Introduction
On the road to enterprise network security construction, with the deployment of security facilities such as firewalls, WAF, and anti-DDoS, the enterprise network boundary has gradually become stable and difficult to penetrate; after deploying zero trust and other security access facilities, the blurred enterprise boundary also makes it difficult for external attackers to find attack entry points. Although the enterprise security construction is gradually improving, there are still weak points, and 'human factors' are one of them,Employee security awareness has become the biggest potential security risk affecting enterprisesUnauthorized access, weak passwords, and other issues have become common security vulnerabilities in enterprises.
phishing emailis one of the attack methods aimed at the 'human factor',Internal phishing email drills are an effective way to enhance employee security awareness, which allows employees to experience security attacks firsthand to achieve the purpose of early prevention of potential security risks.
Recently, the Tianyi Cloud Security Laboratory has practiced internal phishing email drills and summarized some technical experiences from the drills.
First, clarify the type of phishing email to be sent

Common email types include the following, let's analyze them first to determine the most suitable email type for sending phishing emails:
public email: By sending phishing emails through public email services such as 163 email, qq email, and the like. When the victims see that the corporate email has received a message from an external public email, they are likely to feel distrustful, and such phishing emails areare easy to detect.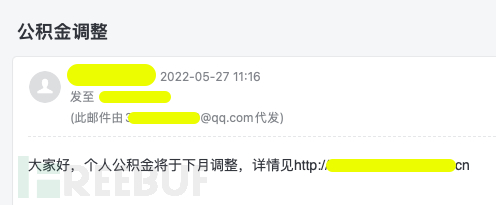
corporate internal email addresses: By sending phishing emails using internal corporate email addresses, it can directly make the victims feel trust, but in actual situationsphishing email attacks come from outside the enterprise, while external attackers usually find it difficult to obtain internal corporate email addresses for phishing, so this methodhave low practical significance.
external email addresses similar to internal corporate email: For example, for phishing email attacks against Apple Inc., use @app1e.comor@apple.netemail addresses, these types of emailIt is easy to confuse employees with low security awareness. Therefore, this article will adopt this method for phishing email drills.
Second, proceed with domain registration
to use a specific @Emails with suffixes require registration of the corresponding domain, for example, to use@app1e.comthis email, you need to register first.app1e.comthis domain. Registering a domain is an easy thing, basicallyas long as the money is available. In fact, in addition to popular domain suffixes such as com, cn, etc., such as .xyz,.mesuch domains are quite cheap, but as phishing email effects are slightly reduced.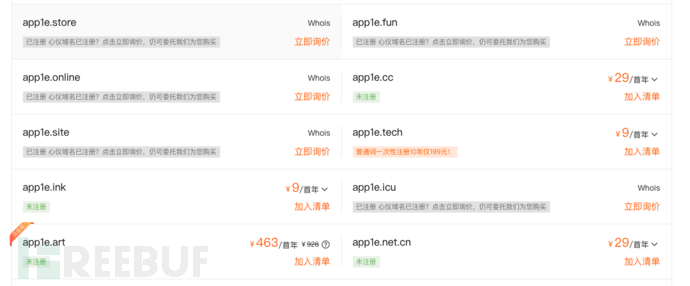
III. Configure Email Server
Once you have your own domain, you can set up email services based on this domain, thus owning your own @ email.
One method isto set up your own email server, the advantage is that there is no sending limit, but the disadvantage is that it takes time and effort.
The second method isto map the corporate email service to your own domain, for example, registerNetEase Corporate Emailor registerWeChat Workand will provide corporate email services, the advantage is convenient to use, but the disadvantage is that there are some limitations. For example, NetEase's corporate email willlimit the number of emails sent per day, WeChat Work email willto monitor spam emails in the sending process. In addition to NetEase and Tencent, there arezohoetc. can be chosen, simple and free.
In summary, this simulation does not consider setting up your own email server, and free corporate email services can meet the needs.Especially since even the monitoring of spam emails sent cannot be bypassed, how can you expect to catch fish?
