Why Conduct Phishing Drills
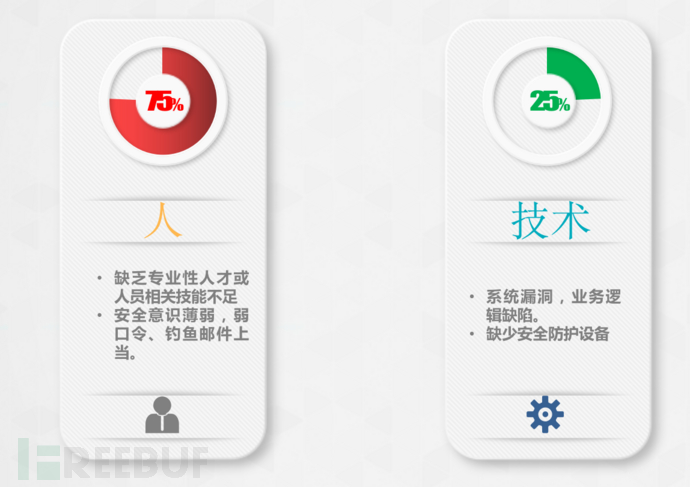
Information security engineers working in Party A are believed to know that regular security awareness training for company employees is one of our work contents, with a clear purpose: to change employees' unsafe behaviors and reduce human risks through security awareness training. According to the data analysis of the origin of network security issues, 75% of security incidents are caused by humans, largely due to weak awareness, such as weak passwords, falling for phishing scams, etc.; only 25% are related to technology, including system vulnerabilities, configuration defects, and business logic defects, etc.
 To better understand the level of security awareness maturity in enterprises, phishing email testing is the best evaluation method, and it is one of the most effective ways to verify the effectiveness of security awareness training. Especially for new information security engineers in the company, conducting a phishing test can quickly understand the stage of security awareness among company personnel and carry out targeted security awareness training. Not trying, not knowing; trying, being startled.
To better understand the level of security awareness maturity in enterprises, phishing email testing is the best evaluation method, and it is one of the most effective ways to verify the effectiveness of security awareness training. Especially for new information security engineers in the company, conducting a phishing test can quickly understand the stage of security awareness among company personnel and carry out targeted security awareness training. Not trying, not knowing; trying, being startled.
Some Matters about Phishing
Current Status of Phishing

In today's internet environment, phishing is a significant security threat faced by individuals and organizations. Being 'phished' is a major risk for organizations of all sizes, as opponents will use malicious emails and websites to attack users.
7. According to the joint monitoring and evaluation by Unisplendour and the 360 Industry Security Research Center, in 2019, Chinese corporate email users received approximately 34.43 billion phishing emails of various types. Globally, about 3 trillion emails are sent every day, of which 90% are spam and virus emails.
6. More than 90% of cyber attacks and data breaches originate from phishing scams. It has been reported that business email compromise (BEC) has resulted in losses of over 125 billion US dollars, but the reported number of cybercrimes only accounts for 10% to 12% of the actual total.
 Common Types of Phishing Attacks
Common Types of Phishing Attacks
-
CEO Fraud or Business Email Compromise (BEC)——Pretending to be the CEO or other senior management of the company, send emails to employees at a lower level (usually accounting or finance department staff) with the purpose of obtaining confidential business information or prompting the victim to transfer funds to a fake account.
-
Clone Phishing——By using the legitimate information received by the victim, a malicious script is simulated to create a clone of the original email, and the recipient is induced to click on the cloned phishing email by claiming that the link in the previous email is problematic and needs to be resent.
-
Domain fraud (Pharming)—Forge a new email header to make it look like an email from a legitimate company's email address. Or create a fraudulent website that makes its domain look legitimate or similar to the domain of a legitimate company.
-
Spear phishing—Use social engineering strategies to customize personalized emails and send them to specific individuals within the organization. The attacker will use the email subject as the topic of interest to the victim, to deceive them into opening the email and clicking on the link or attachment.
