
Since this tool is developed based on Python, we first need to install and configure the Python environment on the local device.
Next, researchers can use the following command to clone the source code of the project locally:
git clone https://github.com/Orange-Cyberdefense/graphcat
Then switch to the project directory and execute the installation command:
cd graphcat pip install .
Tool help information
$ graphcat.py -h usage: graphcat.py [-h] -potfile hashcat.potfile -hashfile hashfile.txt [-john] [-format FORMAT] [-export-charts] [-output-dir OUTPUT_DIR] [-debug] Password Cracking Graph Reporting options: -h, --help Display tool help information and exit -potfile hashcat.potfile Hashcat Potfile -hashfile hashfile.txt File path containing hashes (separated by lines) -john John potfile -format FORMAT Hash file format, 1 for hash; 2 for username; 3 for username:uid:lm:ntlm; -export-charts Generate PNG chart report -output-dir OUTPUT_DIR Output Directory -debug Enable debug mode
The tool is used
We need to use the -potfile parameter to provide a potfile for Graphcat, the default is hashcat, we can also use -john to provide a john potfile, or use -hashfile to provide a hash file:
$ graphcat.py -hashfile entreprise.local.ntds -potfile hashcat.pot [-] Parsing potfile [-] 164 entries in potfile [-] Parsing hashfile [-] 1600 entries in hashfile [-] Generating graphs... [-] Generating report... [-] Report available at graphcat_1672941324.pdf
