In the third season, we found that the situation of malicious links in emails increased by 60% compared to the previous season; the size of spam emails and the number of 419 scams both decreased by about 30% compared to the previous season, and phishing emails were the main attack this season. The following are several special samples found in East Asia this quarter:
Phishing emails that bypass detection through character transformation
In the third season, we observed a special phishing email. This phishing email impersonated Amazon notification letters and appeared with the common features of general phishing emails: the displayed link is inconsistent with the actual link.

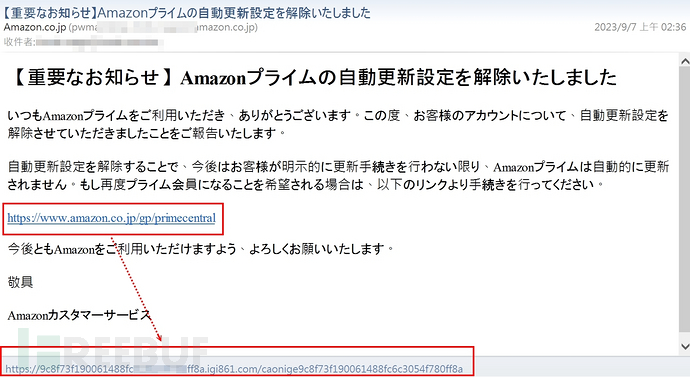
(A common feature of general phishing emails: the displayed link is inconsistent with the actual link)
It is worth mentioning that if the original file of this phishing email is directly checked, some characters will be displayed in a way that feels out of place.
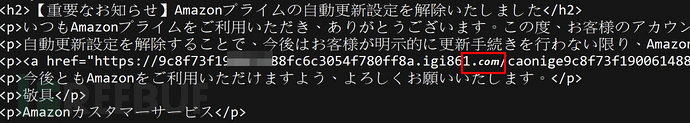
(By examining the original file of this phishing email, it will be found that the display of .com seems to be inconsistent with other English characters)
This is because the attacker uses Unicode characters to replace some characters in the domain name. The attacker can also make other changes to the domain name in the malicious links within the email.For example: switching lowercase letters to uppercase letters, or adding invisible characters...And so on, thereby bypassing the database comparison judgment, and such methods can still be parsed as clickable malicious domain URLs by browsers and email systems.
One button with two phishing links
We also found a strange case: a fraudulent LinkedIn phishing emailTwo phishing links are hidden in the same button. By operating the mouse movement on the button, you can see the switch of the two hyperlinks.
The two hyperlinks lead to different servers, which seem to be compromised websites. In a directory of their website branch, there is hidden redirection program code that will lead the hooked victims to another compromised phishing website, for example: hxxps://cendas.com.ar/wp-content/china/chinaserver-LINKEDIN/#(The victim's E-mail Address encoded in base64), and at the same time, two phishing links are set in a button, which may be to avoid blocking and increase the success rate of phishing.
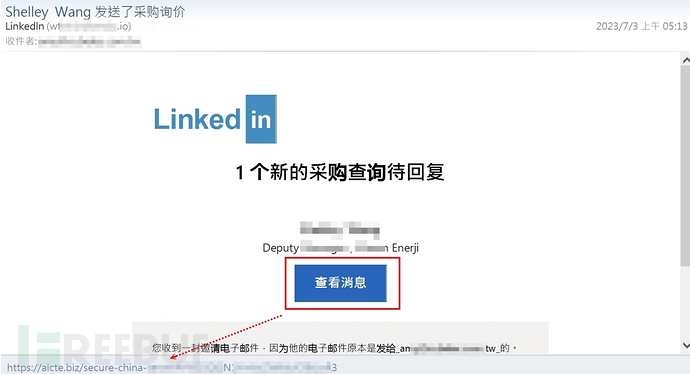
(Common Fake Phishing Email)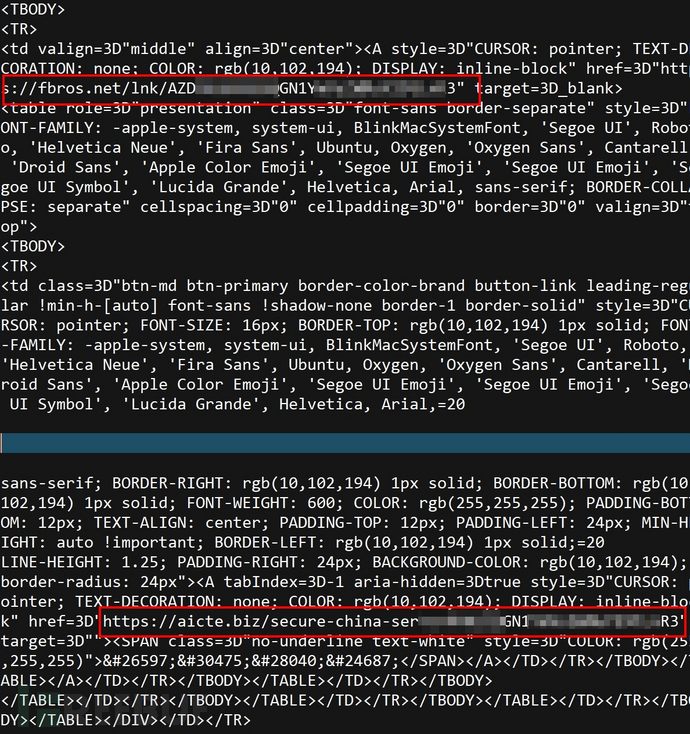
(After viewing the source file, it can be seen that it is linked to two different phishing websites)
Comprehensive Phishing Techniques
Through the fraudulent email of a certain e-commerce in Taiwan, multiple techniques are used. Firstly, social engineering is used to inform the e-commerce that it is unable to verify the user's credit card, which may cause the user to be unable to pay, followed by the explicit display of the e-commerce hyperlink, but actually linked to the compromised phishing web page, which is a common means of phishing emails.