After completing the registration on the above website, the most important step isThrough DNS resolution, parse the MX record of your domain name to its corresponding email server, so that you can use the corporate email service through your own domain. For example, if you use the 163 corporate email, you need to configure the following DNS records:
mx.ym.163.com Priority 5
If you use a WeChat Work email, you need to configure 2 items:
mxbiz2.qq.com Priority 10
mxbiz1.qq.com Priority 5
Finally, add the corporate email account to the email management platform, complete a series of operations, and then you get a dedicated phishing email, such asadmin@app1e.com.
IV. Clarify the Type of Phishing Website Platform
Phishing websites generally use a forged login page to deceive corporate employees' account and password, such as forged company OA login pages, Gitlab login pages, etc. However, in most cases, external attackers do not know what the internal OA looks like, so using a forged Gitlab login page of a public platform is more practical. However, Gitlab can only target developers for phishing, so this article usesConfluenceThis widely used document platform to set up phishing websites.
V. Setting up a Phishing Website
Since phishing websites only need a login page, there is no need to really set up a Confluence. You canzoomeyeand other control mapping tools, find an open Confluence site on the Internet and obtain the login page.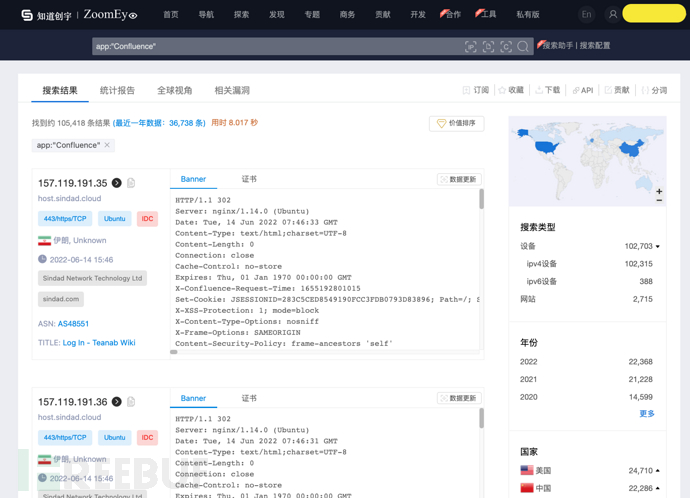
Take Chrome as an example, as long asCommand + Sand can store the static data of the web page locally.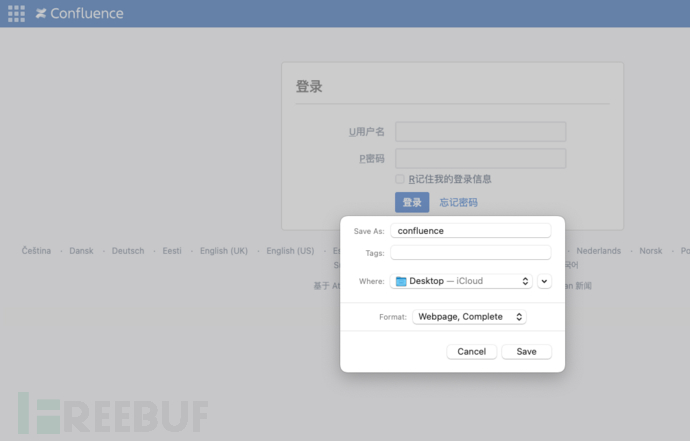
However, if you directly open the index file saved by Chrome, you will find that some elements are missing, such as the LOGO in the upper left corner. You can find the missing elements (usually absolute path access, so CORS occurred) through browser network request debugging, and you need some manual operations to download these actual elements to perfect the display of the login page.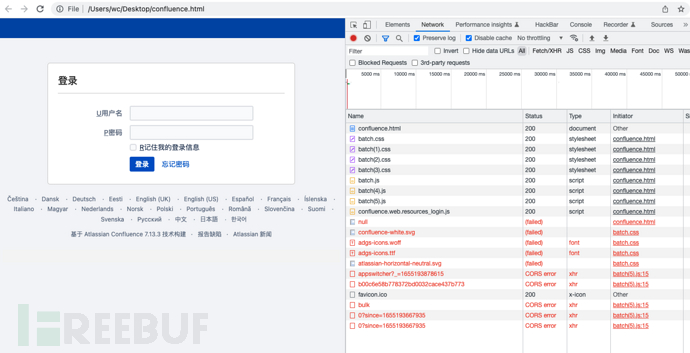
In a real phishing attack, the user clicksLoginAfter pressing the button, the user will generally be redirected to the real confluence page, so the victim may think that they have just entered the wrong password, without realizing that they have been phished. But in the phishing exercise, there is no need for such麻烦, directly remind the internal employees who are phished to improve their security awareness.