-
Watering Hole attack—Attack the websites frequently visited by the company's employees, infect one of the websites and implant malicious software. When you or your employees visit the website, the computer will automatically load the malicious software, so that the attacker can access your network, server, and sensitive information.
-
Whaling attack—is a type of spear phishing, opposite to CEO fraud. The attacker's target is senior management, such as CEOs, CFOs, etc., with the aim of诱导 high-level managers to input sensitive information and company data.
Common phishing attack themes
-
Financial themed
-
IT notification themed
-
Judicial authority fraud
-
Commercial electronic fraud
The harm of phishing
-
Phishing against individuals is conducted by attackers who use deceptive emails and fake web sites to carry out cyber fraud activities. The victims often disclose their personal information. Fraudsters often disguise themselves as trustworthy brands such as online banks, online malls, express delivery, etc., to obtain users' personal information.
-
Phishing against corporate networks is a form of identity theft on the Internet. It uses deceptive emails and deceptive websites to entice people to disclose the account and password of the company's internal system, the company's account and password, and the personal information of the CEO/CFO who affects the company's valuation, such as email accounts and passwords. Stealing user funds, extorting companies, causing economic losses to companies, and affecting the stock price of listed companies.
The purpose of phishing exercises
Compliance-driven
-
Article 34 (ii) of the "Cybersecurity Law": Regularly conduct network security education, technical training, and skill assessment for personnel.
-
6/7/8/9.1.7.3 of "Level Protection 2.0": Conduct security awareness education and job skill training for all types of personnel, and inform them of relevant security responsibilities and disciplinary measures.
-
Article 27 of the "Regulations on the Protection of Critical Information Infrastructure Security": Operators shall organize network security training and education for their personnel, and the training and education time for each person shall not be less than 1 working day per year. For key posts, the professional technical personnel shall not be less than 3 working days per year.
Enhance information security awareness
-
Identify and prioritize the priority of human risks, so as to take targeted measures to deal with the symptoms
-
Change employees' unsafe behavior
-
Reduce human risk
-
Improve security awareness maturity
Steps to carry out network phishing
Technical implementation of network phishing system
Phishing email drill technical support includes both company internal personnel and external suppliers. The following is a comparison of the advantages and disadvantages of the two.
Company internal personnel
Advantages: Have a better understanding of the company's corporate culture and information security maturity, and send targeted phishing email topics to different personnel. The cost is low, the reuse rate is high, and to a certain extent, it can improve the technical capabilities of security personnel.
Disadvantages: Requires technical personnel with certain technical capabilities, including the deployment of the phishing email system environment, front-end page development, and data summarization, etc. The cycle is long, and the content effect is difficult to guarantee.
External suppliers
Advantages: Can achieve a certain degree of customization, with considerable advantages in technical capabilities and industry foresight, and provide guaranteed technical support.
Disadvantages: High cost, lack of in-depth understanding of specific threats to the enterprise and characteristics of positions; the reuse rate of the phishing email system is low, and the old system may not be applicable after changing suppliers
In summary, we can comprehensively consider past drill effects, demand matching, delivery and management, etc. There are many external suppliers to choose from, and this will not be elaborated. If the company's internal personnel are to implement it, it is recommended to use an open-source system gophish as a phishing email platform, with the front-end page using HTML+CSS+JavaScript, etc., which is very good, easy to use, and free to play phishing emails. This is what the boss wants most, free and good. Attached is the GitHub address:
https://github.com/gophish/gophish
 Set email subject
Set email subject
-
Pretend to be the company's IT or administrative department to send phishing emails, facing: all staff.
-
Disguise supplier or customer to send phishing emails, facing: procurement, sales, administration.
-
Forge interview candidate to send phishing emails, facing: finance, legal affairs, HR.
No matter which one is chosen as the test object, the consent of the top management is required.
