
The current version of PiDense supports monitoring the following malicious wireless network activities:
1, Similar SSID broadcasts;
2, Detect SSID brute force;
3, Detect beacon flooding;
4, Monitor de-authentication attacks;
5, Same SSID broadcasts;
6, Calculate the density of unencrypted wireless networks;
7, Monitor SSID broadcasts in the blacklist;
8, KARMA attack;
9, WiFi Pineapple activity;
Tool requirements
Hardware: TP-LINK TL-WN722N
Software: scapy, time, termcolor, argparse
Tool installation
Since this tool is developed based on Python, we first need to install and configure the Python environment on the local device.
Next, researchers can use the following commands to clone the source code of this project locally:
git clone https://github.com/WiPi-Hunter/PiDense.git
Tool usage
Running in monitor mode
airmon-ng start interface(wlan0,wlan1) (Monitor mode)
or
ifconfig wlan0 down iwconfig wlan0 mode Monitor ifconfig wlan0 up
View tool help information
cd PiDense python pidense.py -h
Tool usage screenshot
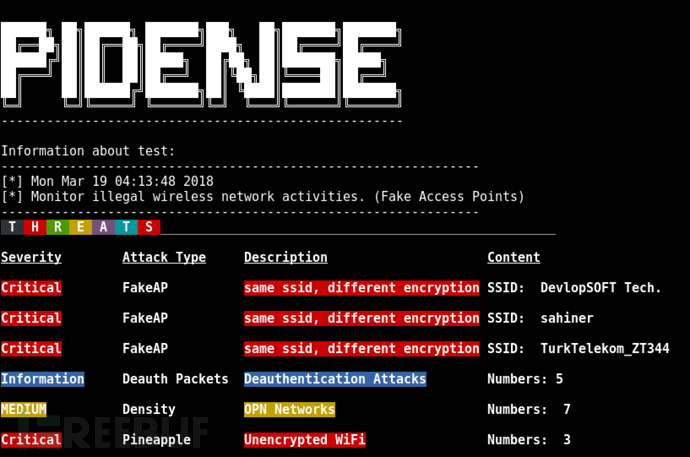
Tool usage demonstration
Demonstration video:【Click to watch】
License Agreement
The development and release of this project followGPL-3.0Open Source License Agreement.
Project address
PiDense:【GitHub link】
评论已关闭