Next, some modifications need to be made to the code to meet the requirements of the phishing exercise:
- Change the HTTP method of the form submission from
POSTtoGETso as to facilitate subsequent log analysis; - Change the address of the form submission to
phish.html, which is a reminder page for employees to be aware of phishing attacks; - Create
phish.html, and write a warning statement.
<form name="loginform" method="GET" action="phish.html" class="aui login-form-container">
After it is ready, after logging in through the forged confluence login page, the user will enterphish.htmlpage. Since the form is submitted using GET, the username and password entered by the user are transmitted in plain text in the URL, making it convenient to analyze logs later.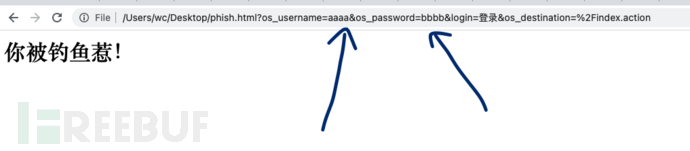
Chapter 6: Phishing Website Publishing
After the phishing website is designed, it can be deployed on the public internet so that others can access it. You can purchase a server with a public IP to build it yourself, or use website building services to do so (some website building services are free).
After completing the second step of registration, the phishing email domain name can be used as the domain name of the phishing website, such asconfluence.app1e.comYou can use the DNS A record of the domain name to the IP address of the server where the phishing website is built.
Chapter 7: Introduction to gophish
gophishIt is an open-source management platform for phishing emails, which is convenient for managing phishing email templates, sender email addresses, and phishing processes.
Chapter 8: Sender Configuration
Configure the registered corporate email aboveadmin@app1e.comAs an example of a phishing email sender email, in order to use the 163 corporate email, you need to configureHostThe SMTP service address and port for 163 corporate emailsmtp.ym.163.com:25.
The SMTP service port used by WeChat Work corporate emailsmtp.exmail.qq.com:25.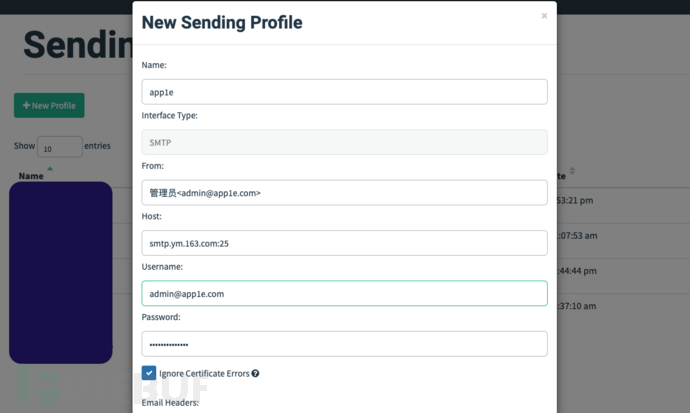
Nine, writing phishing email templates
Next, write the content of the phishing email, gophish providesHTMLformat writing email, this can write cool phishing emails, which are much more formal than plain text emails.
