As one of the key technologies for the realization of the future office industry (see the figure below), do you really understand what Zero Trust is? (The future office industry will revolve around cloud-network-end, cloud-native technology, 5G/6G and other higher-level communication technologies, as well as Zero Trust technology. For more details, please refer to the author's other article,}Please understand cloud-native first before talking about container security》)。This article will give a detailed explanation of Zero Trust technology. Through this article, you can deeply understand the essence of Zero Trust and avoid some of the misunderstandings in your past cognition.

Firstly, let's clarify one point, Zero Trust is only a concept of network security architecture design, just like our traditional network security architecture design concept, that is, the 'partitioning and regional protection, boundary protection' design concept mentioned in the level protection, including a variety of other design concepts, such as 'deep defense', 'dynamic defense', 'active defense', etc. In essence, they are all a paradigm of network security design. Having clarified this, we can talk about how the concept of Zero Trust was born.
We know that the birth or sudden popularity of any technology is not accidental, it must have rich and tortuous accumulation of work. The Zero Trust concept is no exception. It was first released by the U.S. Department of Defense as an enterprise security strategic research, known as the 'Black Core Program'. The Black Core proposed that the security model (idea) based on boundaries should be transformed into a security model based on user operational behavior (from focusing on boundaries to user-centered, isn't this the connotation of the Zero Trust concept!). Then, in 1994, the concept of boundaryless network security was proposed at the Jericho Forum (it sounds familiar, isn't it the core premise of Zero Trust design!). Later, in 2010, John Kindervag formally proposed the concept of Zero Trust in the Forrester report, mainly used to describe the security model from implicit trust based on network location (so-called implicit trust refers to default trust under certain conditions, for example, for traditional network security models, internal network users are implicit trust zones) to a continuous trust assessment security model based on user behavior.
Mindful students will definitely raise questions: Why didn't zero trust develop and promote at that time, even though the concept existed from the 1980s to the 1990s? This is closely related to the development of the Internet. The early development of the Internet was divided into an untrusted Internet and a trusted local area network (LAN). Everyone worked in the LAN, and business/terminal computers were all inside. Therefore, the boundary was very clear, which is why the past cyber security models were based on the security concept of 'boundary protection'. After 2010, with the rise of cloud computing, mobile Internet, BYOD, the Internet of Things, and other factors, users began to move their business to the cloud, engage in mobile office work, and promote BYOD, and achieve everything interconnected. This led to the gradual generalization and blurring of security boundaries. The security concept of 'boundary protection' based on the past faced significant security challenges. Therefore, the zero-trust concept of boundaryless, user/business-centric, has gained the soil and environment for existence. Moreover, the impact of the epidemic in recent years has further promoted the progress and development of a series of technologies around the 'zero-trust' concept.
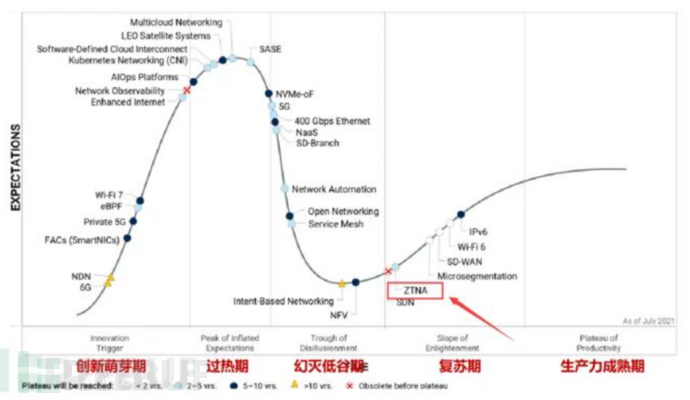
From the 2021 Gartner Technology Maturity Curve, as shown in the figure below, zero-trust technology has moved beyond the development trough and entered a recovery period. Therefore, in the next 5-10 years, the cyber security industry will witness rapid development and application of zero-trust.
Part Two: Zero Trust Technology Architecture
1. How to design to meet the 'zero-trust security concept'
In the previous chapter, we learned that zero trust is just a new security concept, architecture model, or design specification. So, how can we design to meet this concept or model? Don't worry, the National Institute of Standards and Technology (NIST) known to everyone has already helped us design the principles, which is the NIST SP800 technical document 'Zero Trust Architecture'. This document states that if the design follows the following principles, it meets the zero-trust concept and architecture. The specific principles to follow are as follows:
- All data sources, systems, applications, devices, and so on are considered resources, and in other words, they must be in a controllable state.
- Regardless of your network location, such as so-called internal networks, all communications must be secure.
- Access to resources must be based on secure authorization through connections (sessions).
- Access permissions to resources should be adopted using dynamic strategies, such as device status (whether antivirus software is installed/software version status, etc.), geographic location, network changes, behavioral changes, time/date, and installed software, etc.
- Enterprises should monitor and implement strategies for the status of all owned or associated assets, as well as security postures and other information.
The above basically outlines some basic norms of zero-trust architecture design, which means any technical means that comply with the aforementioned principles can be called zero-trust technology.
Discussion on Zero Trust Network Construction and Some Details (Part Two)
Analysis of macOS spyware, are you still dare to download cracked macOS software easily?
Hackers unveil the secrets of WiFi phishing, zero trust brings a breakthrough in protection
1) Progress in the data plane and control plane of zero-trust
'Black Ball' attack is still in progress: from anti-virus detection to installation of mining
评论已关闭