Data Format
Hash Only
aad3b435b51404eeaad3b435b51404ee aad3b435b51404eeaad3b435b51404ee aad3b435b51404eeaad3b435b51404ee
Username+Hash
test1:aad3b435b51404eeaad3b435b51404ee test2:aad3b435b51404eeaad3b435b51404ee test3:aad3b435b51404eeaad3b435b51404ee
Secretsdump
waza.local\test1:4268:aad3b435b51404eeaad3b435b51404ee:aad3b435b51404eeaad3b435b51404ee::: waza.local\test2:4269:aad3b435b51404eeaad3b435b51404ee:aad3b435b51404eeaad3b435b51404ee::: waza.local\test3:4270:aad3b435b51404eeaad3b435b51404ee:aad3b435b51404eeaad3b435b51404ee:::
If a hash appears more than once in the hash file, the tool will also perform multiple calculations on it.
In addition, if the secretsdump you provided contains password history, the tool will also analyze the similarity of the password history.
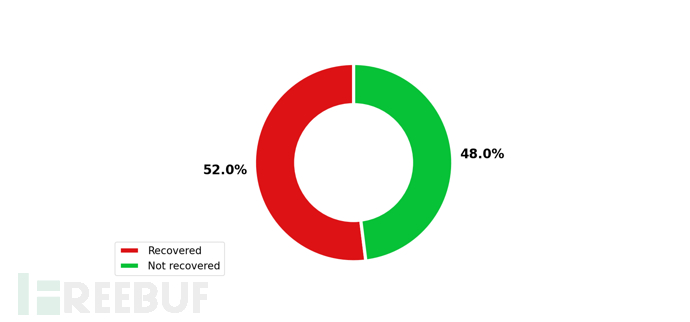
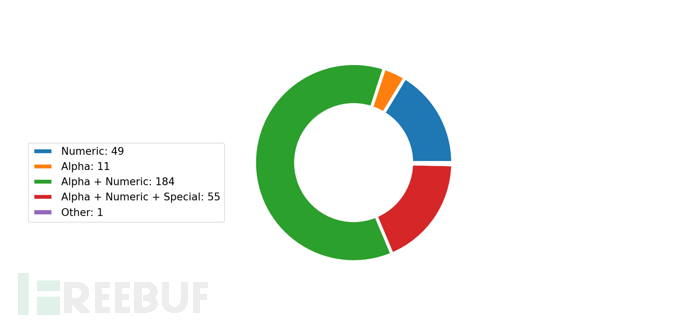
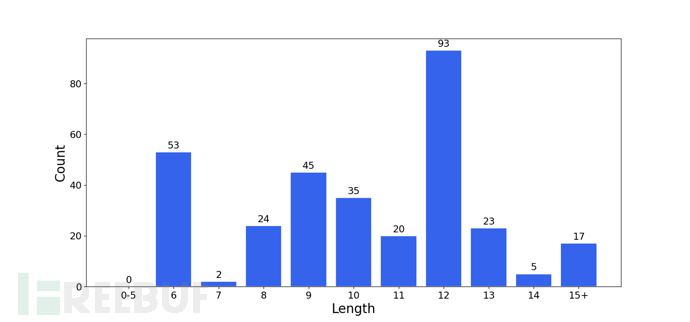
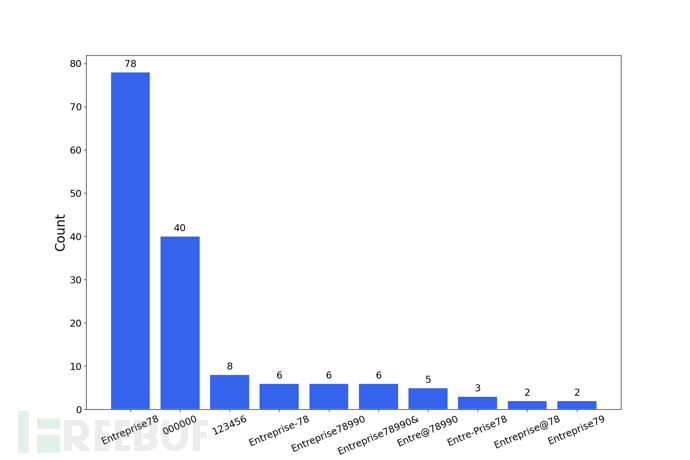
Tool Output Example
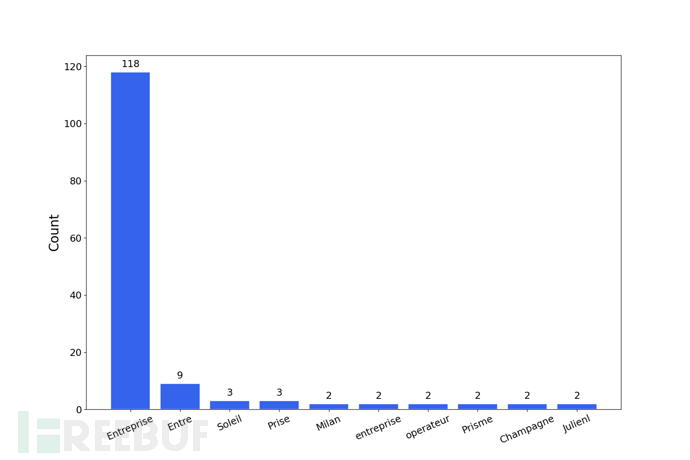
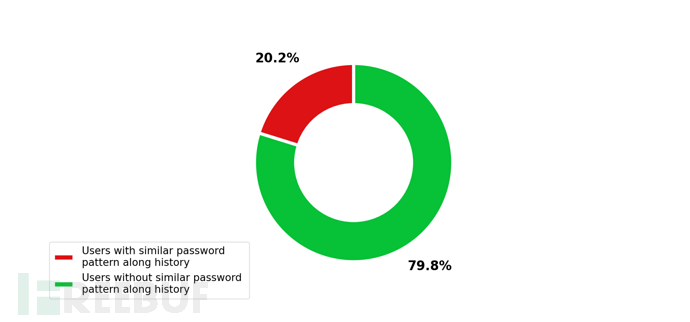
License Agreement
The development and release of this project followMITOpen Source License Agreement.
Project Address
Graphcat:【GitHub Gateway】
评论已关闭