
③ The confidentiality of data refers to encrypting the data, allowing only authorized users to use it, and ensuring that the data is not stolen during the circulation process. This includes network transmission confidentiality and data storage confidentiality. This characteristic requires encryption technology to be automatic, real-time, accurate, and reliable.
(2) Focus on the basic characteristics of data security, i.e., the basic requirements of data security, to protect data. In fact, data protection can be divided into prevention of accidental deletion, prevention of tampering, prevention of leakage, and complementary data encryption and decryption methods.
① Prevent accidental deletion. Data should be protected from malicious deletion through security devices, security policies, or system functions. There are three levels worth protecting against malicious deletion: application system level, operating system level, and database level. Strict control should be exercised over the operation permissions of these three levels, and physical deletion should be prohibited, only allowing logical deletion, and keeping detailed log records, including deletion time, deletion personnel, deletion object, and content before deletion. In addition, for the prevention of accidental deletion, corresponding backup strategies should be formulated, and the backup set should be strictly controlled to ensure that data can be quickly restored through technical means even if it is deleted.
② Prevent tampering. Data tampering should be prevented through security devices, security policies, or functions provided by the system itself. Preventing data from being maliciously tampered with includes data tampering during transmission and data tampering during storage and use. Consistent with data anti-deletion, permission control, log recording, and backup strategy formulation should be carried out at different levels to prevent data from being maliciously tampered with. In addition, to prevent data from being maliciously tampered with, data encryption, data watermarking, and data verification methods should be provided for detection and protection.
③ Prevent data leakage. There are many channels for data leakage, and scientific, reasonable, and comprehensive measures should be adopted to prevent data from being leaked according to different channels. Common security devices include: Terminal DLP, Network DLP, Hard Drive Encryption, File Encryption, Mobile Media Encryption, Watermark, GitHub Monitoring gitminer, etc., among which gitminer should be particularly noted, which can help monitor whether the company has leaked sensitive code or data information on GitHub. For data leakage prevention, two points should be achieved: first, prevent data from being leaked out; second, when data is leaked out, it should be quickly investigated who, when, how, and what terminal leaked it to where, etc., and at the same time, the network security management should have management systems and penalty mechanisms.
(3) Database security
As one of the most important carriers of data, database security protection is crucial. The security protection of the database can be carried out from three aspects: database high availability and disaster recovery, database firewall, and database auditing, etc.
Firstly, one shouldDatabase high availability architectureTo ensure the stable operation of the database, avoid single-point failures, and work in conjunction with disaster recovery solutions such as data center disaster recovery and storage disaster recovery, there are also various high availability solutions for databases, such as master-slave synchronization (such as Oracle's DG, MySQL's replication, etc.) and clusters (such as Oracle's RAC, MySQL's Cluster, etc.).
The next isDatabase firewall. The database firewall system is deployed before the database server, addressing issues on both the application side and the operation and maintenance side, and is a database security protection system based on database protocol analysis and control technology. DBFirewall implements access behavior control, dangerous operation blocking, and suspicious behavior auditing based on an active defense mechanism. Taking MySQL as an example, the firewall function can be realized using db proxy. In fact, the position of db proxy is consistent with that of the database firewall, so the combination of both functions is a good choice.
The last isDatabase auditing. It can record database activities on the network in real-time, perform compliance management of fine-grained auditing of database operations, issue alerts for risky behaviors that the database is subjected to, andAttack behaviorTo block it. It records, analyzes, and reports on user access behavior to the database, helping users generate compliance reports and trace the root cause of accidents after the fact, while strengthening the recording of internal and external database network behavior, and improving data asset security. Taking MySQL as an example, there are open-source auditing tools such as mysql-audit and mysql sniffer, as well as its own auditing features.
In fact, in addition to the three main aspects mentioned above, database security also includes contents such as database vulnerability scanning, database encryption, and data anonymization. Common database security risks include: brute force attacks, data theft, and credential stuffing, with SQL injection attacks being the most commonly used means of database security attacks. Database security is protected by a combination of database security devices, database security policies, and the database's own security framework, as well as high availability of the database, etc.
(4) Other data security
The main protection object of the data security domain is data. In fact, in addition to the data of the application system, it also includes company files, meeting minutes, company logo, intellectual property, etc., and these contents are also one of the important components of the content security domain. The security of this part of the data, combined with the protection of products and equipment for data leakage prevention and strategies, and at the same time, it should also strengthen safety management and control, enhance the safety awareness of all staff.
Return to the data security domain, data as one of the important core assets of the enterprise, must strengthen the protection of data. At the same time, in the process of protection, it is also necessary to accurately identify different levels and types of data assets, implement hierarchical protection, and maximize the benefits of data security.
7. Business security domain
If the data security domain is the most important part of the network security domain, then the business security domain is very likely to be the most difficult part of the network security domain. Because the business security domain needs to have a deep understanding and integration of security technology and business knowledge in order to do a good job in business security protection.