It should be noted here that the link to the phishing website must be placed in the content of the phishing email. Thanks toHTMLwith the support of<a>The link created by the tag, making the user think they clickedapple.comIn fact, however, clickedapp1e.com.
and the parameter in the URL{{.Rid}}Then replace it with the user's unique identifier when gophish actually sends the email, for subsequent positioningWho is the internal staff member who clicked the phishing link.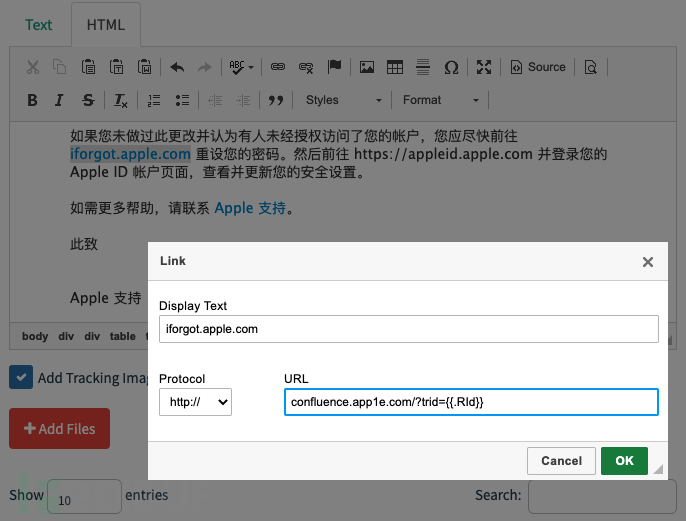
Ten, target configuration
ThroughUser & Groupsmodule, you can import the internal staff's email using a csv file.
Eleven, launch phishing
All is ready, throughCampaignsmodule to send the phishing email finally. SelectSender email configuration, selectPhishing email template, selectTarget email group, clickLaunch CampaignAfter completing the sending of the phishing email, inCampaignsYou can view the details of the phishing email sending in the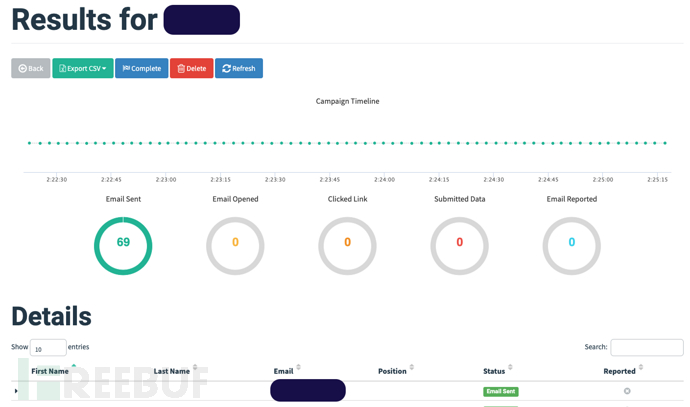
Twelve, harvest
This drill usesQuery logto monitor the results of the phishing, to know which internal staff member clicked the phishing email, even entered the username and password. Since the form submission method has been changed to GET, it can be accessed through the access log (access.log).
For example, if using a phishing website hosted by an Nginx server, you can/var/log/nginxin the directory, execute the commandsudo cat access.log | grep trid=Filtered to get the results of the phishing email clicks; execute the commandsudo cat access.log | grep phish.htmlcan filter the information entered by the user name and password on the phishing website.
(Here I wanted to paste an image, but there was too much need for watermarking, so it was omitted)
parametertridis the identifier for each user, through which it can be learned in gophish to find out which employee's email clicked the phishing email, thereby conducting targeted safety awareness training. For example, the field can be filtered using the above commandtrid=5V6PL8R, which can be searched for in the Campaigns module: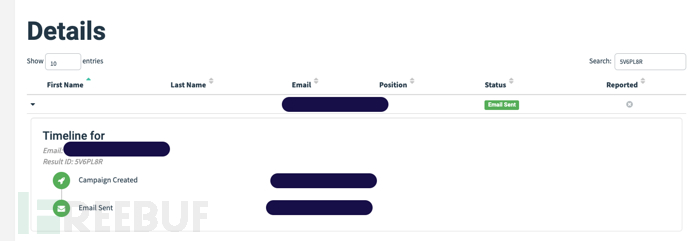
Declaration
The content of this article is only for internal phishing email drills for corporate training and learning reference, please do not use it for phishing attacks, otherwise the consequences are at your own risk. Everyone should abide by the law and jointly maintain a green and safe cyber environment.
评论已关闭