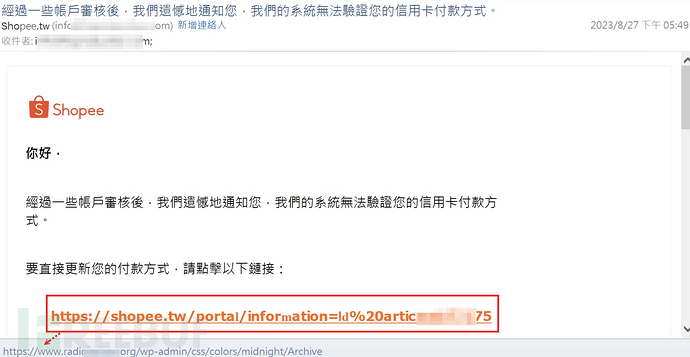
(Fraudulent E-commerce Email)
Analyzing the original file, we found that the attacker has hidden a 1x1 image in the email, the source of which is [[TRACKINGPIXEL]], which may be due to the attacker forgetting to replace the variable defined in the phishing template with the tracking link. However, if a valid tracking link is placed here, when the user opens this email, if the image is not blocked, it will notify the statistical host to record all the clickers' information of this letter, including time, IP, MUA version, and let the attacker know the protective status of the target...and other relevant information.
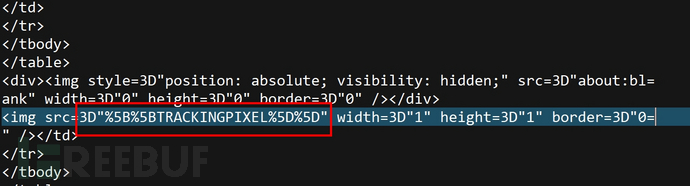
(The attacker forgot to replace the variables defined in the phishing template with tracking links)
When the victim accidentally visits the phishing web page, the first thing deceived is the account password used for e-commerce. At this stage, no matter what account password is entered, it will be recorded by the attacker. Subsequently, it will successfully jump to the next page; the stolen account password may be used for subsequent other attacks.
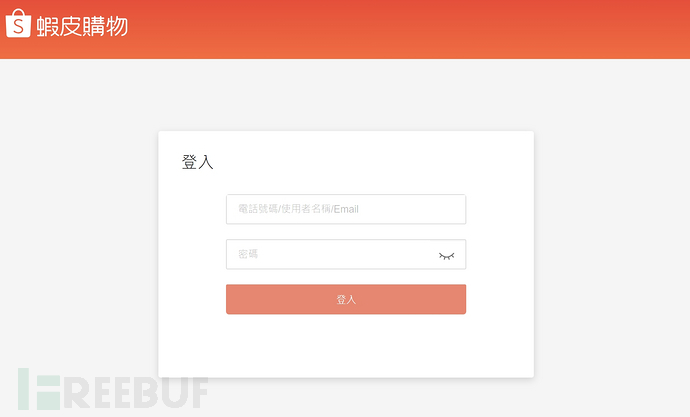
(The first thing deceived is the account password used for e-commerce)
The second step is to defraud the relevant information of the credit card. At this stage, the victim may be deceived into adding a new credit card for shopping convenience. It is clever that no matter what credit card data is entered on this page, it will be recorded by the attacker after sending, and then a prompt 'Error occurred, please enter the card number' will be displayed, and the related fields of credit card data will be cleared. The victim may change another card to input in a hurry, which may result in the continuous theft of multiple credit card data. This attacked phishing website is still running until the time of this report.