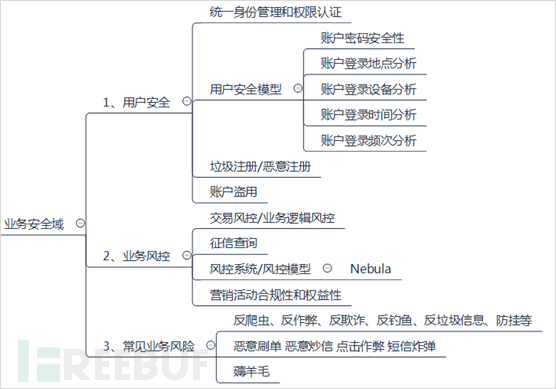
The business security domain can be introduced from three aspects: user security, business risk control, and common business risks.
(1) User security
Firstly, user security, which is also an important content that needs to be paid attention to in the design of application systems. User security requires a unified identity management and authentication module in the design of application systems, formulate user, authority classification, classification design and management of application systems, and also prevent content such as garbage registration and malicious registration. At the same time, it is also necessary to establish a user security model, analyze the abnormal situations of users, prevent the misuse of user accounts or abnormal information in system user management, etc. In addition to the requirements for user password security and complexity, the user security model also analyzes the user's login location, login device (or browser), login time, login frequency, etc., through recording user account login information, to judge whether the user is in an abnormal high-risk situation. For the requirements of user account passwords, it is recommended to comply with the following principles:
The minimum password length is greater than or equal to 8 characters
The shortest password usage period is greater than or equal to 2 days
The longest password usage period is less than or equal to 90 days
Retain the number of password history is greater than or equal to 5
Reset account lockout counter is greater than or equal to 15 minutes
Account lockout time is greater than or equal to 15 minutes
Account lockout threshold is less than or equal to 10 times
(2) Business risk control
The business security area is actually mainly about identifying and controlling business risks to ensure
(3) Common business risks
Storage storage storage pool
8. Content Security Domain
Content security domain is often overlooked in network security work, especially in the network security work of some small and medium-sized companies. The content security domain mainly refers to the content of network public opinion, media content promotion, and other aspects in the daily operation of enterprises.
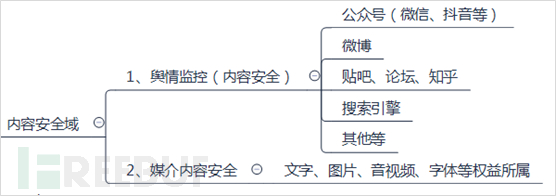
According to the mainstream methods at present, the focus of public opinion monitoring is mainly on areas such as WeChat official accounts, Douyin official accounts, Weibo, Tieba, forums, Zhihu, etc. By monitoring the company's reputation image, sensitive information, key person information, and different evaluations in different information channels, negative public opinion trends are timely contained, and positive guidance is actively carried out to avoid business disruptions caused by public opinion. Especially pay attention to black swan events of public opinion.
In the process of the company's business operations, the documents, fonts, promotional pictures, marketing copy, audio and video materials, etc., should prevent malicious leaks while also paying attention to copyright information. It is not only necessary to prevent the company's rights and interests from being violated but also to protect the legitimate rights and interests of others to avoid infringing on others.
When the company is large in scale, content security is also an important part of network security. It is necessary to monitor and guide public opinion in a timely manner to create a positive and proactive image for the company's production and operation in the Internet world. At the same time, it is also necessary to enhance copyright awareness to avoid infringement and being infringed upon.
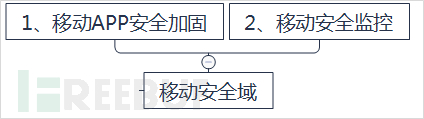
9. Mobile security domain
The mobile security domain is mainly aimed at the enterprise's mobile websites, mobile apps, and other content. The security of this domain mainly involves two aspects: on the one hand, mobile security reinforcement, that is, when developing and releasing mobile websites and mobile apps, active security reinforcement should be carried out to avoid high-risk security vulnerabilities; on the other hand, mobile security monitoring, that is, during the operation of enterprise mobile applications, security monitoring should be carried out, including availability monitoring and security monitoring.
10. Cloud security domain
For details of cloud security domain, please refer to Chapter 4 of the second part of cloud security.
4. Network security support and assistance
From the full process of IT, in addition to the security management, security reinforcement, and security operation that the enterprise needs to do in the field of enterprise network security construction, it should also assist the construction and operation of network security from aspects such as system operation and maintenance and system architecture. Secure system operation and maintenance and secure system architecture can greatly reduce the enterprise network security risk, improve the security and stability of the system and data, and provide strong technical support for the development of enterprise network security work.
1. System operation and maintenance
System operation and maintenance is closely related to network security work. In terms of work nature, both are directly facing the production environment and responsible for the production environment directly, serving as the 'scapegoat' of 7*24 hours, and there are many similarities in their work, while also closely interacting with each other.
