1. Wavecrack is essentially a web application that can use hashcat to achieve asynchronous password破解;
2. The operational interface is user-friendly, making it convenient for users to select password破解 methods, and has achieved continuous automation of various attack modes;
3. It supports displaying statistical information about the破解 passwords and allows the破解 password list to be exported in CSV format;
4. The application supports a multi-user environment, with strict isolation between the破解 results of different users: user authentication can be completed through LDAP directory or basic authentication;
Tool Requirements
Flask
Celery
SQLite
rabbitmq-server
hashcat rule (Example)
Dictionary file (Example)
Tool installation
First, we need to use the following commands to clone the source code of this project locally:
git clone https://github.com/wavestone-cdt/wavecrack.git
Install RabbitMQ server and python-ldap dependencies:
$ apt-get install libsasl2-dev libldap2-dev libssl-dev rabbitmq-server
InstallationPython dependencies:
$ pip install -r requirements.txt
Create a cracker/app_settings.py configuration file using the cracker/app_settings.py.example file and modify the Mandatory settings field as needed.
Initialize the contents related to the local database in the cracker/app_settings.py configuration file:
$ sqlite3 base.db < base_schema.sql
Start the RabbitMQ server:
$ sudo service rabbitmq-server start
Start Celery:
$ celery worker -A cracker.celery
Start the Flask web server:
$ python server.py
Tool operation screenshot
Tool homepage
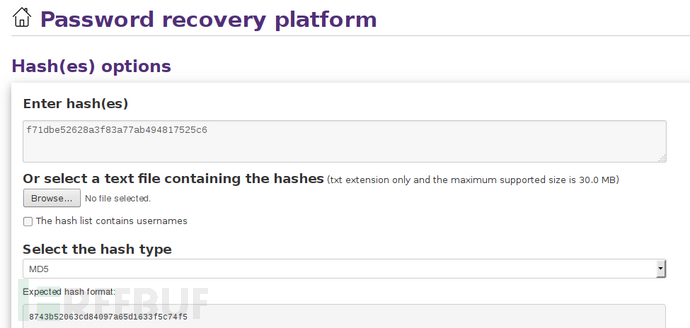
Add a hash to be cracked
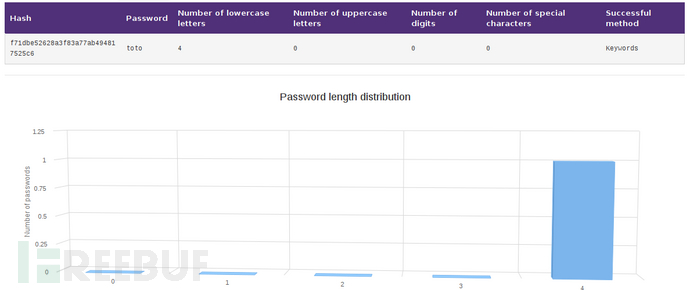
View results and other status information
License Agreement
The development and release of this project follow the GNU General Public License Agreement.
Project address
Wavecrack:【GitHub link】
Reference materials
https://bugs.kali.org/view.php?id=3432#c6062
https://hashcat.net/wiki/doku.php?id=rule_based_attack
https://hashcat.net/forum/thread-1236.html
https://github.com/wavestone-cdt/wavecrack/blob/master/setup_resources/requirements.txt
评论已关闭