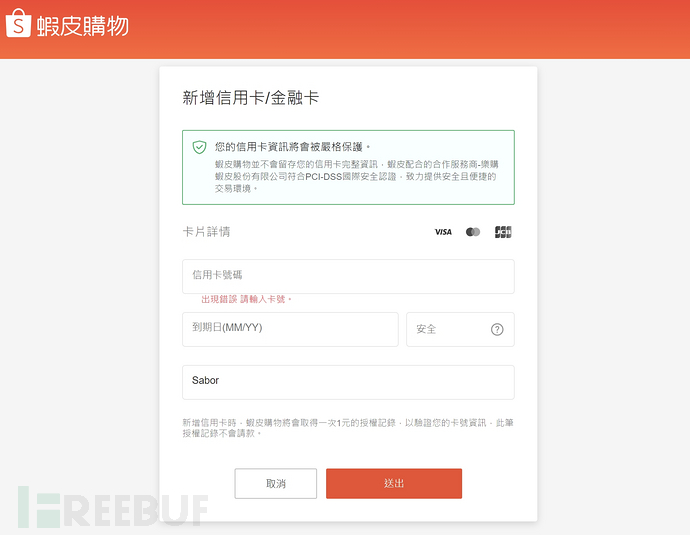
(The victim may change another card to input in a hurry, which may result in the continuous theft of multiple credit card data)
Be aware of the abuse of remote control and maintenance software
In this season, it was also found that attackers tried to place remote control software in external public links in the way of social engineering, without mentioning remote and maintenance actions in the email, and cunningly avoid detection by email security system scanning, causing users to inadvertently execute installation and be remotely controlled for malicious purposes.
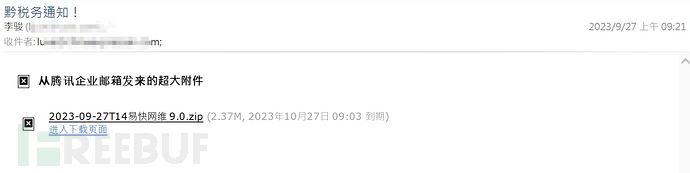
(Placing the remote control software on external links to avoid detection by email scanning)
After the victim downloads the remote control software compressed file, the attacker sets the configuration file of the remote control software as a hidden file; therefore, under the default settings of Windows, the decompressed files look like only one remote control software.
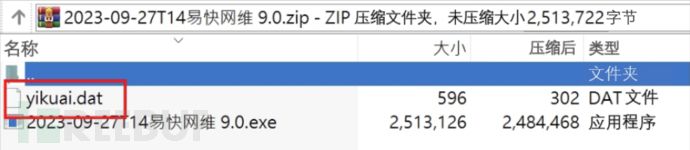
(The configuration file of the remote control software is set as a hidden file by the attacker)
Looking at the content of the configuration file, it can be found that this configuration file is not simple. In addition to changing the title displayed by the installed software, it also sets the connected IP and communication port, and can remotely monitor and operate the victim's computer without the victim's awareness after installation. And the remote control software originally used for remote maintenance may not be considered harmful by all antivirus software.
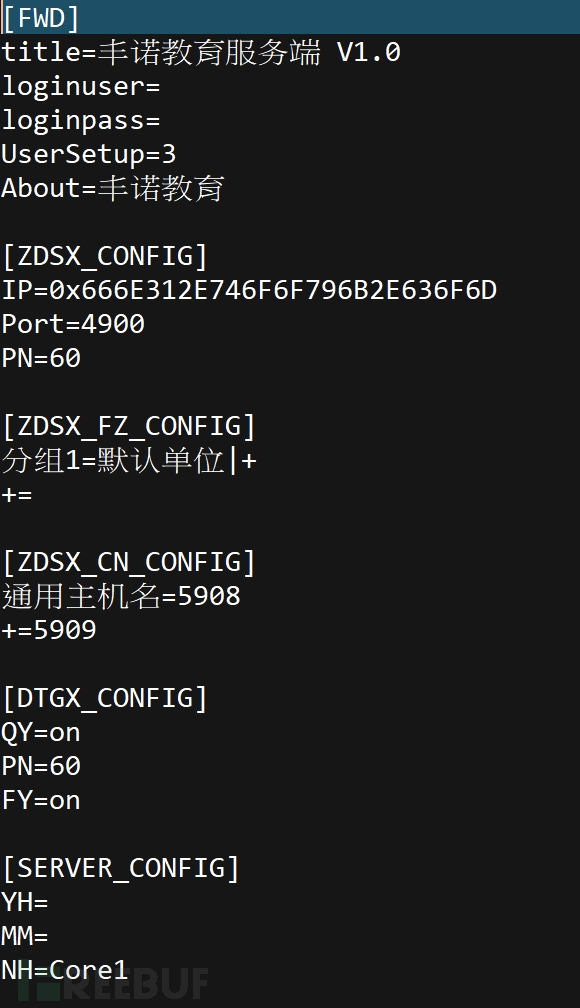
(Looking at the content of the configuration file, it can be found that this configuration file is not simple)
Conclusion
In this season, although some vulnerabilities have been exposed, they seem to have not been widely exploited on a large scale, and the overall attack mainly relies on phishing emails. As the name suggests, the goal of phishing emails is to fish for information that can be reused later; in addition to constantly evolving various detection avoidance techniques, we also notice that the attackers of phishing emails are more focused on the targets of phishing, such as: click-through rate, whether they are hooked, the effectiveness of fishing data, and more information of the target that can be obtained at the same time. These sensitive information that has been fished can be combined, pieced together, and reused repeatedly, or combined with attacks such as fraud and identity forgery.
评论已关闭