The construction of enterprise operation and maintenance management system mainly includes the establishment process from operation and maintenance standardization, process-oriented to operation and maintenance automation and intelligence. Under the premise of standardization and process orientation, the basic operation and maintenance data CMDB, monitoring management, disaster recovery management, emergency management and other contents are completed synchronously, forming an operation and maintenance capability center to empower the enterprise IT operation and maintenance. Security runs through the whole process of operation and maintenance construction, including system security baseline, system security reinforcement, high availability deployment, disaster recovery and backup set verification, as well as under the requirements of security bottom line and self-inspection, supervision and inspection, to carry out secure, traceable, reversible, auditable, and interruptible operation and maintenance work.
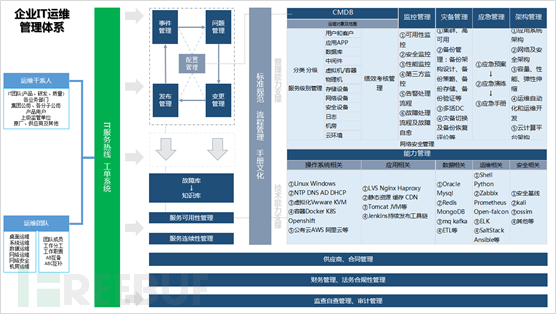
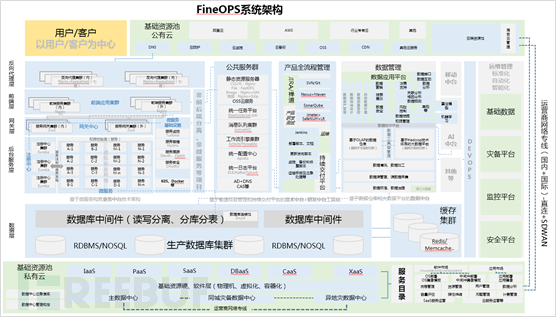
2、系统架构
安全、可靠的系统架构可以为企业网络安全建设工作提供高可用、易扩展、安全、稳定的运行环境,良好的系统架构在大幅降低自身安全风险的同时还可提供容错、容灾以及备份等相关内容,进一步提高系统可靠度。
另在进行系统架构设计时,也应遵循一些安全基本原则,特别是在微服务开展时,一定要竭力避免服务化的系统架构增加网络安全风险,为攻击者提供更过的攻击入口和渠道的情况。因为系统服务化之后,对原本复杂的系统进行了解耦,形成的服务独立部署、注册和服务化的调用,从安全角度来说,增加了网络安全攻击面,在架构设计时如不多加注意(如安全网关、内外网关分离、白名单机制、服务调用认证等,再如日志设计、链路监控等微服务基础设施的建立),很容易降低系统攻击难度系数,提高系统安全风险。另针对开源组件、开源框架的选择时,要特别注意与之版本相关联的安全漏洞,开展开源安全评估专题,对已用、在用和计划使用的开源组件、框架进行全面安全评估,有效的降低安全风险。
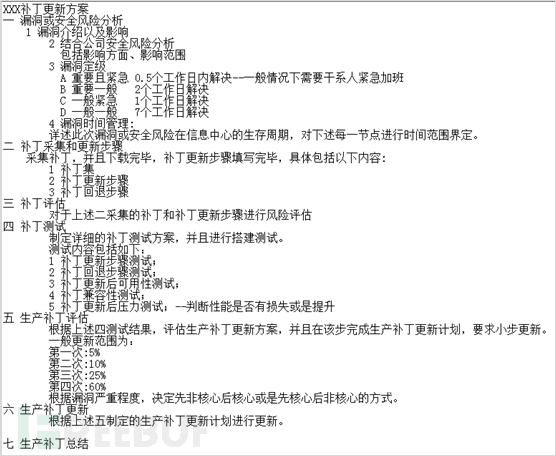
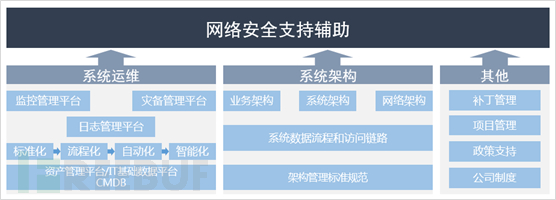
3、其他
为企业网络安全建设起支持辅助作用的除了系统运维、系统架构外,还有补丁更新方案规定(可以放在网络安全域中)、项目管理流程、业务架构等,具体不再一一展开,正如前面所言,网络安全是一个贯穿IT全生命周期、全链路的持续性工作,时刻紧绷安全弦的同时,不断建立和完善与之相关的安全标准规范,围绕最大程度降低安全风险为目标(最少最大限度地降低人为风险和主观风险)。
-------------------------------------------------------------------------------------------------------------------
作者简介:
战学超(Jan) ,某航空公司运维经理,高级架构师。曾任职于NEC软件、海尔集团。拥有丰富系统运维、系统架构经验,熟悉企业运维管理、系统架构、数据库架构、数据平台搭建、虚拟化、混合云部署及管理、自动化运维以及企业网络安全等。

评论已关闭