Set difficulty
-
Level 1 phishing attacks - there are many indicators that can easily identify them as 'phishing emails'
-
Level 2 phishing attacks - emails based on company information or personal information
-
Level 3 phishing attacks - targeted and specific phishing attacks
-
Level 4 phishing attacks or spear phishing attacks - characterized by personalized information, trademarks, and no spelling errors.
When conducting drills in the enterprise, the following points should be noted:
- Cannot pretend to be related regulatory units of public security, procuratorate, and judiciary, including logos, phone numbers, and real information of staff
- The content needs to be in compliance. The email body cannot publish or spread anti-party and anti-social opinions; it cannot infringe on business secrets; it cannot obtain state secrets illegally; it cannot infringe on citizens' personal information.
- Cannot cause damage to the company's existing system to steal the company's business secrets
Script
After testing phishing emails, we will receive reports from employees. We need to unify the script to avoid revealing the secret early, such as
Thank you for your feedback. We will first confirm whether the email is a phishing email. Please do not perform any operations before confirmation. We will notify you as soon as possible. Thank you.
Tracking and statistics
-
The number of clicks
-
The number of people who reported phishing email attacks
-
The number of people who clicked but did not report
-
The number of people who clicked and reported
-
The number of people who did not click and did not report
-
The number of people who did not click but reported
The above data can be obtained from gophish, with a focus on click-through rate and reporting rate
Conduct training
-
Review this phishing email drill, show the data in the previous step, and conduct information security awareness training for employees
-
Introduce common types of phishing emails and how to prevent them, as well as the reporting channels after receiving phishing emails
Repeat
-
Conduct phishing email tests regularly to avoid employees lowering their vigilance after a long time. For new employees, they may lack relevant information security awareness training. Improve information security awareness through real drills.
-
Keep up with the popular phishing email attack methods
-
Compare the test results with the previous test after each test, check whether the unsafe behavior of employees has been improved. Summarize the existing deficiencies and areas that need to be improved to avoid the same problems in the next test.
Common problems of phishing and improvements
Common problems
-
Overly focus on the emotions and feelings of employees.
-
Senior leaders are exceptions.
-
Content causes discomfort to employees and forces the test to be stopped.
-
Think too much training is boring.
-
Employees directly delete phishing emails.
-
Employees may not be able to distinguish between phishing emails and normal emails.
-
Employees do not know the reporting channels (especially new employees).
-
Emails may be automatically identified as spam, and users are unaware of the existence of the email, which may affect the scope of the test.
 Corresponding measures
Corresponding measures
-
Phishing attacks return to reality, increase the 'weight' of phishing attacks over time, but avoid too personal topics.
-
Arrange phishing attack training according to the current popular phishing methods.
-
Provide a channel for reporting suspicious emails.
-
Before the drill, it is necessary to communicate with the department or business unit in charge of the test and obtain authorization from the top management.
-
Add the current situation of phishing emails and how to identify them to the security awareness courses to strengthen the awareness of phishing emails
Summary
We need to conduct phishing attack tests like attackers and test employees based on the current popular attack methods, so that employees can learn to identify phishing attacks in the tests, avoid being deceived by real phishing attacks, and integrate phishing attacks and social engineering into security awareness training. Before carrying out phishing attack drills, it is necessary to set reasonable goals for the organization unit and how to measure this goal.
These are my views on the phishing email drills for enterprises, hoping they can help you who are reading this article. If you have better opinions, please leave me a message and do not hesitate to teach me. May we help the company reduce the security risks caused by human factors to the maximum extent and safeguard the pure land of cyber security.
Note: Some data in this article is quoted from the China Cybersecurity Talent Education Alliance
Enterprise internal phishing email drill guide
How to deploy and implement (cloud) host EDR + situation awareness platform for large enterprises
How to effectively handle enterprise data security complaints and reports?
How does Wine implement the cross-platform compatibility layer for Windows?
Full-patch domain forest collapsed in 5 seconds? Trust avalanche after encryption upgrade.
How to use large language models (LLMs) to automatically detect BOLA vulnerabilities
4. Corporate Defense and Attack Exercise: Email Phishing Practice
评论已关闭